Read The 4 Layers of Threat Intelligence where we provide background information to help you better understand TIS.
– Chuck Palahniuk, Fight Club author, American novelist, and freelance journalist
“SIEM and threat intelligence (TI) feeds are a marriage made in heaven,” says Anton Chuvakin, Gartner Research VP and Distinguished Analyst. “Indeed, every SIEM user should send technical TI feeds into their SIEM tool.”
Security operation center (SOC) managers certainly know their security analysts spend an enormous amount of time sifting through information and alerts across a variety of non-integrated tools, trying to find the data they need to investigate potential threats.
Consider all the steps in a typical analyst workflow:
- Review a suspicious finding in their SIEM.
- Visit their threat intelligence platform to learn more about it.
- Return to the SIEM, pivot, and query to gather more evidence.
- If an incident is found to be critical, the analyst must perform a full investigation, involving even more querying and pivoting.
- Afterwards analysts can finally respond to the security incident.
Keep in mind all of this is a manual, time consuming process that requires using third-party point products. This results in disjointed workflows, leading to decreased efficiency and missed alerts.
The challenges of legacy threat intelligence
While traditional threat intelligence can be helpful with defending against cyberattacks, there are a lot of issues trying to manage a manual process:
- Too much data—Without effective workflows and prioritization, large volumes of data can become overwhelming. Analysts soon face alert fatigue.
- Lacks context—Too often threat intelligence provides pertinent information, but without the needed context. How important is a threat to your security? Have others been hit by this attack? Which other events may be correlated with its signature?
- Requires advanced processes and skills—TI feeds aren’t useful on their own; rather, they require trained analysts to turn them into actionable insights. But many organizations don’t have enough analysts to review all the relevant feeds and alerts. Or, they don’t have an efficient process in place to proactively discover new threats.
- A less productive workflow—When analysts get an indicator of compromise (IoC) through a basic threat intelligence feed, they need to shift away from their current tool to investigate and respond to the event by using other tools. This erodes analyst productivity.
Enable Smart Workflows with Exabeam Threat Intelligence Service
Integrating many complex and disparate cybersecurity tools and processes into a single, robust platform, Exabeam Threat Intelligence Service aggregates all the relevant security events across your network, providing the needed context—for faster, more effective threat investigations.
Exabeam Threat Intelligence Service provides the following:
- Natively integrated threat intelligence
Many other vendors only provide the threat intelligence infrastructure such as the STIX™ (Structured Threat Information Expression) and TAXII™ (Trusted Automated eXchange of Indicator Information) to bring feeds into the system. Exabeam Threat Intelligence Service fully integrates a natively curated TI feed using SIEM, UEBA, and SOAR workflows within its security management platform.
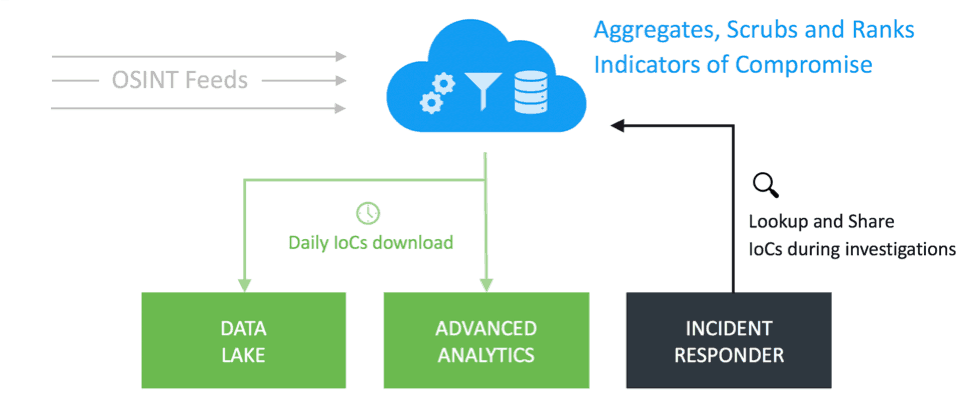
Figure 1 – Natively integrated threat intelligence for the entire Exabeam Security Management Platform
In addition, with its integrated contextual approach, Exabeam provides all the relevant information in a single UI. For example, alerts fired from threat intelligence data automatically create incident timelines listing all the indicators of compromise (IoC) and the surrounding context, as shown in Figure 2. This eliminates the need for analysts to continually toggle back and forth between various third-party tools, i.e. the “swivel-chair” incident response.
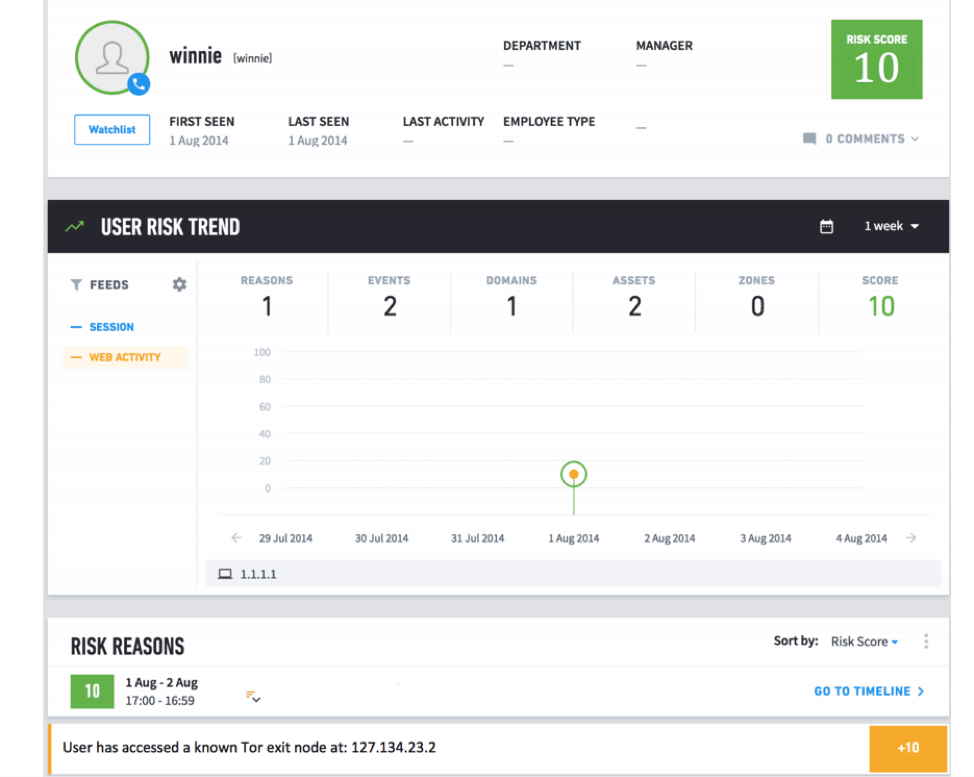
Figure 2- Alerts fired from TIS automatically create incident timelines listing the IoCs.
According to Ponemon Institute[1] research, around 30 percent of respondents weren’t satisfied with their legacy SIEM intelligence due to all the complexity.
Exabeam Threat Intelligence Service (TIS) is very easy to use. Now analysts can leverage known malicious IP addresses, domain reputation, and other indicators of compromise without needing to install apps, write scripts, or alter workflows. This ensures that the feeds analysts choose are easy to deploy. It also doesn’t require additional operational talent, which increases threat detection time.
With Exabeam Advanced Analytics, TIS can be easily used with rules. Your SOC team can easily search through and select the rules they need. For example, Figure 3 shows a rule using TIS in Exabeam Advanced Analytics.
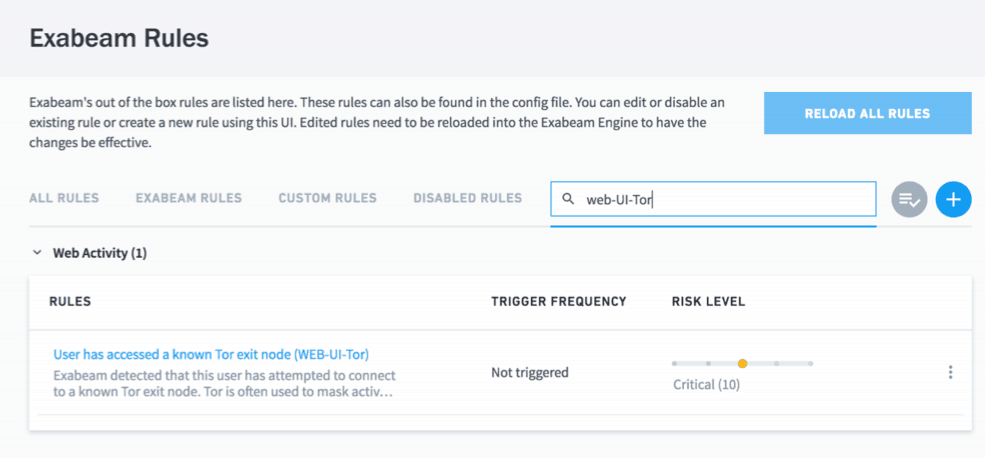
Figure 3 – Using TIS in Exabeam Advanced Analytics through rules.
You can also see additional details on how TIS is set up by clicking the rule (Figure 4).
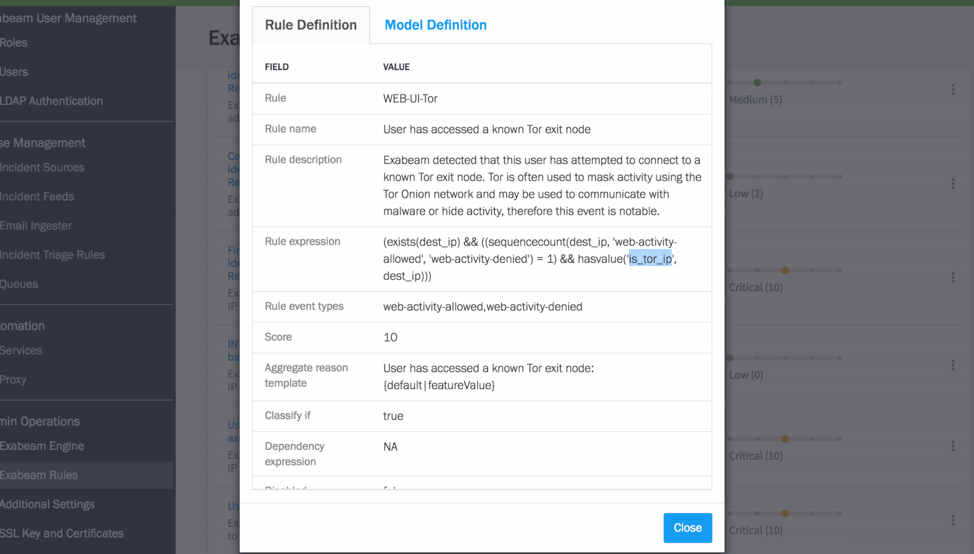
Figure 4 – Exabeam Advanced Analytics showing details of a rule that uses TIS
In Incident Responder, you can take advantage of Exabeam’s Threat Intelligence Service by triggering Incident Response playbooks as shown in Figure 5.
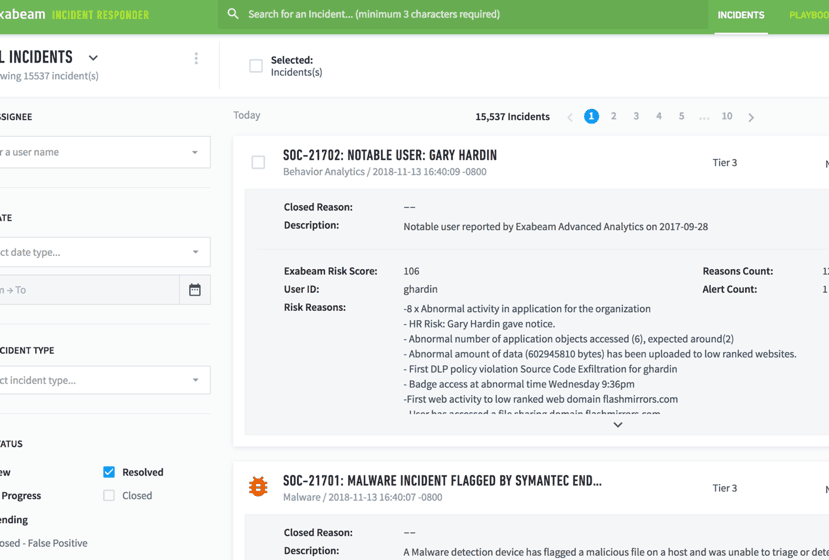
Figure 5 – A threat intelligence value triggering a playbook in Incident Responder.
With Exabeam Data Lake, you can enrich the logs ingested with these threat indicators by appending or inserting new fields.
- Highly accurate feeds of malicious IoCs for use in threat detection
Exabeam Threat Intelligence Service delivers a constant stream of up-to-date threat indicators to the Exabeam Security Management Platform. The result is more accurate correlation rules and behavioral analysis models, with more detailed forensic data, which can be found in automated response playbooks. IoC categories include:
- IP addresses associated with ransomware or malware attacks
- IP addresses associated with the TOR network
- Domain names associated with ransomware, phishing, or malware attacks
Exabeam Threat Intelligence Service is a preconfigured out-of-the-TI-box solution that provides new security capabilities at no added cost or impact to the customer. With Exabeam’s threat intelligence feed directly integrated with your current SIEM, security teams can now have the most up-to-date threat intelligence—enabling them to quickly identify and mitigate new and emerging attacks.
[1] Ponemon Institute report, Challenges to Achieving SIEM Optimization
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













