How to build an incident response plan around the 6 phases of incident response, examples to get you started, and a peek at incident response automation.
What is an incident response plan?
An incident response plan is a set of tools and procedures that your security team can use to identify, eliminate, and recover from cybersecurity threats. It is designed to help your team respond quickly and uniformly against any type of external threat.
Incident response plans ensure that responses are as effective as possible. These plans are necessary to minimize damage caused by threats, including data loss, abuse of resources, and the loss of customer trust.
Need an incident response solution? Request an incident response demo.
In this article:
- Why is an incident response plan important?
- What are the incident response steps?
- What incident response planning typically includes
- Incident response plan templates to get you started quickly
- Incident response plan examples: learn from leading organizations
- How to make an incident response plan successful
- What are the key roles in an incident response plan?
- The next generation of incident response: Security Orchestration, Automation and Response (SOAR)
Why is an incident response plan important?
The Ponemon Institute’s Cost of Cyber Crime Study showed that the typical organization experiences an average of 145 security incidents per year and spends $13 million annually year to defend itself. An effective response process can act to significantly reduce these costs. Incident response planning also protects your company’s reputation. IDC found that 80% of consumers would take their business elsewhere if directly affected by a data breach. If a security breach is not handled properly, the company risks losing business, as well as investor and shareholder confidence.
Additional benefits of incident response plans include:
- Data protection — securing backups, ensuring sufficient identity and access management, and timely patching of vulnerabilities.
- Reputation reinforcement — Effective incident response shows a brand’s commitment to security and privacy, and can save a company’s reputation in the event of a breach.
- Cost reduction — According to a study by IBM, the average cost of a breach is $4.35 million. Incident response planning can significantly reduce this cost by limiting the damage caused by an attack.
What are the incident response steps?
According to the SANS Institute’s Incident Handlers Handbook, there are six steps that should be taken by the Incident Response Team, to effectively handle security incidents.
1. Preparation – Perform a risk assessment and prioritize security issues, identify which are the most sensitive assets, and which critical security incidents the team should focus on. Create a communication plan, document roles, responsibilities, and processes, and recruit members to the Cyber Incident Response Team (CIRT).
2. Identification – The team should be able to effectively detect deviations from normal operations in organizational systems, and when an incident is discovered, collect additional evidence, decide on the severity of the incident, and document the “Who, What, Where, Why, and How”.
3. Containment – Once the team identifies a security incident, the immediate goal is to contain the incident and prevent further damage:
- Short-term containment — for example, isolating network segments or taking down infected production servers and handing failover.
- Long-term containment — applying temporary fixes to affected systems to allow them to be used in production, while rebuilding clean systems.
4. Eradication – The team must identify the root cause of the attack, remove malware or threats, and prevent similar attacks in the future. For example, if a vulnerability was exploited, it should be immediately patched.
5. Recovery – The team brings affected production systems back online carefully, to ensure another incident doesn’t take place. Important decisions at this stage are from which time and date to restore operations, how to verify that affected systems are back to normal, and monitoring to ensure activity is back to normal.
6. Lessons Learned – This phase should be performed no later than two weeks from the end of the incident, to ensure the information is fresh in the team’s mind. The purpose of this phase is to complete documentation of the incident, investigate further to identify its full scope, understand where the response team was effective, and areas that require improvement.
Incident response planning typically includes:
- The organization’s incident response strategy and how it supports business objectives
- Roles and responsibilities involved in incident response
- Procedures for each phase of the incident response process
- Communication procedures within the incident response team, with the rest of the organization, and external stakeholders
- How to learn from previous incidents to improve the organization’s security posture
An incident response plan forms the basis of your incident response cycle:
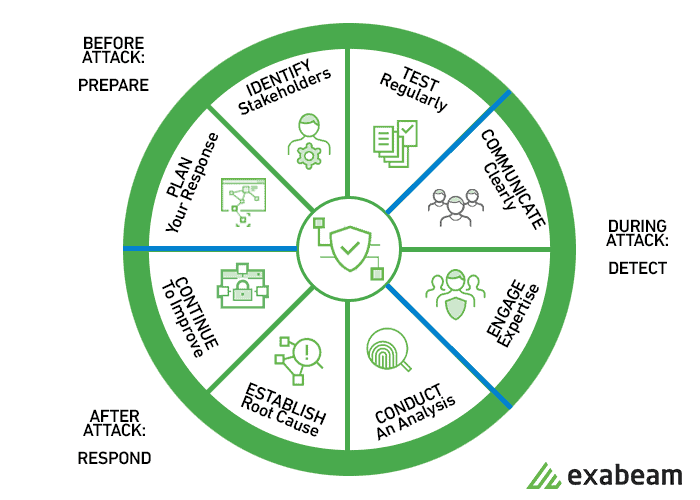
Incident response plan templates to get you started quickly
Following are four detailed templates you can use to kick off your incident response planning:
TechTarget’s incident response plan template (14 pages) includes scope, planning scenarios, and recovery objectives; a logical sequence of events for incident response and team roles and responsibilities; notification, escalation and declaration procedures; and incident response checklists. Download the template
Thycotic’s incident response template (19 pages) includes roles, responsibilities and contact information, threat classification, actions to be taken during incident response, industry-specific and geographic-dependent regulations, and a response process, as well as instructions on how to customize the template to your specific needs. Download the template (requires registration)
Sysnet’s security incident response plan (11 pages) includes how to recognize an incident, roles and responsibilities, external contacts, initial response steps, and instructions for responding to several common incident types, such as malware and unauthorized wireless access. Download the template (requires registration)
California Government Department of Technology incident response plan (4 pages) includes a 17-step checklist for incident team members to follow, with reference to more detailed procedures for specific types of incidents (which you will have to create on your own). Download the template
Incident response plan examples: learn from leading organizations
When developing an incident plan, it is valuable to see actual examples of plans created by other organizations. Some of the examples won’t be applicable to your industry’s incident scenarios, but can provide some inspiration.
See examples of plans from the following organizations:
- Carnegie Mellon University — including definitions, roles and responsibilities, methodology, incident response phases, guidelines for insider threats and interaction with law enforcement, and documentation
- Tulane University — including scope, roles, and responsibilities, incident definitions, escalation levels and response stages per level of criticality
- Wright State University — including scope, response steps, usage of security tools, and an intrusion checklist
How to make an incident response plan successful
What are the key considerations for incident response?
An incident response plan should include the following elements to be effective:
- Senior management support — Management support will allow you to recruit the most qualified members for your response team, and create processes and information flows that will help you manage an incident effectively.
- Consistent testing — An incident response plan is not worth much if it’s only on paper: it must be put to the test. Conducting a planned (or even better, unplanned) security drill, running through the plan, and identifying weak spots will go a long way toward validating that the team is ready for a real incident.
- Balance between detail and flexibility — The plan must have specific, actionable steps the team can follow quickly when an incident occurs. At the same time, creating rigid processes leads to complexity and an inability to deal with unexpected scenarios. Create a detailed plan, but allow for flexibility to support a wide range of incidents. Updating the plan frequently can also help with flexibility — reviewing the plan every six months or so can help you account for new types of security issues and attacks that affect your industry.
- Clarify communication channels — The plan should make it clear who the incident team should communicate with, via which communication channels, and what information should be conveyed. This is a critical and sometimes overlooked part of the response process. For example, there should be clear guidelines on what level of detail should be communicated to IT management, senior management, affected departments, affected customers, and the press.
- Know your stakeholders — Who are the key roles within the organization who should care and be involved in a security incident? These might change depending on the type of incident and the organizational resources targeted. Stakeholders could include department managers, senior management, partners, customers, and legal.
- Keep the plan simple — A well-known management principle, “Keep it Simple, Stupid” (KISS), should also be applied to response plans. A complicated plan, even if very well thought out, is not likely to be accurately followed in real time. Keep details, steps, and procedures down to an absolute minimum, to ensure that the team can process and apply them to the incident as they enter the “fog of war.”
What are the key roles in an incident response plan?
An incident response plan is not complete without a team that can carry it out — the Computer Security Incident Response Team (CSIRT). An incident response team is a group of people — either IT staff with some security training or full-time security staff in larger organizations — who collect, analyze, and act upon information from an incident.
They are the focal point of the incident, and are responsible for communicating with other stakeholders within the organization, and external parties such as legal counsel, press, law enforcement, affected customers, etc.
What is the relationship between an incident response plan and a disaster recovery plan?
An incident response plan should be complemented by a disaster recovery plan. The latter prescribes how an organization manages a catastrophic event such as a natural disaster or accidental loss of data. While an incident response plan focuses on identifying a security event and bringing it to closure, disaster recovery aims at bringing systems back online, subject to a Recovery Time Objective (RTO).
The next generation of incident response: Security Orchestration, Automation, and Response (SOAR)
There is no replacement for crafting an incident response plan and assigning dedicated individuals to be responsible for it. However, to make incident response more effective and make it possible to deal with more security incidents, a new category of tools has evolved that helps automate the response to security incidents.
Security Orchestration, Automation, and Response (SOAR) tools can:
- Integrate with other security tools, orchestrating them to enable a complex response to an attack
- Automate multi-step response procedures using security playbooks
- Support case management by recording all information related to a specific security incident, creating a complete event timeline, and helping analysts collaborate and add data and insights to the event
To see an example of an integrated security solution that includes SOAR as well as User and Entity Behavior Analytics (UEBA) and Security Information and Event Management (SIEM) capabilities, see Exabeam’s Incident Responder.
Learn more about Incident Response
- The Three Elements of Incident Response: Plan, Team, and Tools
- The Complete Guide to CSIRT Organization: How to Build an Incident Response Team
- 10 Best Practices for Creating an Effective Computer Security Incident Response Team (CSIRT)
- How to Quickly Deploy an Effective Incident Response Policy
- IT Security: What You Should Know
- Incident Response Steps: 6 Tips for Responding to Security Incidents
- Beat Cyber Threats with Security Automation
- IPS Security: How Active Security Saves Time and Stops Attacks in their Tracks
Need an incident response solution? Click here for an incident response demo.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













