SIEM Security Explainers:
Battling Cyber Threats Using Next-Gen SIEM and Threat Intelligence
Exabeam Threat Intelligence Services (TIS) with SIEM: While SIEMs are central for SOC cybersecurity, SIEMs are often not enough. With the growing sophistication of organized, modern cyber attackers and their highly-targeted techniques, organizations can be left with serious vulnerabilities using SIEM alone.
While SIEMs are central for SOC cybersecurity—collecting logs and data from multiple network sources for evaluation, analysis, and correlation of network events for threat detection—SIEMs are often not enough. With the growing sophistication of organized, modern cyber attackers and their highly-targeted techniques, organizations can be left with serious vulnerabilities using SIEM alone. To best identify and stop cyber attackers and increase the capabilities of their SIEM security, organizations need a full arsenal of tools that will help them understand how attackers think, work, and what they are after.
Threat Intelligence in Addition to SIEM
By using threat intelligence in addition to SIEM, organizations can create greater visibility into their threat landscape, providing the needed context for monitoring and determining the actions of bad actors, and determining where organizations may be most vulnerable from an attack.
So, exactly what is threat intelligence? According to Gartner, “Threat intelligence is evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice about an existing or emerging menace or hazard to assets, which can be used to inform decisions regarding the subject’s response to that menace or hazard.”
“SIEM and threat intelligence feeds are a marriage made in heaven, according to Anton Chuvakin, Research VP and Distinguished Analyst, Gartner. “Indeed, every SIEM user should send technical TI feeds into their SIEM tool.”
When Using Threat Intelligence Falls Short
Many organizations benefit by using threat intelligence to better help them prioritize, guide, and add value to their SIEM. However, they may struggle understanding how to do this effectively.
Many organizations rely on legacy, signature-based intelligence feeds that are insufficient. A deeper contextual understanding of the origin and scoring process of the intelligence feeds is needed so that the intelligence can be used properly instead of being not just noise.
In addition, even the best analysts have limitations and struggle with the volume of information coming at them such as the tremendous volume of false alerts. And with the analyst skills shortage, getting the right talent is always a challenge. And finally, too often SOCs turn on the threat intelligence within their SIEM, but then quickly turn it off again due to the barrage of alerts and false positives.
Benefits of Combining SIEM and Threat Intelligence
Implemented correctly, SIEM integrated with threat intelligence can improve your organizations defenses, save time, and help you make better strategic security decisions. Here are some benefits:
- Faster detection – By combining internal intelligence gathered by a SIEM with threat intelligence, organizations have a way to empower real-time threat identification. Applying threat intelligence to the process of uncovering potential indicators of compromise helps deliver powerful security capabilities.
- Improved response – With an integrated threat intelligence mechanism and built-in rules, organizations can contextualize data and get a better understanding of threats for actionable insights.
- Improved productivity – It can help to automate previously manual tasks and improve productivity in security operations.
Exabeam Threat Intelligence Services (TIS)
Exabeam Threat Intelligence Services (TIS) provides real-time, actionable insight into potential threats, which SOCs need, by uncovering indicators of compromise (IOC) and malicious hosts.
Exabeam is the first enterprise SIEM to fully integrate natively developed threat intelligence services directly into their SIEM platform and all of its workflows.
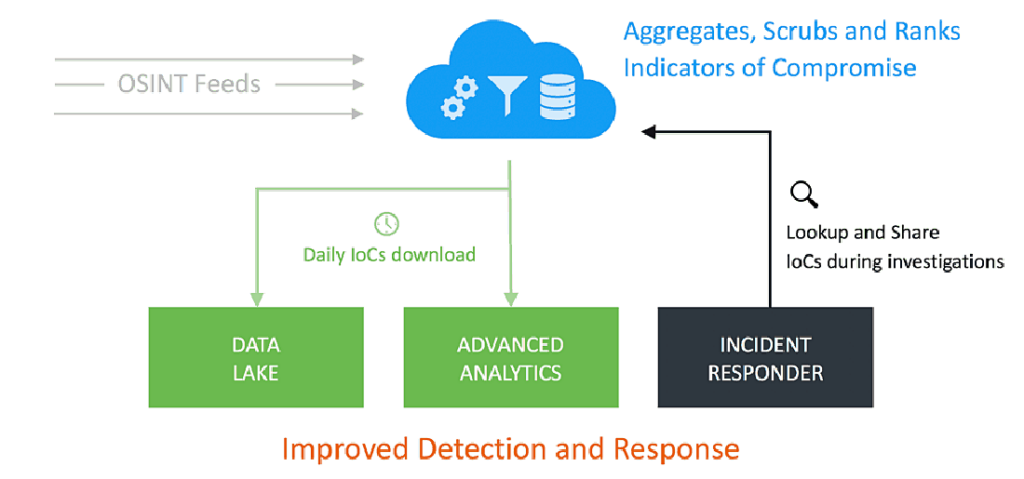
Exabeam TIS automatically leverages IP and domain reputation without needing to install apps, write scripts, or alter workflows. TIS can be used in correlation rules or behavioral analysis models to add risk to notable users and entities. For example, you can add rules to automatically receive alerts if any IP from the Threat Intelligent Service is found in your environment, or it can be used for analytics to add to the risk-scoring algorithm.
Exabeam Threat Intelligence Services is pre-configured out-of-the-box and provides new security capabilities at no added cost or impact to customers. With the threat intelligence feed integrated directly into your SIEM, you always have the most up-to-date threat intelligence, enabling you to quickly identify and mitigate new and emerging attacks.
See Exabeam in action: Request a demo






