A timeline presents the operational events underlying a security incident in sequential order. It’s a vital tool for threat hunting, investigation, and remediation by a security operations center (SOC).
Exabeam Smart Timelines™ (Figure 1, below) are machine-created. They depict user and device behavior to further reduce the time and specialization required to detect attacker tactics, techniques, and procedures (TTPs).
This automation is a major shift from legacy security information and event management (SIEM) solutions, which require skilled SOC staffers to manually correlate events—often from obscure raw log data pulled from multiple sources. Smart Timelines eliminate the time wasted on this manual effort. They graphically show the full scope of user and device activity (including all related normal behavior) to quickly pinpoint anomalous behavior and risk.
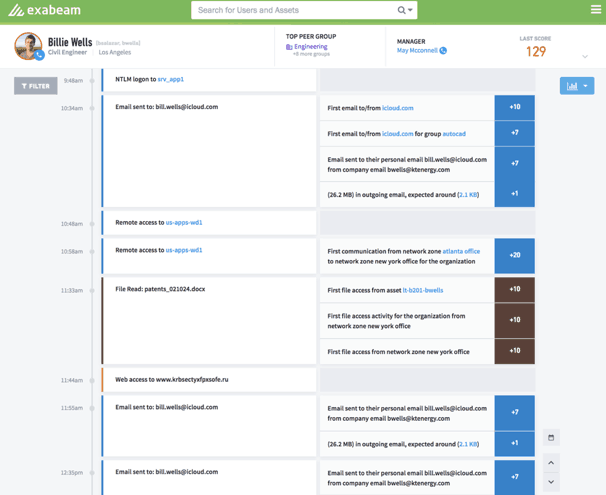
Having an instant graphical timeline of all relevant events, coupled with plain language explanations is the pinnacle of SIEM timeline creation. This capability eases the pressure of having to hire increasingly hard-to-find, skilled staff typical for many other SIEMs. Exabeam’s modern approach reduces the time, effort, and skill historically needed for security management.

Smart Timelines also enable new benefits for the enterprise:
1. Collect Unlimited Data
Security management improves as the amount of information available to analysts increases. This is analogous to a traditional crime scene, where investigators benefit from having more clues. Exabeam helps analysts get the clearest picture of user and asset activity by ingesting logs from more than 300 vendors.
Unlike most SIEM and log management vendors, Exabeam doesn’t set its price based on log volume. Instead, the collection of logs underlying Smart Timelines is based on the number of users and/or devices, which enables better security at a predictable, budget-friendly SIEM cost.
2. Collect Log Data from Any Source
The cryptic nature of log files means that a lot of work and normalization is usually required to ingest disparate data into a SIEM. But not with Exabeam; it provides customers with over 2,200 built-in parsers representing over 300 vendors to help quickly make sense of logs. If a parser doesn’t already exist for a particular data source, customers can quickly obtain one—usually within days—simply by sending log samples to Exabeam.
3. Normalize Obscure Data
Automatic identification of nearly 100 commonly occurring events for Smart Timelines is enabled by an abstraction layer. It maps log information to event type, making it easy for analysts to quickly understand what a user or device did during any session.
4. Automatically Add Context
Data from log files tell only part of an event’s story. Exabeam enriches event data in thousands of ways by adding information that wasn’t in the log source. Creation of a data graph for each event helps analysts automatically fill in missing holes within log data. This happens in real time with machine learning—often using millions of logs from thousands of users and devices that are constantly changing IP addresses.
Context is critical for identifying lateral movement by attackers. Smart Timelines present context in plain language to simplify comprehension, even for tier 1 analysts.
5. Organize Events
Smart Timelines organize events by user sessions, with defined start and end times. A typical session might comprise a work day, during which user or device activities are tracked throughout your network environment.
6. Define Normal Behavior
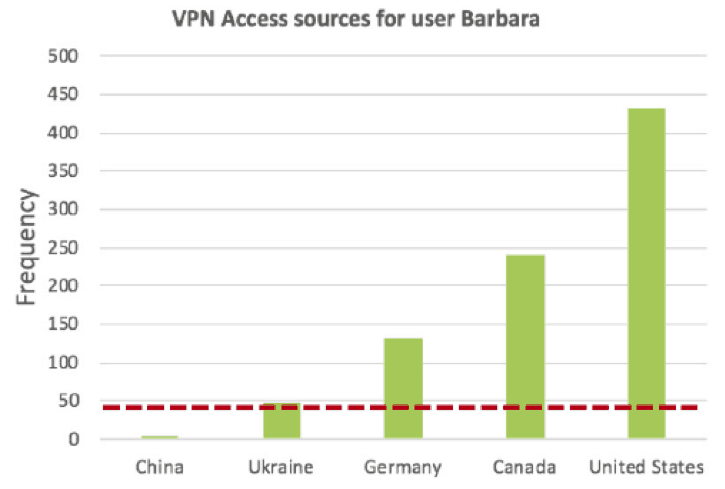
Understanding what constitutes normal behavior is the baseline for identifying that which is anomalous. Exabeam uses machine learning and rules to perform this automatically. An example is one that baselines VPN log-in behavior, examining such factors as where a user typically logs in, their role, peer group behavior, privilege level, and risk severity. For example, data for user Barbara would be normal except for her log-in from China (Figure 3).
7. Detect Anomalies While Minimizing False Positives
Triggering an alert typically requires various anomalies in different dimensions. Here, the system triggers an alert if the total risk score for multiple models exceeds a predetermined value. In this manner, Smart Timelines dramatically minimize false positives and help analysts focus their attention on quickly detecting unknown threats.
8. Score Risk for Anomalous Activity
With Smart Timelines, models assign risk scores for specific users whose observed event patterns sufficiently differ from their past patterns. Cross-user comparisons are also created to normalize behavior. Thresholds are established for different types of events, and models factor in varying weights for the importance of each anomaly type.
9. Enable Insight without Knowing Data Science
Exabeam developed Smart Timelines with analysts in mind. They have a very intuitive user interface and require no data science knowledge. This lets more junior analysts perform investigations that might have otherwise required the attention of someone more senior.
All the benefits of Smart Timelines are included with every Exabeam SIEM subscription.
See these resources for more information on modern SIEMs:
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!