UEBA Tools: Key Capabilities and 7 Tools You Should Know
What Are UEBA (User and Entity Behavior Analytics) Tools?
UEBA tools are software systems that use machine learning and statistical methodologies to identify anomalous behavior or instances within a network. These tools are responsible for some of the earliest uses of artificial intelligence (AI) in security operations. They operate by analyzing and learning from historical data to establish a baseline of normal behavior. This baseline is then used to detect deviations or anomalies that could indicate a potential security threat.
These tools do not rely on predefined security rules or signatures. Instead, they use machine learning algorithms to continuously learn and adapt to new patterns and behaviors. This makes them highly effective at detecting unknown threats, such as compromised credentials, zero-day exploits and advanced persistent threats (APTs), which traditional security solutions may miss.
Furthermore, UEBA tools analyze not just user behavior, but also entity behavior. This means they can monitor and analyze the behavior of devices, applications, and network traffic—essentially, any entity that is part of an organization’s digital ecosystem. This holistic approach allows for a much more comprehensive and accurate threat detection and response.
The leading EUBA tools provide robust detection capabilities, combined with greater insights for investigation and response. They also provide automated incident timelines, which highlight events by risk, along with more dynamic alerting techniques which allow analysts to prioritize the triage of 3rd-party alerts with greater precision.
Key Features of UEBA Tools
Machine Learning (ML) and Analytics
UEBA tools leverage machine learning to analyze vast amounts of data in real-time, enabling them to identify subtle patterns and correlations that may be indicative of a security threat. This represents one of the earliest uses of ML in security operations.
These algorithms can learn from historical data to establish a baseline of normal behavior for users and entities within the network. Any deviations from this baseline are flagged as potential threats. This ability to learn and adapt over time makes UEBA tools highly effective at detecting new and evolving threats.
Moreover, the use of advanced analytics allows these tools to sift through the noise and focus on the most critical threats. They can prioritize alerts based on the severity of the threat and the value of the affected assets.
Data Ingestion and Cross-Vendor Integration
UEBA tools can ingest and analyze vast amounts of data from a variety of sources. These include log files, network traffic data, identity information, and threat intelligence feeds.
Moreover, UEBA tools have robust cross-vendor integration capabilities. This means they can seamlessly integrate with other security tools and systems, creating a unified security infrastructure. Systems typically integrated with UEBA tools are SIEM (Security Information and Event Management), IDS (Intrusion Detection System), and firewalls. The leading UEBA products offer an integrated solution, working together within a SIEM.
Real-Time Monitoring and Alerting
UEBA tools offer real-time monitoring and alerting capabilities. They continuously analyze network activity, allowing them to detect threats as they occur. This is crucial in today’s threat landscape, where threats can proliferate and cause damage in a matter of minutes. Once a threat is detected, UEBA tools can send out alerts in real-time, enabling security teams to respond swiftly and mitigate the threat before it can cause significant damage. In some cases, higher severity alerts can trigger response actions using automation.
Threat Hunting Capabilities
In addition to real-time threat detection, UEBA tools also support threat hunting. This proactive approach to cybersecurity involves searching for threats that may have evaded traditional detection methods. With UEBA tools, security teams can conduct in-depth investigations into suspicious activities earlier in the attack cycle to uncover hidden threats.
These tools provide a wealth of data and analytics that can aid in threat hunting. They can reveal patterns of behavior that may indicate a coordinated attack, identify relationships between different entities that could signify a compromised device, and provide insights into the tactics, techniques, and procedures (TTPs) used by attackers. Some of the leading solutions provide sophisticated threat hunting capabilities, allowing hunters to search across known anomalies uncovered by the UEBA.
Visualization and Reporting Tools
UEBA tools come equipped with visualization and reporting tools. They provide a visual representation of the network and its activity, making it easier for security teams to understand the current threat landscape. They can visualize patterns and trends, identify hotspots of activity, and track changes over time.
Additionally, UEBA tools provide detailed and actionable reporting on the detected threats. They can generate reports on various metrics, such as the number and types of threats detected, the affected assets, the response times, and more. These reports can aid in decision-making and strategic planning, helping organizations enhance their cybersecurity posture.
Automation and Orchestration
Finally, a key feature of modern UEBA tools is their ability to automate and orchestrate various security tasks. Automation allows these tools to execute predefined actions automatically when certain criteria or thresholds are met. For example, if the system detects multiple failed login attempts from a user within a short period, it can automatically lock the account to prevent unauthorized access.
The orchestration capabilities work in tandem with automation to streamline the workflow of security operations. Through orchestration, UEBA tools can interact with other security solutions like firewalls, endpoint protection platforms, and incident response tools. This integration enables a coordinated and rapid response to detected threats. For instance, when a UEBA tool detects unusual data movement that could be indicative of data exfiltration, it can trigger the firewall to block the suspicious IP address involved, all without human intervention.
Related content: Learn more in our detailed guide to UEBA incident response.
Notable UEBA Tools
There are several UEBA tools available in the market today. Let’s review the key capabilities of six popular options.
1. Exabeam
Exabeam is an AI-driven security operations platform that leverages integrated user and entity behavioral analytics to protect organizations from cyberthreats and advanced attack techniques. This tool uses machine learning and behavioral modeling to identify abnormal activities and alert security teams in real-time based on risk.
Exabeam goes beyond threat visibility, also offering actionable insights that can help you respond effectively to incidents. Its advanced analytics capabilities allow for detailed forensic investigations, making it easier to understand the context of security events. Additionally, Exabeam can integrate with existing security infrastructure, enhancing its efficiency and effectiveness.
The Exabeam platform is cloud-native, designed to be user-friendly, making it suitable for businesses of all sizes and budgets. It offers a streamlined threat detection, investigation, and response (TDIR) workflow, and leverages intelligent automation that enables security teams to respond quickly and effectively to threats.
Learn more about Exabeam Security Analytics
2. Micro Focus Interset UEBA
Micro Focus Interset UEBA uses advanced analytics and machine learning to detect and respond to threats. It provides real-time threat detection and prioritizes alerts based on risk, ensuring that security teams focus on the most critical threats.
Micro Focus Interset UEBA can adapt to changing environments. It learns from your organization’s data, enabling it to identify new threats and patterns as they emerge. It also offers flexible deployment options, including cloud and on-premises, and an intuitive user interface that makes it easy to navigate and understand threat data.
3. Splunk User Behavior Analytics
Splunk User Behavior Analytics helps organizations detect insider threats, targeted attacks, and fraud. It offers visibility into user behavior, enabling security teams to identify and respond to anomalies quickly.
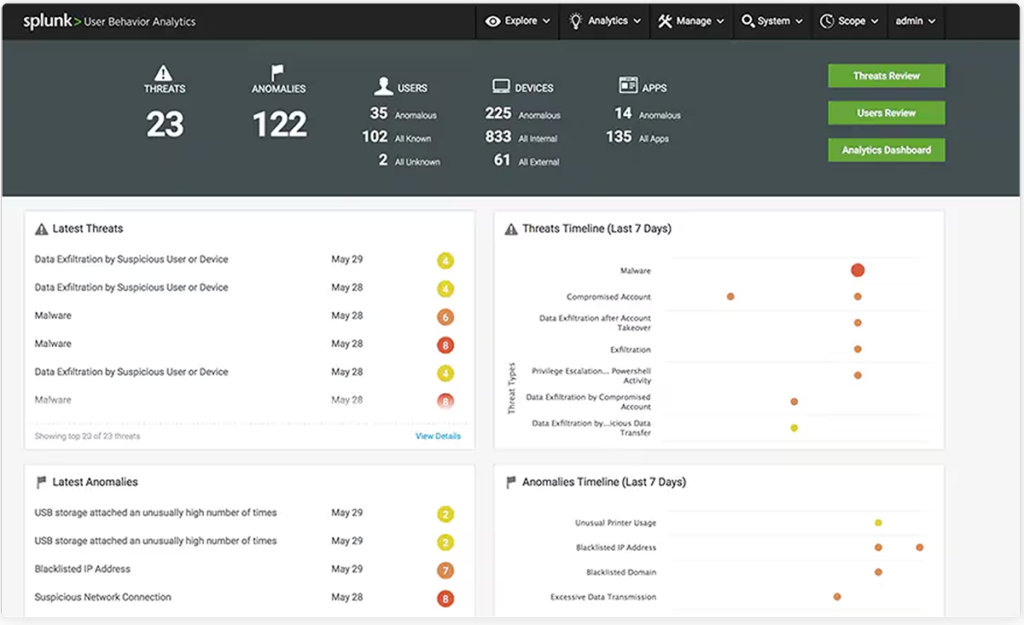
One of Splunk’s main features is its ability to correlate data from different sources, providing a holistic view of user behavior. This can help security teams pinpoint the root cause of a security incident, enabling them to respond more efficiently. The tool offers several deployment options, including on-premises, in the cloud, and hybrid.
4. IBM Security QRadar
IBM Security QRadar is a security intelligence platform that uses behavioral analytics to detect anomalies and threats. It provides real-time visibility into network activity and user behavior, allowing security teams to identify and respond to threats quickly and effectively.
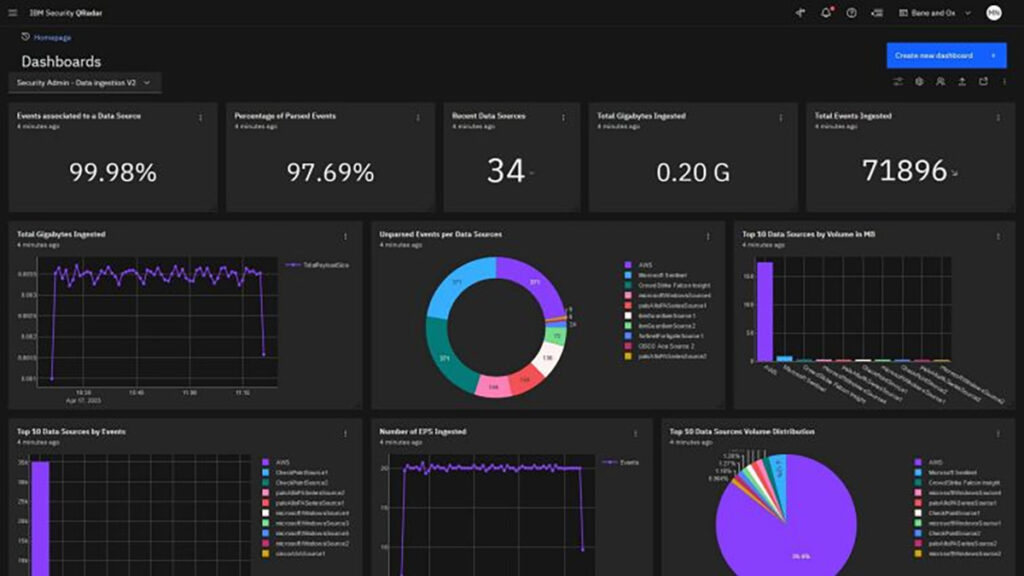
QRadar’s advanced analytics capabilities enable it to detect even the subtle signs of a security breach. Its threat intelligence feature leverages data from various sources to enrich its analytics, providing in-depth insight into threats.
In addition, IBM Security QRadar offers a centralized dashboard that gives security teams a consolidated view of their security posture. It also integrates with other security tools.
5. LogRhythm UEBA
LogRhythm UEBA uses machine learning and behavioral analytics to detect and respond to threats. It offers advanced threat detection capabilities and provides security teams with actionable insights to help mitigate risks.
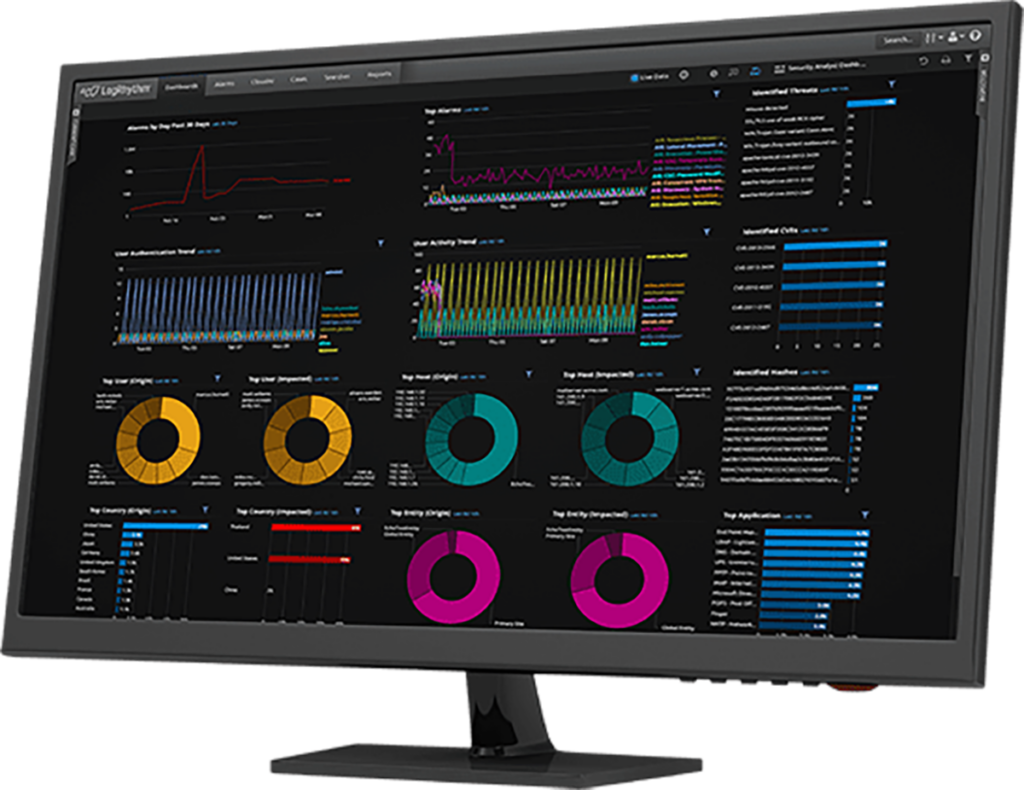
One of LogRhythm’s key features is its advanced threat lifecycle management functionality. This feature streamlines the process of detecting, investigating, and responding to threats, making it easier for security teams to manage incidents. LogRhythm UEBA also integrates with other security tools, enabling automated threat response.
6. Microsoft Sentinel
Microsoft Sentinel is a cloud-based SIEM and SOAR solution that uses advanced analytics and artificial intelligence to detect and respond to threats. It provides real-time threat visibility and prioritizes alerts based on risk, ensuring that security teams focus on the most critical threats. A unique aspect of Sentinel is that it uses data from Microsoft’s Security Graph, which collects threat data from billions of endpoints worldwide.
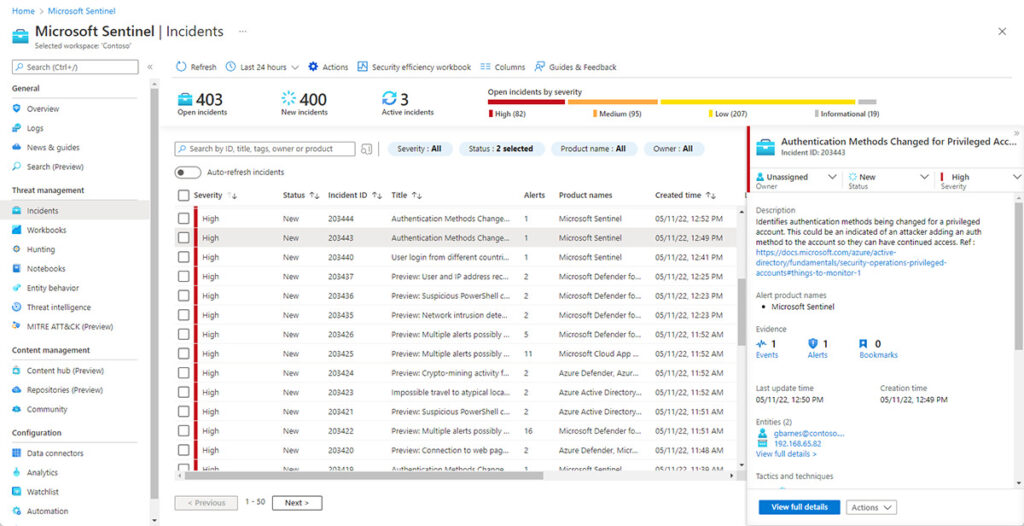
Microsoft Sentinel offers a centralized dashboard where security teams can monitor and manage threats. It also integrates with other Microsoft security solutions, enabling a coordinated response to threats.
7. Securonix
Securonix is a UEBA tool that offers detailed insights into user and entity behavior, helping you detect and respond to threats more efficiently. It has a strong focus on threat detection, using behavioral profiling and anomaly detection to identify potentially elusive threats. It can also correlate events across multiple data sources, providing a comprehensive view of your security landscape.
Securonix offers a risk scoring system that helps prioritize threats based on severity, allowing you to focus on the most critical issues first. Lastly, it provides a set of customizable dashboards that make it easy to monitor and manage the security environment.
The Exabeam Security Operations Platform: The Leader in UEBA
Cloud-scale Security Log Management and SIEM: Securely ingest, parse, and store security data with lightning-fast search, compliance reporting, and dashboards. Combines powerful correlation and threat intelligence with case management. (199/250)
Powerful Behavioral Analytics: Machine learning-based behavioral models increase detection fidelity and automated AI-driven timelines prioritize anomalies based on risk. (138/250)
Automated Threat Detection, Investigation, and Response (TDIR): An automated TDIR workflow uses ML and AI to identify threats, accelerate investigations, and reduce response times with consistent, repeatable results.
Related content: Learn more about Exabeam Behavioral Analytics






