A ransomware attack can be one of the most crippling cybersecurity threats for an organization. During an attack, cybercriminals will block access to your files or network, claiming that if you pay a ransom fee, your access will be restored. An effective ransomware defense strategy is essential to prevent extensive damage and must include three pillars: prevention, protection, and quick removal.
In this blog post you will learn about:
- What is a ransomware attack
- How ransomware attacks work
- Who is a target for ransomware
- Types of ransomware
- A 4-step plan for ransomware prevention
- A framework for ransomware protection
- Ransomware removal – 4 quick steps to mitigate an attack
- Bonus: A security analyst’s ransomware cheat sheet
What is a Ransomware Attack?
Ransomware is a form of malware that prevents users from accessing their files. Victims can regain access by paying a ransom to the cybercriminals behind the attack. Payment is often demanded in cryptocurrency so that the identity of the cybercriminal remains unknown. The costs can range from a few hundred to thousands of dollars.
How Ransomware Works: The Kill Chain
A ransomware attack doesn’t begin with the encryption of files. Long before, an attacker plans a ransomware campaign against a specific target or group of targets. They use a number of methods (see below) to infect an organization’s systems.
Then after having penetrated, they stage an attack, scan local files to decide which data is valuable enough to hit, encrypt the data, and await payment.

Figure 1: Ransomware Attack Chain
Methods of Infection
Ransomware can hit a consumer or an organization in several ways, including malicious email attachments and fake links to social media scams:
- Social engineering—Cybercriminals use psychological manipulations to trick people into downloading malware. A common technique is phishing—sending emails that appear to be from a trusted institution or a friend; however, they contain links to malicious websites or direct downloads.
- Malvertising—Attackers can buy ad space on popular social media and online advertising websites and load them with ads infected by viruses, spyware, and malware. By clicking on these ads, users are directed to malicious servers.
- Exploit kits—Tools that help attackers automatically search for numerous exploits and vulnerabilities on a website or network, and attack via the exploits it finds. Exploit kits lower the barrier of entry for attackers, allowing them to effectively penetrate organizations and inject malware without much technical knowledge.
- Drive-by downloads—Some malicious websites take advantage of out of date browsers or apps to download malware to a user’s computer without their knowledge.
Who is a Target for Ransomware?
When it comes to ransomware, anyone can be a target, including home users, small to large businesses, public or government agencies, and even politicians or celebrities. This is why ransomware prevention is essential. This is how some of the top targets are vulnerable:
Academic Organizations: Colleges and Universities
These organizations are a prime target for cyber and ransomware attacks. They have smaller IT teams, budget constraints, a high rate of network file sharing, and sensitive data like the intellectual property, research, and financial data of faculty, staff, and students.
Government Agencies
These organizations retain important and personal data, which makes them a potential target for a ransomware attack. Cybercriminals know these organizations need to respond quickly, and that they’re more likely to pay the ransom, rather than wait and conduct a proper counter attack.
Healthcare: Hospitals
The critical nature of hospital infrastructure makes it a popular target for ransomware attacks. Cybercriminals know that if hospital data is inaccessible, it can be a matter of life or death, and their hope is that hospitals will prefer to pay immediately rather than wait for a proper solution.
HR Departments
HR has access to personnel records and financial systems, making it a potential target for attacks. Hackers often pretend to be job applicants; HR professionals open the job application email and the attachments and unknowingly spread ransomware.
Mobile Devices
Mobile devices contain personal data, which makes them a potential target for attackers looking to extract personal photos or video for their personal benefit. Since data can easily be restored by syncing devices, cybercriminals often prefer blocking smartphones instead of just encrypting files.
Small and Medium-Sized Businesses
The ability of malware to lock up data makes SMBs one of the most popular targets for ransomware attacks. Within minutes, a business can lose critical file such as financial data, customer records, inventory data, and order information.
Ransomware Types
There are four main categories of ransomware, ranging in severity from mildly disruptive to highly dangerous:
1. Scareware
Fake security software, which claims to have found issues on your PC and demands money to fix them. Some types flood your screen with pop up alerts, while others lock your computer. If you do nothing, the interruptions will continue, but your files are probably safe.
2. Encrypting Ransomware
Locks access to your files by encrypting them, and then progressively deletes them. Hackers know your files are important to you, and that you are likely to pay quickly rather than waste time and lose critical data.
3. Screen-locking Ransomware
Screen-locking ransomware locks you out of your computer and displays a warning. In many cases, the software claims the machine has been locked by the FBI, the police, or some other authority, and that illegal activity has been detected on your computer and you must pay a penalty.
4. Doxware
This type of ransomware threatens to publish stolen sensitive files or photos online unless the ransom is paid. You may find it hard to avoid paying the ransom because of the threatened release.
How to Stop Ransomware: A 4-Step Ransomware Response Plan
To stop ransomware, you should take three important steps:
- Protect your network using measures like access control, application whitelisting and behavioral analytics technology
- Protect endpointsusing endpoint protection platforms and email protection tools that help prevent social engineering
- Update software and operating systems and ensure all important data is backed up
- Educate employees and ensure they stay informed about social engineering, malware and ransomware
Learn more about how to stop ransomware in the subsections below, which explain each step in depth.
Step 1: Protect Your Network from Ransomware
The first step to ransomware protection takes a look at your entire network and implements key preventive measures, which should help you gain visibility and control, including:
- Network access control—Organizations should have measures to secure their network perimeter and ensure attackers do not gain access to internal systems. This is becoming more complex as attackers become more sophisticated and insider threats become a greater concern.
- Application whitelisting—Using tools or processes that enable only known application signatures to run on the network, preventing infection by malicious or unauthorized applications.
- Advanced security analytics—the above solutions are effective, but cannot prevent all attacks. User and entity behavior analytics (UEBA) solutions help identify and stop attacks missed by other security tools. For example, Exabeam Advanced Analytics is a UEBA platform that establishes behavioral baselines of users and IT systems, and detects abnormal behavior that might signal ransomware or other damaging attacks.
Step 2: Ransomware Endpoint Protection
Endpoints play a key role in ransomware infections. The second step takes care of prevention of ransomware in endpoints, and should cover the following aspects:
- Endpoint protection—antivirus solutions on your endpoints are no longer sufficient. Organizations are adopting complete endpoint protection platforms which provide access control, a device firewall, intrusion prevention, internet content filtering, and more.
- Email protection—most ransomware infections occur via a malicious download or from an email attachment. Organizations should block email messages with attachments from unknown or blacklisted sources.
Step 3: Create Backups and Update your Systems
To ensure your data is not taken hostage, you should implement a backup and recovery strategy. This third step should leverage the following techniques:
- Conduct regular data backup checks—Organizations should use recovery plans for all critical data, and hold regular drills to ensure that data is safe and can be restored within the organization’s recovery time objective (RTO).
- Application and operating system updates must be up to date—There should be a process to ensure security updates and patches are promptly installed to avoid any potential vulnerabilities. Efficient patch management reduces the chances of attacks via known vulnerabilities.
Once you set up these measures, you should be able to use backup data and retain business continuity while you initiate ransomware removal processes.
Step 4: Educate and Stay Informed
Help your personnel and any integrated collaborator understand the risks and signs of ransomware. This fourth step is critical to ensure everyone helps protect the organization. It includes the following measures:
- Create user awareness—Employees are often the weakest link in the cybersecurity process. It is important to educate and invest in cybersecurity training, so individuals do not succumb to phishing or other social engineering attempts.
- Real-time threat intelligence—It’s important to know your enemy. Take advantage of threat intelligence feeds to understand attack patterns, threat actors, and the evolution of malware systems used for ransomware or similar attacks.
A Framework for Ongoing Ransomware Protection
A typical ransomware attack can be divided into four stages: pre-execution, pre-damage, damage, post-damage.
Pre-Execution
Goal 1: Keep ransomware away from system endpoints by preventing delivery.
Examples of solutions that can help:
- Gateway defenses: firewalls, email, and spam filtering
- User anti-phishing tests and awareness training programs
- Exploit prevention: patch management, ad blockers
Some attacks may penetrate these defenses, especially due to human error.
Goal 2: Block ransomware payloads from executing.
Examples of solutions that can help:
- File scanning and filtering, including antivirus
- Program isolation solutions, including sandboxing tools
- Application whitelisting
Pre-Damage
Goal: Stop executed ransomware from doing harm.
Examples of solutions that can help:
- Runtime protection that identifies malicious behavior and stops it automatically before any damage is done.
Stopping attacks at runtime is your last opportunity at ransomware prevention. The next two groups of solutions help you react to effective infections by quickly identifying and recovering from them.
Damage
Goal: Isolate ransomware infections to prevent them from spreading.
Examples of solutions that can help:
- Security Information and Event Management (SIEM) systems can identify security alerts or network events signaling a ransomware attack and help security teams contain it.
- UEBA and incident response tools can identify ransomware attacks even if the attack or malware signature is unknown. Next-generation SIEMs come with UEBA built in.
- Setting up monitoring on file servers to notify of infections
- Restricting admin and usage rights to sensitive files
Post-Damage
Goal: Recover quickly without paying the ransom.
Examples of solutions that can help:
- Backup, as part of a robust disaster recovery plan
- Decryptor tools
- Malware removal tools
Ransomware Removal: What to Do if You’re Infected
If you’re under attack, the following four steps will help you contain the attack and recover as much data as possible.
- Isolate—Disconnect infected machines from the network and lock down shared network drives. Since ransomware encrypts files quickly, in many instances the infected devices will already have been damaged.
- Investigate—You must know what type of ransomware you’ve been infected with. Some types of ransomware don’t encrypt data effectively. Other types have been cracked and decryption tools are on the market. Also, other types may not actually deliver a working decryption key even if you chose to pay the ransom.
- Recover—In most cases, once files are encrypted you cannot unlock them without the decryption key. However, malware researchers sometimes find flaws in ransomware encryption and create decryption tools. Try to find a decryption tool for the malware you found in your systems. If no decryption tool is available, restore files from backup. If no backup is available, unfortunately the only option is to pay the ransom (which is not recommended by the authorities).
- Reinforce—Once the crisis has passed, it’s important to evaluate what happened and the lessons learned. How was ransomware successfully executed? Which vulnerabilities made penetration possible? Why did antivirus or email filtering fail? How far did the infection spread? Was it possible to wipe and reinstall infected machines, and were you able to successfully restore from backup? Address the weak points in your security posture to be better prepared for the next attack.
Balancing Ransomware Prevention, Protection, and Containment
Ransomware is a complex problem. In this blog we offered three ways of dealing with the problem:
- Ransomware prevention through robust cybersecurity measures, a backup and disaster recovery plan, and user training
- Protecting against ransomware at every stage of the damage chain
- Containing and recovering when an attack occurs
In real life, you will need to balance all three measures. A ransomware prevention plan is essential, but it’s no replacement for specific protection measures to prevent malware from infecting and spreading on your network. In addition, you must be prepared with an action plan to contain and recover if and when attacks occur. Only a three-layered program covering ransomware prevention, protection, and containment can keep organizations safe from this devastating threat.
A Security Analyst’s Ransomware Cheat Sheet
Below is a cheat sheet that can help security analysts with ransomware prevention by allowing them to identify, analyze, and mitigate ransomware attacks.
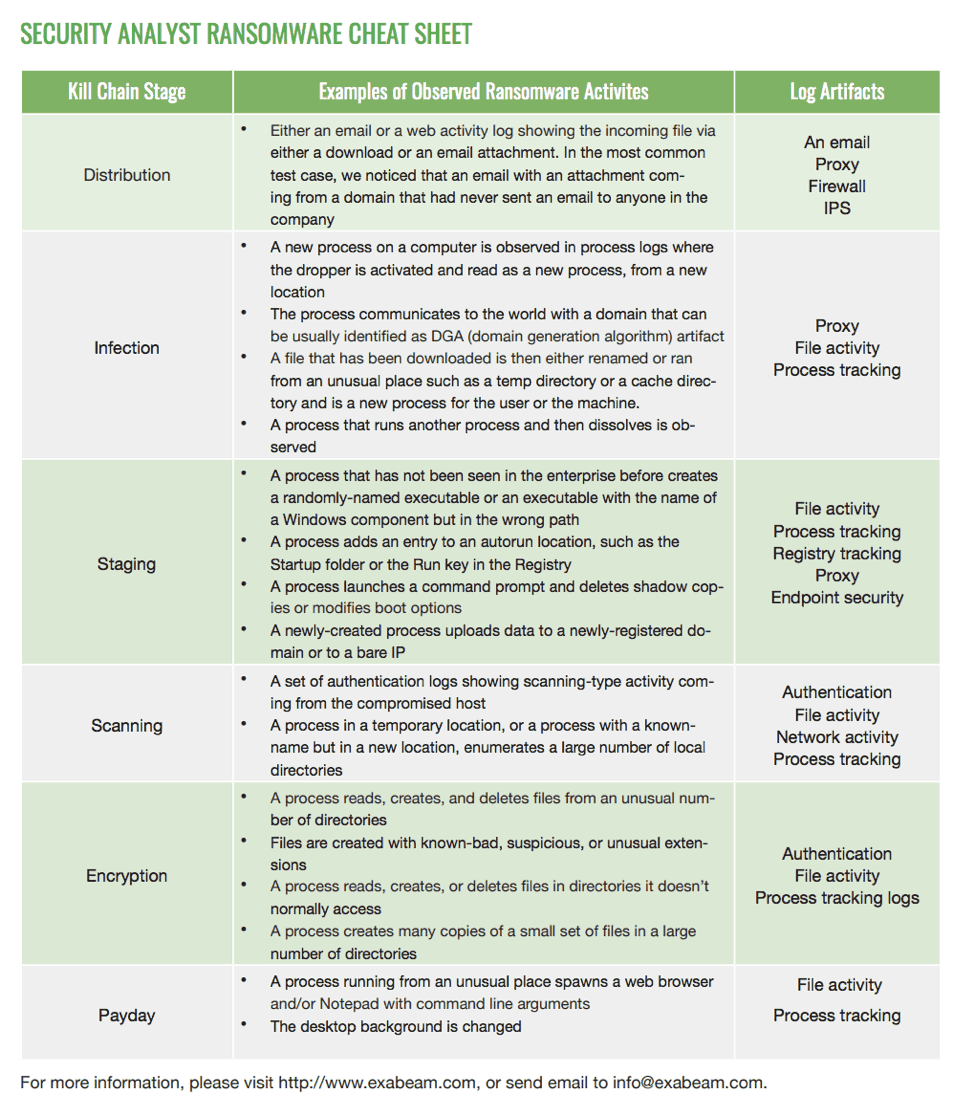
Click to download
Want to learn more about Cybersecurity Threats?
Have a look at these articles:
- 21 Top Cybersecurity Threats and How Threat Intelligence Can Help
- Information Security Threats and Tools for Addressing Them
- Drive By Downloads: What They Are and How to Avoid Them
- Cyber Crime: Types, Examples, and What Your Business Can Do
- What is MITRE ATT&CK: An Explainer
- Mitigating Security Threats with MITRE ATT&CK
- Top 5 Social Engineering Techniques and How to Prevent Them
- Privilege Escalation Detection: The Key to Preventing Advanced Attacks
- SIEM Concepts: Security Incidents
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












