Before we dive into how modern SIEMs combat threats, here’s a quick primer on threat hunting, which involves proactively and continuously searching for patterns that lead to discovering a threat that may evade your existing security tools. According to a 2017 SANS Institute study, 45 percent of organizations only conduct such threat hunting on a limited, ad hoc basis. To obtain better efficiency and security while also reducing stress for the SOC team, modern SIEMs provide automated, point-and-click search systems to assemble evidence. The result: usable and actionable insights, run around the clock
However, many analysts use techniques such as running a series of manual, query-based searches through their SIEM to find adversaries. Let’s look at how this process of query-based threat hunting works.
How do analysts use a legacy SIEM to hunt for threats?
Legacy SIEMs provide log management and correlation capabilities that can help analysts search and correlate between data sources. But first, the team needs to determine which data they need to evaluate for threat patterns. Sources include network data from firewalls, DNS, web traffic, proxies, netflow, and endpoint data. Investigators also need to take into account threat intelligence and identity sources such as Active Directory, LDAP, or HRM systems. All selected logs need to be ingested and indexed so analysts can then search for known Indicators of Compromise (IoCs).
Let’s run through an example:
- Usually, analysts will have saved a set of queries that detect potential indicators of compromise in their environment. They typically begin with known IoCs, such as blacklisted IPs or malicious hostnames, as they look for anomalies.
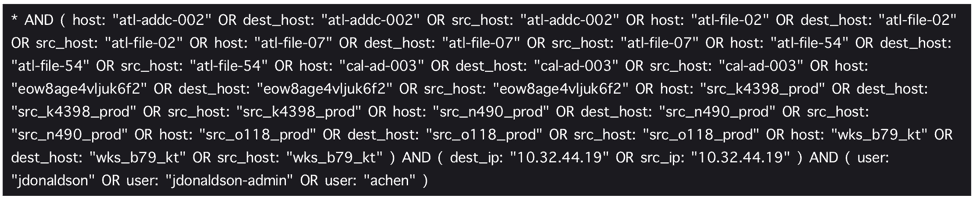
Figure 1: Legacy SIEM query that searches for known IPs, users, and hostnames
2. They then include parameters from the results in subsequent, expanded searches to reveal unusual activities. Figure 2 reveals some processes they haven’t seen before that are running on an endpoint. This may require further investigation to determine if they’re normal executables.
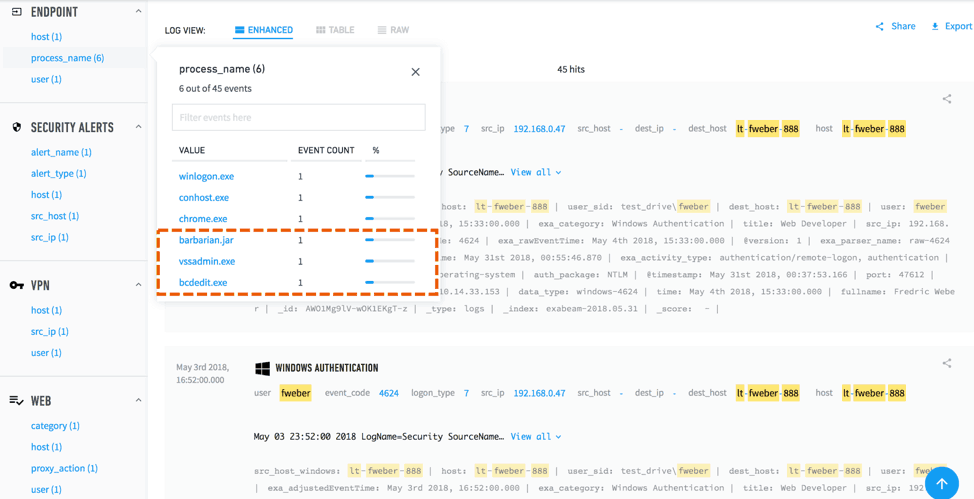
Figure 2: A search result within Exabeam Data Lake shows some processes running on an endpoint. This requires further investigation to determine if these processes are normal executables.
3. Next they include additional search parameters based on step 2 results.
4. They repeat steps 1 – 3, and possibly perform other search queries until they find any anomalous activities or threats.
5. By manually stitching events together from their disparate search results, they painstakingly assemble a timeline.
6. Finally they create new correlation rules and/or update existing ones based on what they’ve been fortunate enough to discover.
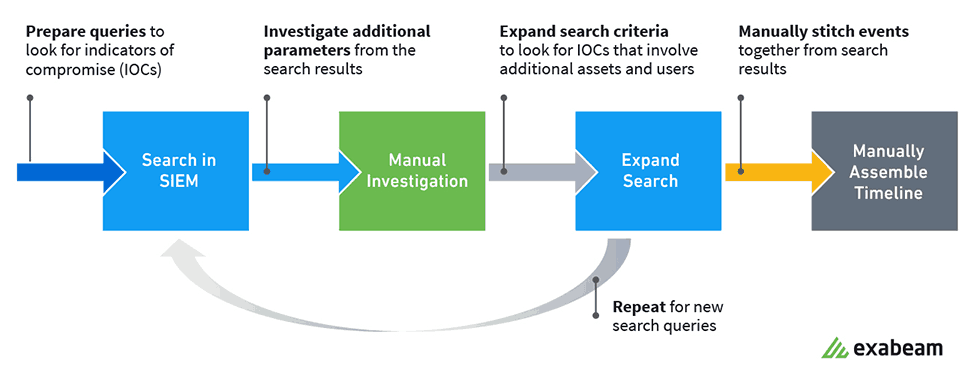
Figure 3: Threat hunting using a legacy SIEM.
Such hit and miss investigations are both tedious and inefficient. It’s difficult for an analyst to quickly and fully understand the scope of an incident, for multiple users, processes, devices, and network connections are involved. This threat hunting approach in a legacy SIEM has several limitations:
- Analysts miss threats — Search queries and correlation rules only find known threats. They’re unlikely to ever detect unknown threats.
- Overwhelming scale — Most environments have too many IOCs to hunt for. There isn’t an effective way to investigate them all.
- Extraordinary manual effort — It takes an enormous amount of time and effort to assemble results from multiple threat hunting searches into an incident timeline.
- Maintenance overhead — Analysts have to maintain and update correlation rules and constantly write new search queries to keep up with the influx of incoming security alerts.
Modern threat hunting with Exabeam Advanced Analytics
Replacing legacy discovery methods, Exabeam’s automated threat hunting understands the tactics, techniques, and procedures (TTPs) used by today’s most advanced hackers. It analyzes user and device behaviors while leveraging data from the MITRE ATT&CK framework, which tracks well-defined techniques and tactics that detect recognizable attack patterns. This lets security analysts more effectively pinpoint specific threats, thereby exposing all activities bad actors may be using to attack your infrastructure.
Let’s drill down into how Exabeam Threat Hunter does this. To look for specific threats, a modern SIEM lets analysts define broad or narrow searches using behavior (the TTPs) as search criteria, instead of artifacts (IoCs). Saving time on repetitive tasks, a simple point-and-click user interface (UI) enables even junior analysts to easily create complex queries without having to learn a proprietary search query language. They’re able to search by user type, user labels, activity type, asset labels, usernames, and risk reasons. And they can quickly string together conditions from available menus to make their search criteria as deep or wide as needed (Figure 4).
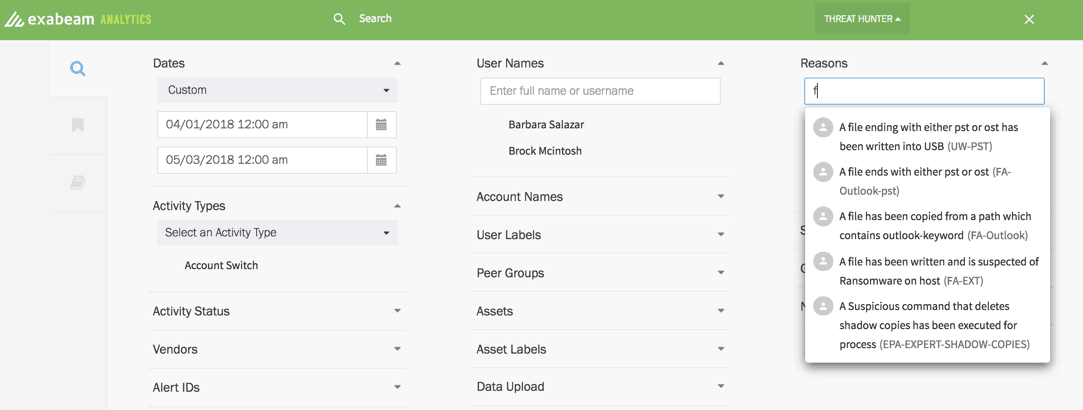
Figure 4: Modern threat hunting with a simple point-and-click interface to search for TTPs
Unlike legacy SIEMs that return event logs requiring additional analysis and manual timeline creation, modern SIEMs automatically create them showing relevant events (Figure 5). This lets analysts easily interpret the results and quickly review any suspicious activity.
Security investigators are able to review all anomalous events—not just those related to the limited set of tactics they were hunting for. These include lateral movement, file movements, web activities, and more—all stitched together in a way that follows any given threat and its affected users and assets. This helps them efficiently respond to incidents far more quickly and accurately.

Figure 5: Threat hunting search results returning timelines, instead of individual event logs
Modern threat hunting also lets analysts save search queries and modify them as they learn more about their environment. For example, they’re able to easily save tactics relating to the MITRE ATT&CK framework by including all risk reasons associated with the particular tactic or a technique (Figure 6). Additional risk reasons can be easily added or removed as they learn more about an attack.
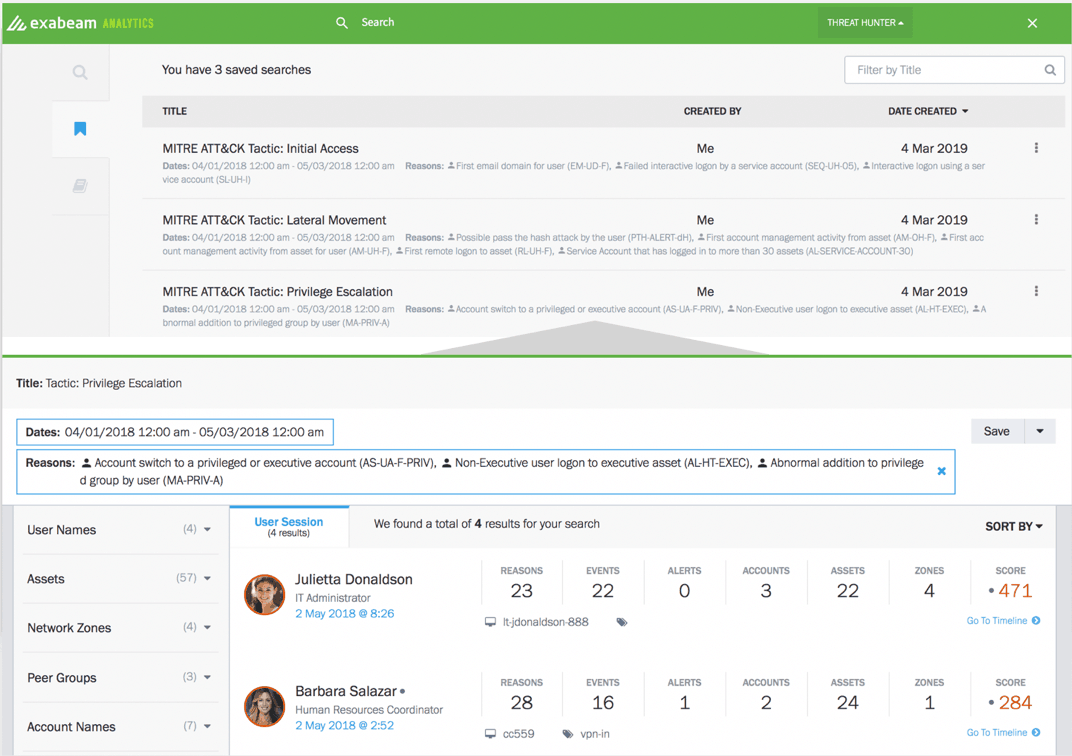
Figure 6: Examples of tactics used within the MITRE ATT&CK framework saved as threat hunting queries
Compared to a legacy model, modern SIEM threat hunting provides key advantages:
- Threat hunting is proactive, not reactive, thereby helping analysts discover threats in advance of an issue.
- It’s easier to hunt for threats using TTPs vs. IoCs, since investigators can also be alerted about previously unknown threats.
- Events are automatically stitched together into timelines, saving analysts time they can now allocate to more critical activities such as incident response.
- Investigators can respond to security incidents more accurately because timelines provide deep context about each incident.
Why a mature behavior analytics tool is a must for effective threat hunting
Behavior analytics tools create a baseline for user behavior and entity activities. They detect potential or actual intrusions, as well as malicious activities, and analyze anomalous activity through the use of behavioral modeling, peer group analysis, and machine learning algorithms.
Rather than requiring your security experts to manually whitelist or create and maintain correlation rules, modern SIEMs replace traditional Boolean alerts with behavioral models that weigh the risks associated with various behaviors.
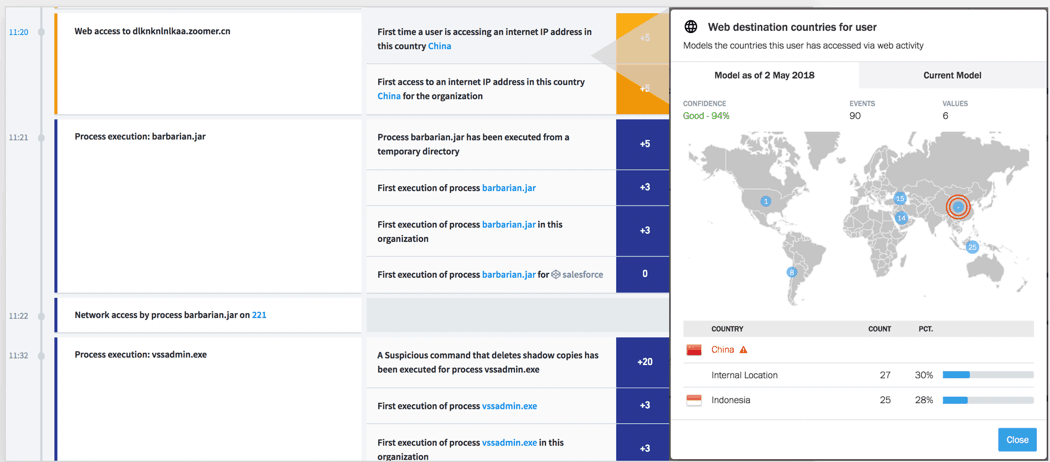
Figure 7: A model showing anomalous internet IP address access
It becomes extremely easy to detect threats using behavior analytics because there are hundreds of models to help detect deviations from user or asset baselines. Associated risk reasons provide a strong foundation to hunt down threats using behavioral indicators (TTPs), as opposed to conventional SIEM correlation rules (IOCs).
Providing analysts with additional data, behavior analytics assemble events by tracking behavior within your organization or network—in addition to cloud services, mobile devices, and IoT assets. User and entity behavior analytics (UEBA) can provide dramatic time savings because teams don’t have to manually dig into logs from diverse locations in a time-consuming effort to piece together the story of an incident.
Summary of legacy SIEM and modern threat hunting differences
| Query-based legacy threat hunting | Modern Exabeam threat hunting |
| Query-based | Intuitive, point and click UI |
| Can hunt for known IOCs | Can search for tactics, techniques and procedures (TTPs). Hunts for unknown threats used by attackers |
| Requires analysts to manually assemble all related events, which takes time and causes them to miss detecting threats | Automatically stitches together normal and anomalous behavior in incident timelines to easily pinpoint anomalous behavior and mitigate incidents faster |
| Can save search as a query
Analysts need to know the exact error/alert code to change the query |
Can save searches with various risk reasons associated with tactic or technique used in attacks Saved searches can be changed very easily; analysts don’t have to know or understand the underlying alert code and can update the risk reasons within the query |
| Legacy log management is used for anomaly detection and it’s primarily based on correlation rules | User and entity behavior analytics (UEBA) is used for threat detection; it’s primarily based on behavior analysis and machine learning |
Threat hunting in a modern SIEM provides several advantages over a legacy model, including:
- An intuitive point-and-click UI without needing to know how to write complex queries. Ability to run complex searches using context-aware data
- Ability to look for TTPs (tactics, techniques, and procedures) rather than just IOCs (indicators of compromise)
- Aids investigators by stitching all the events together from disparate sources, assesses normal/abnormal behavior, and embeds smart timelines into search results so analysts can easily pinpoint anomalous behavior and mitigate incidents faster
- Ability to save searches for future investigations
To learn more about Exabeam threat hunting capabilities, here are some helpful resources.
Why Understanding the Entire Attack Chain Before Responding is Critical
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













