In today’s digital age, the financial sector faces an array of cyberthreats that evolve as quickly as the technology itself. With financial markets in constant flux and the increasing shift to cloud and hybrid work environments, it is imperative for financial entities to adhere to a robust security framework. The Digital Operational Resilience Act (DORA) provides such a framework, aiming to bolster the cybersecurity posture of financial entities within the EU. This post explores the significance of DORA and how the Exabeam Security Operations Platform facilitates compliance while improving cyber resilience.
In this article:
- The urgency of cybersecurity in finance
- Understanding DORA’s role
- Risk and incident management
- Fostering cyber resilience and testing
- Charting the road ahead: achieving DORA compliance with Exabeam
The urgency of cybersecurity in finance
Consider this compelling statistic from the IBM Cost of a Data Breach Report 2023: The financial sector experiences the second-highest losses due to cyber incidents globally, trailing only behind the healthcare industry, with average damages amounting to approximately $5.9 million per incident. This figure contrasts starkly with the cross-industry average of $4.45 million, underlining the acute vulnerability and financial stakes for banks and financial institutions. Beyond the financial repercussions from ransomware attacks and data theft, there’s a broader impact on customer trust and regulatory compliance.
Understanding DORA’s role
DORA aims to unify and strengthen the operational resilience of financial entities against cyber risks. Unlike previous frameworks primarily guided by the ISO 27001:2022 standard, DORA sets forth specific requirements for financial institutions, including mandatory breach reporting to regulators and contractual compliance with third-party suppliers. This holistic approach ensures comprehensive risk management and operational continuity in the face of cyberthreats.
The DORA framework, alongside other industry guidance like MITRE ATT&CKⓇ and regulatory guidelines like GDPR, underscores the importance of adopting best practices in compliance and governance tailored to specific regional, industry, or customer-centric objectives. With today’s rapidly changing privacy laws, data compliance initiatives, and new modes of customer interaction, the ability for organizations to remain nimble and prepared is paramount. This includes the capacity to swiftly adapt to changing regulatory landscapes, document potential risks accurately, and devise strategies for risk acceptance or mitigation. Integrating these practices into both strategic planning and current operations not only enhances compliance, but optimizes the cost effectiveness of security program maintenance.
The advent of observability platforms marked the beginning of comprehensive network visibility. However, the complexities of cloud computing, remote work, and mobile access demand a consolidated platform capable of correlating events and detecting anomalies. Modern security information and event management (SIEM) solutions integrate security log management, user and entity behavior analytics (UEBA), and security orchestration, automation, and response (SOAR), expediting response times and reducing attack dwell time.
Data pipeline and observability
The Exabeam Security Operations Platform aligns with the DORA framework’s visibility requirements and enhances threat detection through advanced analytics. The platform offers a scalable log collection mechanism from various sources, including both on-premises and cloud based. Importantly, it supports thousands of log parsers from over 600 products, offering unparalleled flexibility to match your existing security tools. This capability ensures seamless convergence of visibility into a single, user-friendly platform.
One of the key features, Outcomes Navigator, offers prescriptive insights into each data source, enabling financial entities to assess their current security posture effectively. Outcomes Navigator facilitates this by mapping common use cases, such as lateral movement, account creation, and data exfiltration. This feature is instrumental in identifying where a financial entity’s security stack might have gaps, offering opportunities for risk discovery and mitigation.
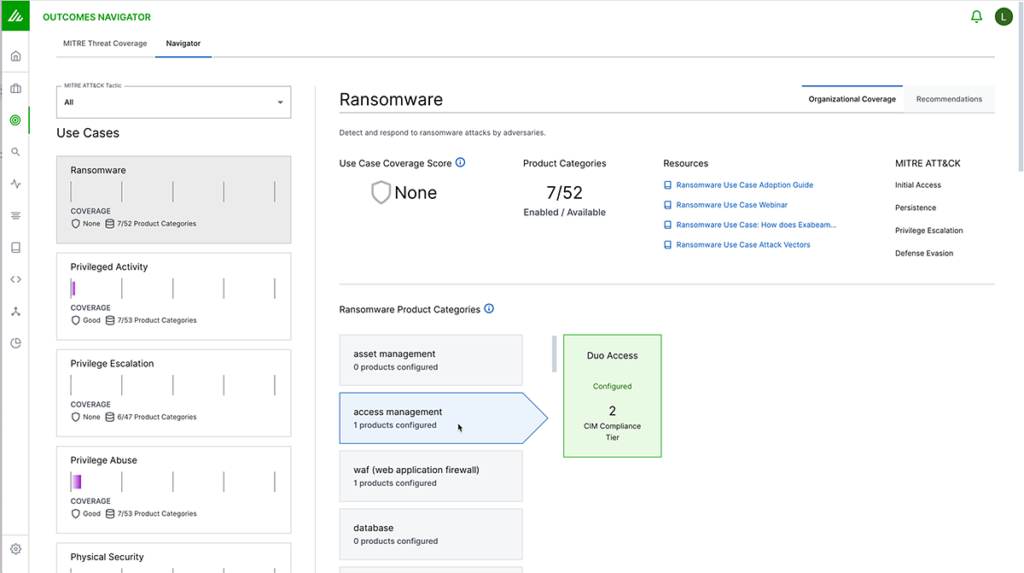
Through comprehensive correlation rules and UEBA anomaly detection, the Exabeam Security Operations Platform integrates these insights to identify threats quickly, ensuring that all associated activities are efficiently investigated and escalated, in compliance with DORA’s stringent standards.
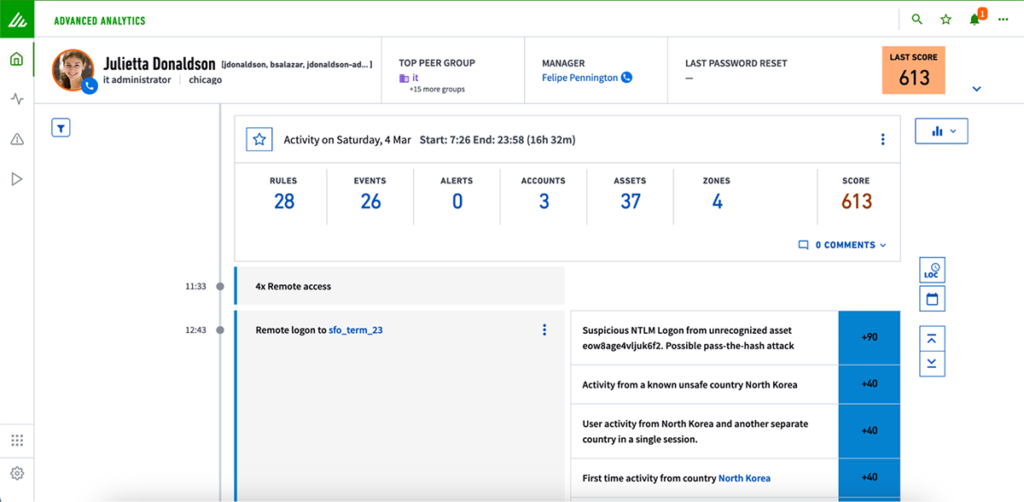
Continuous risk assessment
DORA’s core initiative is to maintain operational resilience during cyber incidents. This necessitates a thorough understanding of emerging threats and the potential for more severe breaches. Exabeam supports the classification of critical applications, assets, and users. This includes systems housing sensitive personal identifiable information (PII), payment card information (PCI), and custom applications widely used in the financial sector.
At the heart of our approach is UEBA, which employs machine learning and AI to monitor all network activity continuously. This technology establishes a baseline of normal behavior patterns, making it possible to detect anomalies that may indicate a threat. This capability is essential in reducing the impact and costs associated with data breaches. Also, during an investigation, Exabeam improves operational efficiency by generating a chronological timeline of all related activities. These detailed threat timelines provide extensive context for each alert, including activities preceding and following an incident, and whether the alert corresponds to a specific ATT&CK tactic, technique, or procedure (TTP).
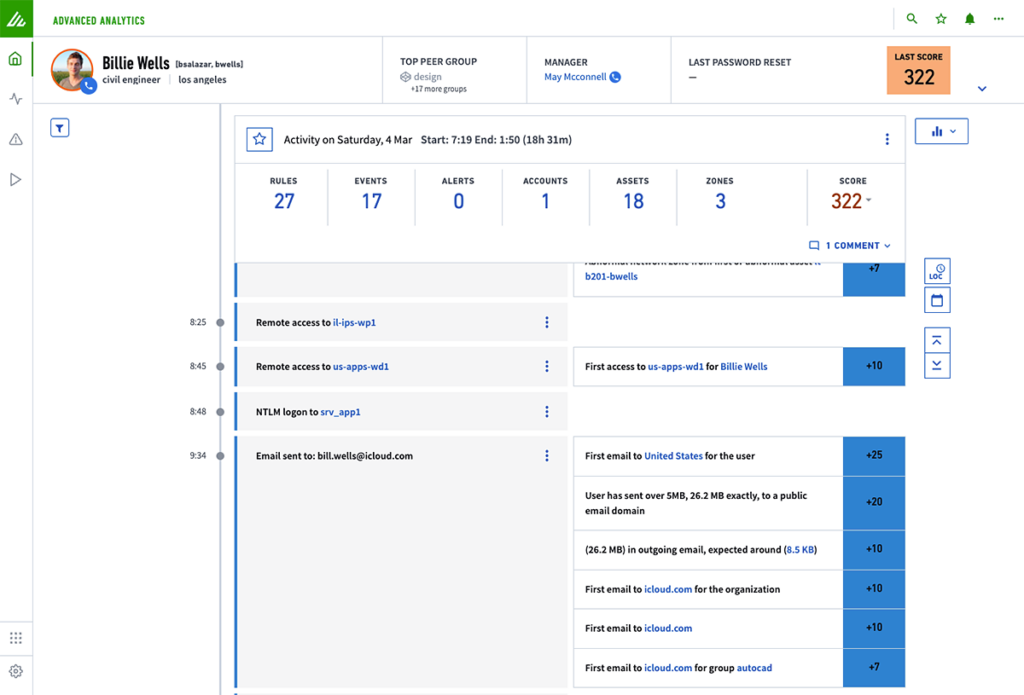
Risk and incident management
In compliance with DORA, it is mandatory for financial institutions to report significant information and communication technology (ICT) risks without delay. Exabeam enables rapid threat analysis through an intuitive risk scoring system. This system is augmented by an AI-assisted threat explainer that outlines the nature of a threat, its potential implications, and recommended steps for mitigation. Given the frequency of incidents like compromised credentials, the ability to quickly identify suspicious activities or unusual logins is key. Exabeam makes it possible for organizations to meet rigid reporting deadlines to authorities while conducting thorough internal investigations and evaluating material risks.
Boosting the efficiency of event searches, Exabeam Copilot uses natural language processing (NLP) to allow analysts to use simple language for queries, bypassing the need for complex query languages. This lowers the learning curve for new analysts and speeds up the identification of security events. The AI threat explainer offers detailed insights into incidents within Threat Center, improving communication speeds. These insights can be quickly shared with non-security personnel, ensuring complete understanding of threats, risks, and next steps across departments.
Fostering cyber resilience and testing
Strengthening cyber resilience is a complex undertaking, where Exabeam provides significant support. The Exabeam Security Operations Platform specializes in highlighting critical ICT systems for enhanced monitoring. By enriching the context around these systems, Exabeam enables precise monitoring for anomalies that could signal cyberthreats. Integration with threat intelligence services allows for the mapping of vulnerability information, leveraging machine learning and AI to detect potential cyberthreats through anomalous behavior or correlations with known issues alerted by third parties.
Additionally, the Service Health and Consumption feature offers valuable insights into data usage patterns, monitoring key connections and log volumes. This represents the health of critical log sources and aids in preemptive actions against potential security breaches.
Charting the road ahead: achieving DORA compliance with Exabeam
DORA represents a pivotal framework for financial institutions, aimed at reinforcing operational resilience in the face of cyberthreats. It mandates not just operational compliance, but encourages organizations to fortify their cybersecurity measures, aligning closely with existing ISO compliance frameworks for resilient and secure ICT systems. DORA provides a structured approach to protecting organizations against cyberthreats, emphasizing the importance of good cybersecurity metrics and their alignment with supply chain considerations.
The Exabeam Security Operations Platform integrates AI and automation into security operations workflows, offering a holistic solution to combat cyberthreats. Through AI-driven detections, Exabeam learns normal user and entity behavior patterns, pinpointing high-risk threats quickly. These threats are then prioritized with context-aware risk scoring for fast, accurate, and consistent threat detection, investigation, and response (TDIR). This approach encourages direct compliance with DORA and assists organizations in identifying significant changes in their security posture. With Exabeam, financial institutions can clear threat and case summaries, along with security reporting to meet voluntary disclosure requirements.
To discover how Exabeam can assist your organization in complying with DORA and elevating your cybersecurity measures, we invite you to contact us for a demo.
Unlock Advanced TDIR Strategies
Discover the critical insights and advanced strategies needed to enhance your TDIR capabilities. Read The Ultimate Guide to TDIR — a comprehensive resource with essential practices to understand and master the TDIR workflow. Leverage the latest in security information and event management (SIEM) technologies, optimize your log management, and achieve excellence in incident response.
Elevate your cybersecurity strategy and improve your security team’s efficiency and effectiveness. Download your guide now.

Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!















