Securing Your Remote Workforce, Part 4: How to Detect Fraudulent Logins and Policy Violations Using UEBA

With businesses moving to the cloud, technology has emerged as a key sector offering access to a distributed workforce. Most businesses today offer an account setup process that is quick for consumers but also requires them to provide personal information. This makes them an attractive target for fraudsters looking to either test stolen credentials or create fake accounts to access the services. Once stolen, this information can be used to facilitate fraudulent activity, giving personal information genuine value in illicit markets. In fact, per the Fraud and Abuse Report today released by Arkose Labs, about half of the logins (53 percent) on social media sites are fraudulent and 25 percent of all new account applications on social media are fake.
This post will discuss briefly how fraudulent logins affect enterprises and how enterprises can utilize modern analytics technology to detect these fraudulent logins and any policy violations.
How do fraudulent logins affect businesses?
Fraudsters typically use large-scale bot attacks to steal information, credentials, spread spam and launch social engineering campaigns. If the attackers are able to steal personal credentials, they are able to impersonate and can get into the user’s enterprise account, since a lot of users use the same credentials across accounts. Once the fraudsters are able to impersonate a business account, they can steal billions of dollars from small and large businesses. Here are some of the illegal practices that are carried out.
- Identity theft – Identity theft is the seventh-largest crime in the U.S. Business identities can be used to open card accounts, initiate wire transfers or commit tax fraud. Imposters can use stolen information and pose as a patient to receive medical care or apply for government benefits, file a fraudulent tax return and other crimes.
- Banking and credit fraud – Fraudsters can steal credit card account numbers, PIN and security codes to make unauthorized transactions. How can they do that? They often use an individual’s personal identifiable information (PII) to contact their credit card company or bank, to take over the account or use personal information including SSNs to apply for a credit card in the individual’s name.
- False invoicing – This scam often involves someone posing as a legitimate supplier and diverting the payments into an alternative account.
Best practices to guard organizations from fraud
While there are many ways fraudsters can attack individuals and organizations, the most important step organizations can take is to protect their corporate sensitive data and employee personal information. Let’s look at some of the best practices that organizations can take in order to prevent any loss of data and key information.
- Re-educate employees on phishing and spam: With employees getting numerous updates on the latest health and new travel policies, it is also important to train them on the security implications of this new situation. Sophisticated email attacks can often be indistinguishable from real emails. Refer to Part 1 of this blog series which talks in detail about “Detecting Phishing Scams”
- Limit the exposure of sensitive information: Limit disclosure of sensitive information except when it’s absolutely necessary. Lock down your classified or key corporate data. It’s not a bad idea and never too late to evaluate or reinforce an additional layer of authentication if your organization doesn’t have it already.
- Re-visit security controls: Organizations have to assess risks to critical assets and then choose appropriate security controls to put in place. This can be physical controls like detecting and preventing unauthorized access to physical areas, systems, or assets or logical controls such as having security controls on firewalls, antivirus software, intrusion detection systems (IDSs), as well as access control lists (ACLs).
How UEBA can help detect fraudulent logins and policy violations
The 2018 Global Fraud and Identity Report states that only 40 percent of business executives are confident of detecting fraudulent activities. Even with all the best practices and security controls in place, monitoring user behavior is one of the most efficient ways to detect and flag anomalous behavior immediately. It may seem very complex to monitor each and every behavioral artifact to look for threats and not load the security team with heaps of alerts to look at. That’s where machine learning-based user and entity behavior analytics (UEBA) comes into the picture to help security teams detect fraudulent activity efficiently.
UEBA is an analytics-driven threat detection technology that uses machine learning and data science to gain an understanding of how users within an environment typically behave. Next, the system finds risky and anomalous activities that deviate from users’ normal behavior that may be indicative of a threat to an organization. It is important to find any fraudulent and/or policy violations early before it becomes a data breach.
While IT and security teams can have controls in place, employees should adhere to security policies. UEBA tools like Exabeam Advanced Analytics can detect any policy violation and stitch the anomalous events in a timeline to make it easier for analysts to detect defaulters easily. As an example (Figure 1), unusual user logon events are detected where the user is trying to remotely login to an asset from unauthorized geolocations, ISPs and it’s the first time logon to an asset for the user and the group the user belongs to. These events by themselves may not seem like policy violations at first glance, and so a smart timeline like the one shown below is important to get the complete picture of the threat. Smart Timeline not only stitches all events in chronological order but also lets analysts know exact reasons why a particular event is abnormal. This helps minimize the false positives that the security team has to deal with on a daily basis along with millions of events and alerts.
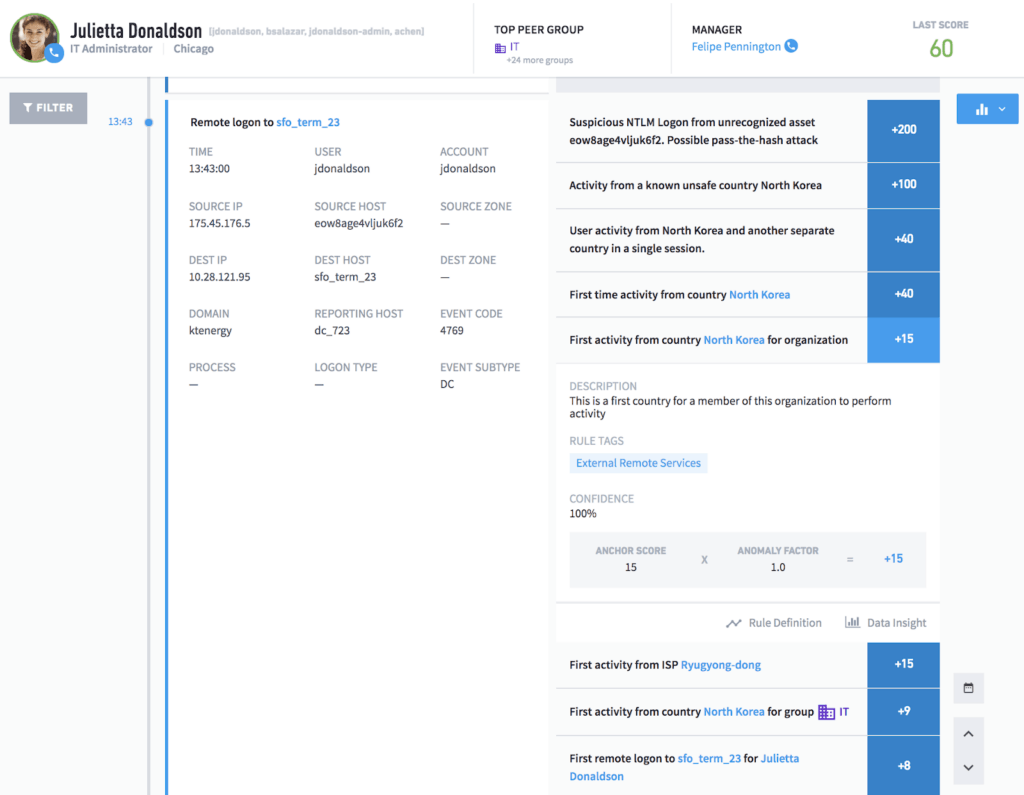
Figure 1: Examples of various fraudulent events showing unusual remote login activity from a unauthorized country, ISP and first time remote login to an asset.
Exabeam UEBA technology starts with baselining normal behavior for every user and machine in an organization. Any deviation from the baseline is given a risk score by machine learning algorithms based on the amount of the deviation and type of behavior. For example, Figure 2 shows just a sample of machine learning-based behavior models that help Exabeam UEBA monitor user logins to their workstations, remote assets, time of login, assets the user access and also track failed logins to company resources. These behavior models help analysts track and detect any departure from their normal behavior and shows it in the smart timeline to pinpoint any policy violations.
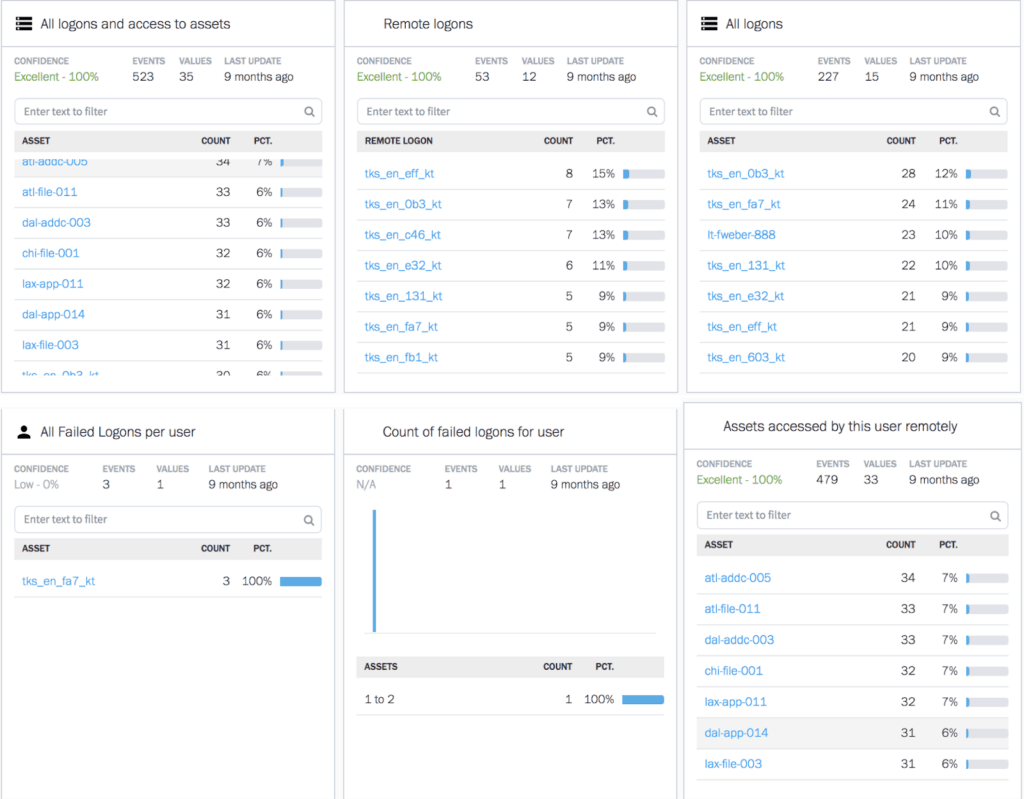
Figure 2 – Sample of behavior models shows Exabeam UEBA monitoring user logins to workstations, remote assets and also tracking failed logins for the user.
Want to learn more?
Stay tuned. This is part four of a five-part series on common issues security teams face with remote workers. Next week, we will publish a post on how to design device policies.
Part 1: Detecting Phishing Scams Disguised as Updates
Part 2: Detecting Unusual VPN Access and Best Practices to Secure VPN Services
Part 3: How to Detect Malware in the Guise of Productivity Tools
Part 4: How to Detect Fraudulent Logins and Policy Violations Using UEBA
Part 5: Best Practices for Personal and Corporate Device Usage
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












