Securing Your Remote Workforce, Part 2: Detecting Unusual VPN Access and Best Practices to Secure VPN Services

When your employees work from home, VPN servers become all the more important. To support a secure, agile organization, VPN security and availability needs to be the focus for enterprise IT and security teams. In this post, we look at how VPN services can be vulnerable and discuss some methodologies to detect unusual VPN access. Enterprises can also put in place some best practices to secure VPN services as a preventive measure.
If you are looking for additional information on how to protect your home-bound organization, please refer to the first article in our five-part series, “Detecting Phishing Scams Disguised as Updates.” It discusses how threat actors are using the pandemic to launch new attacks.
VPNs are essential security tools
Per the Ponemon 2018 State of Cybersecurity Study, VPNs are one of the most essential security technologies (see Figure 1). Enterprises consider VPNs the de facto method to provide secure access for all employees to access resources and data within their organization. Advanced encryption technologies SSL (Secure Sockets Layer) and TLS (Transport Layer Security) have been introduced into VPN products to make it easier for large corporations to adopt VPN technology, provide privacy and security for organizations, and allow employees to seamlessly work remotely.
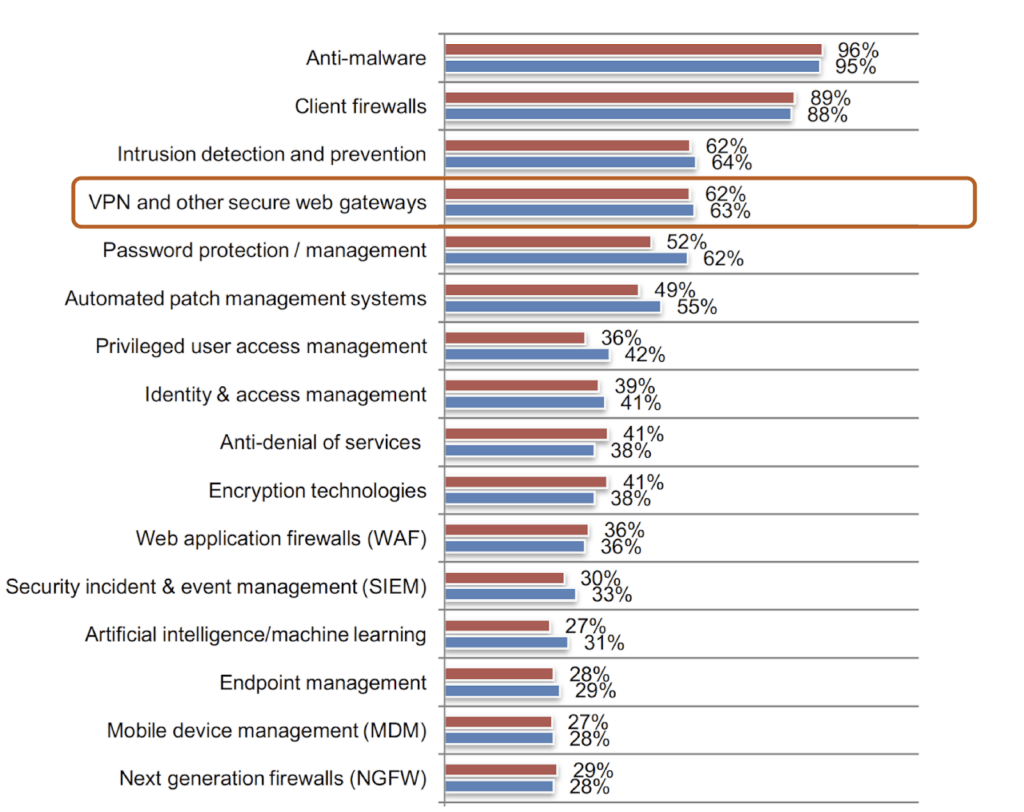
Figure 1: Showing VPNs as one of the essential security technologies for enterprises. Image Source: Ponemon 2018 State of Cybersecurity Study
But VPNs have vulnerabilities
Vulnerabilities exist in VPNs. For example, here are some of the sample vulnerabilities from the CVE database. These VPN loopholes allow attackers to retrieve sensitive corporate data, including authentication credentials. Adversaries can use these stolen credentials to connect to the VPN and change configuration settings, or connect to other internal resources. Unauthorized connections to a VPN can also provide the attacker with the privileges needed to run exploits. As an example of VPN attacks, late last year, aerospace giant Airbus was hit by a series of attacks by hackers who targeted VPNs used by airline suppliers to steal sensitive company data.
Challenges for IT and security teams to secure VPN tools
Depending on the number of employees and the size of your organization’s IT and security teams, there can be many challenges that IT teams face, which will force organizations to re-examine the VPN security policies and controls they have in place. Security teams face tremendous pressure to comply with security controls, and they face many challenges such as the following:
- Identify stolen credentials: Most VPNs require a traditional username and password combination, which can easily be guessed or stolen. In fact, according to the Verizon 2019 Data Breach Investigations Report (p.10), stolen credentials are the number one vector for data breaches. To improve security, IT teams might have very strict deadlines to re-evaluate authentication tools like SSO and MFA and deploy them or reinforce stricter authentication policies across the organization.
- Accommodate VPN capacity: With 100 percent of your employees working remotely, increasing VPN capacity to accommodate more staff could be expensive. This might involve planning for more user licenses or the purchase of additional appliances.
- Track unusual user access: Security teams have to make sure all the rules are in place to track any unusual user access to key company resources. With most employees working remotely, enterprises may have to enforce additional security controls to authorize user access.
- Patching employee machines: Many larger organizations may require an employee to either be on the local network or VPNed in to install necessary patches on their machines. If remote employees aren’t regularly connecting to the VPN, their machines may go unpatched for weeks, if not months. IT/security teams may have to allocate dedicated time to track and call in those employees to upgrade their machines to the latest OS/application patch release or configure machines to automatically update patches from internet resources directly from software vendors.
How behavior analytics can help detect unusual patterns in VPN access
While security teams should follow best practices to make sure data privacy and security controls are in place, they often aren’t enough to protect your data. Behavior analytics technology lets you detect unusual VPN activity that could represent misuse, and respond effectively to minimize or prevent data loss, sabotage, or other adverse effects to your business. Behavioral analytics can help identify a number of abnormal circumstances which may indicate an unusual VPN activity, including:
- Abnormal VPN connections from the user
- Abnormal VPN session duration
- First VPN connection from an unknown device
- VPN connection from an anonymous proxy
- Abnormal amount of data uploaded during a VPN session
- Increase of company-related data files access
- MFA from a new device for a user
- Physical badge access after VPN access
- Too many failed VPN logins
- VPN access from a disabled account
- Source IP from unauthorized location
- Malicious VPN source IP
For example, Figure 2 below shows Frederic Weber’s timeline that outlines parsed VPN log data and VPN logins from a particular location, then stitches it together with Frederic’s other activity. Behavior analytics can detect Weber’s VPN login from Sweden as an anomalous behavior, as it’s outside of his normal location.
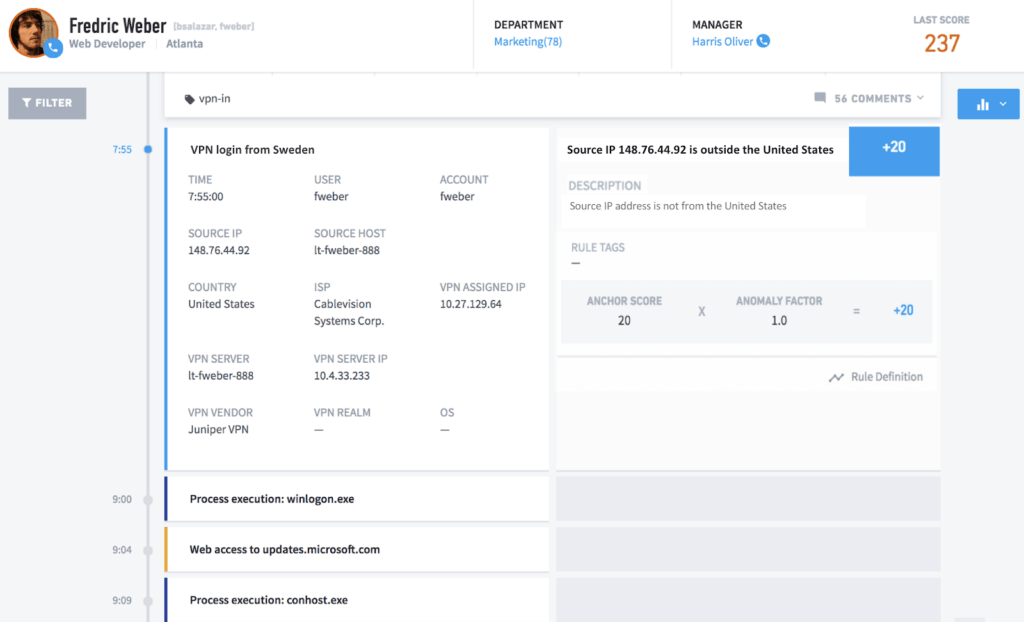
Figure 2: This user timeline shows the user Fredric Weber VPNing from outside his normal location.
The advantage of behavior analytics is its ability to create baselines of normal activity and then automatically find deviations from that normal activity that may indicate compromise. Regardless of whether an organization is a small business or an enterprise of tens of thousands of employees, behavior analytics is able to stitch millions of logs including VPN access, endpoint, web access, and firewall, then model the behavior for every user and all machines in an organization. For example, Figure 3 shows a sample of behavioral models for a particular user on VPN activities like VPN source IPs, VPN session time, VPN login from countries, and other activity being baselined to make it easier for analysts to detect any unusual deviation from normal behavior.
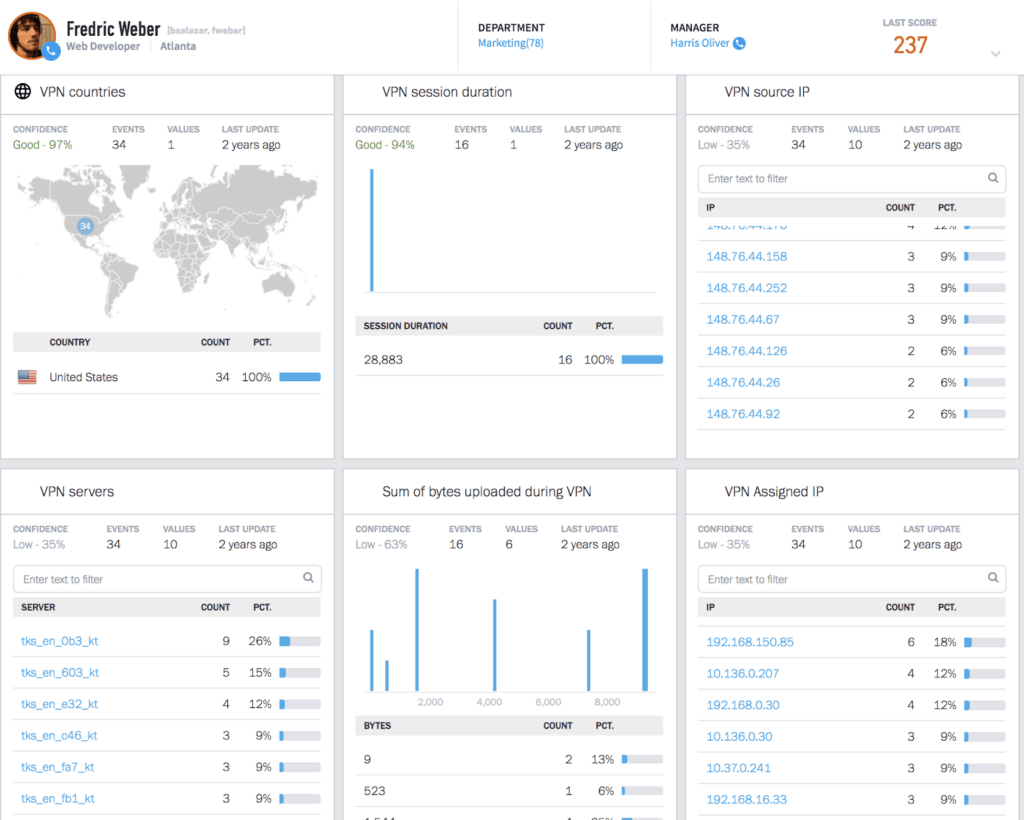
Figure 3: Examples of machine learning models show normal baseline user behavior around VPN activity for the user.
Best practices to secure VPN services
Having your workforce working remotely brings an opportunity to validate some best practices to further secure your environment. This will guide your organization to look at existing or new security tools that your IT/security teams might need to evaluate and reinforce.
- Enforce strong authentication methods
Without strong authentication methods, organizations expose themselves to risks where hackers can gain unauthorized access to sensitive data. In addition to enforcing single sign-on (SSO) to access various applications, organizations should evaluate multi-factor authentication (MFA) options. SSO and MFA can deliver secure authentication for all environments, protecting identity and access to data wherever users go. This is extremely pertinent for organizations using VPNs and expanding into the cloud.
- Re-evaluate all points of entry
In addition to VPNs, organizations should evaluate all points of entry into their networks, from web applications to email to cloud, and identify whether there is any vector which an adversary could gain access to their environment with a compromised username and password. Anything that allows access from outside a company’s network should be reinforced by multifactor authentication, and organizations should monitor for indications of compromised accounts. This could include watching for successful authentications via username and password followed by failed multifactor authentication attempts
- Re-tune rules and threat hunting queries
Behavior analytics can alleviate some pain for security teams as they automatically adapt to the environmental changes and make it easy for SOC teams to detect threats. But the SOC team should consider re-tuning any existing rules and threat-hunting queries in their SIEM to look for adversary techniques, since advanced threats usually have no pre-defined indicators for analysts to look for. Rules and threat-hunting queries can help SOC analysts monitor for any unusual access to the environment, privileged accounts, lateral movements, or abnormal data exfiltration.
Many of the techniques used by adversaries are outlined in the MITRE ATT&CK framework, including T1056 Input Capture and T1133 External Remote Services that exploit gaps in VPN security. By learning more about them SOC analysts can tune their rules and threat hunting queries to detect these exploits.
- Secure remote wireless networks
Employees working from home often use laptops connected to a cable or DSL modem through their own wireless access point. Unfortunately, many wireless routers are never configured for security: they are merely connected and turned on. Teach employees how to configure their wireless routers and computers for WPA or WPA2, and why it is important to keep their home networks secure. Also, encourage employees to keep their antivirus software up to date on other personal machines that are joined to their home networks. If their personal machine is compromised by an attacker, and is on the same network as their work machine, that can open up the corporate network to additional risks.
Want to learn more?
Stay tuned. This is part two of a five-part series on common issues security teams face with remote workers. Over the next several weeks, we will also publish posts covering malware detection, remote access monitoring and device policies.
Part 1: Detecting Phishing Scams Disguised as Updates
Part 2: Detecting Unusual VPN Access and Best Practices to Secure VPN Services
Part 3: How to Detect Malware in the Guise of Productivity Tools
Part 4: How to Detect Fraudulent Logins and Policy Violations Using UEBA
Part 5: Best Practices for Personal and Corporate Device Usage
Just added: Webinar on April 1 Threat Hunting for First/Abnormal VPN Anomalies. Register now for your spot.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!











