What Is Threat Intelligence?
Threat intelligence is knowledge about security threats, threat actors, exploits, malware, vulnerabilities, and compromise indicators (according to SANS) that can help bolster your SIEM security. The more aware you are of possible threats, and the more details you have about their mode of operations, capabilities, infrastructure, motives, and goals, the better you are equipped to defend your organization.
With the growth in cybercrime and the huge proliferation of attackers and attack types, threat intelligence has become an industry. Commercial providers operate research bodies and sell threat intelligence feeds based on their research. Government institutes and independent research bodies also provide threat intelligence feeds with valuable data, typically open for use. And there are threat intelligence tools which help organizations receive, organize and act upon all this information.
In this post you will learn about:
- Why threat intelligence is important
- The four layers of threat intelligence
- Sources of threat intelligence
- Threat intelligence feeds
- The importance of open source threat intelligence feeds
- Threat intelligence tools
- Challenges of threat intelligence
Why is Threat Intelligence Important?
Threat intelligence enables you to understand and track conditions in the cybersecurity landscape. New attack techniques, malware tools, and threat actors are constantly developing. If you are unaware of these developments, it is difficult to anticipate how you might be attacked or where your vulnerabilities lie.
By integrating threat intelligence into your security practices you can:
- Ensure security relevance—having up to date threat intelligence can help you ensure that your security efforts are prioritized appropriately. This includes understanding what threats currently exist, what techniques are being used, and who is being targeted.
- Gain attacker insight—understanding the methods and goals of attackers can help you predict their behavior both in and outside your systems. This can help you track down intruders more quickly and better anticipate where vulnerabilities lie.
- Improve security tools and strategies—you can use threat intelligence to train your security teams and grow their expertise. You can also use it to inform the creation of stronger policies and tools for protecting your systems.
The 4 Layers of Threat Intelligence
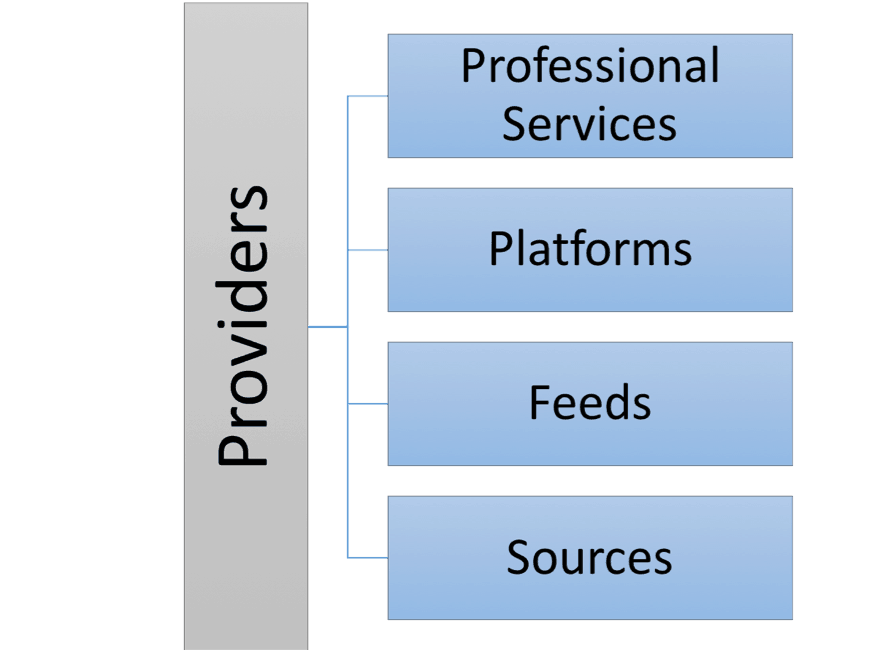
Figure 1 – Threat intelligence is made up of four layers, which help organizations ingest and make use of threat data.
From bottom to top in the diagram above:
- Sources—raw data about security incidents and threats
- Feeds—raw data packaged into a standardized format which enables real time streaming of new events, around a certain security theme
- Platforms—a system that helps an organization receive data from multiple feeds, correlate it with internal data, manage it and derive insights
- Professional services—in many cases threat intelligence providers go beyond supplying data and software, they also provide experts who can help their customers review threat data and identify pertinent information
A threat intelligence provider is a commercial body that provides some or all of the four layers. We list some of the leading tools in the tools section below.
Sources—Where Does Threat Intelligence Come From?
A threat intelligence source is the raw data, which can be parsed, analyzed and packaged to create an intelligence feed. Organizations should have their own sources, and not base all their knowledge on external providers.
There are many other important sources of threat data which organizations typically cannot access or consume on their own—they rely on feeds provided by others in the industry.
A few examples of sources available directly to security staff at organizations:
- In-house threat analytics—based on network monitoring and data about past incidents from incident response and Security Operations Center (SOC) teams
- Professional communities—such as a Financial Services Information Sharing and Analysis Center (FS-ISAC) for financial security pros
- Security news and blogs—reading security publications and being aware of current attacks and exploits in your industry is an excellent source of threat intelligence
- The dark web—many security professionals dive into the dark web of underground forums to identify stolen assets, learn who threat actors are targeting, analyze exploit kits, and so on (proceed with caution)
There are six primary sources of data used by public or commercial threat intelligence feeds:
- Open source—open data collected and shared among security professionals
- Customer telemetry—information collected from security companies operating tools across many organizations
- Dark web and honeypots—obtaining intelligence directly from attackers
- Scanning and crawling—systematically crawling the internet to find exploits, attacks, or malicious entities
- Malware processing—identifying malware and running it in a safe sandbox environment to understand its properties
- Human intelligence—analysts investigating incidents and discovering vulnerabilities through exploration
Feeds: Packaged Threat Intelligence for the Masses
A threat intelligence feed is a packaged collection of data, taken from a variety of sources, typically falling into one or more of the six sources we list above. Most feeds focus on one area of interest, such as domains, malicious IP addresses, or botnet activity. Many security feeds are freely available; others require paid subscriptions.
Threat intelligence feeds stream information in real time—as soon as a new threat or malicious entity is discovered, the information is packaged into the feed format and streamed to subscribers. Time is of the essence, because a primary goal of users is to become aware of threats and defend against imminent attacks before they happen.
Security professionals use feeds by:
- Coupling them to security tools—for example, some firewalls can accept feeds about bad IP addresses and can block those IP addresses.
- Using them to generate alerts—for example, threat intelligence feed data can be saved to a Security Information Event Management (SIEM) or User Event Behavioral Analytics (UEBA) solution, which can correlate threat data with internal security events, and generate alerts when threats are relevant for your organization.
- Manual review—many security professionals receive threat intelligence feeds and review them manually, investigating threats that seem relevant to their security posture.
Here are a few lists of important threat intelligence feeds:
- Lists of threat intelligence feeds by commercial providers
- List of cyber intelligence data provided by governments
The Importance of Open Source Threat Intelligence Feeds
Knowledge sharing in the security community is extremely important. Most organizations that experience breaches might take a long time to discover the breach, and even then, may not publicly report it. Open source threat intelligence databases encourage organizations to contribute information about security threats to the public domain.
The following diagram illustrates how, without open data sharing, multiple organizations may be targeted by the same attacker, and each must detect and respond to the attack independently. By using (and contributing to) an open source threat database, once one organization is attacked, everyone is aware of the risk and able to easily identify and defend against the attacker.
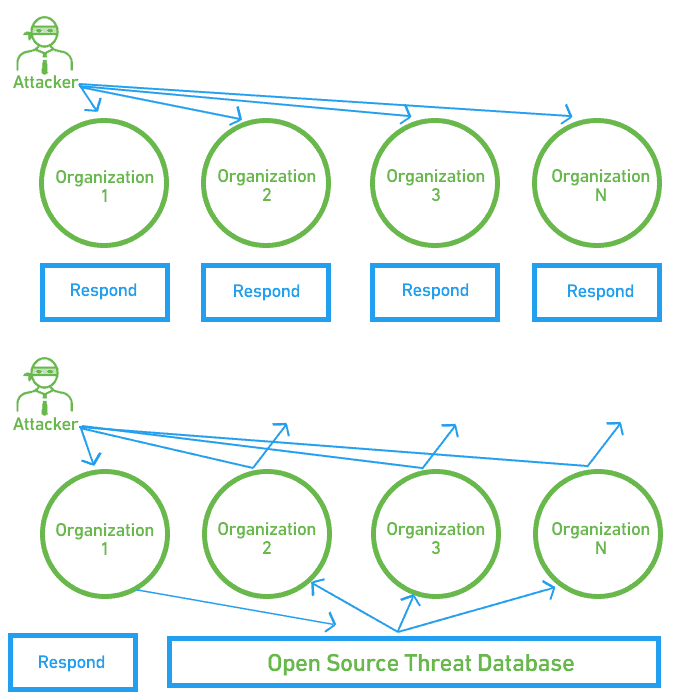
Figure 2 – Attack response with and without threat intelligence
The following are popular open source threat intelligence feeds:
- Department of Homeland Security Automated Indicator Sharing—compiled using data shared by private companies with the DHS
- FBI Infragard Portal—organized according to 16 sectors of critical infrastructure
- SANS Internet Storm Center—uses a sensor network that collects 20 million log entries per year from thousands of organizations
- Cisco Talos Intelligence—a commercial threat database used by Cisco customers, but has a free version available which makes the data publicly accessible
- Google Safe Browsing—a service that flags malicious websites compromised by hackers and makes the data publicly available
- Spamhaus Project—a non-profit organization that maintains comprehensive blacklists for known spammers and malware distributors
Threat Intelligence Tools
Threat intelligence tools help organizations take in, store, analyze, organize and compare multiple threat intelligence feeds. A threat intelligence tool combines all your feeds into one, correlates them with internal security events, and creates prioritized alerts for security analysts to review. A SIEM, while it has many other uses, also functions as a threat intelligence platform.
A few popular threat intelligence tools include:
- Palo Alto Networks AutoFocus—threat intelligence service with threat analytics. Provides intelligence, correlation, added context and automated prevention workflows.
- Anomali ThreatStream—helps identify new attacks by collecting millions of threat indicators. Helps deduplicate data, remove false positives, and feeds intelligence to security tools.
- ThreatQuotient—helps accelerate security operations with an integrated threat library, shared contextual intelligence that empowers security teams, and customizable workflows combining human and automated threat detection.
- ThreatConnect—combines external threat data from trusted sources with in-house data, provides analytics showing the impact of security efforts and the most relevant threats to your organization.
Challenges of Threat Intelligence
Threat intelligence has proven to be extremely valuable in helping defend against cyber attacks. However, there are several common difficulties experienced when managing it:
- Too much data—analysts are drowning in alerts and data. Feeds only add large volumes of data to this mix. Without effective workflows and prioritization, data can become overwhelming and lead to alert fatigue.
- Selecting the wrong feeds—helps identify new attacks by collecting millions of threat indicators. Helps deduplicate data, remove false positives, and feeds threat intelligence to security tools.
- Context—threat intelligence often provides pertinent information, but without the relevant context. How important is a threat to your security posture? Have you or organizations in your neighbourhood been hit by this attack? Which current events may be correlated with this attack signature?
- Process and skills—threat intelligence feeds are not useful on their own; they require trained analysts to turn them into actionable insights for the organization. Many organizations do not have enough analysts available to review all relevant feeds and alerts, or do not have an efficient process in place to proactively discover new threats, leveraging threat intelligence data.
- Workflow—when analysts get an Indicator of Compromise (IoS) via a threat intelligence feed, they commonly need to leave the solution to investigate and respond to the event via other tools. This erodes analyst productivity. Platforms are introducing automated workflows and orchestration to help streamline the analyst workflow.
Leveraging Next-Gen SIEM to Put Threat Intelligence to Real Use
Next generation SIEM platforms, like Exabeam’s Security Management Platform, can help organizations effectively consume threat data, and put it to use.
Next generation SIEMs include several capabilities that can improve the effectiveness of your threat intelligence operation:
- Advanced analytics—using behavioral analytics to identify anomalous behavior that might indicate an attack, and correlating with threat analytics data to identify the type and source of the attack.
- Smart forensic analysis—collecting all relevant information about a security incident, across multiple users, IP addresses and IT systems, combining it with threat intelligence data, and laying it out on an incident timeline. This provides context that is sorely missing in traditional systems.
- Incident response automation—gathering data from hundreds of tools, automatically identifying incidents, referencing them with threat intelligence data, and even automatically orchestrating containment and mitigation steps.
- Threat hunting—using threat intelligence data, combined with free exploration of internal data, to identify new and unknown threats that might be affecting your organization.
Modern SIEMs that are designed to work with threat intelligence from the ground up, can provide data exactly where and when you need it. This dramatically improves productivity compared to most traditional intelligence tools, which require analysts to extract threat data and go to other tools to respond to the event or incident.
For more on threat intelligence, read our blog post about boosting the effectiveness of threat intelligence with next gen SIEM.
To learn more about Exabeam’s Threat Intelligence Service, read our blog about how to Enable Smarter Workflows Using Exabeam Threat Intelligence Service.
Learn more about SIEMs
- What is SIEM?
- SIEM Architecture
- Events and Logs
- UEBA
- SIEM Use Cases
- SIEM Analytics
- The SOC, SecOps and SIEM
- Incident Response and Automation
Want to learn more about SIEM Security?
Have a look at these articles:
- A SIEM Security: Primer: Evolution and Next-Gen Capabilities
- 7 Open Source SIEMs: Features vs. Limitations
- SIEM Solutions: How They Work and Why You Need Them
- Combating Cyber Attacks With SOAR
- Battling Cyber Threats Using Next-Gen SIEM and Threat Intelligence
- Threat Intelligence Feeds: Keeping Ahead of the Attacker
- How a Threat Intelligence Platform Can Help You
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













