What is a SOC team?
A security operations center — commonly referred to as a SOC — is a team that continuously monitors and analyzes the security procedures of an organization. It also defends against security breaches and actively isolates and mitigates security risks.
There are five key roles on a SOC team:
- Security analysts are cybersecurity first responders. They report on cyberthreats and implement any changes needed to protect the organization. They’re considered the last line of defense against cybersecurity threats, work alongside security managers and cybersecurity engineers, and usually report to the CISO..
- Security engineers are usually software or hardware specialists, and are in charge of maintaining and updating tools and systems. They are also responsible for any documentation that other team members might need, such as digital security protocols.
- The SOC manager is responsible for the SOC team. They direct SOC operations and are responsible forsyncing between analysts and engineers; hiring; training; and creating and executing on cybersecurity strategy. They also directand orchestrate the company’s response to major security threats.
- The chief information security officer (CISO) is a leadership position responsible for establishing security-related strategies, policies, and operations. They workclosely with the CEO, and inform and report to management on security issues.
- The director of incident response (IR) is a role in larger security organizations that isresponsible for managing incidents as they occur, and communicating security requirements to the organization in the case of a significant data breach.
In this article, you will learn:
- SOC roles and responsibilities
- SOC team vs. CSIRT – What is the difference?
- How to determine if you need a SOC team, CSIRT team, or both?
- Best practices for building a winning SOC team
- Measuring SOC team
SOC roles and responsibilities
SOC analysts are organized in four tiers. First, SIEM alerts flow to Tier 1 analysts who monitor, prioritize and investigate them. Real threats are passed to a Tier 2 analyst with deeper security experience, who conducts further analysis and decides on a strategy for containment.
Critical breaches are moved up to a Tier 3 senior analyst, who manages the incident and is responsible for actively hunting for threats continuously. The Tier 4 analyst is the SOC manager, responsible for recruitment, strategy, priorities, and the direct management of SOC staff when major security incidents occur.
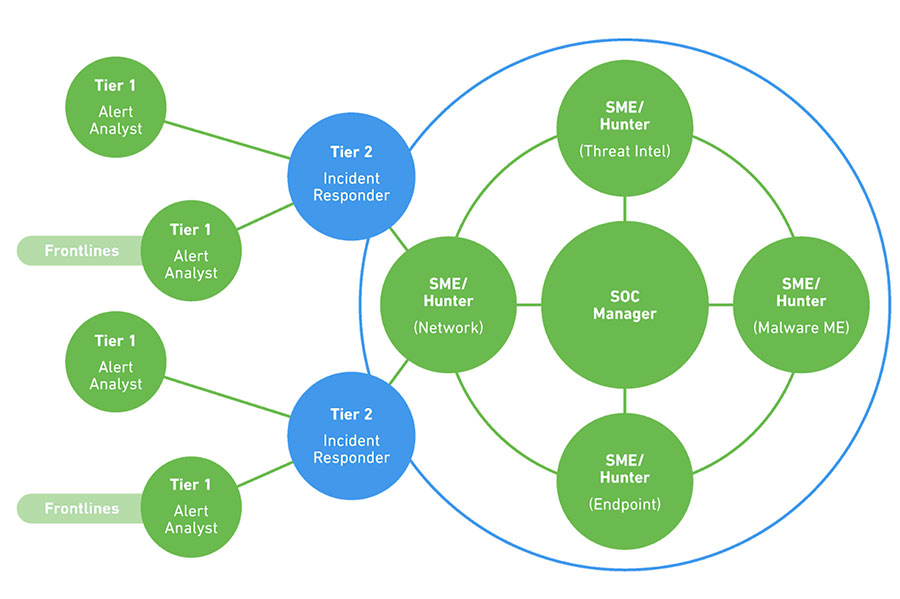
The table below explains each SOC role in more detail.
| Role | Qualifications | Duties |
|---|---|---|
| Tier 1 AnalystAlert Investigator | System administration skills; web programming languages, such as Python, Ruby, PHP; scripting languages; security certifications such as CISSP or SANS SEC401 | Monitors SIEM alerts, manages and configures security monitoring tools. Prioritizes and triages alerts or issues to determine whethera real security incident is taking place. |
| Tier 2 AnalystIncident Responder | Similar to Tier 1 analyst, but with more experience including incident response. Advanced forensics, malware assessment, threat intelligence. Ethical hacker certification or training is a major advantage. | Receives incidents and performs deep analysis; correlates with threat intelligence to identify the threat actor, nature of the attack, and systems or data affected. Defines and executes on strategy for containment, remediation, and recovery. |
| Tier 3 AnalystSubject Matter Expert/Threat Hunter | Similar to Tier 2 analyst but with even more experience, including high-level incidents. Experience with penetration testing tools and cross-organization data visualization. Malware reverse engineering, experience identifying and developing responses to new threats and attack patterns. | Day-to-day, conducts vulnerability assessments and penetration tests, and reviews alerts, industry news, threat intelligence, and security data. Actively hunts for threats that have madetheir way into the network, as well as unknown vulnerabilities and security gaps. When a major incident occurs, teams with the Tier 2 Analyst in responding to and containing it. |
| Tier 4 SOC ManagerCommander | Similar to Tier 3 analyst, including project management skills, incident response management training, and strong communication skills. | Like the commander of a military unit, responsible for hiring and training SOC staff, in charge of defensive and offensive strategy. Manages resources, priorities and projects, and manages the team directly when responding to business-critical security incidents. The organization’s point of contact for security incidents, compliance, and other security-related issues. |
| Security EngineerSupport and Infrastructure | Degree in computer science, computer engineering or information assurance, typically combined with certifications like CISSP. | A software or hardware specialist who focuses on security aspects in the design of information systems. Creates solutions and tools that help organizations deal robustly with disruption of operations or malicious attacks. Sometimes employed within the SOC, and sometimes supportsthe SOC as part of development or operations teams. |
SOC Team vs. CSIRT – What is the Difference?
A computer security incident response team (CSIRT), also called CERT or CIRT, is responsible for receiving, analyzing, and responding to security incidents. CSIRTs can work under SOCs or can stand alone.
What differentiatesa CSIRT from a SOC? While the core function of a CSIRT is to minimize and manage damage caused by an incident, the CSIRT does not just deal with the attack itself; they also communicate with clients, executives, and the board.
How to determine whether you need a SOC team, CSIRT, or both?
The case for a single entity
Often, it’s desirable to have a single entity that unites the SOC and CSIRT. Why? Because the distinction between detection and response is not clear cut, and may even become irrelevant. For example, threat hunting is used to identify threats, but also operates as a method of response.
Both SOC teams and CSIRTsuse security orchestration, automation and response (SOAR) tools, which could indicate that these teams need to be merged, as it is not always clear who owns the tool and is accountable for its evolution. Threat intelligence (TI) related activities also provide a case for having a single entity. A single TI consumption position can offer insights into identification and response methods.
Another reason to unite these groups is related to managing the workforce. One problem with SOCs is that it is difficult to keep Tier 1 analysts motivated, particularly when they work nights and weekends. By bringing incident response and threat hunting together, you create the option for job rotation.
The case for separate entities
Some industry experts argue that keeping SOC teams and CSIRTsseparate allowsthem to concentrate on their core objectives, namely detection vs. response. Also, occasionally multiple SOCs are required because of multiple regional offices or subsidiaries, yet organizations wish to keep incident response centralized due to the sensitivity of investigation results.
Strategic plans for outsourcing may demand the separation of these two functions. Today, this may not be an issue, as many SOCs operate as hybrid organizations. However, keeping SOC and CSIRT separate may help an organization clearly define the responsibilities of a partner.
Best Practices for Building a Winning SOC Team
Security operations teams face many challenges: they can be overworked, understaffed, and often gain little attention from upper management. Security operations best practices can give companies the tools they need to protect themselves and offer SOC teams a better working environment.
- Efficient SOCs use security automation – By using highly-skilled security analysts alongwith security automation, organizations can analyze more security events, identify more incidents, and protect against those incidentsmore effectively.
- Use effective technology – The abilities of your SOC are dependent on its technology capabilities. Technology should collect and aggregate data, prevent threats, and respond as the threats occur. A team that is equipped with tools and data sources that reduce false positives to a minimum can maximize the time analysts spend investigating real security incidents. Learn more in our detailed guide about the SOC, SIEM, and other tools used in a modern SOC.
- Be up to date with current threat intelligence – Threat intelligence data from within the organization, in conjunction with information from external sources, provides insight into vulnerabilities and threats to the SOC team. External cyber intelligence includes signature updates, news feeds, incident reports, vulnerability alerts, and threat briefs. SOC staff can leverage SOC monitoring tools that provide integrated threat intelligence.
- People and responsibilities – Organizations often share administrative duties across subsidiaries, and between partner organizations and business units. The organization’s security policy standards should be used to define responsibilities in relation to tasks and accountability for response. An organization can also define the role of each business unit or agency in relation to the SOC.
- Defend the perimeter – A key responsibility of a SOC team is to defend the perimeter, but what information are analysts required to gather? Where can they find that information?
The SOC team can take into account all data input, for example:
- Network information, such as URLs, hashes, and connection details
- The monitoring of endpoints, vulnerability information revealed by scanners, security intelligence feeds, intrusion prevention (IPS), and detection (IDS) systems
- Operating systems
- Topology information
- External-facing firewall and antivirus
Measuring SOC Teams
Organizations need to measure the performance of SOC teams to continuously improve their processes. Here are a few important metrics that can help demonstratethe scale of activity in the SOC, and how effectively analysts are handling the workload.
| Metric | Definition | What it Measures |
|---|---|---|
| Mean Time to Detection (MTTD) | Average time the SOC takes to detect an incident | How effective the SOC is at processing important alerts and identifying real incidents |
| Mean Time to Resolution (MTTR) | Average time that transpires beforethe SOC takes action and neutralizes the threat | How effective the SOC is at gathering relevant data, coordinating a response, and taking action |
| Total cases per month | Number of security incidents detected and processed by the SOC | How busy the security environment is and the scale of action the SOC is managing |
| Types of cases | Number of incidents by type: web attack, attrition (brute force and destruction), email, loss or theft of equipment, etc. | The main types of activity managed by the SOC, and where preventative security measures should be focused |
| Analyst productivity | Number of units processed per analyst — alerts for Tier 1, incidents for Tier 2, threats discovered for Tier 3 | How effective analysts are at covering maximum possible alerts and threats |
| Case escalation breakdown | Number of events that enter the SIEM, alerts reported, suspected incidents, confirmed incidents, escalated incidents | The effective capacity of the SOC at each level and the workload expected for different analyst groups |
Key Takeaways:
- Modern SOCs require cooperation and collaboration between development, operations, and security teams. Increasingly complex infrastructures and the speed of agile processes require capabilities that security teams cannot achieve on their own.
- Effective security tools should support all steps of the incident response process. Centralizing information, providing fast analyses, and supporting in-depth investigations are key.
- Metrics can help you evaluate the effectiveness of your SOC processes when used carefully. Make sure to incorporate metrics results into evaluation and refinement processes.
Learn More about Security Operations Centers
See our additional guides about key SOC topics:
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!











