What is the Incident Response (IR) Process?
When a security incident occurs, every second matters. Malware infections rapidly spread, ransomware can cause catastrophic damage, and compromised accounts can be used for privilege escalation, giving attackers access to more sensitive assets.
Incident response (IR) is a structured methodology for handling security incidents, breaches, and cyber threats. A well-defined incident response plan (IRP) allows you to effectively identify, minimize the damage from, and reduce the cost of a cyberattack, while finding and fixing the cause, so that you can prevent future attacks.
During a cybersecurity incident, security teams face many unknowns and must immediately focus on the critical tasks at hand. Having pre-planned incident response steps during a security incident can prevent many unnecessary business impacts and reputational damage.
Read on to learn a six-step process that can help your incident responders take action faster and more effectively when the alarm goes off.
In this article:
- What do compliance standards require in case of a cybersecurity incident?
- What are the NIST and SANS incident response methodologies?
- What are the 6 steps of incident response?
What do compliance standards require in case of a cybersecurity incident?
When a cybersecurity incident is confirmed by security analysts, it is important to inform relevant parties as soon as possible. There are specific requirements in common compliance standards:
- Privacy laws such as GDPR and California’s CCPA require public notification, and in some cases, personal notification to data subjects, in the event of a data breach.
- PCI DSS compliance specifies the steps an incident response plan should contain. In particular, Requirement 12 specifies your incident response plan should assign certain employees to be available 24/7, properly train incident response staff, and set up alerts.
Depending on the severity of the breach, legal, press and executive management should be involved. In many cases, other departments such as customer service, finance, or IT need to take immediate action. Your incident response plan should clearly state who should be informed, depending on the type and severity of the breach. The plan should include full contact details and how to communicate with each relevant party, to save time in the aftermath of an attack.
What are the NIST and SANS incident response methodologies?
The two most commonly used incident response frameworks are the National Institute of Standards and Technology (NIST) Computer Security Incident Handling Guide (SP 800-61) and the SANS institute Incident Handler’s Handbook.
The table below shows incident response steps according to each of these methodologies.
| NIST Incident Response Steps | SANS Incident Response Steps |
|---|---|
| 1. Preparation | Step 1. Preparation |
| 2. Detection and Analysis | Step 2. Identification |
| 3. Containment, Eradication, and Recovery | Step 3. Containment |
| Step 4. Eradication | |
| Step 5. Recovery | |
| 4. Post-Incident Activity | Step 6. Lessons Learned |
The incident response steps in each of these methodologies are similar, but there are subtle differences. The key difference is in step 3 of the NIST process, which groups together containment, eradication, and recovery into one step — meaning that these activities should be performed together. By contrast, in the SANS process these are distinct steps which should be followed one after the other.
The image below illustrates the NIST process and the flow between the four process steps.
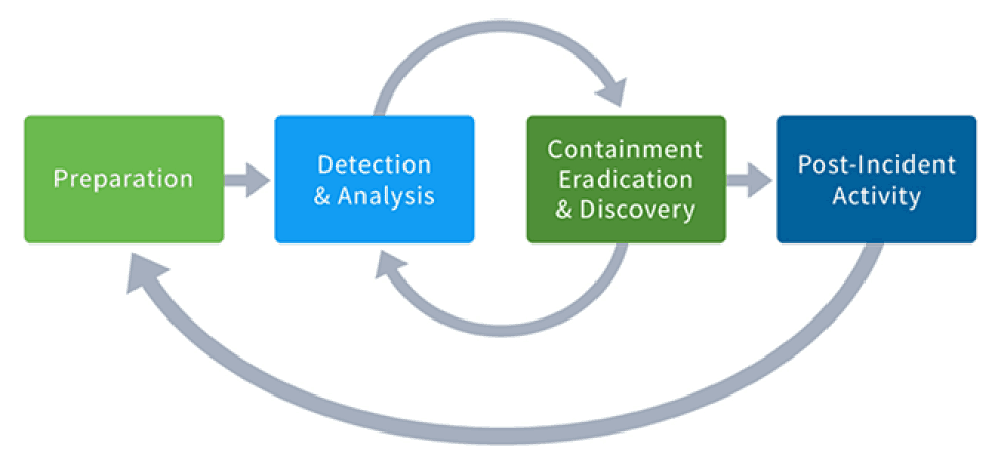
What are the 6 steps of incident response?
The first priority when implementing incident response cybersecurity is to prepare in advance by putting a concrete IR plan in place. Your incident response methodology should be battle-tested before a significant attack or data breach occurs.
Building on the NIST incident response phases, here are specific incident response steps to take once a critical security event has been detected:
1. Assemble your team
It’s critical to have the right people with the right skills, along with associated tribal knowledge. Appoint a team leader who will have overall responsibility for responding to the incident. This person should have a direct line of communication with management so that important decisions—such as taking key systems offline if necessary—can be made quickly.
In smaller organizations, or where a threat isn’t severe, your SOC team or managed security consultants may be sufficient to handle an incident. But for the more serious incidents, you should include other relevant areas of the company such as corporate communications and human resources.
If you have built a Security Incident Response Team (CSIRT), now is the time to activate your team, bringing in the entire range of pre-designated technical and non-technical specialists.
If a breach could result in litigation, or requires public notification and remediation, you should notify your legal department immediately.
2. Detect and ascertain the source.
The IR team you’ve assembled should first work to identify the cause of the breach, and then ensure that it’s contained.
Security teams will become aware that an incident is occurring or has occurred from a very wide variety of indicators, including:
- Users, system administrators, network administrators, security staff, and others from within your organization reporting signs of a security incident
- SIEMs or other security products generating alerts based on analysis of log data
- File integrity checking software, using hashing algorithms to detect when important files have been altered
- Anti-malware programs
- Logs (including audit-related data), which should be systematically reviewed to look at anomalous and suspicious activity with:
- Users
- External storage
- Real-time memory
- Network devices
- Operating systems
- Cloud services
- Applications
3. Contain and recover
A security incident is analogous to a forest fire. Once you’ve detected an incident and its source, you need to contain the damage. This may involve disabling network access for computers known to be infected by viruses or other malware (so they can be quarantined) and installing security patches to resolve malware issues or network vulnerabilities. You may also need to reset passwords for users with accounts that were breached, or block accounts of insiders that may have caused the incident. Additionally, your team should back up all affected systems to preserve their current state for later forensics.
Next, move to any needed service restoration, which includes two critical steps:
- Perform system/network validation and testing to certify all systems as operational.
- Recertify any component that was compromised as both operational and secure.
Ensure your long-term containment strategy includes not only returning all systems to production to allow for standard business operation, but also locking down or purging user accounts and backdoors that enabled the intrusion.
4. Assess damage and severity
Until the smoke clears it can be difficult to grasp the severity of an incident and the extent of damage it has caused. For example, did it result from an external attack on servers that could shut down critical business components such as e-commerce or reservation systems? Or, for example, did a web application layer intrusion perform a SQL Injection attack to execute malicious SQL statements on a web application’s database or potentially use a web server as a pathway to steal data from or control critical backend systems? If critical systems are involved, escalate the incident and activate your CSIRT or response team immediately.
In general, look at the cause of the incident. In cases where there was a successful external attacker or malicious insider, consider the event as more severe and respond accordingly. At the right time, review the pros and cons of launching a full-fledged cyber attribution investigation.
5. Begin the notification process
A data breach is a security incident in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by an individual unauthorized person. Privacy laws such as GDPR and California’s CCPA require public notification in the event of such a data breach. Notify affected parties so they can protect themselves from identity theft or other fallout from the disclosure of confidential personal or financial data. See Exabeam’s blog on how to create a breach notification letter in advance of a security incident.
6. Take actions to prevent the same type of incident in the future
Once a security incident has been stabilized, examine lessons learned to prevent recurrences of similar incidents. This might include patching server vulnerabilities, training employees on how to avoid phishing scams, or rolling out technologies to better monitor insider threats. Fixing security flaws or vulnerabilities found during your post-incident activities is a given.
Also, review lessons learned from the incident and implement appropriate changes to your security policies with training for staff and employees. For example, if the attack resulted from an unwitting employee opening an Excel file as an email attachment, implement a company-wide policy and training on how to recognize and respond to a phishing email.
Lastly, update your security incident response plan to reflect all of these preventative measures.
Conclusion
An incident response methodology enables organizations to define response countermeasures in advance. There is a wide range of approaches to IR. The majority of security professionals agree with the six incident response steps recommended by NIST, including preparation, detection and analysis, containment, eradication, recovery, and post-incident audits.
When it comes to preparation, many organizations leverage a combination of assessment checklists, detailed incident response plans, summarized and actionable incident response playbooks, as well as policies that can automate some of the processes. While well-planned, an incident response methodology should remain flexible, allowing for continuous improvement.
Want to learn more about Incident Response?
Have a look at these articles:
- The Three Elements of Incident Response: Plan, Team, and Tools
- The Complete Guide to CSIRT Organization: How to Build an Incident Response Team
- 10 Best Practices for Creating an Effective Computer Security Incident Response Team (CSIRT)
- How to Quickly Deploy an Effective Incident Response Policy
- Incident Response Plan 101: How to Build One, Templates and Examples
- IT Security: What You Should Know
- Beat Cyber Threats with Security Automation
- IPS Security: How Active Security Saves Time and Stops Attacks in their Tracks
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













