Ask the Experts Series
“Malware is becoming more vicious. And it’s harder to combat. We now face everything from network-based ransomware worms to devastating wiper malware. At the same time, adversaries are getting more adept at creating malware that can evade traditional sandboxing.”
What this quote doesn’t mention is that many of the most devastating data breaches are caused by attackers using stolen credentials to gain access to organizations’ network assets.
Compromised insider using a credential-based threat
A compromised insider can be an employee, contractor, or other trusted user who has either intentionally or unintentionally exposed your network to bad actors. The following security incidents that we will review use valid, active user names and passwords that are in the hands of an attacker.
Many organizations think, “We have up-to-date, active antivirus (AV) software running on all of our systems, and have alerts configured to notify us when something serious happens.” But AV software provides only so much protection—successful malware detection and remediation doesn’t ensure a system isn’t compromised.
The limitation of AV software—and that of other solutions that target specific points in the attack chain—is that it doesn’t differentiate normal user and system behaviors of your users and systems from the abnormal activity. Numerous false positives pile up along with the mountain of data collected by your log management or SIEM system, adding to the background noise.
A valid attack can often go unnoticed, hidden in the background noise that is being generated by events that are actually within the parameters of normal behavior for your users.
The Attack Chain
The security breach lifecycle has been thoroughly studied; Figure 1 shows the phases of an advanced persistent attack (APT).
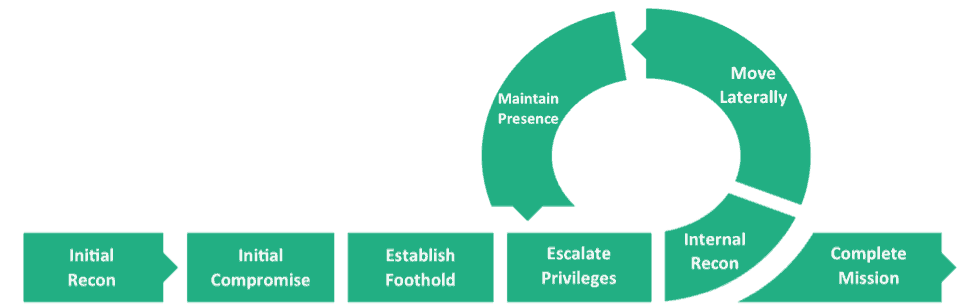
Figure 1- Mandiant’s representation of an APT Attack Chain
Most security operations centers (SOC) attempt to stop attackers at each phase. And many organizations spend the bulk of their security budget attempting to detect the initial compromise at the host or network level. They also might implement a data lost prevention (DLP) solution to try to catch data leaving the organization after an attack is underway.
There are a number of problems with this approach. When stolen credentials are used, there are multiple ways for an attacker to successfully execute each phase while impersonating a trusted user. If one method fails, they simply try another until they succeed in moving to the next phase. Conventional security solutions are typically oblivious that someone other than a trusted user has penetrated the network—until it’s too late.
Understanding the attackers’ goals
Missing from most legacy SIEM solutions is an understanding of the difference between goals of a trusted user and those of an attacker. They’re not the same, yet the same systems and actions are used to accomplish their respective tasks.
Knowledge of the “white space”
Figure 2 shows attack chain points where stolen credential use allows an attacker to move closer toward their goal. Behavioral analytics enables you to easily compare normal versus abnormal activities, so you are equipped to examine what’s happening in these “white spaces.”
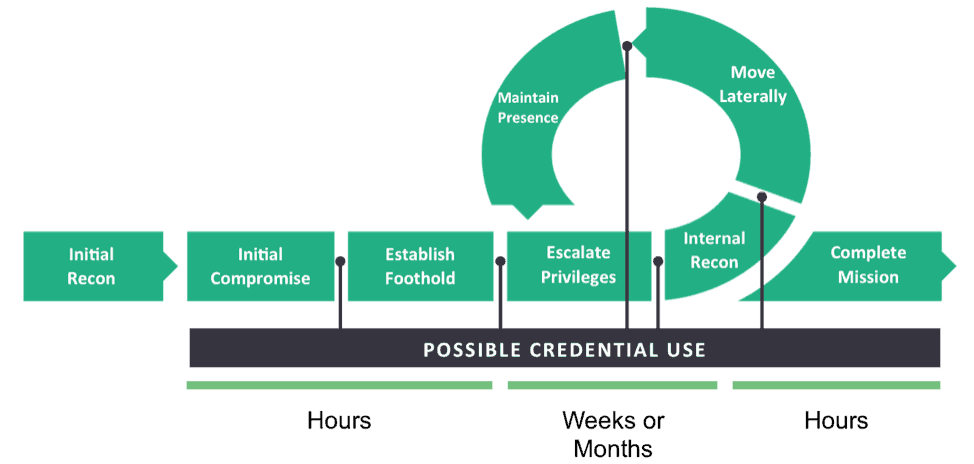
Figure 2 – Attack chain points where stolen credentials can be used.
During a typical attack, the hacker spends the most time—sometimes weeks or months—in the middle of the chain. Unfortunately, this is the least visible section with most security point and inline DLP products. But in deploying user and entity behavior analytics (UEBA), you can focus on this critical area. Based on deviation from normal behavior, each event is automatically scored as it occurs and raises an alert if the score reaches a predetermined tipping point.
Focus on unusual events
You can also gain insight into unusual events by examining those that occur the least often. For example, common malware attacks that can be detected and cleaned by your AV software probably include thousands of adware, malvertising, potentially unwanted programs, and other low-impact events. But in examining more unusual events, such as unique signatures and malware your organization has never seen before, you can discover the more serious threats more quickly, giving you more time for mitigation.
Using a behavioral approach
Throwing resources at individual malware attack chain phases is a losing battle in the ever-escalating cyber war. Instead, focus your security investment on understanding the normal user behaviors within your organization, so that you can more easily and rapidly spot the abnormal behaviors of threat actors. Without comprehensive log data and UEBA, manual cybersecurity tactics are unable to correlate the critical information needed to identify a credential-based attack that can cripple your organization.
More information
- For a more detailed look at the scenario presented in this blog and another comprehensive malware investigation, see: Exabeam Practitioner Training: Malware Investigations.
- See Introducing Behavioral Analysis for Devices – Exabeam Entity Analytics for more information about analyzing the behavior of assets versus users.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!











