The adoption of cloud infrastructure by organizations has become increasingly popular due to its numerous advantages, such as scalability, security, and performance. Infrastructure as a service (IaaS) is particularly attractive as it offers computing power, storage, and networking resources without the need for organizations to invest in physical servers or manage complex data center infrastructure. By embracing IaaS, organizations can reduce the burden of maintaining on-premises data centers, cut hardware costs, and unlock valuable business insights.
However, even with robust compliance programs in place, such as PCI-DSS, HIPAA, FedRAMP, and the EU Data Protection Directive, IaaS can create new entry points for potential adversaries. Compromised credentials or malicious insiders who have access to an organization’s IaaS solution can easily expose sensitive data without detection. Cloud providers use a shared responsibility model, meaning that while they offer a secure operating environment, it is the customers’ responsibility to protect their own data, identities, devices, and applications. To prevent threats like account hijacking, unauthorized data exfiltration, or service disruptions, organizations require centralized visibility into their cloud environments.
In this blog post, we will explore why organizations require visibility and threat detection in their cloud environments, introduce TDIR for Public Cloud, and explain how it works to address four key threats organizations face in their cloud infrastructure. By implementing the appropriate safeguards, organizations can mitigate potential vulnerabilities and ensure the protection of sensitive data like personally identifiable information (PII), customer records, and API data, while maintaining uninterrupted service delivery.
In this article:
Visibility and threat detection for cloud environments
To address the critical need for visibility and threat detection in cloud environments, Exabeam offers an extended range of behavioral analysis capabilities tailored to the three major cloud providers: Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure. With our Threat Detection, Investigation, and Response (TDIR) for Public Cloud solution, organizations can proactively detect unauthorized access to cloud environments and effectively defend against various threats targeting cloud-based data. This comprehensive approach enables organizations to identify and respond to malicious activities, such as data exfiltration and the hosting of malicious files.
By leveraging TDIR for Public Cloud, organizations gain a deep understanding of the “normal” behavior patterns within their cloud infrastructure. This understanding is crucial for identifying anomalous user behavior and effectively combating cloud threats. Here are some of the key threats that Exabeam helps organizations address:
- Compromised credentials and lateral movement
- Data exfiltration
- Privileged activity
- Malware
How does it work?
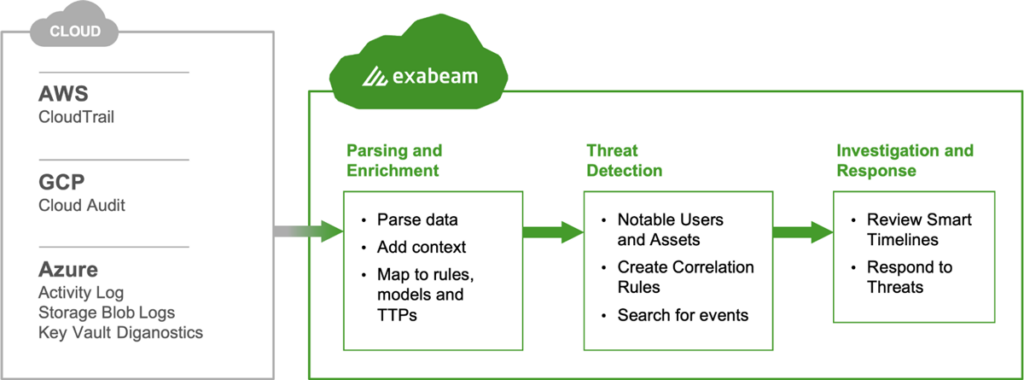
TDIR for Public Cloud provides a unified platform that monitors user and entity activities, including those within IaaS solutions. By leveraging the visibility offered by CloudTrail logs, CloudAudit logs, Azure Activity logs, Azure Storage Blob Logs, or Key Vault Azure Diagnostics, Exabeam helps organizations identify anomalies and enables security teams to more efficiently detect, prioritize, and investigate threats targeting their IaaS solutions.
The process begins with Exabeam ingesting logs from AWS, GCP, or Azure, which are then parsed and enriched with relevant content. The data is mapped to rules; models; and tactics, techniques, and procedures (TTPs) to facilitate effective threat detection and response. Leveraging behavioral analytics, Exabeam learns the normal behavior patterns of users within the IaaS environment, allowing it to identify abnormal behaviors, such as:
- Users creating or attaching policies denoting universal access
- Abnormal or first time access to an IaaS solution within an organization by a user
- Unusual amounts of data being transferred from buckets and other storage services
- Uploads of malware or cryptominers
- Irregular activity from cloud administrators
Through machine learning techniques, Exabeam establishes a baseline of normal activity for all users and entities within the environment, it automatically detects deviations from this baseline and assigns a risk score to identified activities. To aid in investigations, Exabeam provides machine-built Smart Timelines™ that stitch together both normal and abnormal behavior for users and machines. These timelines include comprehensive information, including the context surrounding an alert, such as what occurred before and after, and whether the alert maps to a specific MITRE ATT&CK® TTP.
With visibility into IaaS activity, security analysts can effectively track threats targeting their IaaS solutions. They can swiftly detect, investigate, and respond to potential attacks, mitigating the risk of service disruption, financial fraud, or the exposure of sensitive information.
With the behavioral analytics and comprehensive investigative tools Exabeam offers, organizations can enhance their security posture in the cloud. The solution empowers security teams to proactively identify and respond to threats, ensuring the integrity, availability, and confidentiality of their IaaS environments.
How to get started
If your organization operates in a multi-cloud environment and you’re seeking consistent TDIR capabilities, Exabeam is here to deliver across the three major cloud providers: AWS, GCP, and Azure. The Exabeam Security Research Team (ESRT) dedicated extensive time and effort to thoroughly understand how these cloud providers manage identities, roles, permissions, data, and storage buckets; and what data is made available in audit logs. By delving deep into these intricacies, the ESRT successfully extracted the complexities and differences, enabling us to offer a consistent TDIR experience to our customers and partners.
Now it’s time for you to explore and deploy TDIR for Public Cloud in your Exabeam environment. With this powerful solution, you can improve your security posture and effectively detect, investigate, and respond to threats across your cloud infrastructure. Experience the benefits of consistent detection capabilities, regardless of the cloud provider you rely on.
Want to learn more about protecting your data in the cloud?
Read our eBook, Insider Risk Management: Adapting to the Evolving Security Landscape.
In today’s fast-paced business world, it is increasingly difficult for organizations to secure their critical assets, and insider threats pose a burgeoning risk to those assets. As the workforce rapidly evolves, with employees working remotely and businesses adopting cloud-based technologies, critical corporate data can be accessed from almost anywhere and at any time. This leaves critical assets susceptible to being accessed, downloaded, and stolen within seconds, and without raising suspicion.
In this eBook, insider threat expert Shawn M. Thompson, Esq. draws on his experience training and building insider threat programs for more than 500 companies.
You’ll learn:
- The risks that organizations face from insider threats
- The “new breed” of insiders and the dangers they pose
- Best practices for developing an insider risk management program

Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













