What Is UEBA (User and Entity Behavior Analytics)?
User and Entity Behavior Analytics (UEBA) is a category of security solutions that use innovative analytics technology, including machine learning and deep learning, to discover abnormal and risky behavior by users, machines and other entities on the corporate network often in conjunction with a Security Incident and Event Management (SIEM) solution.
UEBA can detect security incidents that traditional tools do not see, because they do not conform to predefined correlation rules or attack patterns and span multiple organizational systems and data sources.
What is User and Entity Behavior Analytics (UEBA)?
UEBA solutions build profiles that model standard behavior for users and entities in an IT environment, such as servers, routers and data repositories. This is known as baselining. Using a variety of analytics techniques, UEBA technology can identify activity that is anomalous compared to the established baselines, discover threats and detect security incidents.
About this explainer: This is part of an extensive series of guides about cybersecurity.
Three pillars of UEBA
Gartner defines UEBA solutions across three dimensions:
- Use cases — UEBA solutions provide information on the behavior of users and other entities in the corporate network. They should perform monitoring, detection and alerting of anomalies. And they should be applicable for multiple use cases–unlike specialized tools for employee monitoring, trusted hosts monitoring, fraud, and so on.
- Data sources — UEBA solutions are able to ingest data from a general data repository such as a data lake or data warehouse, or through a SIEM. They should not deploy agents directly in the IT environment to collect the data.
- Analytics — UEBA solutions detect anomalies using a variety of analytics approaches–statistical models, machine learning, rules, threat signatures and more.
Convergence of UEBA and SIEM
There is a close relation between UEBA and SIEM technologies, because UEBA relies on cross-organizational security data to perform its analyses, and this data is typically collected and stored by a SIEM.
Gartner views UEBA as a feature incorporated into a SIEM. Behavior analysis is one of the capabilities by which Gartner evaluates the vendors in the Magic Quadrant for Security Information and Event Management. Gartner outlines the following capabilities for a SIEM:
- Aggregate event data produced by security devices, network infrastructure, systems and applications
- Combine event data with contextual information about users, assets, threats, and vulnerabilities for the purpose of scoring, prioritization and expediting investigations
- Normalize the data to analyze more efficiently
- Offer real-time analysis of events for security monitoring, advanced analysis of user and entity behaviors, querying analytics, supporting incident investigation and management, and reporting.
UEBA use cases
Insider threats
There are three types of insider threats:
- Negligent insider – A negligent insider is an employee or contractor with privileged access to IT systems, who unintentionally puts their organization at risk because they do not follow proper IT procedures. For example, someone who leaves their computer without logging out, or an administrator who did not change a default password or failed to apply a security patch. Identifying normal vs abnormal activity for a user is key to detecting a user that has been compromised by negligence.
- Malicious insider – A malicious insider is an employee or contractor with privileged access to IT systems, who intends to perform a cyber attack against the organization. It is difficult to measure malicious intent or discover it through log files or regular security events. UEBA solutions help by establishing a baseline of a user’s typical behavior and detect abnormal activity.
- Compromised insider – It’s common for attackers to infiltrate an organization and compromise a privileged user account or trusted host on the network, and continue the attack from there. UEBA solutions can help rapidly detect and analyze malicious activity that the attacker carries on via the compromised account.
Traditional security tools find it difficult to detect a compromised insider if the attack pattern or kill chain is not currently known (such as in a zero day attack), or if the attack moves laterally through an organization by changing credentials, IP addresses, or machines. UEBA technology, however, can detect these types of attacks, because they will almost always force assets to behave differently from established baselines.
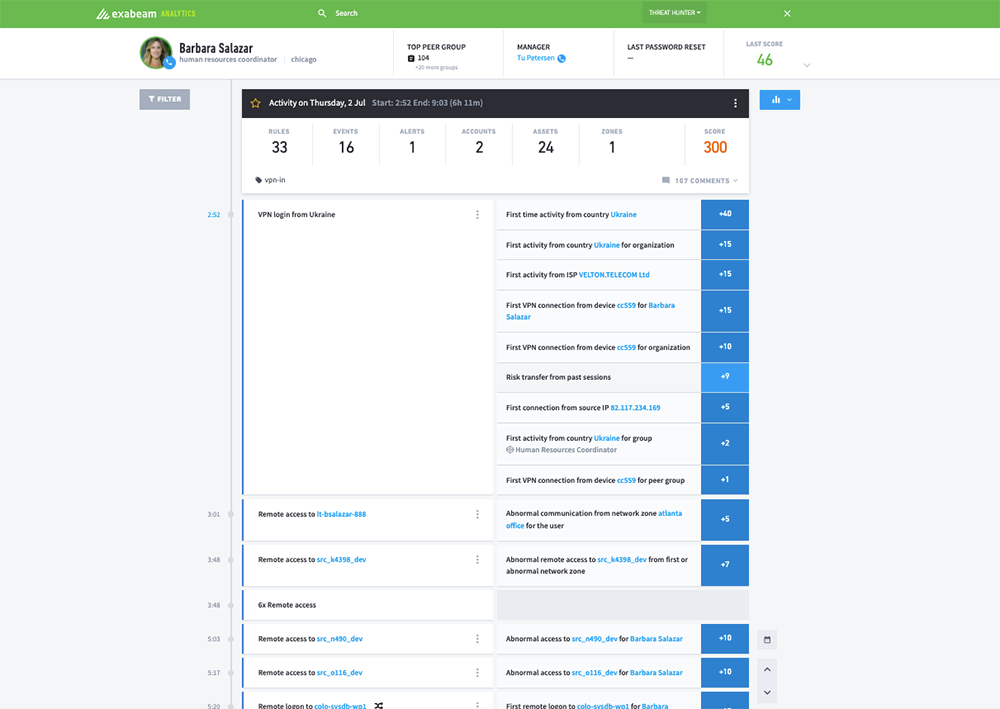
Incident prioritization
A SIEM collects events and logs from multiple security tools and critical systems, and generates a large number of alerts that must be investigated by security staff. This leads to alert fatigue, a common challenge of Security Operations Centers (SOC).
UEBA solutions can help understand which incidents are particularly abnormal, suspicious or potentially dangerous in the context of your organization. UEBA can go beyond baselines and threat models by adding data about organizational structure–for example, the criticality of assets and the roles and access levels of specific organizational functions. A small deviation from norm for a critical protected system or a top-level administrator, might be worth a look for an investigator; for a run-of-the-mill employee only a major deviation would receive high priority.
Data loss prevention (DLP) and data leak prevention
Data Loss Prevention (DLP) tools are used to prevent data exfiltration, or the illicit transfer of data outside organizational boundaries. Traditional DLP tools report on any unusual activity carried out on sensitive data–they create a high volume of alerts which can be difficult for security teams to handle.
UEBA solutions can take DLP alerts, prioritize and consolidate them by understanding which events represent anomalous behavior compared to known baselines. This saves time for investigators and helps them discover real security incidents faster.
Entity analytics (IoT)
UEBA can be especially important in dealing with Internet of Things (IoT) security risks. Organizations deploy large fleets of connected devices, often with minimal or no security measures. Attackers can compromise IoT devices, use them to steal data or gain access to other IT systems, or worse–leverage them in DDoS or other attacks against third parties.
Two sensitive categories of IoT are medical devices and manufacturing equipment. Connected medical devices may contain critical data, and may be life threatening if used directly for patient care. Manufacturing equipment can cause large financial losses if disrupted, and in some cases may threaten employee safety.
UEBA can track connected devices, establish a behavioral baseline for each device or group of similar devices, and immediately detect if a device is behaving outside its regular boundaries. For example:
- Connections to or from unusual addresses or devices
- Activity at unusual times
- Device features activated which are typically not used
UEBA analytics methods
Some UEBA solutions rely on traditional methods to identify suspicious activity. These can include manually-defined rules, correlations between security events and known attack patterns. The limitation of traditional techniques is that they are only as good as the rules defined by security administrators, and cannot adapt to new types of threats or system behavior.
Advanced analytics involves several modern technologies that can help identify abnormal behavior even in the absence of known patterns:
- Supervised machine learning–sets of known good behavior and known bad behavior are fed into the system. The tool learns to analyze new behavior and determine if it is “similar to” the known good or known bad behavior set.
- Bayesian networks–can combine supervised machine learning and rules to create behavioral profiles.
- Unsupervised learning–the system learns normal behavior, and is able to detect and alert on abnormal behavior. It will not be able to tell if the abnormal behavior is good or bad, only that it deviates from normal.
- Reinforced / semi-supervised machine learning–a hybrid model where the basis is unsupervised learning, and actual alert resolutions are fed back into the system to allow fine tuning of the model and reduce the signal-to-noise ratio.
- Deep learning–enables virtual alert triage and investigation. The system trains on data sets representing security alerts and their triage outcomes, performs self-identification of features, and is able to predict triage outcomes for new sets of security alerts.
Traditional analytics techniques are deterministic, in the sense that if certain conditions were true, an alert was generated, and if not the system assumed “all is fine”. The advanced analytics methods listed above are different in that they are heuristic. They compute a risk score which is a probability that an event represents an anomaly or security incident. When the risk score exceeds a certain threshold, the system creates a security alert.
How UEBA works
User and entity behavior analytics (UEBA) is a category of cybersecurity solutions or capabilities that analyze user and entity behavior and apply advanced analytics and behavioral modeling to determine anomalous behavior. UEBA is used to discover advanced security threats like malicious insiders and privileged account compromises, which traditional, rule-based security tools cannot see. UEBA solutions ingest operational data from many sources and determine what is the normal behavior of any user or non-human entity. Entities may include IT assets such as hosts, applications, network traffic, service accounts, and data repositories. Over time, the solution builds standard profiles of behavior for users and entities across peer groups to create a baseline for what is normal in an organization. When anomalous activity is identified, it is assigned a risk score. The score rises with increasing amounts of anomalous behavior until it crosses a predefined threshold triggering an alert to security analysts. Some solutions can automate response actions.
Holistic analysis across multiple data sources
The true power of a UEBA solution is in its ability to cut across organizational boundaries, IT systems and data sources and analyze all the data available for a specific user or entity.
A UEBA solution should analyze as many data sources as possible, some example data sources include:
- Authentication systems like Active Directory
- Access systems like VPN and proxies
- Configuration Management Databases
- Human resources data–new employees, departed employees, and any data that provides additional context on users
- Firewall, Intrusion Detection and Prevention Systems (IDPS)
- Anti-malware and antivirus systems
- Endpoint Detection and Response systems
- Network Traffic Analytics
- Threat Intelligence feeds
For example, a UEBA solution should be able to identify unusual login via Active Directory, cross reference it with the criticality of the device being logged onto, the sensitiveness of the files accessed, and recent unusual network or malware activity which may have enabled a compromise.
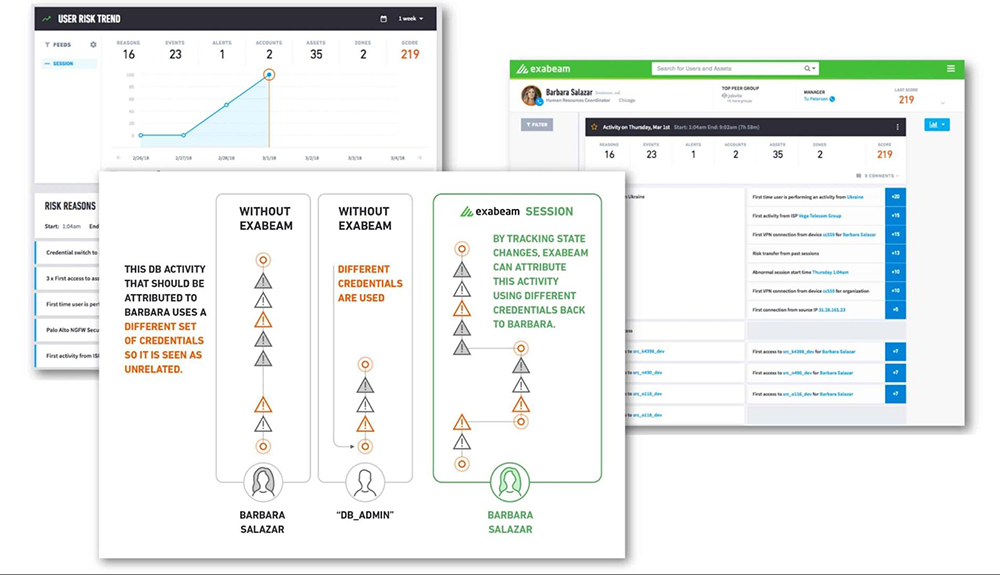
Behavioral baselining and risk scores
A UEBA solution learns normal behavior to identify abnormal behavior. It examines a broad set of data to determine a user’s baseline or behavioral profile.
For example, the system monitors a user and sees how they use a VPN, at what time they arrive to work and which systems they log into, what printer they use, how often and what size of files they send by email or load to a USB drive, and many other data points that define the user’s “normal behavior”. The same is done for servers, databases or any significant IT system.
When there is deviation from the baseline, the system adds to the risk score of that user or machine. The more unusual the behavior, the higher the risk score. As more and more suspicious behavior accumulates, the risk score increases until it hits a threshold, causing it to be escalated to an analyst for investigation.
This analytical approach has several advantages:
- Aggregation – the risk score is made up of numerous events, so there is no need for analysts to manually review large numbers of individual alerts and mentally combine them to detect a threat.
- Reduced false positives–one slightly abnormal event on its own will not result in a security alert. The system requires multiple signs of abnormal behavior to create an alert, reducing the number of false positives and saving time for analysts.
More context — traditional correlation rules defined by security administrators may have been correct for one set of users or systems, but not for others. For example, if a department starts employing shift workers or offshore workers, they will start logging in at unusual times, which would trigger a rule-based alert all the time. UEBA is smarter because it establishes a context-sensitive baseline for each user group. An offshore worker logging in at 3am local time would not be considered an abnormal event.
Timeline analysis and session stitching
When analyzing security incidents, the timeline is a critical concept which can tie together seemingly unrelated activities. Modern attacks are processes, not isolated events.
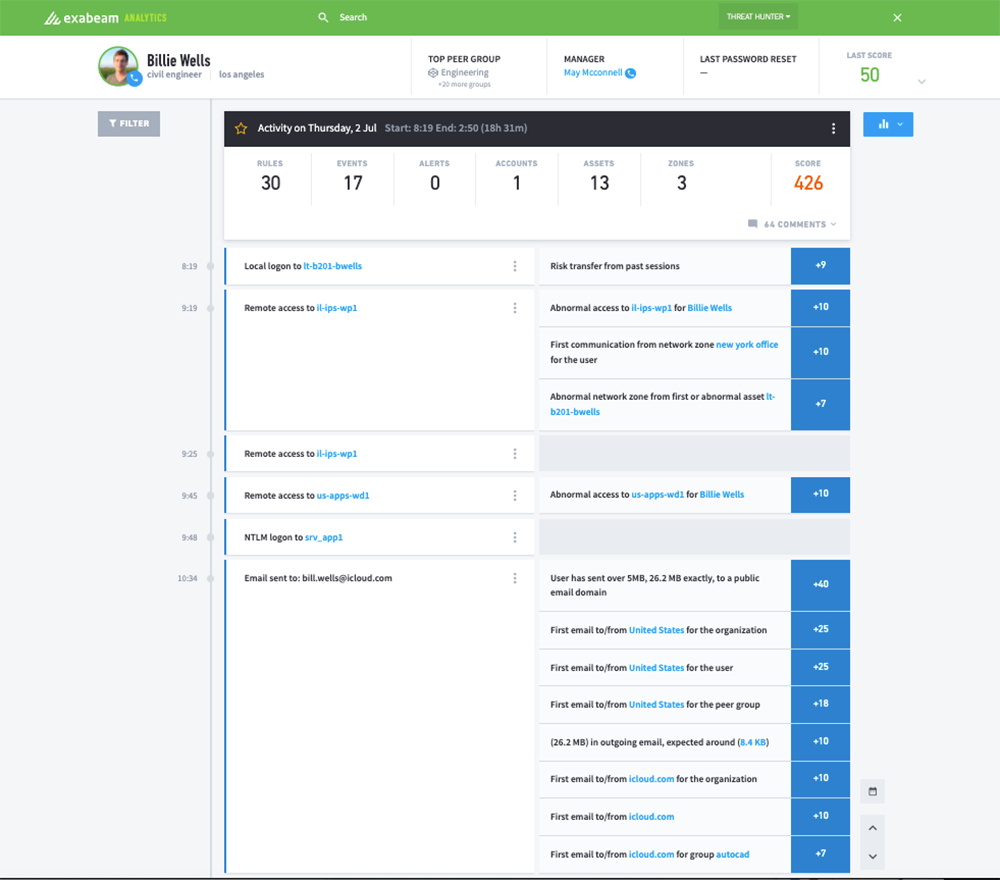
Advanced UEBA solutions can “stitch” together data from different systems and event streams, to construct the complete timeline of a security incident.
For example, consider a user who logged in, performed suspicious activity and then disappeared from the logs. Was the same IP used to connect to other organizational systems shortly afterwards? If so, this could be part of the same incident, with the same user continuing their attempt to penetrate the system. An additional example could be an attacker logging in to the same machine multiple times using different credentials. This also requires “stitching” together data about the various login attempts and flagging them as a single incident.
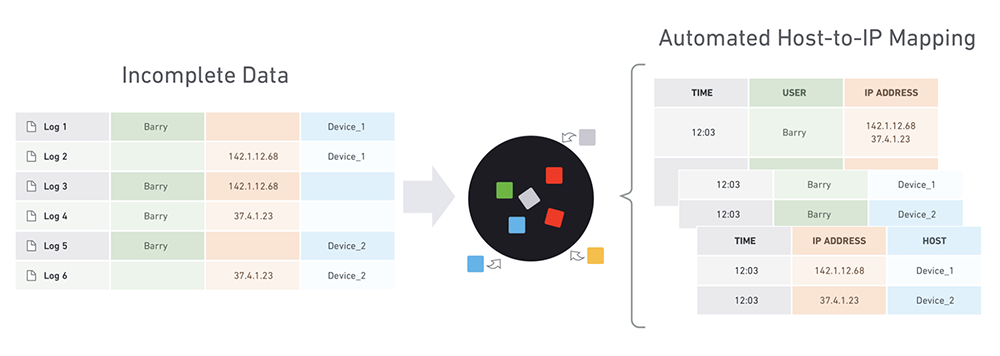
Once a UEBA solution stitches together all relevant data, it can assign risk scores to any activity along the event timeline.

Example of an integrated SIEM and UEBA solution
Several systems are deployed in the field which combine the breadth of data in a SIEM with the deep analytics made possible by cutting-edge UEBA engines.
One example of an integrated system is the Exabeam SOC Platform. Exabeam is a full SIEM solution based on modern data lake technology. In addition, it provides the following UEBA capabilities:
- Rule and signature-free incident detection — Exabeam uses advanced analytics to identify abnormal and risky activity without predefined correlation rules or threat patterns. It provides meaningful alerts without requiring heavy setup and fine tuning, and with lower false positives.
- Automatic timelines for security incidents — Exabeam can stitch together related security events into a timeline that shows a security incident, spanning multiple users, IP addresses and IT systems.
- Dynamic peer groupings — Exabeam not only performs behavioral baselining of individual entities, it also dynamically groups similar entities (such as users from the same department, or IoT devices of the same class), to analyze normal collective behavior across the entire group and detect individuals who exhibit risky behavior.
- Lateral movement detection — Exabeam detects attackers as they move through a network using different IP addresses, credentials and machines, in search of sensitive data or key assets. It ties together data from multiple sources to connect the dots and view the attacker’s journey through the network.
See Additional Guides on Key Cybersecurity Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of cybersecurity.
What Are TTPs
Authored by Exabeam
- What is Lateral Movement and How to Protect Against It | Exabeam
- What Are TTPs and How Understanding Them Can Help Prevent the Next Incident
Medical Device Cyber Security
Authored by Sternum
- Post-Market Surveillance for Medical Devices: Ultimate 2024 Guide
- Understanding Medical Device Regulation and Cybersecurity Standards
Zero-Day Attack
Authored by Cynet






