MITRE ATT&CK Explainers:
What is MITRE Engage (Formerly MITRE Shield)?
MITRE Engage is a knowledge base developed by the MITRE corporation, initially known as MITRE Shield. It provides active defense information based on ten years of adversary engagement experience. Engage provides information for a range of levels, including:
- Practitioner-friendly discussions of defense tactics, techniques, and procedures (TTP).
- CISO-ready considerations of objectives and opportunities.
The information is offered in both structured and unstructured forms, although the first release focuses only on structured elements. To help work with the data, MITRE provides mappings that organize views. It includes a mapping between Engage and the MITRE ATT&CK® framework. Additional views are added to the knowledge base as it continues to expand.
According to MITRE, Engage is a work in progress. It was released in order to stimulate conversations about adversary engagement and active defense, as well as ways in which defenders can employ active defense.
What is Active Defense?
According to the U.S. Department of Defense, active defense involves using limited offensive counterattacks and action for the purpose of preventing enemies from intruding into a contested area or position.
MITRE Engage combines several active defense types, including basic cyber defensive actions alongside adversary engagement and cyber deception operations. Together, these defenses enable organizations to counter attacks while also obtaining additional information about the adversary. This intelligence can help organizations better prepare for future attacks.
Related content: Read our blog Mitigating Security Threats with MITRE ATT&CK
How Can MITRE Engage Help Your Organization?
General cyber defense
MITRE Engage outlines foundational defensive techniques that can be applied to any defensive plan. Organizations can use MITRE Engage techniques within the corporate network to deter and detect adversaries. Ideally, organizations should conduct an assessment to understand the particular risks and threats the organization faces, and then apply the relevant Engage techniques.
Cyber deception
Deception security, also known as the tripwire approach, proactively searches for threats. Deception systems are designed to be indistinguishable from regular production systems and are capable of serving as high-fidelity systems. Organizations can apply deception for the purpose of detection, deterrence, or any other effect.
Adversary engagement
The majority of MITRE Engage techniques are designed to help defenders collect, observe, and understand adversary activities performed against the targeted system. Organizations can deploy MITRE Engage techniques in synthetic environments as well as in production, to promote effective and productive engagements.
Additionally, the MITRE Engage knowledge base can help analyze known information about a certain adversary (using ATT&CK insights), plan appropriate defenses, and capture the information needed to inform future considerations.
The MITRE Engage (MITRE Shield) Model, Tactics, Techniques, and Procedures
The MITRE Engage model includes several components, including:
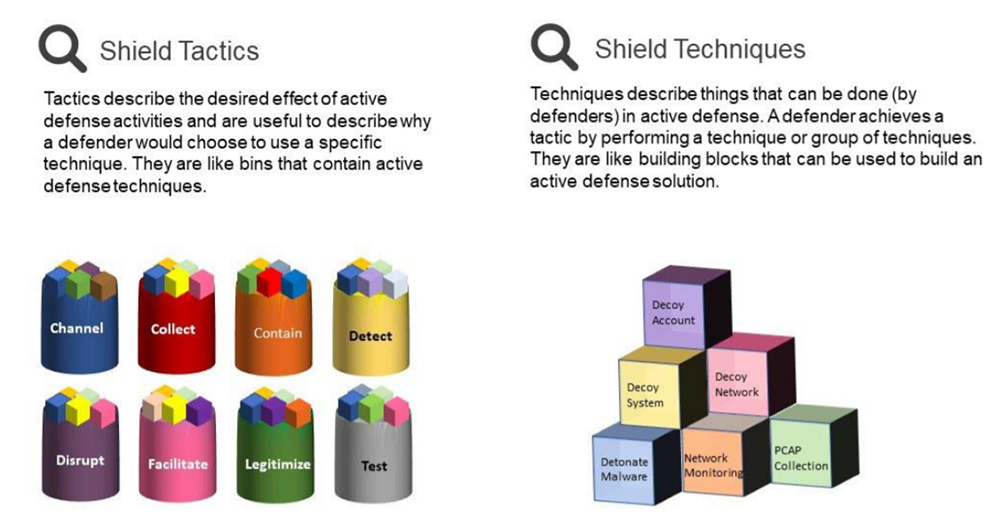
- Techniques — form the foundation of the Engage model and include active defense operations for defenders.
- Tactics — include abstract, high-level descriptions of the objectives defenders want to achieve by applying the operations. Tactics classify groups of techniques that can be referenced as needed and can serve as a shorthand for higher-level planning.
This model can help defenders use tactics to quickly identify the most relevant technique for each tactical objective. Defenders can use the model to build the most relevant defense solution out of the variety of Engage active defenses.
Related content: Read our explainer What are TTPs
The MITRE Engage matrix
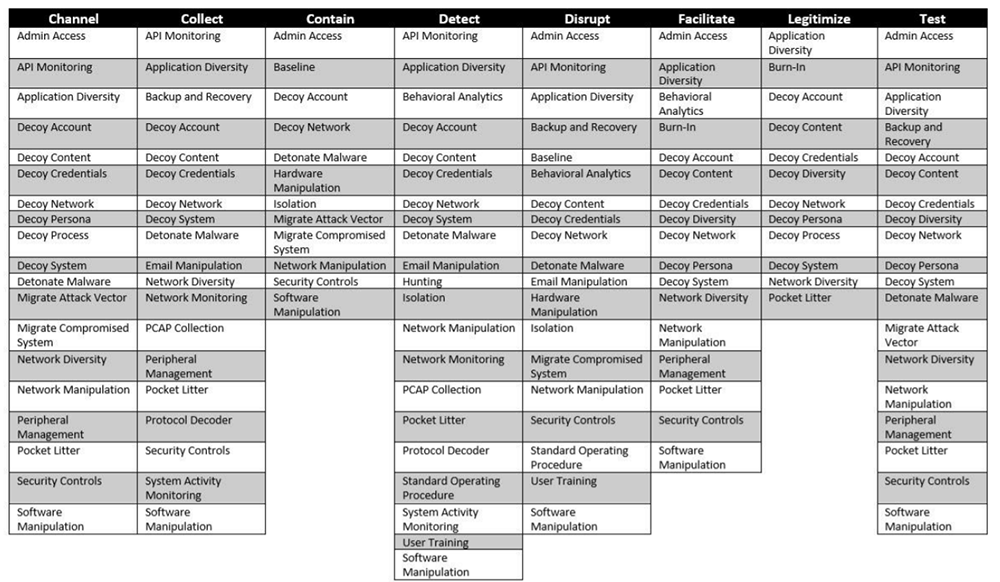
The MITRE Engage matrix (formerly the Shield Matrix) illustrates the relationship between techniques and tactics. It consists of:
- Tactics — the objective of defenders (illustrated in the columns below).
- Techniques — how each defense can help achieve one or multiple tactics (illustrated in the individual cells).
Techniques and procedures
MITRE Engage techniques outline active defense actions. A defender can achieve a predefined tactical objective by performing one or multiple actions. For example, a defender can add decoy credentials to an adversary engagement system. This action can help see whether an adversary dumps these credentials and then uses them to try to gain access to any other system located within the engagement network.
MITRE Engage techniques include a wide range of actions, including:
- Basic foundational techniques — applicable across a broad scope of organizations and can be layered on top of advanced techniques. Foundational techniques may include network monitoring, system activity monitoring, and backup and recovery.
- Advanced techniques — deployed for the purpose of manipulating software and networks. Advanced techniques are usually deployed by deception vendors or organizations attempting to engage or study adversaries on a deeper level.
MITRE Engage procedures describe in detail how to implement a technique.
Linking tactics and techniques
MITRE Engage associates active defense tactics with the relevant techniques. This is an important aspect of any active defense operation because techniques help build the systems and controls in an operational environment.
When linking tactics and techniques, a single technique can support multiple tactics. Similarly, a single tactic can use multiple techniques. For example, you can tighten security controls to disrupt an adversary activity or loosen certain controls in order to allow further engagement.
MITRE ATT&CK vs MITRE Engage
MITRE ATT&CK provides a continuously updated knowledge base that includes technical, tactical, sub-technical, and procedural aspects related to adversarial behavior. It was first created in 2013 and has undergone several major updates and improvements. The latest knowledge base offers matrices for enterprises, industrial control systems, and mobiles.
MITRE ATT&CK focuses on the perspective of adversaries, while MITRE Engage focuses on the perspective of defenders. Both knowledge bases use matrices but Engage considers defense techniques and tactics rather than adversarial behaviors. Engage offers eight defensive tactics that can help defenders accomplish their objectives.
The eight Engage tactic umbrellas include channel, contain, collect, detect, facilitate, test, disrupt, and legitimize. Each tactic umbrella includes 34 defense techniques which further refine and define all methods involved. The entire Engage matrix consists of all basic technologies required to achieve active defense, including general defense, adversary engagement, and deception.
Mapping MITRE Engage with ATT&CK
MITRE Engage defensive techniques and ATT&CK adversarial techniques are closely connected. This is why MITRE developed a page entirely devoted to ATT&CK techniques and tactics. Each ATT&CK tactic includes the associated adversary ATT&CK techniques as well as all applicable active defense information.
Engage provides concrete ways in which the ATT&CK knowledge base can be used. Mapping ATT&CK with Engage helps create active defense playbooks that address certain adversaries. Using the two knowledge bases together can help defenders achieve two main objectives:
- Gain a better understanding of adversary behavior and engagements (ATT&CK)
- Discover ways to achieve more active defenses (Engage)
How Exabeam Fusion Leverages MITRE
Exabeam security researchers participate in MITRE discussions and events. They have also contributed several new techniques that are pending publishing and researchers have performed extensive research on how to perform machine learning-based anomaly detection to effectively apply MITRE content into the security analyst’s detection arsenal.
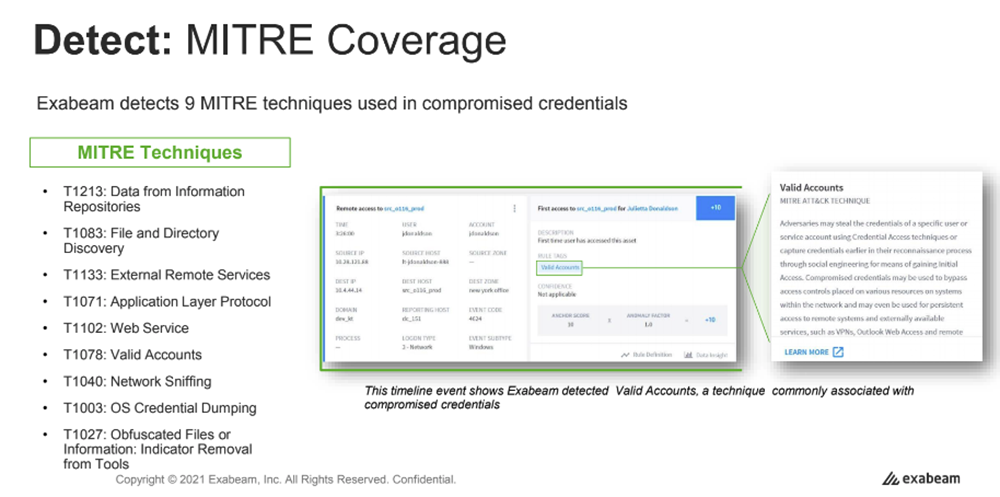
Exabeam Fusion SIEM and XDR include a set of pre-packaged use cases. These pre-packaged use cases include threat-specific content, pre-defined investigation checklists, and response playbooks tailored to each defined scenario. Exabeam in-house security experts mapped each use case scenario across the MITRE ATT&CK framework, including the specific MITRE tactics and techniques associated with every use case, providing more insight for the security analyst investigating potential threats in Exabeam. For example, the compromised credential use case maps to nine different MITRE techniques.
Exabeam Fusion consists of two products:
- Exabeam Fusion XDR: Market-leading behavioral analytics, alert triage, threat hunting, pre-built investigation playbooks, TDIR workflow automation, and integrations with hundreds of third-party security and productivity tools enable organizations to find complex threats that often go unnoticed across their diverse environment.
- Exabeam Fusion SIEM: All Fusion XDR features and capabilities plus centralized log storage, powerful search, and reporting to meet common regulation and compliance use cases.
No other SIEM or XDR provider delivers more out-of-the-box content in support of the framework. For a detailed mapping of Exabeam’s support of the MITRE ATT&CK Framework, please follow this link (Exabeam in shades of Green – minor to major): ATT&CK® Navigator






