What is a security operations center (SOC)?
While a SOC traditionally refers to a physical facility within an organization, it more regularly refers to in-house or outsourced information security professionals that analyze and monitor the organization’s security systems. The SOC’s mission is to protect the company from security breaches by identifying, analyzing, and reacting to cybersecurity threats. SOC teams are composed of management, security analysts, and sometimes, security engineers. The SOC works across teams, with the company’s development and IT operations teams.
SOCs are a proven way to improve threat detection, decrease the likelihood of security breaches, and ensure an appropriate organizational response when incidents do occur. SOC teams identify unusual activity on servers, databases, networks, endpoints, applications, etc., investigate security threats, and respond to security incidents as they occur.
Once upon a time, it was believed that a SOC was only suitable for large enterprises. Today, many smaller organizations are setting up lightweight SOCs, such as a hybrid SOC, which combines part-time, in-house staff with outsourced experts, or a virtual SOC, which has no physical facility at all, and is a team of in-house staff who also serve other functions.
This is part of an extensive series of guides about information security.
In this article, you will learn:
- What is a security operations center?
- How do security operations centers work?
- Main focus areas of a SOC
- 7 SOC deployment models and their pros and cons
- Security operations center roles and responsibilities
- Benefits of security operations centers
- SOC challenges and how technology can help
- Getting started with a SOC
- The future of the SOC
How do security operations centers work?
SOCs operate by collecting, analyzing, and correlating data from various sources, such as network traffic, log files, and threat intelligence feeds. This data is then used to detect potential security incidents and respond to them in a timely manner. Following are the key components of a modern SOC:
Continuous Monitoring
One of the main functions of a SOC is to continuously monitor an organization’s IT infrastructure for any signs of suspicious activity or potential threats.
This involves the use of various detection tools and technologies, such as intrusion detection systems (IDS), email security, cloud security, and endpoint detection and response (EDR) solutions, collected into a security information and event management (SIEM) system.These tools help the SOC team identify unusual or malicious activities that may indicate a security breach or an attempted attack.
Threat Intelligence
By gathering and analyzing information about current and emerging threats, security teams can better understand the tactics, techniques, and procedures (TTPs) used by malicious actors. This knowledge enables them to proactively defend against potential attacks and respond more effectively to incidents when they occur.
Threat intelligence can be sourced from various channels, including open-source intelligence (OSINT), commercial threat intelligence feeds, and information sharing groups or platforms.
Incident Response
When a potential security incident is detected, the SOC team must quickly assess the situation and determine the appropriate course of action. This involves containing the threat, mitigating its impact, coordinating with other teams within the organization to ensure a swift and effective response, and ensuring recovery of operational systems.
Incident response plans and playbooks are critical components of a SOC’s operations, as they provide a structured, and often automated approach to dealing with different types of security incidents.
Main focus areas of a SOC
A well-designed security operations center should focus on several key areas to ensure the organization’s digital assets are adequately protected. These focus areas include:
Network Security
Network security involves protecting the organization’s network infrastructure from unauthorized access, misuse, or disruption. This includes monitoring network traffic for signs of intrusion, analyzing log data for anomalies, and implementing network segmentation and access controls to restrict access to resources, often through a zero trust security model. This ultimately limits the potential impact of a security breach.
Endpoint Security
Endpoints, such as desktops, laptops, and mobile devices, are often targeted by cybercriminals as they can serve as entry points into an organization’s network. A SOC must focus on securing these devices by implementing strong authentication and access controls, monitoring for signs of compromise, and ensuring that security patches and updates are applied in a timely manner.
Cloud Security
As more organizations are interested in taking advantage of the agility and scale of the cloud, a SOC must include not only cloud access but cloud infrastructure and data security into their monitoring and detection plans to avoid accidental and malicious leaks of sensitive information.
Application Security
Applications are another critical area that SOCs must focus on, as they can be exploited by attackers to gain unauthorized access to sensitive data or carry out other malicious activities.
Application security involves identifying and addressing vulnerabilities in the software development lifecycle, monitoring for signs of application-based attacks, and securing application programming interfaces (APIs) and other components of the application infrastructure.
7 SOC deployment models and their pros and cons
Let’s review the primary models organizations use to deploy a SOC, some of which are innovative models that have emerged over the past few years.
1. Dedicated SOC
A dedicated security operations center is a SOC model that is focused solely on providing security services to a single organization. This type of SOC often has a physical location within the organization’s premises and is staffed by in-house security experts responsible for monitoring, detecting, and responding to security incidents and threats.
Pros: Having a dedicated SOC provides a highly focused and customized approach to security, as the security experts are dedicated solely to the organization’s networks and systems. This results in a more in-depth understanding of the organization’s unique security needs and allows for more effective threat management.
Cons: A dedicated SOC may not be suitable for all organizations. For one, the cost of setting up and maintaining a dedicated SOC can be quite high, as it requires significant investment in infrastructure, technology, and highly skilled security professionals. Moreover, smaller organizations may find it difficult to attract and retain top security talent, as they may not be able to offer competitive salaries and benefits.
2. Distributed SOC
A distributed security operations center is a SOC model that consists of multiple, geographically dispersed SOCs working together to provide security services. These SOCs can be located in different regions or countries and are connected through a centralized management system that allows for seamless communication and coordination between them.
Pros: A distributed SOC offers improved threat visibility and detection. By having multiple SOCs monitoring different parts of an organization’s network, it is more likely that threats will be detected and addressed quickly. Additionally, a distributed SOC can help an organization achieve a more comprehensive understanding of global threat trends, as each SOC will have access to information about threats and incidents occurring in its specific region.
Cons: One potential drawback of a distributed SOC is the increased complexity of managing multiple SOCs, as it can be challenging to coordinate and align the efforts of geographically dispersed teams. Additionally, a distributed SOC may require a significant investment in communication and collaboration tools to ensure seamless communication between the different SOCs.
3. Multifunctional SOC/NOC
A multifunctional SOC/NOC is a hybrid model that combines the functions of a security operations center (SOC) and a Network Operation Center (NOC) into a single, unified unit. This model allows for the integration of security and network management tasks, resulting in a more streamlined and efficient approach to securing an organization’s networks and systems.
Pros: A multifunctional SOC/NOC consolidates the security and network management functions, providing greater operational efficiency, as resources can be shared and allocated more effectively. Additionally, a multifunctional SOC/NOC can lead to improved communication and collaboration between security and network teams, which can result in faster and more effective incident response.
Cons: One potential drawback of a multifunctional SOC/NOC is that it may be difficult to find professionals with the skills and expertise needed to manage both security and network operations. Additionally, combining the functions of an SOC and NOC may result in an increased workload for the team, which could lead to burnout and decreased effectiveness.
4. Fusion SOC
A fusion security operations center is an advanced SOC model that integrates various security functions, such as threat intelligence, incident response, and security analytics, into a single, unified platform. This model leverages advanced technologies, such as artificial intelligence and machine learning, to provide a more proactive and sophisticated approach to security.
Pros: A Fusion SOC offers improved threat detection and response capabilities. By leveraging advanced technologies and integrating various security functions, a Fusion SOC can quickly identify and respond to threats, reducing the likelihood of a security breach.
Cons: One potential drawback of a fusion SOC is the cost of implementing and maintaining it. This type of SOC requires significant investment in advanced technologies and skilled security professionals. Moreover, some organizations may not have the necessary resources or expertise to manage a fusion SOC effectively.
5. Command SOC/Global SOC
A command security operations center, also known as a global SOC, is a high-level SOC model that oversees and coordinates the activities of multiple SOCs within an organization. This model is typically used by large, multinational organizations with multiple SOCs located in different regions or countries.
Pros: A command SOC/global SOC provides a comprehensive, global view of an organization’s security posture. By overseeing the activities of multiple SOCs, a Command SOC/Global SOC can identify trends and patterns in security incidents and threats that may not be apparent when looking at the data from a single SOC.
Cons: The cost of implementing and maintaining a Command SOC/Global SOC can be high, as it requires significant investment in technology, infrastructure, and skilled security professionals. Furthermore, managing and coordinating the activities of multiple SOCs can be complex and challenging, particularly for organizations with limited experience in this area.
6. Virtual SOC
A virtual security operations center is a SOC model that leverages cloud-based technologies and remote security professionals to provide security services. Unlike traditional SOCs, a virtual SOC does not require a physical location or dedicated infrastructure, making it a more flexible and cost-effective option for organizations.
Pros: A virtual SOC offers several advantages, particularly for smaller organizations or those with limited resources. By leveraging cloud-based technologies and remote security professionals, a Virtual SOC can provide many of the same benefits as a traditional SOC, such as continuous monitoring and incident response, at a fraction of the cost.
Cons: One potential drawback of a virtual SOC is the reliance on cloud-based technologies and remote security professionals, which may raise concerns about data privacy and security. Additionally, some organizations may prefer the greater control and visibility offered by a traditional, on-premises SOC.
7. Managed SOC/MSSP/MDR
A managed security operations center (Managed SOC), also known as a Managed Security Services Provider (MSSP) or Managed Detection and Response (MDR) service, is a SOC model that involves outsourcing security operations to a third-party provider. This provider is responsible for monitoring, detecting, and responding to security incidents and threats on behalf of the organization.
Pros: A managed SOC/MSSP/MDR provider can be a more cost-effective option for organizations, as it eliminates the need for significant investment in infrastructure, technology, and skilled security professionals. Additionally, a Managed SOC/MSSP/MDR provider can offer access to a wider range of security expertise and resources than an organization may be able to acquire in-house.
Cons: One potential drawback of managed SOC/MSSP/MDR providers is the loss of control over security operations, as the organization will be relying on a third-party provider to manage its security. Additionally, there may be concerns about data privacy and security, particularly when sensitive information is being shared with an external provider.
Security operations center roles and responsibilities
- Security analyst – The first to respond to incidents. Their response typically occurs in three stages: threat detection, threat investigation, and timely response. Security analysts should also ensure that the correct training is in place and that staff can implement policies and procedures. Security analysts work together with internal IT staff and business administrators to communicate information about security limitations and develop documentation.
- Security engineer/architect – Maintains and suggests monitoring and analysis tools. They create a security architecture and work with developers to ensure that this architecture is part of the development cycle. A security engineer may be a software or hardware specialist who pays particular attention to security aspects when designing information systems. They develop tools and solutions that allow organizations to prevent and respond effectively to attacks. They document procedures, requirements, and protocols.
- SOC manager – Manages the security operations team and reports to the CISO. They supervise the security team, provide technical guidance, and manage financial activities. The SOC manager oversees the activity of the SOC team, including hiring, training, and assessing staff. Additional responsibilities include creating processes, assessing incident reports, and developing and implementing crisis communication plans. They write compliance reports, support the audit process, measure SOC performance metrics, and report on security operations to business leaders.
- CISO – Defines the security operations of the organization. They communicate with management about security issues and oversee compliance tasks. The CISO has the final say on policies, strategies, and procedures relating to the organization’s cybersecurity. They also have a central role in compliance and risk management, and implement policies to meet specific security demands.
Learn more in our detailed SOC team guide.
Benefits of security operations centers
- Incident response – SOCs operate around the clock to detect and respond to incidents.
- Threat intelligence and rapid analysis – SOCs use threat intelligence feeds and security tools to quickly identify threats and fully understand incidents, in order to enable appropriate response.
- Reduce cybersecurity costs – Although a SOC represents a major expense, in the long run, it prevents the costs of ad hoc security measures and the damage caused by security breaches.
- Reduce the complexity of investigations – SOC teams can streamline their investigative efforts. The SOC can coordinate data and information from sources, such as network activity, security events, endpoint activity, threat intelligence, and authorization. SOC teams have visibility into the network environment, so the SOC can simplify the tasks of drilling into logs and forensic information, for example.
SOC challenges and how technology can help
- Increased volumes of security alerts – The growing number of security alerts requires a significant amount of an analyst’s time. Analysts may tend to tasks from the mundane to the urgent when determining the accuracy of alerts. They could miss alerts as a result, which highlights the need for alert prioritization. Exabeam Advanced Analytics uses UEBA technology to provide security alert prioritization, which relies on the dynamic analysis of anomalous events. This ensures that analysts can find the alerts requiring the most immediate attention.
- Management of many security tools – As various security suites are being used by SOCs and CSIRTs, it is hard to efficiently monitor all the data generated from multiple data points and sources. A SOC may use 20 or more technologies, which can be hard to keep track of and control individually. This makes it important to have a central source and a single platform. A SIEM serves this function in most SOCs. For an example of a next-generation SIEM solution with advanced analytics and security automation, see the Exabeam Security Management Platform.
- Skills shortage – Short staffing or lack of qualified individuals is an issue. A key strategy for dealing with the cybersecurity skills shortage is automating SOC processes, to save time for analysts. In addition, an organization may decide to outsource.Some organizations are now outsourcing to MSSPs to help them with their SOC services. Managed SOCs can be outsourced entirely or in partnership with on-premises security staff.
Learn about how security technologies are helping solve SOC challenges in our guide: The SOC, SIEM, and Other Essential SOC Tools
Getting started with a SOC
Questions to ask before setting up a SOC
- Availability and hours – Will you staff your SOC 8×5 or 24×7?
- Format – Will you have a standalone SOC or an integrated SOC and NOC?
- Organization – Do you plan to control everything in house, or will you use an MSSP?
- Priorities and capabilities – Is security the core concern, or is compliance a key issue? Is monitoring the main priority, or will you need capabilities such as ethical hacking or penetration testing? Will you make extensive use of the cloud?
- Environment – Are you using a single on-premises environment or a hybrid environment?
5 steps to setting up your SOC
- Ensure everyone understands what the SOC does – A SOC observes and checks endpoints and the organization’s network, and isolates and addresses possible security issues. Create a clear separation between the SOC and the IT help desk. The help desk is for employee IT concerns, whereas the SOC is for security issues related to the entire organization.
- Provide infrastructure for your SOC – Without the appropriate tools, a SOC team will not be able to deal with a security threat. Evaluate and invest in tools and technologies that will support the effectiveness of the SOC and are appropriate for the level of expertise of your in-house security team. See the next section for a list of tools commonly used in the modern SOC.
- Find the right people – Build a security team using the roles listed above: security analysts, security engineers, and a SOC manager. These specialists should receive ongoing training in areas such as reverse engineering, intrusion detection, and malware anatomy. The SOC manager needs to have strong security expertise, management skills, and battle-tested crisis management experience.
- Have an incident response plan ready – An incident response team should create a specific and detailed action plan. The team can also create a repeatable plan that can be used over time and adapt to different threat scenarios. Business, PR, and legal teams may also be involved if needed. The team should adhere to predefined response protocols so they can build on their experience.
- Defend – A key responsibility of the SOC is to protect the perimeter with a dedicated team focused on detecting threats. The SOC’s goal is to collect as much data and context as possible, prioritize incidents, and ensure the important ones are dealt with quickly and comprehensively.
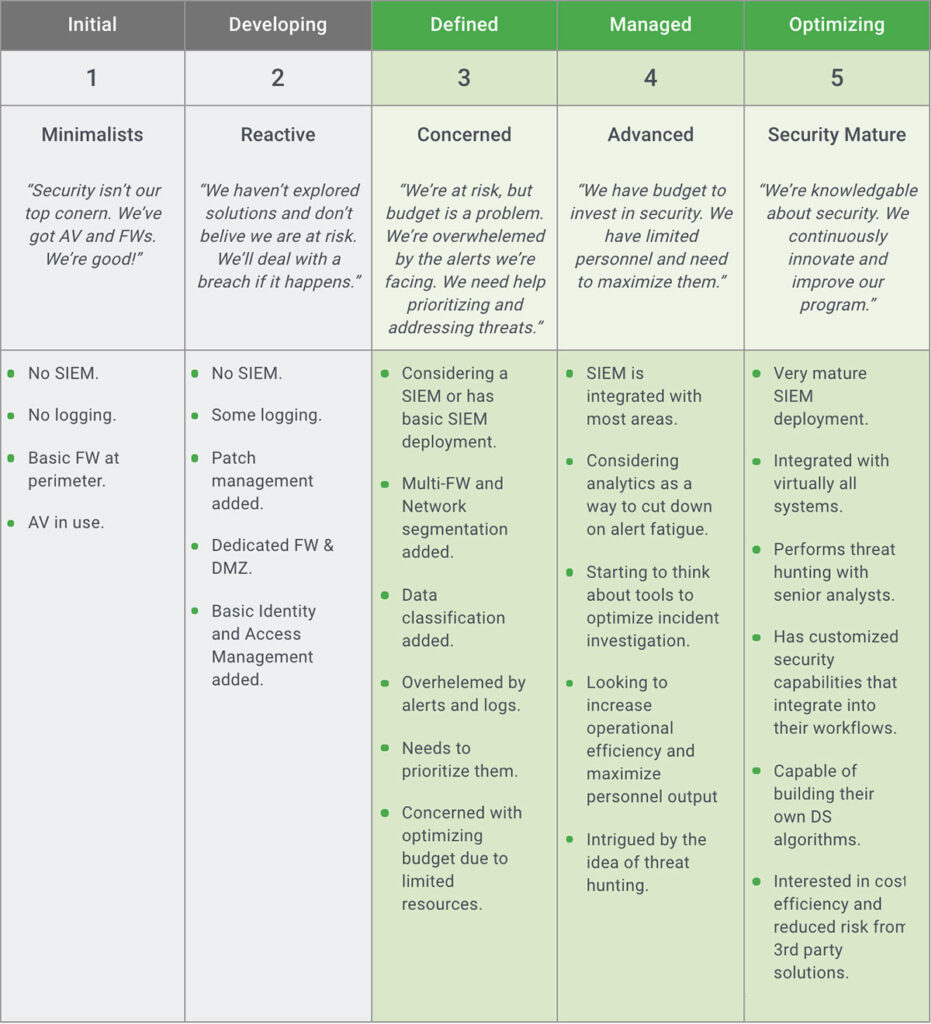
The security maturity spectrum — Are you ready for a SOC?
A SOC is an advanced stage in the maturity of an organization’s security. The following are drivers that typically push companies to take this step:
- Requirements of standards such as the Payment Card Industry Data Security Standard (PCI DSS), government regulations, or client requirements
- The need for the business to secure very sensitive data
- Past security breaches and/or public scrutiny
- Type of organization — For example, a government agency or Fortune 500 company will almost always have the scale and threat profile that justifies a SOC, or even multiple SOCs.
Different organizations find themselves at different stages of developing their security stance. We define five stages of security maturity. In stages 4 and 5, an investment in a security operations center becomes relevant and worthwhile.
The future of the SOC
The security operations center is undergoing an exciting transformation. It is integrating with ops and development departments, and is empowered by powerful new technologies, while retaining its traditional command structure and roles to identify and respond to critical security incidents.
We showed how SIEM is a foundational technology of the SOC, and how next-generation SIEMs, which include new capabilities like behavioral analytics, machine learning, and SOC automation, open up new possibilities for security analysts.
The impact of a next-gen SIEM on the SOC can be significant. It can:
- Reduce alert fatigue via user and entity behavior analytics (UEBA) that goes beyond correlation rules, helps reduce false positives, and discover hidden threats.
- Improve MTTD by helping analysts discover incidents faster and gather all relevant data.
- Improve MTTR by integrating with security systems and leveraging Security Orchestration, Automation and Response (SOAR) technology.
- Enable threat hunting by giving analysts fast and easy access and powerful exploration of unlimited volumes of security data.
Exabeam is an example of a next-generation SIEM which combines data lake technology, visibility into cloud infrastructure, behavioral analytics, an automated incident responder, and a threat hunting module with powerful data querying and visualization.
See Additional Guides on Key Information Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of information security.
Insider Threat
Authored by Exabeam
- What is an Insider Threat? 4 Defensive Strategies
- How to Find Malicious Insiders: Tackling Insider Threats Using Behavioral
Indicators - Insider Threat Programs: 8 Tips to Build a Winning Program
Mitre Att&ck
Authored by Exabeam
Disaster Recovery
Authored by Cloudian
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!











