Lateral movement combined with account switching (using a different account when targeting a different host) is a tactic used by attackers to compromise your network. Modern attackers are well-versed in your countermeasures, and investigation techniques, and know full well that combination-type attacks make it far more difficult for you to detect and respond to them.
Without the advantage of machine learning such tactics can be overlooked. For example, a human will likely not realize that activity A and activity B are two separate pieces of the same attack in the network. Without the understanding that A and B are indeed related, the analyst will miss the correlation and their response will most likely be incomplete.
What is lateral movement?
Lateral movement is a term that refers to techniques cyber attackers use to progressively move through a network, searching for targeted key data and assets. Legacy SIEMs will fire an alert based upon a correlation rule (static rule) for each event, but without context, the system, as well as the analyst, does not know to “tie them together”. This is what leads to inconsistent and incomplete responses and can result in a situation where there is no containment or response, but rather a metric being met that shows two closed attacks. In a day and age of metric-driven “results” it appears to be a win-win but in reality, it’s truly a false sense of security because a threat is not contained and remains present in your organization.
Security teams need smart, data-enriched timelines with contextual insights to surface attacks that involve lateral movement. This is where machine learning shines within the Exabeam Advanced Analytics platform.
Data-driven investigations
What if you approach attack investigations in a new way, relying more on data analytics and machine learning? Let’s say you can ingest all the data from every log, and that cost, regardless of the amount of data, isn’t a factor. Then imagine a technology that constantly examines all of the data collections, stitches it together, and then enriches it with additional data from other sources.
The result is a “smart timeline” with the missing details automatically filled in. Exabeam Smart Timelines stitches together both the normal and abnormal behavior for every user, machine, and asset on your network. It automatically baselines normal behavior, so it becomes easy to detect the deviations. Using a pre-generated timeline for every user and device provides insights you may never have been able to surface before. Exabeam Smart Timelines automatically combine sequence, behavior, identity, and scope into a security information model that’s shared with all Exabeam products, giving you a single, unified dashboard view of your entire network operation.
How lateral movement works
Let’s walk through a scenario where a user’s credentials are compromised and a remote attacker is moving laterally inside your organization—and using account switching to access resources.
The first item to understand is that typical correlation rules, with static alerts generate this sort of view for the analyst.
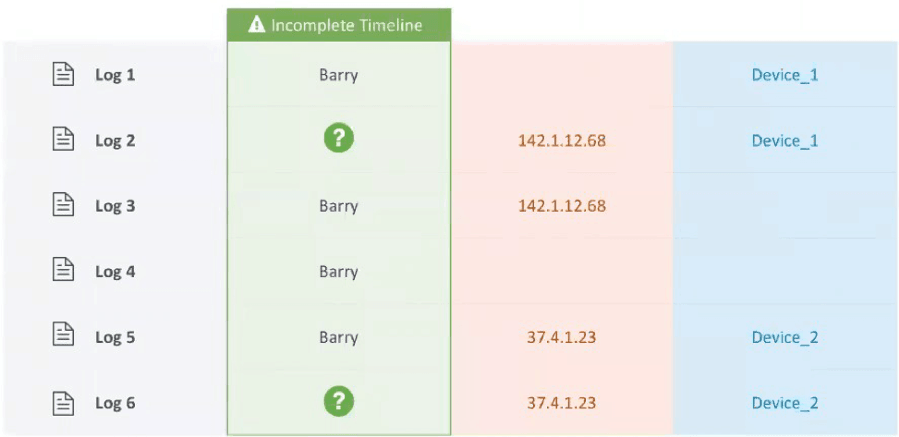
Figure 1: Correlation rules generate static alerts giving analysts an incomplete view of the security event.
The six log types being collected, without machine learning to stitch them together, provide an incomplete timeline for the user Barry. The system and the analyst does not realize there is context in the logs from other hosts that are not directly attributable to Barry. This remains a blindspot in your organization’s response. The lack of visibility into state change leaves the analyst at a disadvantage.
The following example shows user Barbara Salazar’s timeline and a separate timeline for an account “db_admin”. Without state change tracking, these appear to be two separate unrelated incidents. With proper state change tracking, we can recognize that the attempt to log into the database server as db_admin originated from Barbara Salazar’s workstation. We can now tie these two incidents together and begin to understand the intent of the two otherwise separate actions.
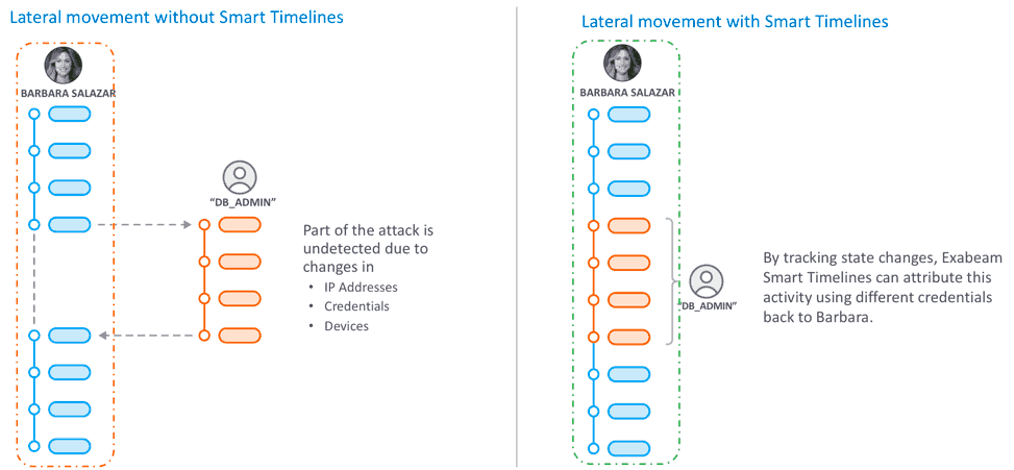
Figure 2: Lateral movement can be detected using machine learning, a key component of Exabeam Smart Timelines.
Tracking state change and tying such activity together is something humans do not do very well, but machine learning does quite well, and quickly. Understanding this sequence and the associated Splunk and Elastic queries below can give you some insight into the challenge that legacy SIEMs have.
- User bsalazar logs into her workstation
- Her workstation receives a DHCP address
- That workstation attempts to connect using a db_admin account to a remote database server
- User bsalazar is an HR director, not a database admin
- User db_admin runs a query and gets the payroll database
- An outbound file transfer of approximately the same size as the query results occurs.
Asking the analyst to tie together the user bsalazar, workstation IP, hostname, remote server, account db_admin, database query, outbound activity in the example provided would lead them to the following two search queries for Splunk and Elastic.
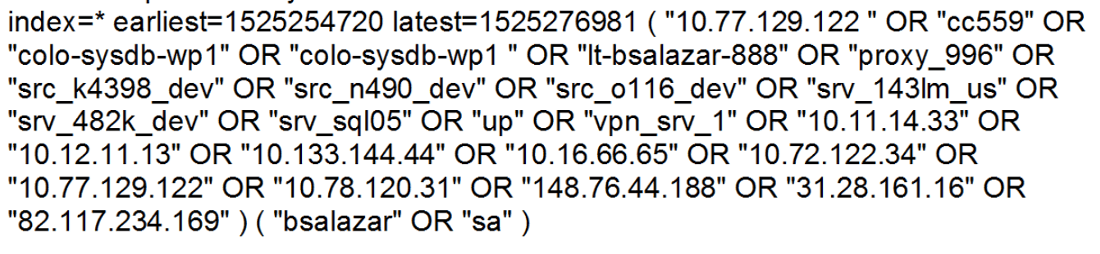
A timeline Splunk query

A timeline Elastic query
Exabeam Advanced Analytics using machine learning shows the results of this being performed automatically in the images below. It is important to note the amount of effort, skill and institutional knowledge the analyst would have to possess to be able to build such a query, one that catches all possible events. Machine learning greatly eases this burden, allowing the analyst to apply their skill and knowledge towards responding, versus figuring out the meaning of a series of related or unrelated events.
Tying disparate events into insights through machine learning
In this example, Advanced Analytics ties together the DHCP logs with the workstations and maintains state change over time, including when the workstation’s IP address is a source address for a remote login attempt. It is knowledge of that workstation’s IP address that allows Advanced Analytics to bring the two events together into a smart timeline:
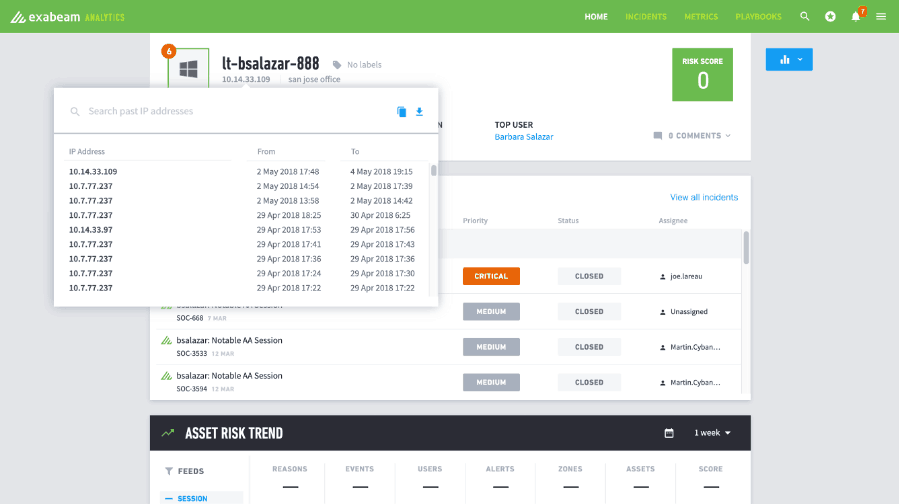
Figure 3: Exabeam Advanced Analytics correlates the IP addresses to detect lateral movement.
The automatic stitching together of the various log sources into individual events are used to build a smart timeline.
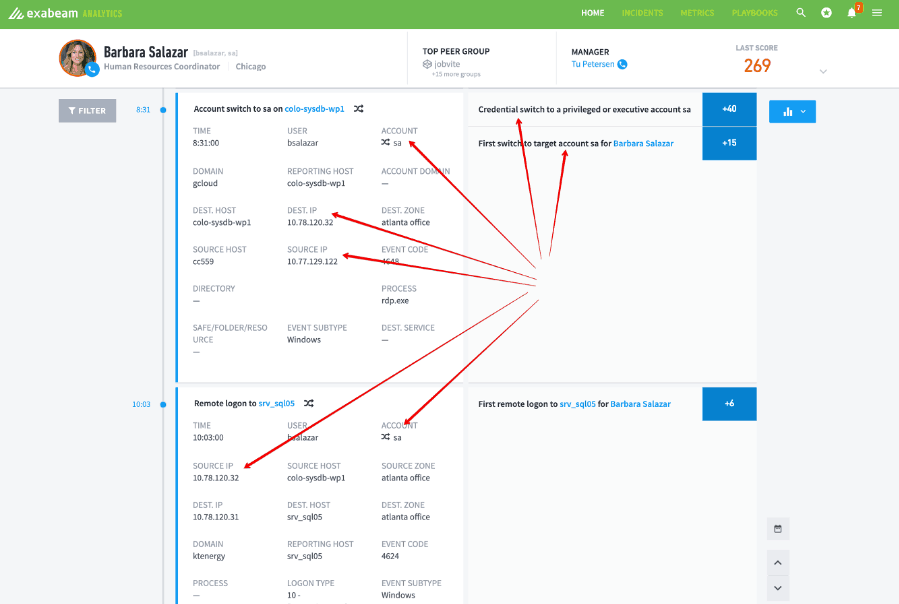
Figure 4: Exabeam Advanced Analytics parses log sources for data to create individual events to build a smart timeline.
The results of the machine learning, state change tracking, and events are being stitched together into a smart timeline.
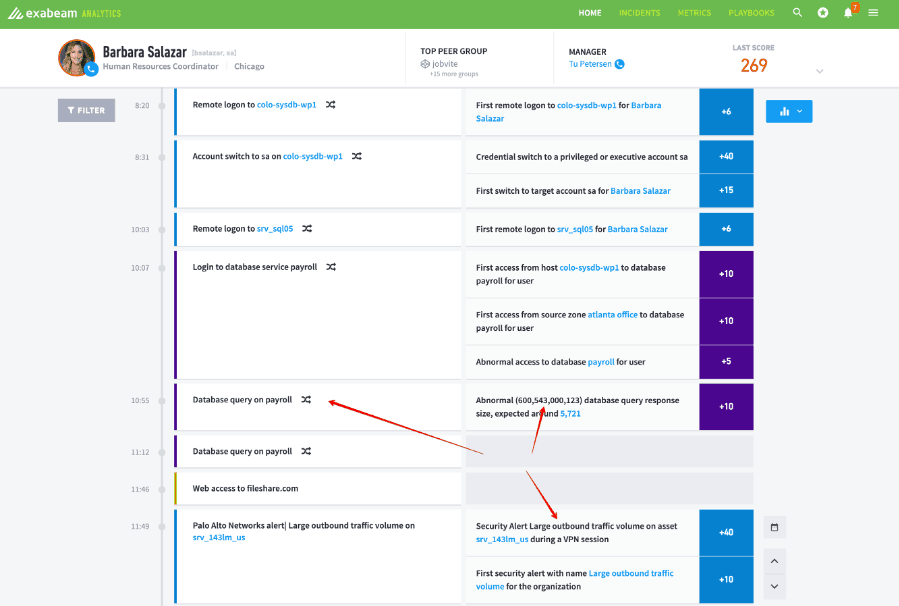
Figure 5: Machine learning, state change tracking and analysis provide all the data for a smart timeline.
Now security analysts have a complete picture of the events inside their organization to focus on. The events that previously appeared to be separate isolated events are now immediately visible to the analyst in a single timeline that they can respond to, actually isolate and contain or eliminate the threat. Hours, if not days, of effort trying to close individual tickets and increase metrics, is now spent on understanding intent, seeing separate events that are part of a single attack campaign, and responding quickly to shut it down.
Want to learn more about what Exabeam can do?
Have a look at these articles:
- How to Use Exabeam for Threat Hunting
- Advanced Analytics Use Case: Detecting Compromised Credentials
- An Incident Investigator’s Cheat Code
- Recreating an Incident Timeline–a Manual vs. Automated Process, Part 1
- Recreating an Incident Timeline–a Manual vs. Automated Process, Part 2
- IT Security: What You Should Know
- Penetration Testing: Process and Tools
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













