Lateral movement refers to techniques cyber attackers use to progressively move through a network, searching for targeted key data and assets. Lateral movement takes place following the initial breach of an endpoint. This attack methodology requires the additional compromise of user account credentials. Using these account credentials, the attacker attempts to access other nodes by moving laterally through the network.
Lateral movement techniques are widely used in sophisticated cyber-attacks such as advanced persistent threats (APTs). The adversary uses these techniques to access other hosts from a compromised system and get access to sensitive resources, such as mailboxes, shared folders, or credentials. These can be used in turn to compromise additional systems, for privilege escalation, or to steal more valuable credentials. This type of attack may ultimately give access to the domain controller and provide full control of a Windows-based infrastructure or business-related operator accounts.
In this article:
- What is lateral movement?
- How does lateral movement work?
- How to detect lateral movement
- Best practices to prevent lateral movement
How does lateral movement work?
As the attackers gather information about the environment, they make parallel attempts to steal additional credentials, exploit misconfigurations, or isolate software vulnerabilities so they can dig deeper into the network.
The attacker then uses lateral movement to control key points in the infected network. These additional positions help the attacker maintain persistence even if a security team detects them on a compromised machine.
Lateral movement can be divided into these five steps:
1. External reconnaissance — the first step for an attacker is to perform reconnaissance on the target organization. Reconnaissance activity includes external network scan, social media and password dumps. The goal is to understand the target’s network and most likely successful attack vector. For example, if credential dumps are available for employees of the target organization, the attacker may attempt to authenticate access to the organization’s VPN or external email. Another method is using open source tools such as Shodan to identify the target’s open ports and vulnerabilities without performing a scan.
2. Initial infiltration — once an attacker identifies the attack vector, they exploit the vulnerability to gain access to the target’s network. Attackers vectors can range from a vulnerable device or application that is accessible via the public internet. This is a vertical move, from outside to inside. Once it is done, they can then move laterally within the network to reach their objective.
3. Internal reconnaissance — attackers gather information, such as operating systems, network hierarchy, and resources used in the servers to map the environment and understand where vulnerabilities exist. Operating system utilities attackers can use to carry out internal reconnaissance include Netstat, IPConfig/IFConfig, ARP cache, local routing table, and PowerShell. In addition, unsecured intranet pages can provide attackers with internal documentation on the infrastructure and location of the target data.
4. Stealing credentials — once inside the network, attackers look for new devices to broaden their control. To move from system to system they may attempt to gather valid user credentials by using keyloggers, network sniffer, brute forcing passwords or phishing to fool users into providing credentials. However, it is not uncommon for attackers to find credentials on intranet pages, scripts, or other easily accessible files/systems. The attacker can use these credentials to escalate their privileges and expand their access. The attacker’s ultimate goal is to escalate their privileges to domain administrators for complete access and control of the domain. With domain administrator privileges, attackers can target a domain controller and dump the NTDS.dit from the system’s volume shadow copy. This gives the attacker access to the password hash for all domain users, including service accounts. Obtaining the password hash for the KRBTGT can allow attackers to create a golden ticket with unfettered access.
5. Compromise more systems — now that attackers have the credentials to access their target systems, they will use remote control tools such as psexec, PowerShell, remote desktop protocol, or remote access software to access those systems. IT staff often access desktops this way, so remote access is generally not linked to a persistent attack. However, attackers will create a persistent connection to the network to keep multiple avenues of access open. Lastly, the attacker will exfiltrate the data to a command and control server using techniques such as data compression, data encryption, and scheduled transfers to remain undetected.
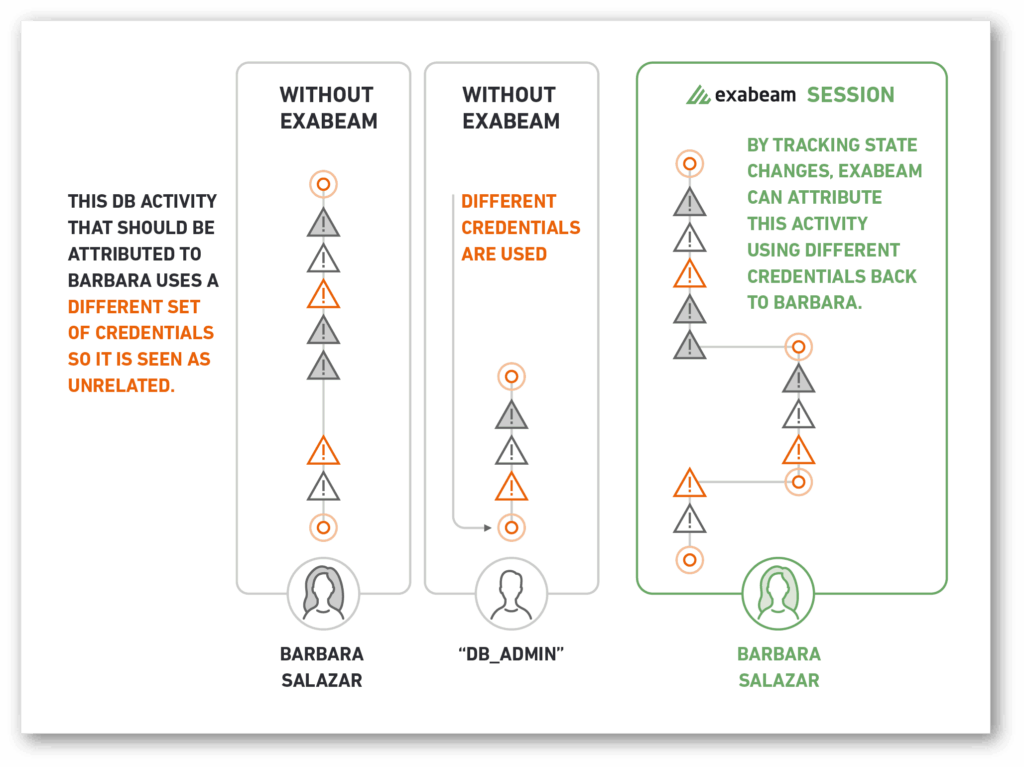
How to detect lateral movement
Detecting lateral movement in a network can be challenging, as attackers often use legitimate tools, verified credentials, and abuse normal processes to blend in with normal traffic. However, there are various strategies and tools that can be employed to identify suspicious activities indicative of lateral movement. Here are some approaches:
- Monitor user behavior: Analyze user behavior for anomalies, such as unusual login times, locations, or access patterns. Tools like User and Entity Behavior Analytics (UEBA) can help detect deviations from normal behavior.
- Network segmentation: Divide the network into smaller segments with limited access between them. This not only restricts an attacker’s movement within the network but also makes it easier to detect unusual traffic patterns.
- Regularly review privileged accounts: Monitor accounts with elevated privileges and ensure that access is limited to those who genuinely need it. Regularly review these accounts for unusual activities.
- Regularly review service account activity: Monitor service accounts. Any deviation accessing new systems or attempts to swap logins should result in immediate review and action.
- Deploy intrusion detection systems (IDS) and intrusion prevention systems (IPS): These technologies can help identify and block suspicious activities within the network by monitoring traffic and looking for known attack patterns.
- Monitor network traffic: Analyze network traffic for unusual patterns, such as spikes in data transfers, connections to unusual ports, or connections to known malicious IP addresses.
- Monitor endpoint activities: Implement endpoint detection and response (EDR) tools to track activities on endpoints (like servers, workstations, and mobile devices) and detect unusual process executions or file modifications.
- Inspect log files: Regularly review log files from various sources, such as firewalls, servers, and applications, to identify suspicious activities. Seeing large file movement from unexpected sources or to unknown destinations should always flag as an event.
- Implement strong authentication: Use multi-factor authentication (MFA) to reduce the likelihood of compromised credentials being used for lateral movement.
- Regularly patch and update: Keep software, operating systems, and firmware up-to-date with the latest security patches to minimize vulnerabilities that can be exploited for lateral movement.
- Security training and awareness: Educate employees about security best practices and how to spot potential threats, such as phishing emails, which can lead to an attacker gaining initial access to the network.
Remember that no single approach is foolproof. It’s crucial to adopt a multi-layered security strategy that combines various techniques to detect and prevent lateral movement effectively.
Best practices to prevent lateral movement
There are several practices you can use to prevent and protect lateral movement inside your network:
1. Least privilege — each user must be properly categorized and have access only to the systems, applications or network segmentations their job requires them to access. For example, in a corporate network, only IT staff should manage devices such as desktops and notebooks. IT staff should not provide users with administrator privileges.
2. Allowlisting — any application requested by a user should be evaluated carefully. It’s worth following a list of reputable applications and restricting those with known vulnerabilities. If there is a request to an application whose functions are already fulfilled by another, there may be no need to enable the service. For example, NotPetya infected a large shipping company via a third-party application update.
3. EDR security — endpoint detection and response (EDR) solutions monitor online and offline endpoints, collecting and storing data on historical endpoint events and mapping that data against actionable security intelligence feeds and known tactics, techniques, and procedures (TTPs). The data collected by an EDR solution provides visibility that helps identify patterns and behaviors that attackers leave behind as they attempt to gain a stronghold inside an environment. IT personnel can stop active attacks while they repair the damage quickly, isolate infected systems to prevent lateral movement, and remove malicious files left by the attackers.
4. Password management — enforcing password management is an important practice to protect your user accounts and also helps you cope with possible attempts of lateral movement. Organizations should enforce a policy of strong and unique passwords across all privileged systems and accounts. Most importantly, administrators need to practice good account management hygiene. For example, Microsoft recommends, “Be sure that you change the password [KRBTGT] on a regular schedule.” This is recommended at least quarterly, including for administrative or service accounts.
5. Multi-factor authentication — multi-factor authentication adds an additional layer of security to the standard username and password authentication. This is done by implementing multi-factor authentication for access to internal systems, applications and data. This increases the level of effort attackers need to make to compromise an account protected by multi-factor authentication.
Wrap up
Lateral movement plays a significant role in cyberattacks and is used by APT groups. This is the stage where attackers actively explore an organization’s network to find its vulnerable elements. Following practices such as applying least privilege, whitelisting, implementing an EDR solution, and requiring multi-factor authentication and strong passwords will make it more difficult for intruders to move around, even when they are already inside.
Lateral movement is also the stage where the attacker’s activity is most exposed. Taking advantage of this exposure to detect lateral movement is possible with EDR solutions that offer visibility over an organization’s network. A security operations team will be able to recognize any abnormal behavior and detect lateral movement before achieving their objective, data exfiltration. To learn more about how Exabeam can help detect lateral movement within your organization, find out more here.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












