An Exabeam customer used Fusion SIEM to identify, investigate, and remove the evasive Lapsus$ criminal hacking group from their environment. We are sharing their Exabeam in Action story anonymously.
In this article:
- What is Lapsus$ and why is it hard to detect?
- How Lapsus$ was detected using Exabeam
- What the investigation uncovered
- Why Exabeam is invaluable for detecting compromised credential attacks
Attack Name/Attack Type: Lapsus$/Compromised Credentials
What is Lapsus$ and why is it hard to detect?
Lapsus$ is a criminal hacking gang that has been in the news lately due to a spate of cyberattacks against large, high-profile organizations. The Lapsus$ group has been known to recruit employees via messages on social media and secure messaging apps, offering them tens of thousands of dollars a week to perform inside jobs. So, in addition to attackers already being able to purchase credentials online, now employees are willing accomplices in these crimes that promise big payoffs for them.
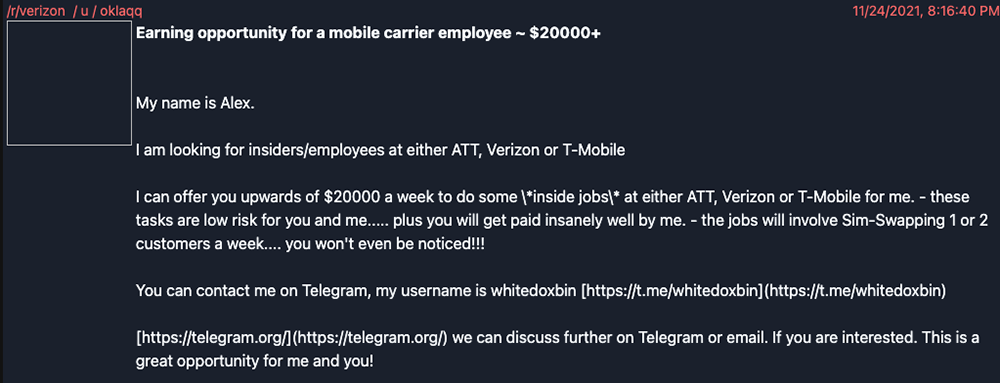
That’s what makes Lapsus$ attacks so difficult to detect; the intrusion appears to be coming from inside the house. When credentials are stolen or purchased (as they were in this case), and used to move laterally within an organization, nearly all security teams are unable to detect abnormal behavior associated with legitimate credentials.
Telegram, an encrypted messaging application that allows users to make messages untraceable and self-destructing, is one of the platforms that is known to have been used by Lapsus$ in its recruiting efforts, as well as to share screenshots and data from breached organizations.
How Lapsus$ was detected using Exabeam
Exabeam Advanced Analytics notable user detections were responsible for bringing the compromised user to light. The behavior of the compromised user was detected by Exabeam Advanced Analytics in our customer’s environment and was flagged as notable, meaning that the behavior stood out as something unusual that needed to be investigated by the level 1 SOC analyst.
The unusual behaviors that triggered alerts were:
- Impossible travel (CountryA + CountryB virtual desktop infrastructure (VDI))
- An abnormal number of systems logged into for the user
- Anonymous Tor network = login origin
Overall, 10-15 behavioral rules fired in Exabeam. These behaviors validated that an attacker was in the act of reconnaissance. What’s worth noting about the behavioral models that triggered is that these behaviors were similar to tactics, techniques, and procedures (TTPs) we have seen in other attacks. As we are witnessing in most major attacks these days, indicators of compromise (IOCs) are constantly changing, but the behaviors (TTPs) are the same in each case. We see repeatedly that attackers obtain credentials to access the environment, move laterally, and escalate privileges to gain access to increasingly more sensitive systems and information.
The MITRE TTPs detected were:
- T1078 – Valid Accounts
- T1550.003 – Use Alternate Authentication Material: Pass the Ticket
- T1558.003 – Steal or Forge Kerberos Tickets: Kerberoasting
- T1046 – Network Service Discovery
- T1021 – Remote Services
What the investigation uncovered
The detections from Exabeam elevated this employee’s risk score to a Notable User and needed further investigation. The customer’s investigators quickly discovered messages to and from Lapsus$, confirming that the employee was likely paid for their credentials. The SOC team then used Threat Hunter and Data Lake to see if other users had been compromised by looking for behavioral deviations/TTPs in Threat Hunter and searching for the Tor IPs (IOCs) in their Data Lake.
This customer is heavily invested in endpoint detection and response (EDR) and traditional security information and event management (SIEM), but knew they needed user and entity behavior analytics (UEBA) to provide a comprehensive risk-based view across a large employee base for their global SOC. They think of themselves as innovators and are proud of their global security operations modernization. They enhanced their security operations program last year to include behavioral analytics, and they see Exabeam as a way to provide a global risk view, and to prioritize and accelerate investigations.
When asked if they had seen Mimikatz — a favorite adversary tool focused on credential theft and misuse, which is a credential dumper capable of obtaining plain text account logins and passwords — or any other interesting activity in their EDR tool, the Exabeam customer replied, “Nope, because of Exabeam they didn’t get that far along in their attempt to hack us. In fact, Exabeam was the only thing that alerted anything related to their activity.”
“Because of Exabeam, they didn’t get [as far as our EDR] in their attempt to hack us. Exabeam was the only thing that alerted anything related to their activity.”
Why Exabeam is invaluable for detecting compromised credential attacks
Exabeam helps security teams detect compromised credentials. By applying machine learning and user behavior analysis, Exabeam creates a baseline of normal behavior for every user and asset. So, when anomalous behaviors occur that indicate a compromised account, we automatically detect them and elevate the risk score, regardless of the attackers’ TTPs. Once you have an understanding of normal for your environment, our behavioral models can clearly distinguish anomalous activity.
Once inside, attackers will usually focus on privilege escalation to elevate access, move laterally to find high value assets, and exfiltrate the data. Exabeam detects and mitigates attackers’ credential theft and privilege escalation by detecting typically used TTPs. With higher privileges, attackers can do things like manipulate an organization’s active directory, create or delete accounts, or modify group membership and permissions. Exabeam detects account manipulation by identifying abnormal user behavior, and other unusual activity, like hiding behind system accounts.
Furthermore, by combining user and asset activity from a variety of endpoint, email, cloud, and authentication data sources, Exabeam can detect data exfiltration across a variety of channels, including domain name system (DNS), email, or web upload. We can detect anomalous activity associated with evasions, such as tampering with audit logs, file destruction or encryption, and the use of proxies and anonymizers used to obfuscate outbound web traffic.
Want to learn more about detecting compromised credentials?
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













