This week we announced Exabeam Entity Analytics, a product that analyzes the behavior of machines and devices instead of users. Why would you need this? Well, to start with, IoT.
According to Gartner, over 8 billion IoT devices were in use in 2017. Eight billion! Many of these devices are vulnerable due to default credentials, un-updated or proprietary software, or lack of management (or all three). Recent stories of CCTV cameras used to mount denial of service attacks, compromised HVAC systems used to gain entry into corporate networks, medical devices hacked to disrupt medical care, and even drones used to compromise IoT light bulbs, illustrate the scope of the problem.
Unlike a PC or a mobile phone, these devices don’t necessarily have a user in the conventional sense. Sure, they may have an admin or service account, but for a lot of IoT devices, it’s set it and forget it. Users aren’t using the devices, so there is no user behavior to analyze.
Which leaves you with device behavior. Entity Analytics works by first setting a baseline, which represents normal behavior. From normal, the product analyzes activity in device logs to look for suspicious behavior, including:
- trying to access proprietary servers or networks
- uploading or downloading larger than usual volumes of information
- sending packets to unusual locations or in unusual patterns
Security administrators are presented with a prioritized list of risky devices for investigation, with the potential to automatically remediate the problem by isolating it on the network or potentially reconfiguring. These prioritized lists are called watchlists and are shown in the screenshot below. Watch lists help analysts quickly identify any notable assets which may be exhibiting a high degree of anomalous, risky activity. Higher amounts of abnormality result in higher risk scores.
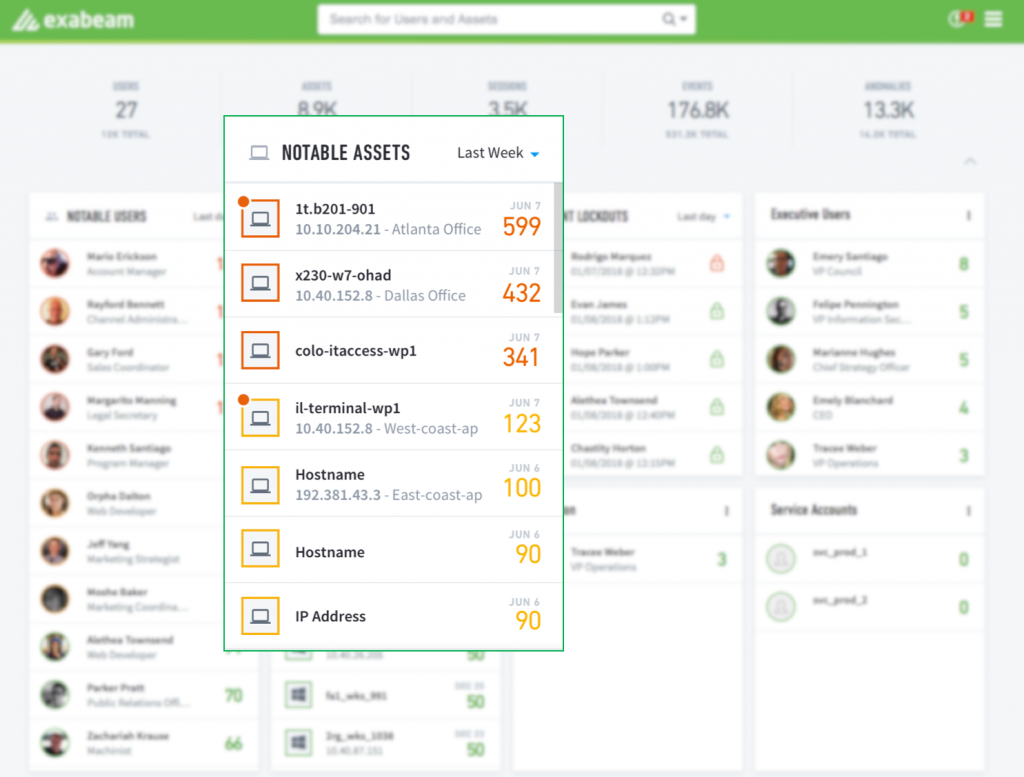
Figure 1 – Notable assets in a watch list sorted by risk score.
The analysis of the devices is done using logs from multiple sources, including firewalls, DNS servers, netflow, EDR, and other monitoring tools. Another aspect of what makes the Exabeam platform so powerful is our ability to map device names to IP addresses at a given time. This can be very difficult to do, given the ephemeral nature of DHCP.
If an investigation is required, then an analyst can click to see the device’s full activity in a timeline, shown below in Figure 2. In this case the device “Rogue_One” has experienced several security alerts for visiting malicious and suspicious domains, has a number of failed logins from users, and has outbound network connections on abnormal ports. All of which may add points of risk to this device’s risk score.
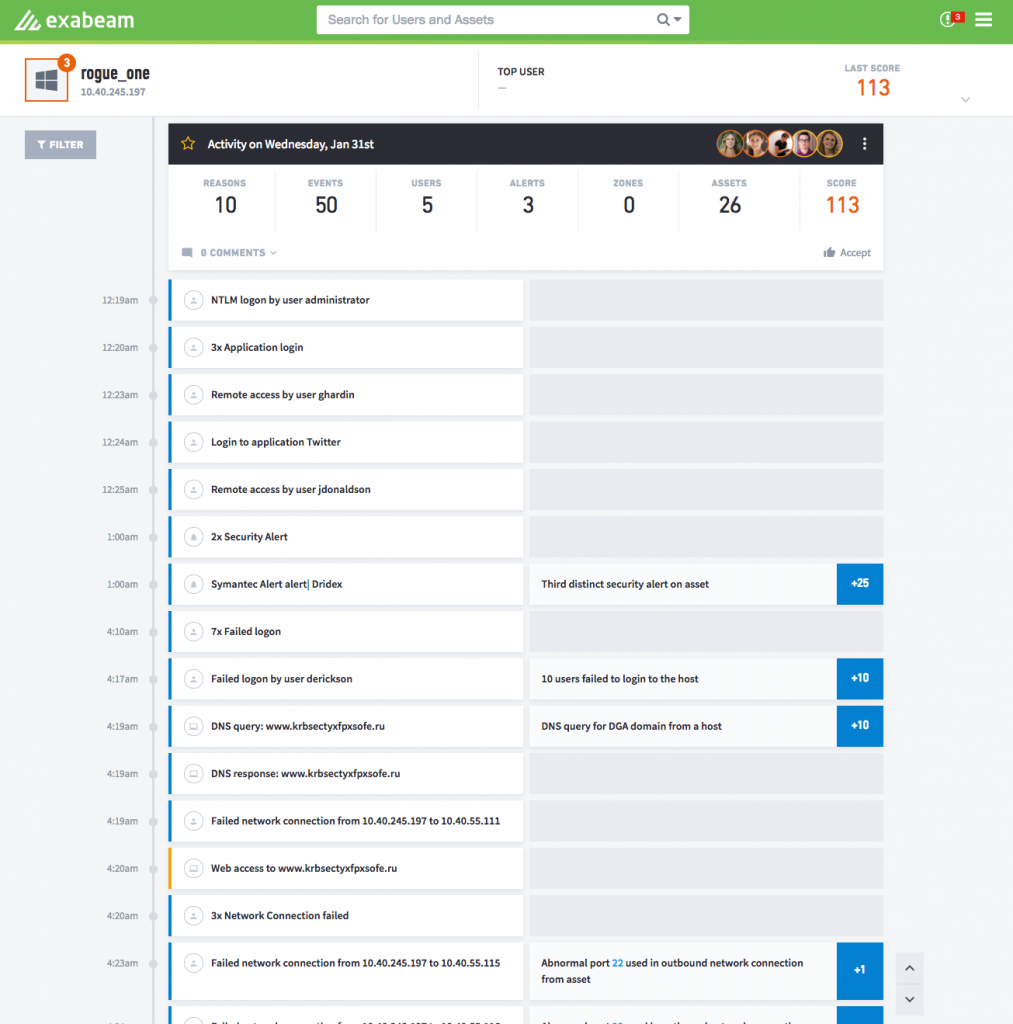
Figure 2 – A prebuilt incident timeline showing a notable device showing anomalous activity.
Entity Analytics can also help in the case where there are users accessing machines. When a server is being accessed inappropriately, it is either a malicious insider or a user whose credentials have been compromised. Allowing a security analyst to seamlessly move back and forth from the device timeline to the user timeline – we call this pivoting – helps the security analyst understand what happened before the device was accessed. In the example below, we see a user Gary Hardin who has been accessing the compromised device Rogue_one. Analysts can easily pivot through the system as needed to “pull the thread” on the investigation by simply clicking on the item they want to investigate further.
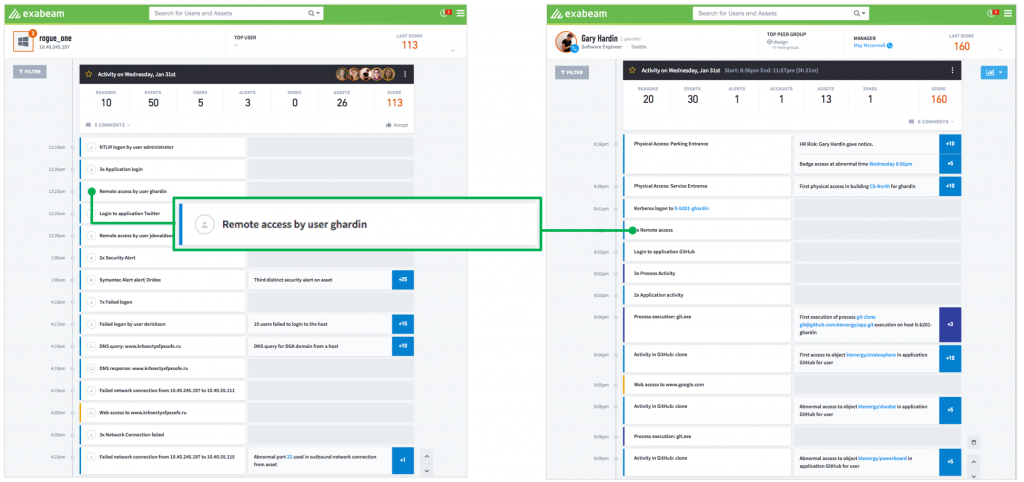
Figure 3 – An example of how a device timeline is connected to the related user timeline.
The use cases for Entity Analytics are almost endless. So far we’ve had customers look at it for everything from routers to medical devices to things like roadside signs (which are networked computers, after all).
Curious to see how it could work for you? Get more details here.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!