Disruptive Transformation: What Caterpillars Can Teach Us about Cybersecurity in the Pandemic Era

It would be an extreme understatement to say 2020 has been a tough year. In many ways it will be the defining year that marks a sudden change in a global society for a number of reasons. What’s on the other side of that change is still unclear. What is clear is that the journey we’re all on is challenging in many ways — but through it we’ll all become stronger. I liken it to the journey of a caterpillar — a classic literary symbol of evolution and transformation — which goes through an oddly similar period of change (and confinement) before transforming into something new. Hopefully this post helps provide some guidance on how security practitioners can adapt to the changes they face as they enter, and then eventually reemerge from their cocoons.
Writer’s Note: This post is modeled loosely after the framework laid out in a recent Gartner report by Nat Smith titled “How Security Product Leaders Should Respond to the 4 Phases of COVID-19” which has concise descriptions of what to expect as we move through the journey of experiencing and reacting to the COVID-19 pandemic (see diagram below).
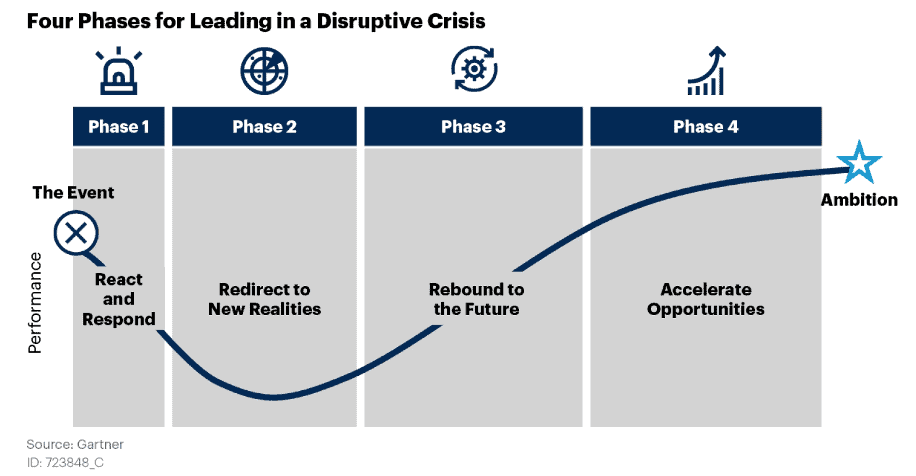
Source: Gartner “How Security Product Leaders Should Respond in the 4 Phases of COVID-19.
However, chances are that if you’re reading this, you’re not a security vendor. With that in mind, I adapted the framework for security practitioners.
Phase Zero — the before times
This phase is not one of the four outlined in Smith’s research. Instead it’s simply the status quo we were experiencing before a global pandemic uprooted our way of doing things. Phase Zero, in this regard, likely started in the 1970s when Bob Thomas wrote Creeper, the first computer virus. Since then, we’ve seen successive waves of new technologies followed by security controls to help prevent those technologies from being abused for ill gain. Over the years, these security controls and best practices have included the use of firewalls, anti-virus, endpoint detection and response (EDR), intrusion prevention systems (IPS), web proxies, authentication, privileged account monitoring (PAM), security information and event monitoring (SIEM) and more.
In short, Phase Zero was a relatively prosperous time when security teams enjoyed steadily increasing visibility in the C-suite, and their budgets increased to reflect that visibility.

Phase 1 — react and respond
When the COVID-19 pandemic began, the world experienced an unprecedented change. This change was deeply felt in a number of ways, but one acute point germane to this conversation was the sudden, unexpected shift of corporate staff to fully remote work if possible. This presented IT teams and security professionals with a series of challenges to overcome and little time to do so.
Phase 1 is all about understanding what has changed and how to react. Some of the common challenges faced by security teams as they looked to adapt to these new circumstances may include the topics listed below. If you’re currently still in this phase, we’ve prepared the following resources to help you navigate some of the top challenges you’re likely dealing with:
Phishing
It’s not that phishing increased per se, it’s that phishing changed its “bait” by using COVID-19-related campaigns that exploited the unease and fear of the situation.
To learn how to identify and mitigate COVID-19 phishing attacks, head over to “Securing Your Remote Workforce, Part 1: Detecting Phishing Scams Disguised as Updates.”
VPN challenges
Even before the COVID-19 pandemic, VPN was an essential technology. However, with the sudden shift to fully remote workforces, VPN infrastructure was suddenly subjected to a never-before-seen level of use. Head over to this post to learn about how to detect unusual VPN access and best practices to secure VPN services.
Malware
Malware is always a problem. However, in a COVID-19 world, employees often find themselves in situations where they must learn to do their jobs using new tools and programs due to the remote nature of their current work environment. This presents ample opportunities for bad actors to create malware disguised as productivity tools. This article may be helpful in order to learn about how to detect malware in the guise of productivity tools.
Fraudulent logins
With workforces suddenly remote and hackers continuing their pursuit of credentials to use for their exploits, fraudulent logins are an area to pay special attention to. This post provides an overview of the abnormal activity indicative of fraudulent logins and how you can tackle the problem.
Helping end-users stay protected
With all of these security controls in place, there is another potential weak link in your security program that needs to be updated: your staff. Business is no longer “as usual,” and with the change in the working environment, technology in play, threats being subjected to, and a myriad of other things being thrown at employees, it’s imperative that we help our users through this transition as well. This post has an interview with Exabeam’s very own director of InfoSec, where we discuss that exact issue — how to help people through the transition.
Managing a remote SOC
We’ve covered security controls and education for end users, now we need to turn our attention to the SOC itself. In many companies, SOC staff are also working remotely. For guidance on how to adapt your SOC, its processes and procedures, check out this webinar: SOC-from-home: Actionable Insights for Security Practitioners.
Both as security professionals and generally as humans, phase 1 saw us hunkering down seeking shelter to weather out the storm of change that the pandemic thrust upon us.

Photo credits: Dawna Moore Photography
Phase 2 — redirect to new realities
According to Gartner analyst Nat Smith’s research, this phase is characterized by “heavy cost cutting attempts to make up for revenue shortages.” For security teams, this translates into security project prioritization and searching for cost efficiencies.
“Security will have to tighten its belt just like everyone else,” said Paul McKay, a senior analyst at Forrester Research Inc. in a recent Wall Street Journal article. In recent years, corporate cybersecurity budgets were often shielded from cuts in other business areas, he added, but this will likely change for some companies.
If you are in this phase, we’ve prepared a few tips that can help you do more with less:
Optimize your logging costs
For years, SIEM has been a drain on budgets due to its use of volume based–pricing models. Nowadays there are several vendors who offer alternative pricing models that are either flat or at least predictable. Shifting some or all of your logging to a lower cost or a more predictable SIEM or logging platform is a great way to free up money for other security projects.
Identify and minimize security product overlap
As security teams grow and evolve, they may find themselves in a situation where they have dozens of point products to manage. Not only does managing many tools consume resources, but it’s often the case that multiple tools will overlap in scope; meaning there are multiple layers of inefficiency in effect. When budgets are tight, reducing redundancy can be a great way to free up resources.
Increase the productivity of existing staff
While this recommendation does not help reduce budgets directly, it can ease the need to hire new analysts by getting more out of your existing team. This in turn can reduce the need for new headcounts, which may be a significant portion of a security budget. Several tools can help increase productivity including user and behavior entity analytics (UEBA) and security orchestration, automation and response (SOAR).
UEBA combines data from all security and contextual data sources to determine normal behavior for all users and machines on a network. Once a behavioral baseline is achieved UEBA will identify high-risk activity and assign it a risk score.
This approach provides several productivity enhancements:
- Reduced maintenance overhead because it tunes itself (no more monkeying with correlation rules).
- Risk-based prioritization points analyst efforts directly at the users and devices that are exhibiting the most unusual behavior. This can focus their attention where it’s needed most.
- Machine-built incident timeline creation can automate the manual steps of gathering evidence.
SOAR tools provide further force multipliers for SOC teams by using pre-built connectors and response playbooks to automate incident response workflows. Using SOAR, analysts of all levels can rapidly respond to incidents at the click of a button (or in some cases without clicking any buttons).
Phase 3 — rebound to the future
Phase 3 is all about making adjustments to the business that prepare it for the future — or perhaps to emerge from its cocoon? Even prior to the pandemic, workforces were shifting to the cloud, but the sudden shift to a fully remote workforce gave this digital transformation a proverbial shot-in-the-arm. According to a recent MarketWatch CIO survey, “68% said cloud services would become more of a priority,” and “CIOs expect to reduce their mix of on-prem workloads from 59% in 2019 to 35% in 2021.” After the COVID-19 pandemic, these numbers will undoubtedly increase. One of the primary ways that security teams can react to this trend is to accelerate the transition of their security controls to the cloud.
One valuable takeaway from the pandemic is that we’ve passed the right time to embrace the cloud by implementing cloud-first and cloud-native strategies. Even if people return to the office in the semi-near future, cloud first-strategies prepare us for similar events in the future. They help security teams skate to where the puck is going by implementing the visibility and control that will be needed when most, if not all, of our critical business services are obtained from the cloud. Why not start that now, as you’re looking to prepare your business for a post-COVID-19 world?

Photo credit: Interesting Insects
Phase 4 — accelerate opportunities
This is where we fully adjust to the new normal of a post-pandemic world. What this will look like remains to be seen, but it’s unlikely to be as it was before. This is a good time to revisit your newly implemented security strategies and technologies and make sure they match the requirements of your organization’s new normal.
I referred to the lessons the humble caterpillar can teach us. By that I mean it’s a journey. Before the COVID-19 pandemic, we were businesses gobbling up security tools and adhering to best practices. We’re currently in the cocoon phase, rebuilding our people, processes, and technology, rethinking our strategies and assessing our investments. Someday we’ll emerge from this pandemic cocoon stronger than before to a new, changed world that we’ll be able to embrace together.
Photo credits: Steve Greer Photography
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!











