The SolarWinds compromise that affected multiple key federal agencies brings into focus the weaknesses of legacy log management and SIEM platforms. A big part of the compromise involved compromised credentials — once the attackers got in, they moved laterally, with the malicious use of multiple user identities. Insider threats isn’t a new concept for federal agencies and it’s been on the radar long enough that guidelines have even been released on how to address and we’ve talked about it before.
Federal agencies are particularly challenged around insider threats. Internally, these organizations look to address whistleblower and confidential information leaks while externally combatting nation-states and other malicious actors trying to gain access to extremely large amounts of data. And with limited budget and personnel, government agencies offer an attractive target for adversaries that are aware these agencies might not have as many resources for their security program.
This brings me back to one of the biggest weaknesses of legacy SIEM tools: correlation rules are static, too coarse (only indicate whether something did or didn’t occur), and not enough to detect modern insider threats and compromised credentials. GovCon expert Chuck Brooks says in his wishlist for the U.S. government: “Agencies are also looking at behavioral identifiers bolstered by machine learning and artificial intelligence to detect and mitigate insider threats. It is an area that needs more attention in government as well as industry as data is continually being breached as a result of human activities.”
A modern solution should not only be simple and easy-to-use to save analysts time when threat hunting, but also be dynamic in correlating and identifying threats, especially when low and slow attacks don’t trigger static correlation rules. These kinds of threats can only be detected with risk and behavioral rules and identifiers that don’t exist in legacy SIEMs.
Here are three requirements federal agencies should look for in modern SIEM platforms.
Requirement #1: Anomalous behavior is detected with machine learning and statistical analysis and not reliant on only static correlation rules
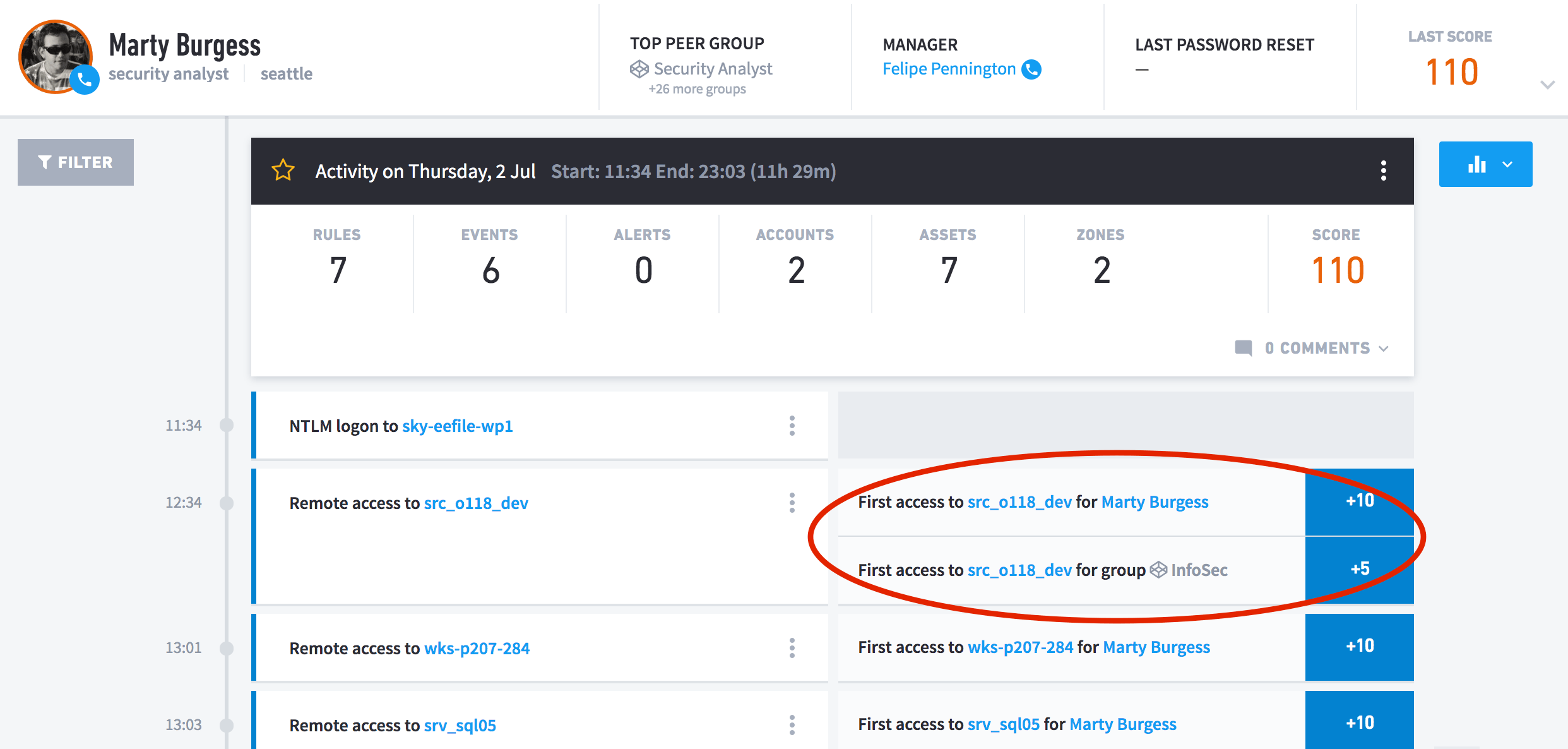
Figure 1: Drive-by Compromise technique shown in Exabeam Smart Timeline rule tags.
As demonstrated with the SolarWinds incident, it can be difficult to detect attacks that take time and slowly move through an agency’s network. Modern SIEM solutions should include user and entity behavior analytics (UEBA) to complement their static correlation rules. Anomalous behavior like lateral movement of compromised credentials can then be bubbled up in the same manner FireEye states in their threat research response. For example, correlation rules aren’t going to trigger based on complex behaviors where you might not know specifically what event or events define risky behavior. UEBA solutions take in security and operational data from a variety of sources to baseline “normal” behavior of users and entities in a network. Anomalous activity like accessing a server or workstation for the first time adds to a user or entity’s risk score and can send alerts to security teams to immediately investigate.
Requirement #2: Threat hunting via point-and-click + filters means easier, faster threat hunting
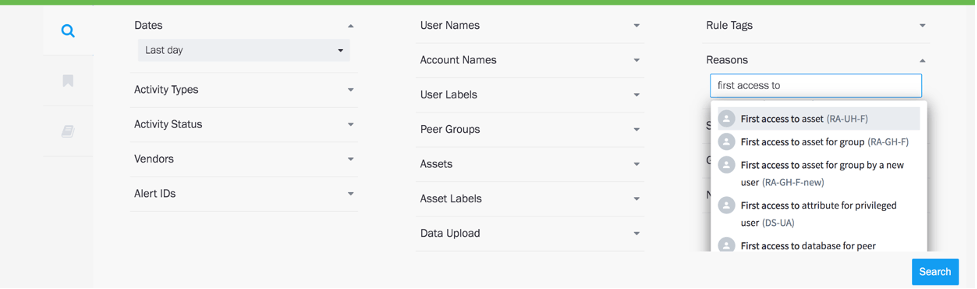
Figure 2: Threat hunting is intuitive and doesn’t involve complex queries and disparate tools.
Federal agencies already have limited resources — so any time savings across threat hunting and training is invaluable to personnel resourcing and resolving incidents and threats. As seen above in Figure 2, modern interfaces with built-in filters can be a huge time savings for security analysts. This ease of use means analysts can threat hunt on day one without having to build complex queries to check for lateral movement. Analysts should be able to focus on performing behavior-based searches, not just use an indicators of compromise (IoC)/static correlation approach. They should be able to use MITRE tactics and techniques with behavior-based searches, allowing them to layer tactics, techniques and procedures with analytics to really understand what is normal versus abnormal. For example, I’ve seen one federal agency review all after-hours anomalous activity; even when the user only had one anomalous event. Being able to easily filter and search across all activities like this should be built into a SIEM solution. This becomes critical when analysts are threat hunting with ad hoc questions like “show all users that logged into a server for the first time” (as indicated in Figure 2 above) or “find every user with a risk score greater than 20.”
Requirement #3: Data, context, and user/asset risk score is stitched into a user timeline and correlated across all systems
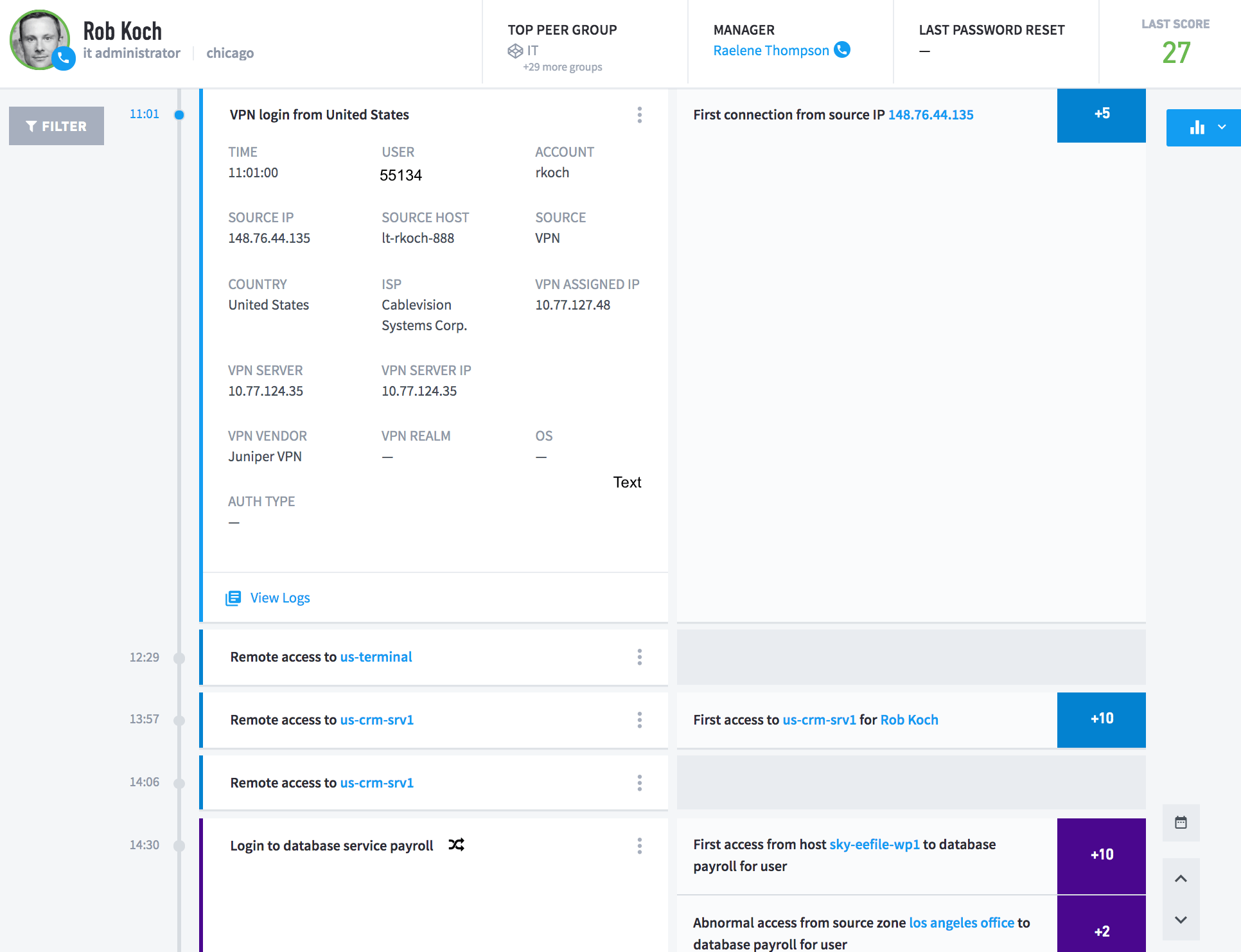
Figure 3: The user authenticated to the VPN with credential ‘55134’ and that account is mapped to ‘rkoch’.
Modern SIEMs need to not only be a single source of truth, but also be able to “stitch” together information from multiple log sources. With the massive amount of data federal agencies collect, it’s not uncommon for security teams to have to access multiple databases and tools to pull together the information they need to properly investigate incidents. The example I like to bring up is the fact that some log sources in federal organizations don’t have specific identifiers like traditional Microsoft Windows user IDs in the data. Security teams often have to log into another system to correlate the user across log sources. Finding a solution that is able to stitch everything, including user identity, into a single user timeline will give analysts a complete view of potential threats and huge time savings with their investigations.
I work with many government agencies looking to take the manual, time-consuming processes out of their threat hunting so analysts can spend more time on threats. As these agencies look at solutions and tools, I work with them to figure out how machine learning and artificial intelligence within modern solutions like Exabeam can fit in with their security training, processes, and existing tools to help keep their network and data secure across budget resource constraints.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













