Cyber attacks and insider threats have rapidly become more common, creative and dangerous. Many of these attacks are carried by threat actors who attempt to bypass an organizations information security and gain access to sensitive data, which they can steal or damage. For this reason, the Information Technology (IT) team is one of the most critical components in the Security Operations Center (SOC) of any organization.
In this post:
- What is IT security?
- What are the types of IT security?
- Cybersecurity vs IT security
- IT security threats
- Information security technologies and tools
- IT security best practices
- Conclusion
What is IT security?
IT security encompasses a set of cybersecurity strategies and procedures to prevent unauthorized access to organizational assets and environments such as hardware, network, software and data. In other words, the goal of IT security is to maintain the integrity and confidentiality of company data.
The importance of IT security
The world is more connected than ever and newer technologies offer many quality-of-life benefits based on Internet-of-Things (IoT) are introduced every day. However, the more technology is connected, the more it is susceptible to cyber attacks. Thus, these technologies often serve as a double-edged sword.
Connected technologies and IoT devices are only half of the equation—the other half being the software. Newer versions of software are frequently released to support newer technologies and fix vulnerabilities. This creates two problems. First, new software updates are released to fix vulnerabilities, but there is no way to ensure that everyone using the vulnerable version installs patched updates. Second, even though new versions were created to fix vulnerabilities, they can contain new vulnerabilities themselves.
Many crucial infrastructures and systems such as hospitals and government offices rely on internet access to efficiently offer services. The connected nature of these systems provides an opening for threat actors to launch sophisticated and dangerous cyber attacks. For these reasons and more, IT security is all the more important in today’s connected world.
Types of IT security
Nowadays, applications are built with multiple access points to the network to offer better connectivity and user experience. Each of these access points introduces new opportunities for vulnerabilities that bad actors can exploit to get network access.
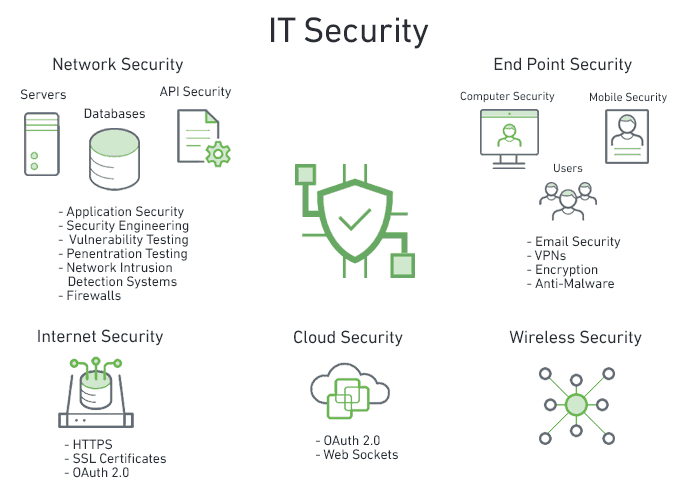
Figure 1: The IT Security chain – types of IT security
Forms of IT security:
- Network security—prevents unauthorized and malicious parties from accessing the network to ensure accessibility, integrity and reliability are uncompromised.
- Endpoint security—protects at the device level by preventing access to the network from endpoint devices that may try to insert malicious code or software into the organizational network. Endpoint protection covers all types of devices including laptops, personal computers and smartphones. Many tools, such as Data Loss Prevention (DLP), offer endpoint protection.
- Internet security—protects from cyber threats such as malicious downloads, intercepted sessions, or use of stolen credentials by filtering and encrypting traffic. Measures include the use of HTTPS, SSL and OAuth.
- Cloud security—provides users with security when they are connected straight to the cloud and therefore are not protected by traditional security measures. Cloud security typically involves applications that are based on Software-as-a-Service (SaaS) and are hosted in a third-party public cloud.
- Wireless security—prevents unauthorized access to systems via wireless networks, such as Wi-Fi or BlueTooth. Common methods include the use of Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), and implementation of pairing confirmations.
- Application security—ensures that applications take security into account from the start and not as an afterthought. This is mostly done by practicing procedures such as DevSecOps as part of the SOC to ensure applications are less vulnerable to attacks while also promoting faster development.
Cybersecurity vs IT Security: What Is the Difference?
In many organizations, IT security and cybersecurity responsibilities overlap since both involve protecting systems and data. There is often no clear definition of IT security vs cybersecurity. However, there are some differences between dedicated cybersecurity and more general security practices.
The scope of coverage
IT security is concerned with all systems and data within an organization. This includes both digital data and any physical copies of data that have been made. It also covers systems that are not connected to external networks.
The approach
IT security uses methods that apply to systems and workflows as a whole. It typically integrates a variety of tools and methods to cover all aspects of data collection, storage, processing, and sharing.
Cybersecurity also applies a variety of tools and methods. However, it only uses those focused on monitoring, detecting, blocking, and responding to threats stemming from cyberattacks.
The techniques implemented
IT security focuses on physical access controls, digital access controls, and system-wide monitoring. IT security policies and procedures apply across an organization regardless of connectivity.
According to Gartner’s CARTA model, cybersecurity has four key focus areas: assessing risks and taking action to prevent threats, detecting attacks or anomalous activity on networks or IT systems, responding to security incidents and mitigating threats, and predicting future attacks by analyzing vulnerabilities, performing threat assessment and leveraging threat intelligence data.
IT security threats
Some of the most common threats that IT security teams face include:
- Malicious software (malware)—a software used by attackers with malicious intent to cause damage to devices, environments, and networks.
- Insider threats—a malicious activity aimed at the company and carried out by someone who is employed by it. Insider threats are the most common and also the hardest to detect. However, there are certain indicators that can point to an insider threat.
- Ransomware—a type of malware designed to extort money from victims by blocking their access to files and settings and demanding payment for the decryption key.
- Structured Query Language (SQL) injection—a technique used by bad actors to access the database of an SQL based server and run malicious code. This technique takes advantage of code vulnerabilities that allow attackers to force SQL servers to execute code and perform actions such as revealing information that is supposed to be hidden to the end-user.
- Denial-of-service (DoS) attack—attackers flood the server or network with traffic to drain resources and reduce bandwidth. Consequently, the system or application becomes unresponsive and unusable to end-users.
Information Security Technologies and Tools
As your system grows, new technologies and security systems should be adopted to ensure you and your data remain protected. Using the right IT security technologies tools can increase the efficiency of your SOC staff and your cybersecurity while reducing manual efforts.
Security information and event management
SIEM—is a category of security solutions that collects security data from across the enterprise, and uses statistical correlations and advanced behavioral analysis to provide actionable information on security incidents. SOC staff can use the information collected by a SIEM to detect threats in real time, prepare audits for compliance objectives, manage incident response efforts and investigate past incidents.
User and entity behavior analytics
UEBA—helps monitor organizational systems and user accounts for anomalies or suspicious behavior, helping uncover threats that might otherwise go undetected.
Security, orchestration, automation and response
SOAR—is an IT security technology designed to help organizations collect data and alerts and on security threats and respond using automated incident response playbooks. SOAR is often used in combination with tools like SIEM and UEBA to augment their capabilities.
Data Loss Prevention (DLP)
Data loss prevention—is the use of information security technologies and practices to protect the confidentiality and availability of data. It focuses on preventing loss through theft, corruption, or unauthorized modification. DLP is also concerned with the unauthorized sharing of information, either intentionally or unintentionally.
Intrusion Detection System (IDS) and Intrusion Prevention System (IPS)
IDS—is a security technology that you can use to monitor your system traffic and identify breaches. It helps you detect malicious traffic or attempts to bypass your security systems and alerts security IT teams so they can respond quickly.
IPS is a similar security technology that you can use to prevent malicious traffic and reduce the success of attempted breaches. The main difference between IDS and IPS is that IDS is focused on monitoring while IPS is focused on control. Typically, these solutions are used together to protect a system.
IT security best practices
There are many types and solutions for effective IT security, here are a few of the best practices:
- Firewalls—helps organizations protect their data against cyberattacks by preventing unauthorized users from accessing information via the web.
- Employee training—many of the threats to the IT is insider threats, many of those are made unintentionally. It is important to educate and train employees on how to safeguard the environment by reducing the chances of introducing vulnerabilities.
- Frequent backups—frequently backing up all data and sensitive information to a separate, preferably isolated system. This practice helps ensure the reliability of the system and data and protects them from any type of damage.
- Incident Response Plan (IRP)—a structured methodology to deal with security incidents can significantly improve efficiency and reduce stress among SOC staff in critical situations where a quick and efficient reaction is key. It is highly recommended for every organization to include an incident response plan as part of a cybersecurity policy.
- Anti-malware software—a software designed to deal with malware. This should be installed on all the systems used by the organization, including personal devices such as laptops and cell phones.
Conclusion
With the growing number of threats facing organizations both from without and within, IT Security teams are a critical part of the SOC. To be effective, security must be applied at multiple levels, including network, cloud, endpoint and application levels. If your IT security teams are implementing the necessary practices and taking advantage of tools like SIEM, UEBA and SOAR, you can rest assured that your IT environment and applications are much safer.
See Additional Guides on Key Information Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of information security.
Security Operations Center
Authored by Exabeam
- SOC Analyst: Job Description, Skills, and Certifications
- What Is a Security Operations Center? Complete Guide
- 5 SecOps Functions and Best Practices for SecOps Success
Mitre Att&ck
Authored by Exabeam
Malware Protection
Authored by Cynet
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












