Protecting your business from security threats on an ongoing basis is essential. But many organizations continue to use outdated threat-hunting procedures that puts them at greater risk. Andy Skrei, Exabeam’s vice president of worldwide sales engineering, recently spoke on Exabeam’s threat-hunting activities at Spotlight19 and how to modernize your security practices to make sure they’re built to tackle today’s dangers.
In his talk, “Using Exabeam to Put Joy Back into Threat Hunting” Andy explained how Exabeam is making threat hunting easier for businesses across all industries. His experience includes serving as the lead information security engineer for eBay, where he helped the company weather a major data breach. He also served as an information protection manager at KPMG, where he advised some of the world’s largest organizations. In this post he describes how today’s threat-hunting techniques are making detection and prevention significantly easier for the businesses embracing them.
The gap in traditional threat hunting
In the past, security experts relied on indicators of compromise (IoCs) to identify threats. Unfortunately, these “indicators” required an activity to take place before security practitioners would know it was even happening. Having to react to incidents rather than be proactive meant that damage was already done before the threat could be stopped.
“If I’m chasing file hashes, and file names, every single day I’m behind the attacker because he’s just going to keep changing IoCs,” Andy says. “It’s very easy to change IoCs. It’s much harder for the attacker to change their TTPs, or behavior. They’re going to be doing the same things over and over, but they can quickly and easily change their IoCs, and this is where we’re spending a lot of our time and effort, is chasing IoCs.”
Andy points to the Threat Hunting Pyramid of Pain, which demonstrates that technology professionals tend to focus on hash values and IP addresses, the two easiest threat types to chase. However, as you move up the pyramid to features like host artifacts, tools, and TTPs, threat hunting gets more challenging.
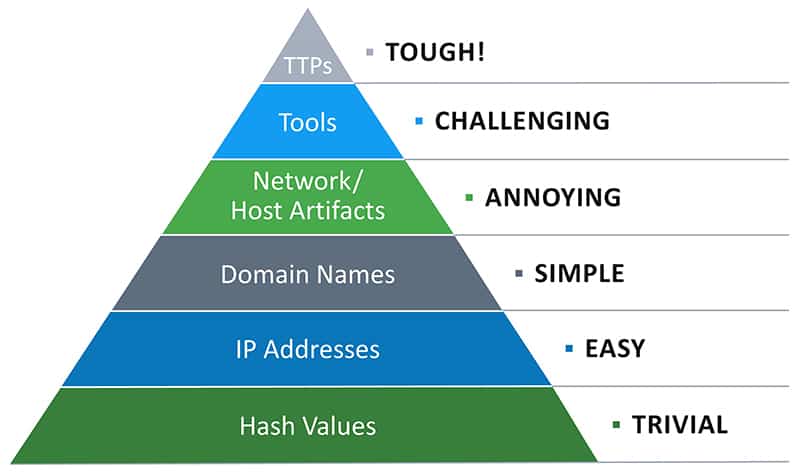
The Pyramid of Pain shows where many security practitioners focus on (hash values and IP addresses) and the importance and difficulty of detecting TTPs when using traditional threat hunting tactics. Image concept: David J. Blanco
TTPs and threat hunting
The key to steering toward a proactive security posture, rather than being reactive, is to look at tactics, techniques, or procedures, also known as TTPs. Instead of waiting for an incident to happen and setting off alerts, TTP monitoring looks for certain behaviors that are telltale signs of an impending attack.
But TTPs aren’t without their weaknesses. One problem security professionals run into is that they routinely alert on things that are regular occurrences within the organization.
“I guarantee almost everyone in the field has an admin in your organization who put their credentials in a script, and they look like brute-forcing after they change their password,” Andy asks. “If you just focus on the behavior, you’re still going to be drowning. You’re still going to be underwater. And this is why we need to pair the TTPs with analytics.”
Pairing TTPs with data analytics
By introducing analytics to the equation, security professionals can filter out those everyday activities. Instead of monitoring for specific risks, analytics watches for changes in patterns. If a new account was created by a user who has never done that before, you’ll be alerted, rather than hearing about every single instance of a new account creation. This can help prevent alert fatigue that comes from too many false positives.
“Data models are key in Exabeam,” Andy says. “This is how we learn what is normal, and we build data models off of different scope types. We build data models for your users. What is the normal behavior of this user? What is normal for this peer group? And sometimes for the organization, what have I seen across the org? Exabeam allows organizations to search any created data model using our Data Insights page.”
Finding unknown anomalies with Exabeam
Andy has found that one of the best things about the Exabeam platform is its ability to pivot. This agility means it’s responding to the risks most facing your organization today, rather than what you were dealing with several days ago. The platform gathers only the most important information so that you can go through it to determine what is, indeed, an actual threat.
“I don’t care about that anomaly that fires 10,000 times every week,” Andy says. “I care about that anomaly I’ve never seen in any organization since Exabeam’s installed. Things like, ‘I have a user with an abnormal number of accesses to the host across the organization.’ This is what you’re going to see when you have lateral movement.”
Exabeam dashboards give analysts visibility into the risk vectors the technology has uncovered making the platform even more useful for staff in the frontlines. When working with a new business, Exabeam starts as broad as possible, then narrows the approach as it gets to know the environment better. This ensures that the platform and businesses learn which events are true anomalies.
Andy says one of the most important things a new Exabeam customer can do is to use the platform regularly. To aid Exabeam’s machine-learning capabilities and to familiarize yourself with what’s going on with your network you need to be in there every day. Even activities that aren’t immediate security threats could go against company policy. Andy has found that when a business is aware of the activities happening across its network, it’s better prepared to protect itself against security breaches.
“You don’t have to exactly know what you’re looking for,” Andy says. “Start broad, start with the event types, start with risk scores. But I guarantee you’re going to find things in this system that may not be a security threat, but they’re probably configuration problems, or users doing things against policy.”
By combining analytics with diligence, businesses can keep their end users, as well as their customers, safe from dangerous breaches. Exabeam’s solutions take you from having to react to incidents to becoming a proactive threat hunter, which positions you well ahead of adversaries when it comes to protecting your organization’s assets. You can hear Andy’s complete presentation with a live demo about Exabeam’s innovative security solutions.
Want to learn more about what Exabeam can do?
Have a look at these articles:
- Advanced Analytics Use Case: Detecting Compromised Credentials
- An Incident Investigator’s Cheat Code
- Recreating an Incident Timeline–a Manual vs. Automated Process, Part 1
- Recreating an Incident Timeline–a Manual vs. Automated Process, Part 2
- IT Security: What You Should Know
- Detecting Lateral Movement and Credential Switching: Human vs. Machine
- Penetration Testing: Process and Tools
Exabeam Security Research Team (ESRT) Mission Statement:
The ESRT strives to provide unique insight into how we look at the world of cyberthreats and risk by highlighting the common patterns that different threats and threat actors use, and why we need to reorient our detections and priorities to tactics, techniques, and procedures (TTPs) vs. indicators of compromise (IOCs).
We aim to share a newer ideology of investigating threats by answering the following questions: “who, what, and how”.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













