MITRE ATT&CK Explainers:
Mitigating Security Threats with MITRE ATT&CK®
In a previous blog post I explained MITRE ATT&CK and the primary ways organizations might use it to improve their security.
As a refresher, the MITRE ATT&CK framework, model, and taxonomy provide a categorized and structured catalog of tactics (the “why” of an attack) and techniques (the “how” and sometimes the “what” of an attack). The relationship between tactics and techniques is organized and presented as the ATT&CK matrix. The philosophy of the ATT&CK model is that by focusing on and prioritizing your defense against documented cybersecurity threat behavior, you can understand, prevent, and mitigate these threats and attacks.
Drilling down into the details with each matrix reveals more details, ultimately leading to an ATT&CK page that includes examples of how known adversaries use a given technique. The ways an organization can use MITRE ATT&CK range from adversary emulation and red teaming to behavioral analytics development and SOC maturity assessment.
In this post, I look at how organizations can use the ATT&CK website as well as the PRE-ATT&CK matrix, which focuses on preventing attacks before adversaries have a chance to infiltrate your network.
Using the ATT&CK website
Let’s say we want to examine the tactic of Credential Access (TA0006). This tactic can be facilitated by many techniques, including Account Manipulation (T1098), Brute Force (T1110), Credentials in Registry (T1214), and at least 15 others (Figure 1).
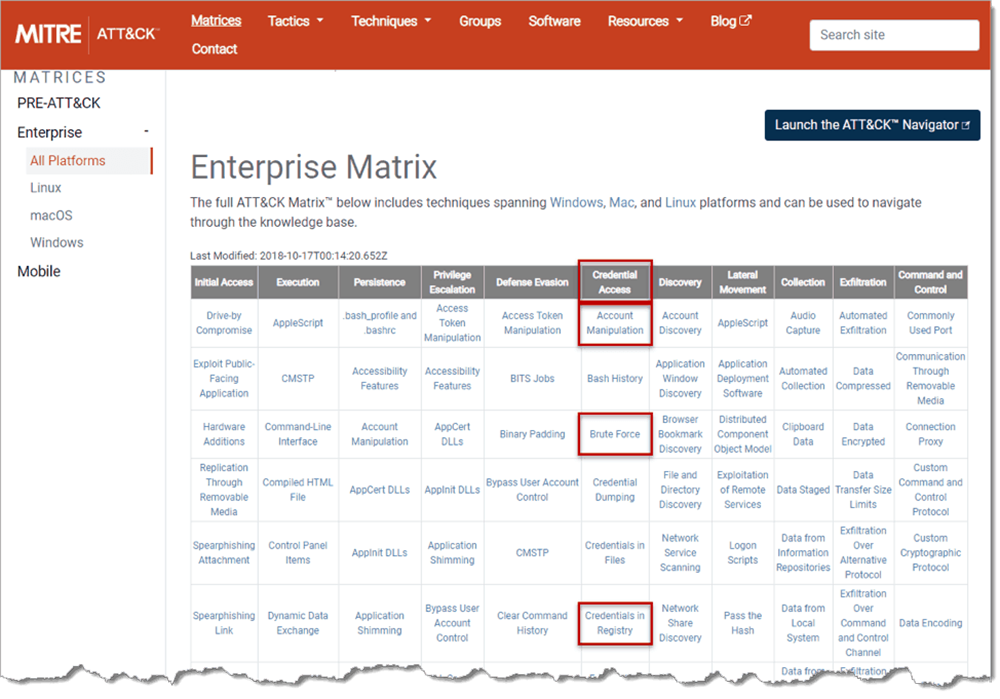
If we drill down into one technique, say, Brute Force, we can get an overview of the technique, see several examples of associated threat actors and/or software that have been used to carry out this technique, and also see mitigation and detection strategies. As of the publication date of this blog, ATT&CK reports that at least five threat actors and three software applications have been involved in perpetrating brute force attacks (Figure 2).
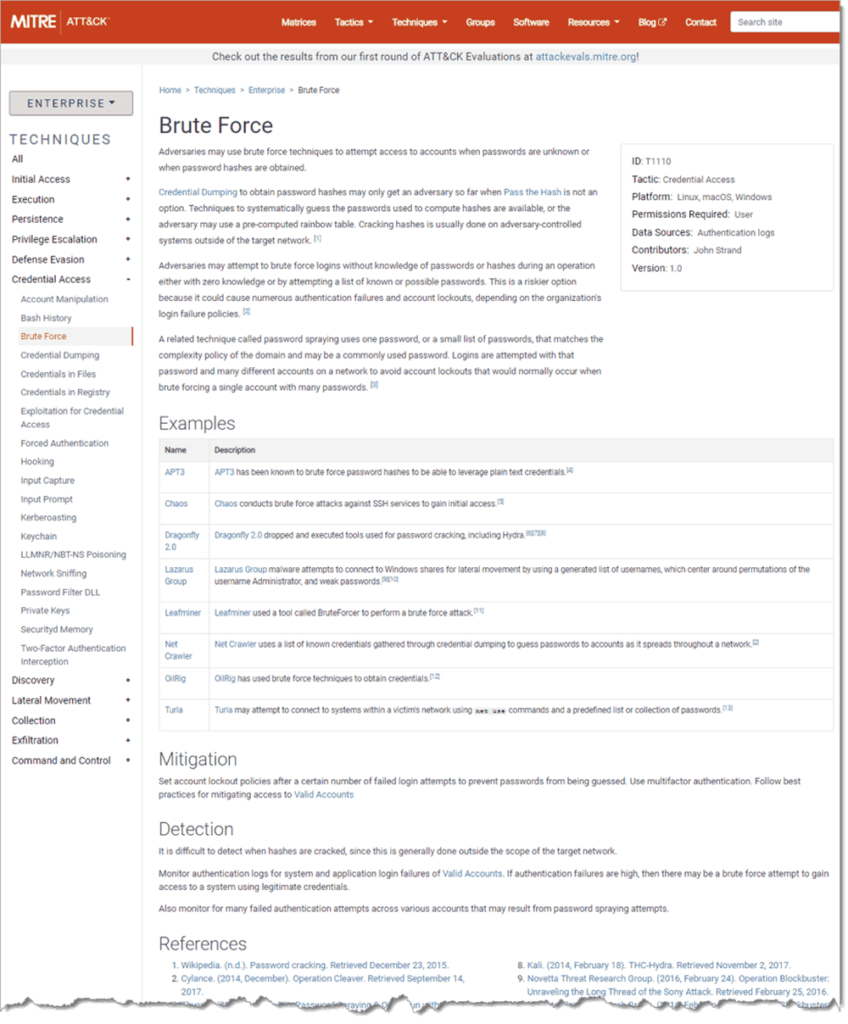
Note that the information that each ATT&CK page provides includes linked citations to sources, so that you can easily verify the validity of the data as well as discover more details.
According to the mitigation and detection information on this page, it turns out that brute force attacks are difficult to detect, but that one way to mitigate them is to employ multifactor authentication.
Using MITRE PRE-ATT&CK
If you’re interested in learning about the behaviors that happen before an attack (and you should be if you want to stay a step ahead of adversaries), you can study the PRE-ATT&CK matrix.
PRE-ATT&CK focuses on preventing attacks before adversaries have a chance to infiltrate your network. The PRE-ATT&CK matrix lets you answer questions such as:
- Are there signs that you are being targeted for an attack?
- What common techniques might be used against you?
- How should you prioritize your resources to get as much insight as possible before an attack is carried out?
You can use PRE-ATT&CK to help understand the various tactics that are commonly used to initiate an attack, and then discover the techniques that align with carrying out those tactics.
For example, one tactic is to Establish and Maintain Infrastructure (TA0022). By drilling down into that tactic, we can see multiple techniques associated with carrying it out. Among these is Domain registration hijacking (T1326).
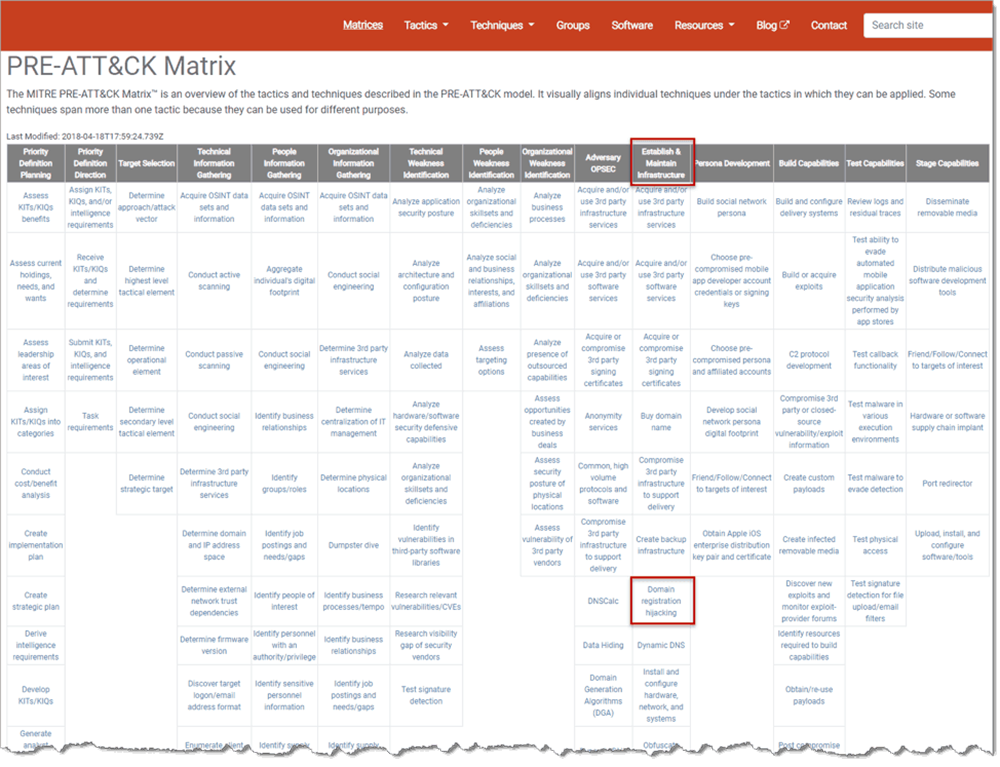
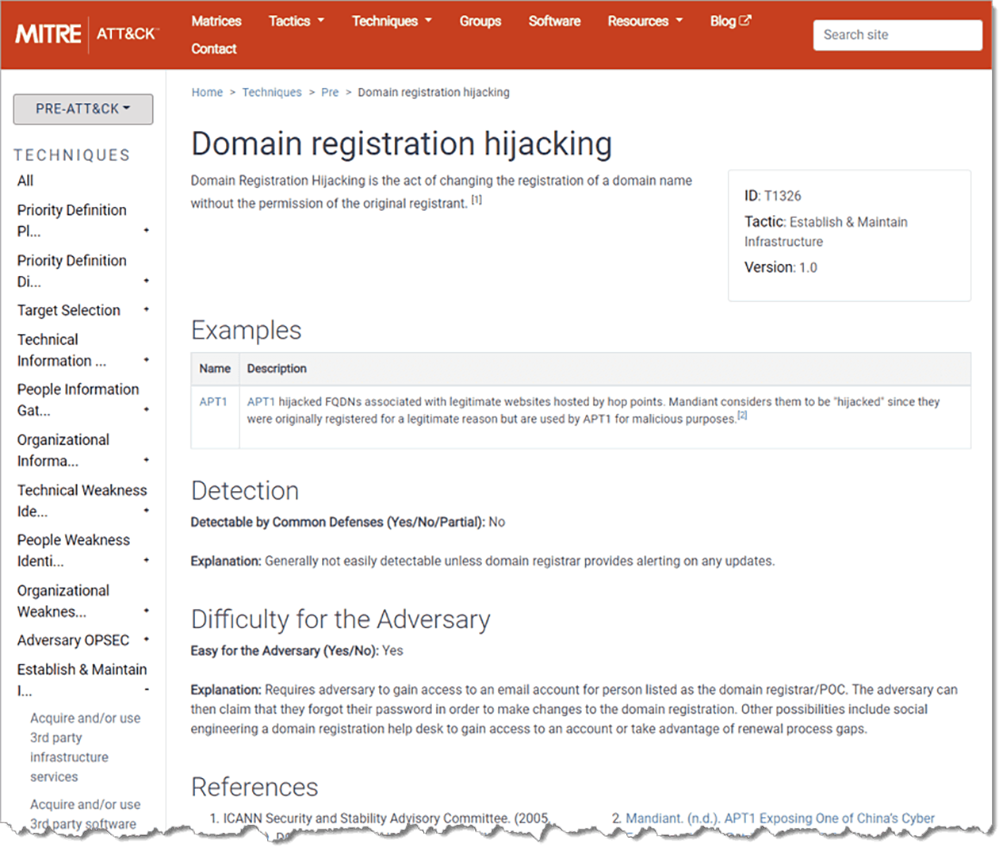
By reading the resulting ATT&CK page (Figure 4), we can see that this technique has been carried out by the threat group APT1, and that such a technique is difficult to detect but is easy for the adversary to carry out.
Using Exabeam Threat Hunter with the ATT&CK framework
You can use the ATT&CK or PRE-ATT&CK matrix along with Exabeam Threat Hunter to look for tell-tale tactics in your environment. Below are some sample queries you might use to examine suspicious initial access, privilege escalation, lateral movement, and exfiltration—a typical attack chain to steal customer details or intellectual property. These are not exhaustive, nor prescriptive lists, but a good place to start.
Tactic: Initial Access (TA0001)
Threat Hunter queries:
- First email domain for user
- Failed interactive logon by a service account
- Interactive logon using a service account
Tactic: Privilege Escalation (TA0004)
Threat Hunter queries:
- Account switch to a privileged or executive account
- Non-executive user logon to executive asset
- Abnormal addition to privileged group by user
Tactic: Lateral Movement (TA0008)
Threat Hunter queries:
- Possible pass the hash attack from the source
- First account management activity from asset
- First account management activity from asset for user
- First remote logon to asset
- Service account that has logged in to more than 30 assets
Tactic: Exfiltration (TA0010)
Threat Hunter queries:
- Possible data exfiltration: Abnormal amount of data had been uploaded to low ranked websites
- Possible data exfiltration: Abnormal amount of data had been uploaded to the web.
Stay tuned for more in the series. We’ll be covering some emerging techniques, as well as more detailed tutorials on how to use ATT&CK and PRE-ATT&CK with Exabeam products.
Want to learn more about Cybersecurity Threats?
- 21 Top Cybersecurity Threats and How Threat Intelligence Can Help
- Information Security Threats and Tools for Addressing Them
- Drive By Downloads: What They Are and How to Avoid Them
- Cyber Crime: Types, Examples, and What Your Business Can Do
- What is MITRE ATT&CK: An Explainer
- Defending Against Ransomware: Prevention, Protection, Removal
- Top 5 Social Engineering Techniques and How to Prevent Them
- Privilege Escalation Detection: The Key to Preventing Advanced Attacks
- SIEM Concepts: Security Incidents






