SIEM Tools Explainers:
Best SIEM Solutions: Top 10 SIEM systems and How to Choose
Understand how SIEM systems can help protect your business and learn about some of the top SIEM solutions.
SIEM solutions provide a consolidated view of security events, making them an essential component of SIEM solutions provide a consolidated view of security events, making them an essential component of cybersecurity. This article is relevant for anyone who does not fully understand how SIEM security solutions work and why they are such a crucial component of cybersecurity. We will discuss the main advantages of using SIEM systems as well as some of the top SIEM vendors and why their products are unique.
What is SIEM and How Does it Work?
Security information and event management (SIEM) is a threat detection system that centralizes security alerts coming from various sources for review and action, and creates compliance reports.
SIEM solutions use data aggregation and data normalization to provide an integrated view of all security events in a single platform. Users can detect threats in real time and security analysts no longer need to waste time searching for all the notifications generated by different threat hunting and monitoring components.
In addition to SIEM, security personnel can define regular and abnormal activity using rules. More advanced solutions, called Next-Gen SIEMs, offer Machine Learning and AI to continuously update user and entity behavior analytics (UEBA) behavioral models to reduce false positives. In Next-Gen SIEMs the data collected by the SIEM system is analyzed relative to the defined rules and identified behavioral patterns. Any time abnormal activity is detected, a notable event is generated for review.
SIEM solutions provide customized cybersecurity protection based on predetermined rules, security event correlations and machine learning. They also store log data over time, making it easy to search for historical information and generate compliance reporting.
Top 10 SIEM Solutions
SIEM has become a basic component of cybersecurity. However, not all SIEM solutions are created equal. When deciding on which SIEM to adopt, it is important to keep in mind that SIEM is not an isolated solution but should be part of a larger security strategy. Some of the top SIEM solutions are listed below.
The information on SIEM solution capabilities and drawbacks was sourced from Gartner Peer Insights and other publicly available sources.
Exabeam Fusion
As a next-gen SIEM, Exabeam Fusion is a cloud-delivered solution that uses a behavior-based approach for Threat Detection, Investigation, and Response (TDIR). By aggregating all relevant events and weeding out illegitimate events, Fusion SIEM boosts analyst productivity and detects threats missed by other tools. This improves detection rates and response time, and ensures that all alerts are considered — even those coming from “noisy” systems that generate many alerts.
In addition, Fusion SIEM is natively integrated with its security orchestration and automation (SOAR) solution, which provides automated incident response. This enables almost any threat to be dealt with automatically (or semi-automated if preferred) in real time. Prescriptive workflows and pre-packaged use-case content (external threats, compromised insiders, and malicious insiders), enable successful SOC outcomes and response automation. Fusion SIEM also provides the cloud-based log storage, rapid and guided search, and comprehensive compliance reporting expected of any modern SIEM.
Splunk

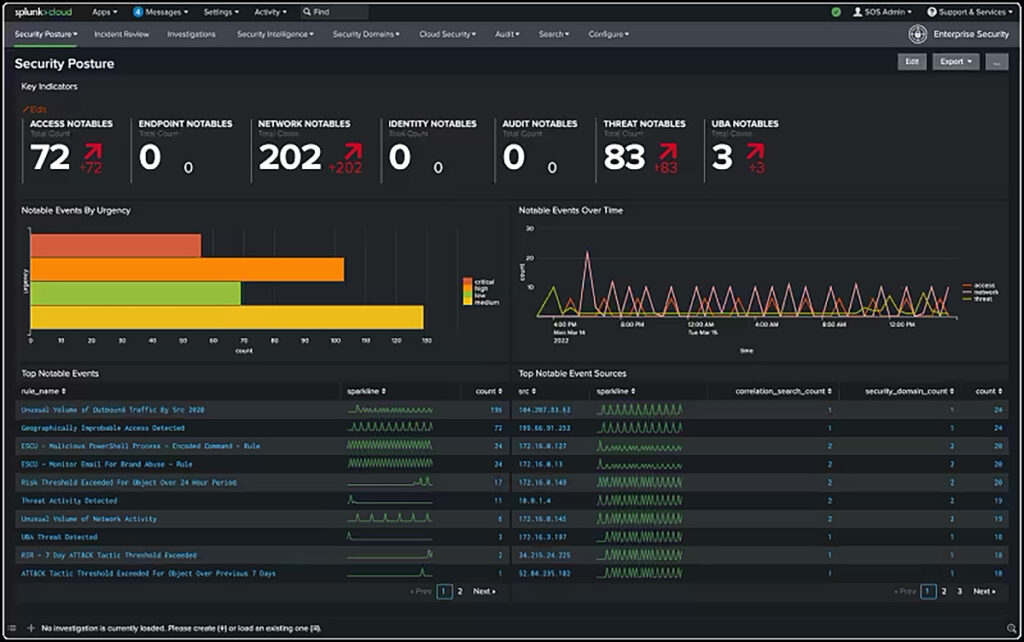
Splunk has a popular SIEM solution. What sets it apart from other vendors is its ability to handle both security as well as application and network monitoring use cases. This makes it popular with both security personnel as well as IT operations users. Like most top SIEM solutions, Splunk’s SIEM provides information in real time, and the user interface is relatively user-friendly. Pricing is based on workloads protected.
However, Splunk Enterprise Security has limited integrated behavioral analytics and automation capabilities which creates a challenge detecting advanced threats and techniques such as lateral movement. The solution requires significant customization to be effective for most organizations and cannot be used “out of the box”. To detect lateral movement, many custom queries need to be run by a specialized user, potentially resulting in a large number of false positives. One other challenge users report is a lack of integration across products: SIEM, SOAR, UEBA.
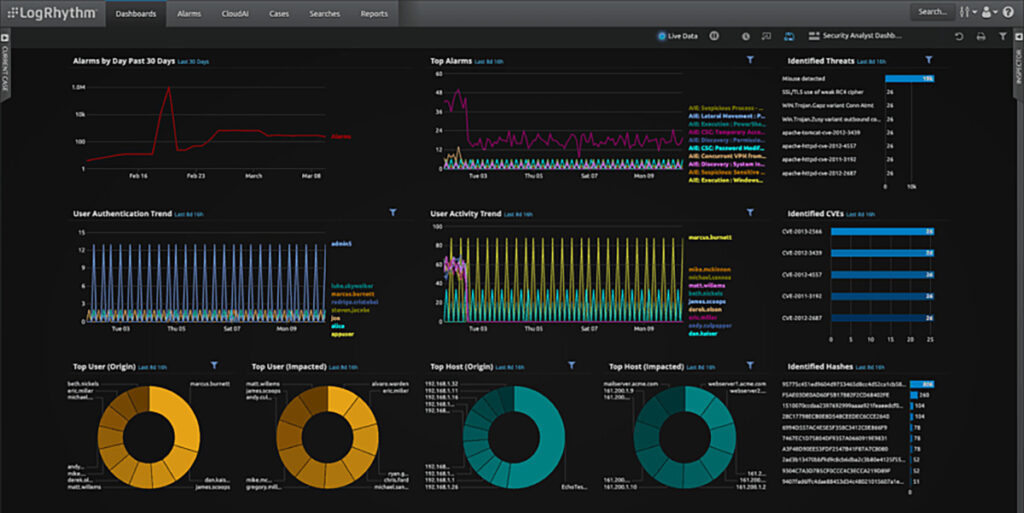
LogRhythm

LogRhythm is a pioneer of SIEM and earned itself a solid reputation. LogRythm’s solution also incorporates many analytical tools, as well as incorporating AI and log correlation. While integrating with LogRhythm is relatively hassle-free, there is a steeper learning curve as it is not considered as user-friendly as other SIEMs.
Moreover, LogRhythm’s solution does not support automated detection of all lateral movement. Therefore, analysts are required to manually combine different timelines to detect account switching. This is problematic because attackers often use lateral movement in your network to search for valuable information or assets. The solution’s detection engine is strongly dependent on indicators of compromise (IOCs), and has difficulty detecting advanced threats.
In addition, as noted in a recent Gartner Magic Quadrant report, LogRhythm has several deficiencies in their cloud-based SIEM offering.
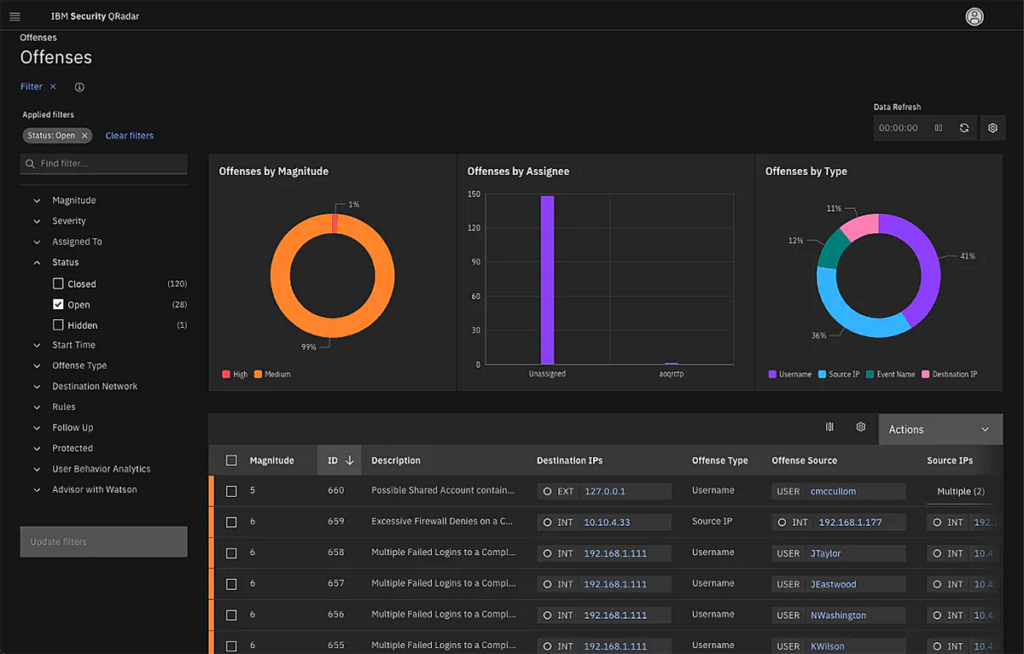
IBM QRadar SIEM

IBM QRadar SIEM allows you to view your IT infrastructure in real time. It is a modular architecture that facilitates the detection and prioritization of threats. It supports multiple logging protocols and offers various configuration-side options, as well as high-end analytics. The solution provides an app store where customers can download additional IBM and 3rd party content to use with QRadar.
However, IBM QRadar has some drawbacks, including the relatively high cost (and complex pricing model), and the requirement for collaboration features like chat tools and improved asset management. In addition, QRadar has weak UEBA capabilities, which are a basic component of next-gen SIEM.
Other drawbacks are that in distributed environments, upgrades can be complex and require extensive effort, as there is often limited product support (although you can purchase upgraded support). The product has limited reporting capabilities, which must be supplemented with externally-developed scripts.
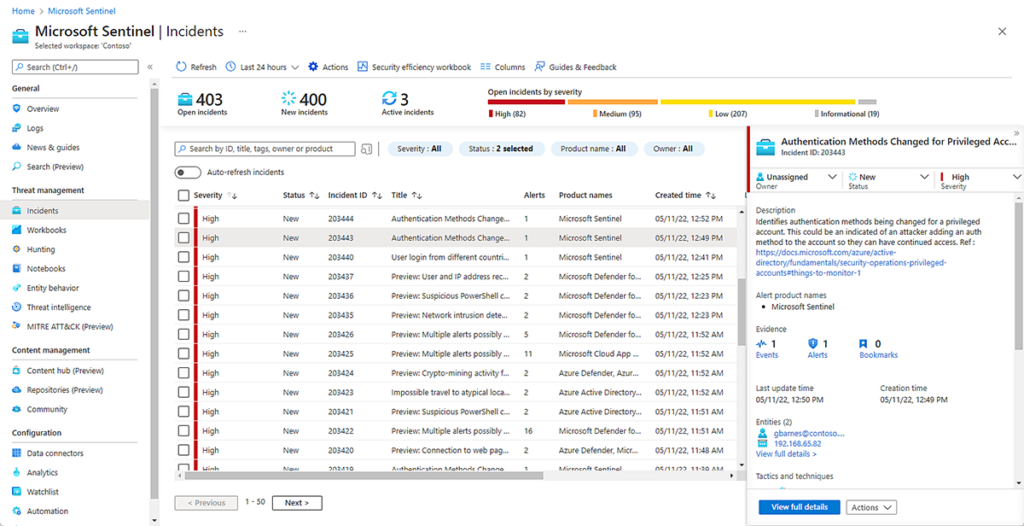
Microsoft Azure Sentinel

Azure Sentinel is a powerful SIEM solution that is relatively new to the market, with Microsoft releasing the platform in late 2019. It is a very popular choice for customers who have existing Microsoft security and IT investments and are looking to unify them under one pane of glass. It also offers a unique “pay-as-you-go” licensing model which meets budget requirements of SMBs, and can also appeal to large enterprises. Azure Sentinel is also known for their smooth data onboarding process.
However, Azure Sentinel has a few notable drawbacks. They take a very Microsoft-first approach to security, and they do not have nearly as many 3rd party integrations with security vendors as other leading SIEMs do. This makes them an unattractive solution for organizations using non-Microsoft security products. There will also be a steep learning curve for security analysts unfamiliar with Microsoft data sources.
Securonix

Securonix has a strong SIEM solution that is highly ranked by analyst firms. Their platform includes next-gen SIEM capabilities, including an analytics-driven UEBA engine. They also advertise deployment partnerships with AWS and Snowflake. In addition to their out of the box rules and models, Securonix offers customers the ability to purchase vertical-specific content via “Premium Apps”, which include packages for fraud, aerospace analytics, etc.
However, customers should be aware that Securonix lacks a built-out native SOAR engine. In the past, they have whitelabeled a SOAR engine from CyberSponse. Securonix now advertises a SOAR component, but it lacks much of the functionality that other leading SIEM vendors incorporate into their security orchestration and automation platforms. As another drawback, Securonix’s standard licensing package includes less hot storage than other SIEM vendors.
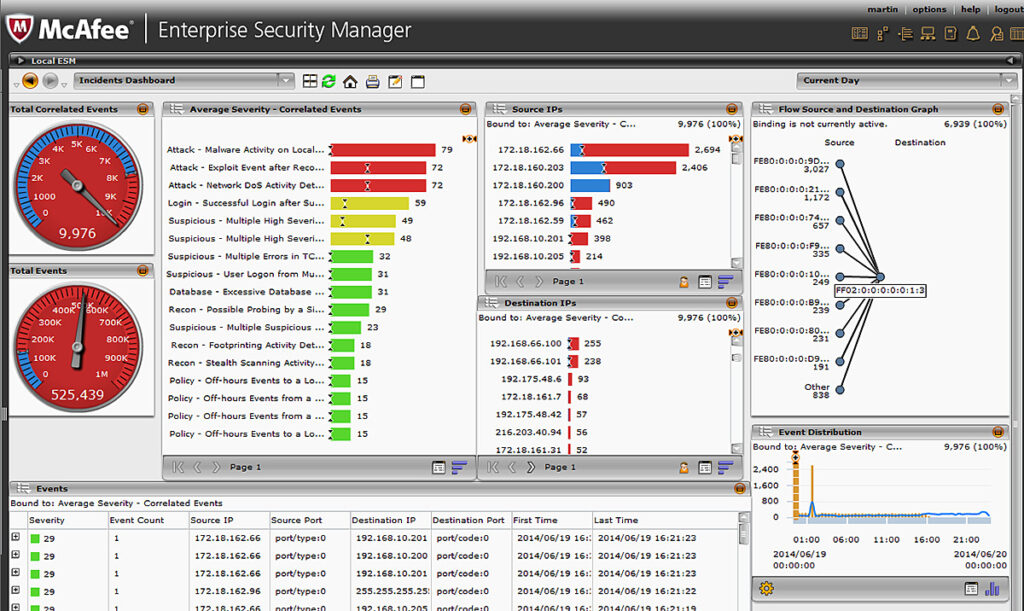
McAfee Enterprise Security Manager

McAfee Enterprise Security Manager allows you to carry out advanced threat detection, manage compliance-related activity, and generate real-time reports. The user interface enables new resources to handle a range of emergency scenarios. You can deploy McAfee Enterprise Security Manager in the cloud or on-premises, and scale up according to your data requirements.
McAfee Enterprise Security Manager works by collecting logs from multiple sources, which can significantly increase network traffic. One reported drawback is logging: the system reduces logs to only the most essential elements — this can result in logs being collected again to see full event contexts.
Some McAfee users report slow performance. Frequent updates can impact continuity, and system prompts can interrupt with regular pop-up windows.
LogPoint

LogPoint is a SIEM that facilitates application event management and enhances application security. It covers most monitoring and security use cases, and is highly scalable. You can scale from one to thousands of servers (or vice versa) according to your needs.
You can implement LogPoint in any environment, including development, production and testing. It facilitates storage, search, filtering, error tracing, and report creation based on log analysis. This helps you detect security issues and investigate them faster.
Users report LogPoint doesn’t have an intuitive user interface, with some features being difficult to find. Alert configurations, for example, are accessed under Alert Rules, which is hidden in the Knowledge Base section in the Settings menu.
Another potential drawback for users can be the query language, which is versatile but has a steep learning curve and can be difficult to handle. The necessary information is not always easily accessible, and setting up UEBA can be complicated and time-consuming. This makes it a less suitable option for organizations that lack highly technical staff.
Elastic Stack

ELK stack is a monitoring and log management tool developed by Elastic, which works with Elasticsearch, Logstash and Kibana. Elasticsearch allows you to search and filter logs as needed. Logstash facilitates the generation and collection of logs in real time, at a single location. Kibana supports visualization of statistics through graphs and charts and graphs.
These tools are open-source, and enable efficient application management and monitoring. With ELK stack, applications can be logged centrally, which allows you to identify and remediate issues quickly, and ensure the applications perform correctly. Organizations use it to detect IT issues early on, so the security team can address them immediately.
Drawbacks of ELK include out-of-memory exceptions for queries with large index sizes, the complexity of setting up and managing projects (due to the multiplex architecture), and a lack of support for integrating third-party tools. ELK is also known to have poor documentation and is difficult to debug, so learning to use it involves a lot of knowledge and trial and error.
ArcSight Enterprise Security Manager

ArcSight Enterprise Security Manager is known to be easy to deploy and maintain (at least initially), and offers many possibilities, provided you are willing to invest in developing the necessary tools. Its powerful capabilities include correlation, action triggers, and a normalization feature.
However, ArcSight can be slow when it comes to deploying large environments, and pulling logs can be time-consuming. It also has a complex backend, which means the proper maintenance may require skilled SIEM engineers — especially if you need to develop meaningful categories of events.
InsightIDR

InsightIDR offers out-of-the-box capabilities, pre-built alerts and triggers. It unifies disparate data sources, enabling security analysts to work more efficiently. It has a cloud-forward approach, although it still offers on-prem log collectors.
A major drawback of InsightIDR is that it can be time-consuming and tedious to search raw logs. This means that teams often rely on established on-host log reviews to speed up discovery. It also lacks a smooth user interface for incident management, making it harder to collect in-context details about security events.
In addition, InsightIDR has limited integrations. The solution works with other Rapid7 tools and selected third party vendors, which goes against one of the main value propositions of SIEM, which is to become a central repository of all security data in the organization.
How to Choose a SIEM Provider
All the SIEM systems we listed above are robust solutions with a broad user base. When selecting a SIEM, evaluate the vendor’s track record and market position, and pay special attention to functionality.
Below we show core capabilities that define a SIEM solution, and next-generation capabilities that add intelligence and automation, to make a SIEM more effective for your organization. The best SIEM solutions cover the core capabilities, and add next generation features that are suitable for your security needs.
Core SIEM Capabilities
- Threat detection – SIEMs provide accurate threat detection with the aid of rules and behavior analytics. They also aggregate threat feeds, backlists and geolocations.
- Threat intelligence and security alerting – many SIEMs connect your security system to a threat intelligence feed. This ensures your business is up to date on the latest cyber threats. SIEMs also aggregate and normalize your security data, cross-checking various sources, assessing your system activity, and alerting you anytime they identify a suspicious event.
- Compliance assessment and reporting – compliance is one of the biggest hurdles for any business, and it is only getting more complex. Regulations such as FFIEC, HIPAA and PCI, define how and what data needs to be stored. Failing to meet regulatory requirements can have catastrophic results for a business. SIEMs provide compliance reporting and can help you identify your business’ effectiveness in meeting regulatory requirements.
- Real-time notifications – where security is concerned, time is of the essence and SIEMs will notify you of any security breaches in real time. This allows your business to respond immediately to a potential threat.
- Data aggregation – centralizing information from many sources and providing a clear picture of all your network activities is the most important feature of SIEM. Without this, it would be easy to lose track of dark corners in your network, especially as your business grows. This lack of visibility is easily exploited by cybercriminals, leaving your network vulnerable to undetected infiltration.
- Data normalization – your security system consists of vast amounts of data from different sources. To identify correlations in security events, all of this data needs to be formatted consistently. SIEM normalizes all your security data, making it easier to analyze and draw meaningful conclusions from it.
Next-Gen SIEM Capabilities
- Data collection and management – next-gen SIEMs can collect and manage data from all available sources, with integration facilitated by built-in connectors. The important types of data sources are cloud resources and services, network data and on-premise log data, and external devices like smartphones.
- Cloud delivery – cloud SIEMs leverage elastic cloud storage and data lakes. This makes them much more scalable than traditional, on-premise SIEMs, which rely on equipment that cannot handle the massive volumes of data generated by large enterprises.
- User and Entity Behavior Analysis (UEBA) – establishes a baseline of typical user behavior and uses ML algorithms to identify behavioral anomalies. This technology enables modern SIEMs to effectively detect zero-day and insider threats, which don’t correspond to known attack signatures.
- Security Orchestration and Automation Response (SOAR) – enables SIEMs to respond to security incidents as they occur, rather than simply monitoring and alerting. Next-gen SIEMs can collaborate directly with IT and security infrastructure, making suggestions for relevant actions. They can also automate threat response using IR playbooks, orchestrate threat detection and response tools used by multiple systems, and manage security systems such as firewalls, email servers and access management.
- Automated attack timelines – traditional SIEMs require analysts to collate data from various sources to make sense of the attack timeline. This can be time-consuming and requires special expertise. Next-gen SIEMs can automatically build an attack timeline and present it visually so that less specialized analysts can understand it. This makes investigation and incident triage much faster.
Conclusion
As cyberattacks become more common and more high profile, it is more important than ever to understand the cybersecurity tools that are available. When it comes to security reporting, there is a conflict between the volume of data and practicality. While you do not want to miss a single security event, managing all the alerts from all the systems in your infrastructure in your security infrastructure is simply impossible.
This is where SIEM comes in. By centralizing all of the notifications in a single platform, you will be notified of any event that needs your attention without wasting time monitoring multiple systems. To further improve your security profile, you can integrate SIEM with solutions like SOAR and UEBA to automate threat detection, reduce false positives and respond to threats, or invest in a Next-Gen SIEM offering.
See Exabeam in action: Request a demo






