What is IPS Security?
An intrusion prevention system (IPS) is a network security technology that monitors network traffic to detect anomalies in traffic flow. IPS security systems intercept network traffic and can quickly prevent malicious activity by dropping packets or resetting connections. They can be a preventative measure as part of your incident response plan.
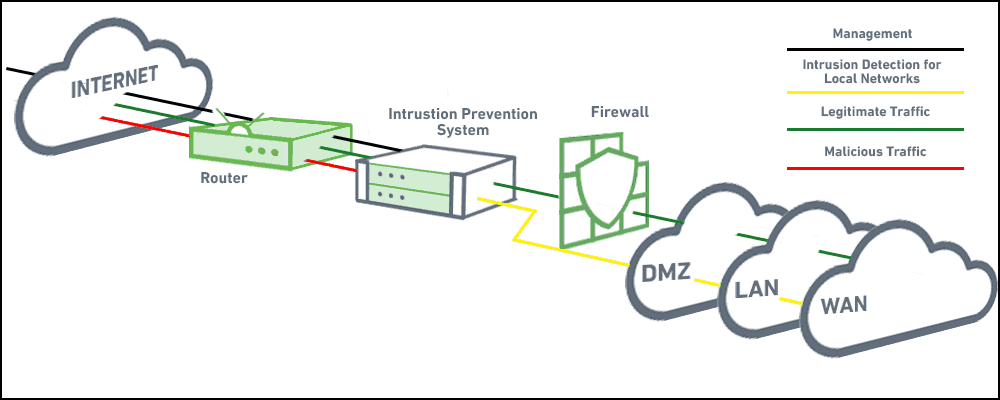
IDS versus IPS: What is the Difference?
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) both analyze network traffic for threat signatures or anomalies in network traffic. The difference is that IDS is a monitoring system that doesn’t alter network packets, while IPS is an inline control system, which can stop packets from being delivered based on security events it detects.
Most IPS security systems also perform an IDS function. IDS systems, by contrast, are passive and do not modify any network communications, so they cannot function as an IPS.
How Do Intrusion Detection Systems and Intrusion Prevention Systems Work?
IDS can be either a hardware device or software application that monitors network traffic, incoming and outbound, for any malicious activity or security policy violation. The same is true for IPS security.
IDS can be either network-based or host-based:
- Network-based intrusion detection systems (NIDS) have sensors strategically placed within the network, sometimes at multiple locations, to monitor as much traffic as possible without creating performance bottlenecks.
- Host-based intrusion detection systems (HIDS) run on specific hosts or devices, monitoring the traffic associated with them.
IPS security can detect the same kind of malicious activity and policy violation that an IDS does, and can additionally respond in real time to stop immediate threats:
- Like an IDS, IPS can be network-based with sensors at various points of the network or host-based with sensors on the host to monitor individual devices.
- Unlike the IDS, IPS has the ability to configure policy-based rules and actions to be executed when any anomaly is detected.
Which Should You Prefer—IDS or IPS?
For the majority of use cases, IPS security is preferable to IDS in today’s security environment:
- IPS can prevent security threats, while IDS only provides information.
- IPS can save time for security teams, while IDS adds more alerts that security teams need to analyze and act upon.
- IPS provides the same functionality as IDS, so it’s the same—plus more.
However, IPS security has an added overhead because it’s deployed inline and intercepts all network traffic. It needs to have sufficient capacity to process your network’s traffic loads, and in case of a malfunction, it can become a single point of failure (SPOF).
How Do Intrusion Prevention Systems Work?
Signature-based detection
Most intrusion detection systems (IDS) are signature-based. They operate similar to a virus scanner, searching for known malicious activity—or a signature—for each intrusion event.
While signature-based IDS is very efficient at detecting known attacks, a signature must be created for every attack, and new types of attacks cannot be detected. Yet, hackers tend to continually test and probe; it’s only a matter of time before they discover a way around even the most sophisticated signature-based intrusion detection systems.
Anomaly-based intrusion detection
While signatures work well against attacks with a fixed behavioral pattern, they don’t work as well against dynamic attack patterns. Anomaly-based IDS establishes a baseline for network behavior. This baseline is a description of accepted network behavior, which is learned or specified by the network administrators. The anomaly detection engine identifies an event when it sees behavior that falls outside the predefined or accepted behavioral model.
Passive network monitoring
IPS security can also be set to passively monitor network traffic at certain points, and identify malicious behavior. It uses security threshold parameters to identify if activity is acceptable or may be malicious, and generate alerts for the security team.
What Does IPS Protect Against?
IPS security solutions can stop any attack based on malicious traffic sent over a network, provided it has a known attack signature, or can be detected as anomalous compared to normal traffic. IPS is commonly used to detect and stop all the attacks below.
There is one important caveat: modern DDoS attacks are waged on a large scale that can overwhelm any single piece of security equipment. Large-scale DDoS can only be mitigated by distributed resources, such as cloud-based traffic scraping services.
| Attack | Description |
| DDoS Attacks | An attempt to make a server, service, or network unavailable by overwhelming it with a flood of traffic from multiple, distributed computing systems. |
| Smurf Attack | A type of DoS attack in which a system is flooded by a large number of Internet Control Message Protocol (ICMP) packets, rendering the victim’s network unresponsive. |
| Ping of Death | A DoS attack in which an attacker attempts to crash a system by sending malformed or oversized packets, using a ping command. |
| SYN Flood Attacks | A DoS attack in which large volumes of SYN (synchronize) packets (connection requests) are sent to a victim’s server or firewall, rendering it unavailable. |
| SSL Evasion | Attackers exploit Secure Sockets Layer (SSL) / Transport Layer Security (TLS) encryption blind spots, using SSL/TLS to hide malicious content, evade detection, and bypass security controls. |
| IP Fragmentation Attack | Attackers overwhelm network resources by exploiting datagram fragmentation mechanisms, confusing the target system as to how TCP/UDP datagrams should be reassembled. |
| Port Scanning Attack | Attackers send requests to a range of server ports, with the goal of finding an active port and exploiting its vulnerability. |
| ARP Spoofing | Attackers send fake Address Resolution Protocol (ARP) messages, linking the attacker’s MAC address with the IP address of a legitimate system and diverting traffic from that system to the attacker. |
| Buffer Overflow Attacks | Attackers exploit buffer overflow vulnerabilities, corrupting the execution path of an application by overwriting parts of its memory. |
| OS Fingerprinting Attacks | Attackers attempt to identify the operating system of a specific target and exploit its vulnerabilities. |
| SMB Probes | Attackers capture Server Message Block (SMB) protocol authentication requests, and relay them to another host. |
How Does IPS Save Time for Security Teams?
- Automated response—IDS/IPS systems are largely automatic. They protect networks from known threats with a limited time investment by the security team.
- Compliance—Compliance often requires proving that you have invested in technologies and systems to protect data. IDS/IPS solutions address a number of the Center for Internet Security (CIS) Security controls, and provide auditing data valuable for compliance investigations.
- Policy enforcement—IDS/IPS helps enforce internal security policies at the network level. For example, if you only support one VPN, you can use the IPS to block traffic from another VPN.
Top 5 Intrusion Prevention Systems
1. Cisco FirePOWER
Cisco’s Next-Generation Intrusion Prevention System (NGIPS) provides complete and unified management over firewalls, application control, intrusion prevention, URL filtering, and advanced malware protection.

2. IBM Security Network Intrusion Prevention System
The IBM Security Network IPS appliances are purpose-built, Layer 2 network security appliances you can deploy either at the gateway or the network. They can block intrusion attempts, DoS attacks, malicious code, backdoors, spyware, and peer-to-peer applications without requiring extensive network reconfiguration.

3. McAfee Network Security Platform
McAfee Network Security Platform (McAfee NSP) is a next-generation intrusion prevention
system that discovers and blocks sophisticated malware threats across the network. It can support up to 32 million connections on a single appliance and uses intelligence to find and block advanced targeted attacks on the network.

4. Radware DefensePro
DefensePro DDoS mitigation uses adaptive behavioral analysis technologies with dedicated high performance hardware to confront all types of DDoS attacks on a network.

5. Trend Micro TippingPoint
Trend Micro TippingPoint Intrusion Prevention System combines application-level security with user awareness and inbound/outbound messaging inspection capabilities.

IPS, IDS, and Security Information and Event Management (SIEM)
SIEM is a foundational system in large data centers, that is gradually entering smaller organizations as well. It can collect logs and events from hundreds of security tools and IT systems, pulling them all together and generating meaningful alerts for security teams.
Next-generation SIEM systems have additional capabilities such as User and Entity Behavior Analytics (UEBA), which establishes baselines for users and enterprise systems, and through machine learning, identifies activity that is abnormal and could represent a security incident.
When a SIEM is deployed together with an IPS or IDS system, it can help by gathering the events it identifies, and correlating them with many other data sources such as network data upstream or downstream, activity on enterprise applications, and antivirus alerts.
Benefits of Using a SIEM with IPS/IDS
A SIEM can identify security incidents that an IPS or IDS with its limited view of network traffic can miss. Even if an IPS security system identifies a problem and drops the problematic packets, a SIEM can give security teams a broader view on the incidents. Next-gen SIEM technology can automatically construct an incident timeline, providing context on what happened before the current event, and can include other user activities or security events that be related.
While IPS is a time saver for security teams, it doesn’t provide a full solution, because security staff still need to analyze the broader context and respond to each IPS alert. With next-gen SIEM, IPS alerts can be immediately visualized within an incident timeline, saving even more time and dramatically speeding incident response.
For an example of a next-gen SIEM that works alongside IDS and IPS systems, and provides advanced analytics and incident timelines, learn more about Exabeam’s Security Management Platform.
Want to learn more about Incident Response?
Have a look at these articles:
- The Three Elements of Incident Response: Plan, Team, and Tools
- The Complete Guide to CSIRT Organization: How to Build an Incident Response Team
- 10 Best Practices for Creating an Effective Computer Security Incident Response Team (CSIRT)
- How to Quickly Deploy an Effective Incident Response Policy
- Incident Response Plan 101: How to Build One, Templates and Examples
- IT Security: What You Should Know
- Incident Response Steps: 6 Tips for Responding to Security Incidents
- Beat Cyber Threats with Security Automation
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!