Cybersecurity threats are becoming increasingly sophisticated, and organized groups of hackers are carrying out advanced attacks against attractive targets. A key component in almost all advanced attacks is privilege escalation — an attempt to compromise an account, and then expand the attacker’s privileges, either by gaining control of more accounts or increasing the privilege level of the compromised account.
Read on to understand how privilege escalation works, how to detect it in your organization, and how to protect your systems and stop advanced attacks before they reach your most sensitive assets.
In this article, we provide you with information about insider threats, including what is an insider threat, the indicators that can help you detect insider threats and the best tools to provide protection against such threats.
In this post you will learn about:
- Horizontal vs vertical privilege escalation
- Detecting privilege escalation incidents
- The connection between privilege escalation and lateral movement
- Ways to protect your systems
- Advanced protection with next-generation SIEM and UEBA
What is privilege escalation?
Privilege escalation involves an attacker gaining access to an account, and finding a way to increase the level of privileges associated with that account (vertical), leverage their access to gain access to other user accounts (horizontal), or both.
Privilege escalation attacks are used to gain access to networks, typically with the aim of exfiltrating data, disrupting business activity, or installing backdoors to enable continued access to internal systems.
Horizontal vs vertical privilege escalation
Horizontal privilege escalation is limited because it does not grant the attacker more powerful permissions, unless the attacker already possesses a privileged account. Vertical privilege escalation is typically more dangerous, because it means the attacker is trying to elevate their permissions, with the ultimate goal of gaining administrator or system user rights on Windows, or root on Unix systems.
With root access, the attacker can steal credentials and other sensitive information, execute backdoors and other malware, erase data and otherwise disrupt business operations, or execute arbitrary code. Attackers can also cover their tracks by deleting evidence of their activity.
Detecting privilege escalation incidents
There are a few data points that can help detect and respond to privilege escalation attacks:
| Initial access point | Which account or system did the attacker initially compromise? |
| Initial threat vector | How did the attacker compromise the initial account? |
| Escalation path | What additional privileges did the attacker manage to obtain? |
| Target systems | Which accounts or systems did the attacker aim to attack and for what purpose? |
| Damage caused | What did the attacker manage to do after gaining access to the target systems? |
Privilege escalation and lateral movement
For an attacker, privilege escalation is not a standalone measure. It is typically part of a technique known as lateral movement, which takes place following the compromise of an endpoint. The attacker will typically combine privilege escalation with an attempt to move laterally across the networks to compromise additional systems and accounts.
Here is a typical lateral movement process:
- External reconnaissance—identifying opportunities for initial access points to the organization, whether via vulnerable systems or ports, social engineering, credential dumps, etc.
- Initial infiltration—the attacker uses the identified security weakness to gain access to an endpoint on the target’s network.
- Internal reconnaissance—the attacker gains information about the network, operating systems and other resources, conducts scans and looks for vulnerabilities they can exploit from the inside.
- Privilege escalation—the attacker uses their initial hold on the network to gain access to additional systems, using techniques like keyloggers, network sniffers, brute force guesses, or phishing, made more convincing by their control of internal accounts.
- Compromise more systems—attackers can use remote control tools such as psexec, PowerShell, or remote access software to access additional systems. These attempts may not arouse suspicion because remote access tools are commonly used by IT staff. Finally, the attacker will reach their end goal, such as the exfiltration of sensitive data.
6 ways to protect your systems from privilege escalation
The following are a few important best practices that can reduce the chance of successful privilege escalation attacks.
1. Password policies
It is essential to ensure users select unique, secure passwords and force them to change passwords periodically. Because this is difficult to enforce in practice, a good way to circumvent the insecure nature of passwords is to apply two-factor authentication, especially for sensitive systems and administrative accounts.
2. Specialized users and groups with minimum privileges
Review your user base and redefine user accounts and groups to ensure they have clear roles, applying the minimum necessary privileges and file access to each role. By doing this, you ensure that even if an account is compromised, the potential for privilege escalation is severely limited. This applies to all accounts — even admins and super-users should have limited access to the systems they are actually supposed to access or manage. No administrator should have broad permissions for most or all network systems.
Most importantly — remove user accounts when they are no longer needed, and have a clear, mandatory procedure for dealing with employee departure.
3. Close unused ports and limit file access
Network ports should be blocked by default and only allowed if they are really needed for legitimate applications. Identify default configurations that have unnecessary services running, and block them. In the same way, files should be read-only, with write access only enabled for users and groups who actually need them.
4. Secure databases and sanitize user inputs
Many database systems have insecure defaults, so special care must be taken to ensure databases are secured and protected by strong authentication. Data at rest should be encrypted whenever possible. Sanitize all user inputs and patch databases to prevent SQL and other code injection attacks.
5. Keep your systems and applications patched and updated
Many privilege escalation attacks leverage software vulnerabilities to gain initial access. Use vulnerability scanners to identify known vulnerabilities in your applications, and rigorously apply security patches to remediate them.
Because it is not always possible or practical to patch or update systems, especially large-scale production systems or legacy components, you may need to apply additional layers of security. For example, a web application firewall (WAF) can identify and block malicious communication related to a vulnerability exploit at the network level, even if the underlying system was not patched.
6. Change default credentials on all devices
Be sure to remove or rename default and unused user accounts. Change the default login credentials for any hardware system, including printers, routers, and IoT devices. A single device with default credentials and an open network port can become an initial access point for an attacker, leading to a privilege escalation attack.
Advanced protection with next-generation SIEM and UEBA
The Exabeam Security Management Platform is a next-generation security information and event management (SIEM), powered by user and entity behavior analytics (UEBA). Exabeam can ingest logs from security tools and IT systems, identify anomalous behavior, and stitch it together with contextual data to identify security incidents. It creates a smart timeline that shows the full path of a malicious user, with both normal and abnormal behavior performed using different user accounts and machines on the network.
Exabeam uses UEBA to create a baseline of normal behavior, making it easy to detect anomalous behavior that might signal an attack. Exabeam can assemble the complete timeline of a privilege escalation attack in minutes, without requiring a manual investigation by security analysts.
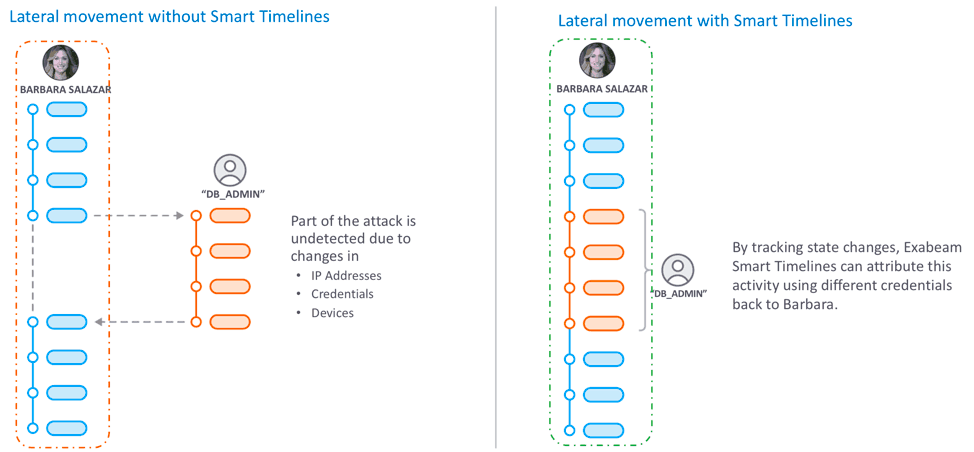
Figure 1 – An example of a lateral movement detection without and with Smart Timelines
Read more in our blog post about detecting and preventing lateral movement and privilege escalation with Exabeam.
Want to learn more about Cybersecurity Threats?
Have a look at these articles:
- 21 Top Cybersecurity Threats and How Threat Intelligence Can Help
- Information Security Threats and Tools for Addressing Them
- Drive By Downloads: What They Are and How to Avoid Them
- Cyber Crime: Types, Examples, and What Your Business Can Do
- What is MITRE ATT&CK: An Explainer
- Mitigating Security Threats with MITRE ATT&CK
- Defending Against Ransomware: Prevention, Protection, Removal
- Top 5 Social Engineering Techniques and How to Prevent Them
- SIEM Concepts: Security Incidents
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













