Recently, the CyberEdge Group released its 2017 Cyberthreat Defense Report, a survey of 1,100 IT security professionals on topics ranging from cyber-attack trends and security investment, to tool effectiveness and security best practices.
Of course there were a lot of interesting findings in this year’s report, however the part that really caught my eye was the chart on “top barriers to establishing an effective cyber threat defense”. As part of the report, respondents were asked to rate which items were the biggest barriers inhibiting their organization from adequately defending themselves against cyber threats.
Here are the results:
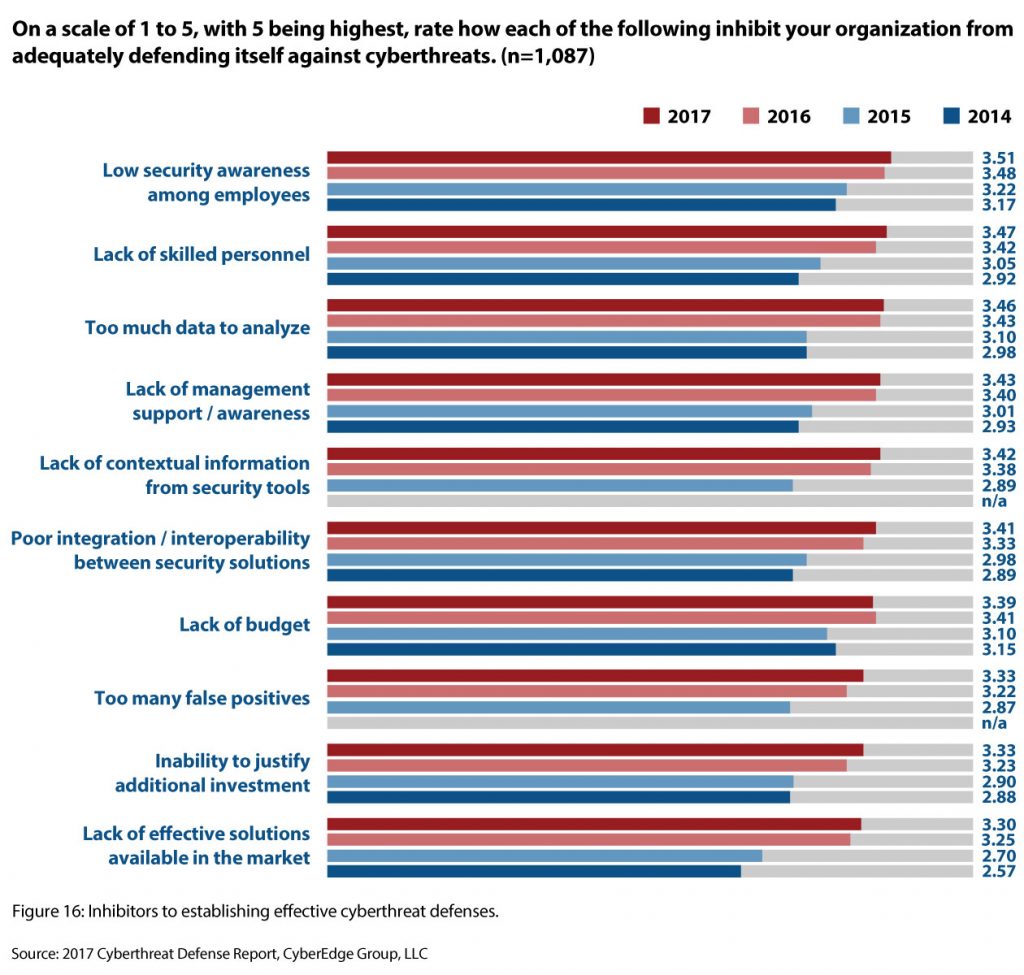
This part of the report really resonated with me because I frequently hear many of these same sentiments from prospects as key pain points of their current security programs. It appears that despite (or perhaps as a byproduct of) an ever increasing investment in security, these problems persist.
Behavioral Analytics Isn’t Just for Detection
When most people think about User and Entity Behavior Analytics (UEBA), they probably think of it as a detection tool. In fact, this mindset was even proven in the results of the survey. The top 4 reasons for implementing UEBA were detection related. Here’s how the respondents were reportedly using their UEBA tools:
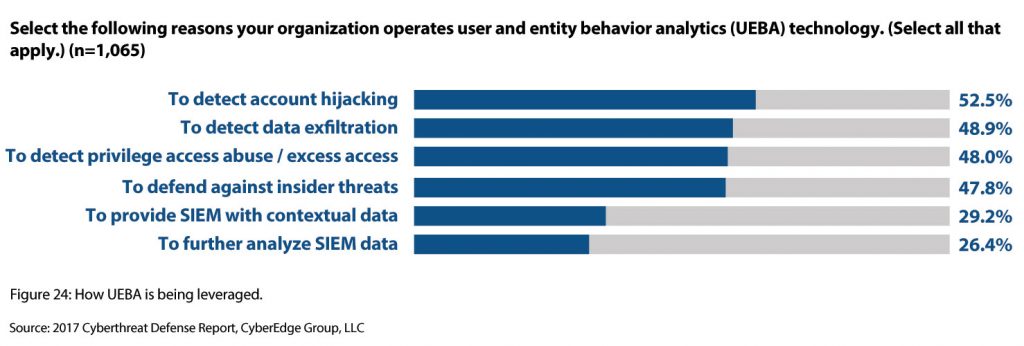
I’m certainly not going to say that this is the wrong way to think about UEBA. In fact, I’d argue that detection IS the primary function of the technology. With that said, I also think that the core technology used in effective UEBA tools – machine learning, statistical analysis, behavioral modeling, etc. – can also have other broader applications that can help streamline security programs and eliminate some of the barriers security practitioners face.
Easing Staffing Shortages
To illustrate my point about UEBA technology, let’s briefly return to the list of barriers I shared above. On this list, we can see the second highest ranked item on the list was “Lack of Skilled Personnel.” The problem here is really twofold – there’s too much work for existing staff to handle and we can’t hire enough skilled talent to sufficiently expand our team.
By reducing workloads through alert prioritization and false positive reduction, streamlining analyst workflows, enriching contextual information about incidents, and automating the creation of incident timelines UEBA is able to greatly increase the productivity of SOC teams. The net result is being able to do more with your existing staff, thus easing hiring pressure to acquire new talent amidst a skills shortage.
Watch Webinar Recording
In our webinar titled “7 Ways UEBA Breaks Down Barriers in Traditional Cyber Defense”, we take a deeper dive into this example as well as cover six other ways to use UEBA to help streamline security programs by breaking down common barriers.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












