Quality over quantity
It is a common pitfall that security information and event management (SIEM) vendors often encourage customers to input more and more data. But when it comes to solving a particular use case, you don’t always need large amounts of data — you need the right data. Simply ingesting large amounts of data can give a false sense of security and “coverage,” but what data are being logged and analyzed is far more important than how much. It can be challenging to answer the “what” — particularly if you are trying to add a new data source and are at or beyond your current license storage limits.
This blog post will shed light on this paradox and guide you through the process of identifying and leveraging the right data for your cybersecurity needs.
In this article:
- Understand the value of the data
- Detailing use case coverage with Outcomes Navigator
- Unveiling New-Scale SIEM™
Understand the value of the data
It is important to understand the value of the data being sent. This means verifying those logs are being ingested and parsed successfully, and understanding how they map directly to business risk and security goals via use case coverage. When SIEM solutions were introduced years ago, most of what they analyzed were firewall logs and Intrusion Detection System (IDS) logs, along with the occasional host-based IDS log. Today, many organizations focus myopically on only endpoint solutions and ignore Active Directory (AD) or VPN traffic entirely. The truth is that, for most use cases, you need to see a variety of logs from many different security systems — but not every field from every log contributes equally to seeing the complete attack picture.
Detailing use case coverage with Outcomes Navigator
Outcomes Navigator, part of the Exabeam Security Operations Platform, offers security engineers and security leaders an interactive view of the strength of coverage based on their licensing, and maps to the MITRE ATT&CKⓇ framework. Customers can compare their current scored coverage, including custom and pre-built dashboards, report rules (both custom and native) to available product coverage, and understand how to close the gap between their current coverage and their desired security goals. Outcomes Navigator organizes use cases into three main categories: compromised insiders, malicious insiders, and external threats.
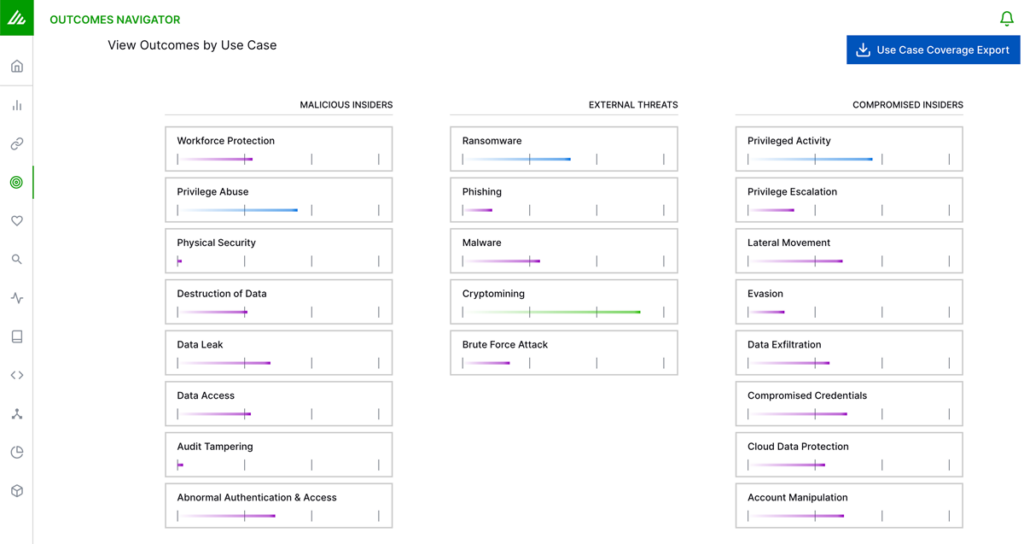
For each use case, a detailed view shows:
- Which other use cases are in the same category
- What is your current coverage for each category (None, Good, Better, Best)
- Which data sources support each use case, and which data sources you are currently bringing in and parsing
- Which rules in each use case are receiving the necessary data to trigger (satisfied) versus rules that are just enabled
- How well those data sources are being parsed in support of that use case
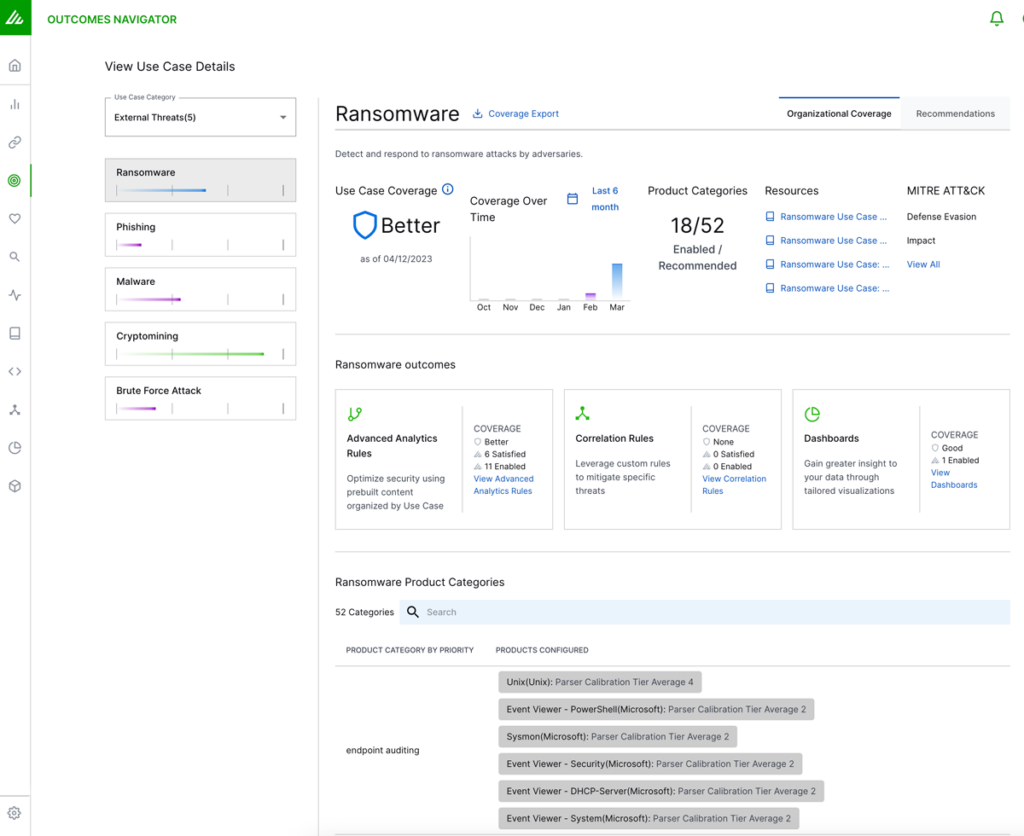
Outcomes Navigator will provide recommendations for improving your coverage of each use case, including:
- For desired security goals (use cases), which additional data sources would improve your visibility and coverage
- Which data sources would benefit from improved field parsing
- Verifying that your data sources are not being inadvertently excluded by filtering
Unveiling New-Scale SIEM™
Traditional SIEM solutions require complicated searching and reports to answer two basic questions:
- Am I sending enough data?
- Am I sending the right data?
Exabeam has developed a new approach to quickly and effectively answer these questions: New-Scale SIEM™. This new approach enables you to quickly understand what coverage is available from Exabeam, what your current coverage level is to support your security goals, or how much value are you getting from your data currently and how to improve in key areas — all with 100% self-service tools provided by Exabeam. With this added insight, security teams can get more value from their security investment and vastly improve their security posture.
Want to learn more about improving your cybersecurity?
Download our guide, 7 Best Practices for Secure Enterprise Log Management.
Log management is fundamental to enterprise cybersecurity, but many log management solutions are out-of-date or were never intended to address today’s security challenges in cloud and hybrid environments.
Organizations need to quickly identify and resolve incidents from vast log repositories, discovering threats that impact organizational security as well as compliance mandates. This guide presents seven best practice requirements for secure enterprise log management to make log data at scale actionable so organizations can quickly address these issues.
Learn what enterprises should insist on when considering log management solutions for today’s hyperscale cloud and hybrid world, including:
- Easy configuration, management, and monitoring of data transport into the log management system at scale from all data sources
- Analytics enriched with context such as threat intelligence, providing the ability to write correlation rules against IoCs
- Simple and intuitive search with fast query performance at big-data scale

Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













