Adding monitoring, analytics, and automation to achieve “optimal Zero Trust” under the CISA – NIST maturity model.
There’s a lot of confusion in the market about what exactly is zero trust. Zero trust products, zero trust postures, zero trust strategies, zero trust models, and finally, zero trust architectures (ZTA). Last year, the White House’s Executive Order (EO) 14028, “Improving the Nation’s Cybersecurity”, recognized the need to adopt zero trust models across federal agencies. Quoting from the source, “The Federal Government must bring to bear the full scope of its authorities and resources to protect and secure its computer systems, whether they are cloud-based, on-premises, or hybrid….It is the policy of my Administration that the prevention, detection, assessment, and remediation of cyber incidents is a top priority and essential to national and economic security. ”
A good number of security products and solutions broadly label themselves as “zero trust”. Buzzword bingo? Maybe so. We see zero trust as a concept, and an architectural framework that spans product boundaries. No one product in the market ensures you “zero trust coverage”, rather, it’s a collection of products, processes, and a mindset that combine to enable a Zero Trust Architecture. The security vendor marketplace is likely making this more confusing than it needs to be.
Zero trust capabilities versus products
For end users, sourcing the capabilities of zero trust might be more valuable than looking for a single product unicorn. Some zero trust capabilities include: providing a health check for endpoints connecting to services combined with single sign-on tools; the ability to add policies and additional controls for authentication and privilege model review; brokering access between clients and servers as third-party secure environments; not to mention policy- and threat-based step-up authentication, multifactor authentication (MFA), and identity management. I suppose that vendors of these approaches are happy to help organizations check the ZTA box from last year’s Executive Order. But are those capabilities by themselves enough?
The Executive Order doesn’t think so. It instructs departments to “develop a plan to implement Zero Trust Architecture, which shall incorporate, as appropriate, the migration steps of the National Institute of Standards and Technology (NIST).” It is important — and NIST validates this — when architecting a solution that works for your organization’s ZTA workflows, to also add end-to-end log monitoring, advanced analytics, and response automation as additional capabilities to support detecting anomalies and incidents. These three capabilities are common characteristics of any Next-gen SIEM (Security Information and Event Management) product.
As a secondary concern, attacks have escalated on the frontline security tools, platforms, and software supply chains used to protect organizational secrets and data. A compromise could come at any point within the ecosystem, and it’s clear that “watching the watchers” in security terms is important. This is where the Threat Detection, Investigation, and Response (TDIR) capabilities of a SIEM focus, and why any security operations team needs to consider having visibility of their identity management, security log management, and other threat detection tools across their on-premises and cloud attack surfaces.
The pillars of zero trust
Zero trust (ZT) is the term for an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources. Zero Trust Architecture is a way of constructing how users and entities (e.g., devices, servers, network devices, etc.,) are connected to organizational and agency resources — anywhere. “Never trust, always verify” means that even an authenticated user logged into a network is still verified when touching a new system, and is operating under the least privilege in terms of authorization, keeping it appropriate to the role and function of the individual.
NIST defines the pillars of zero trust in figure 1 below, combining identity security, device health, network/environment services, application workloads, and data as the key areas in need of protection through a combination of constructing architecture, processes, and tools.
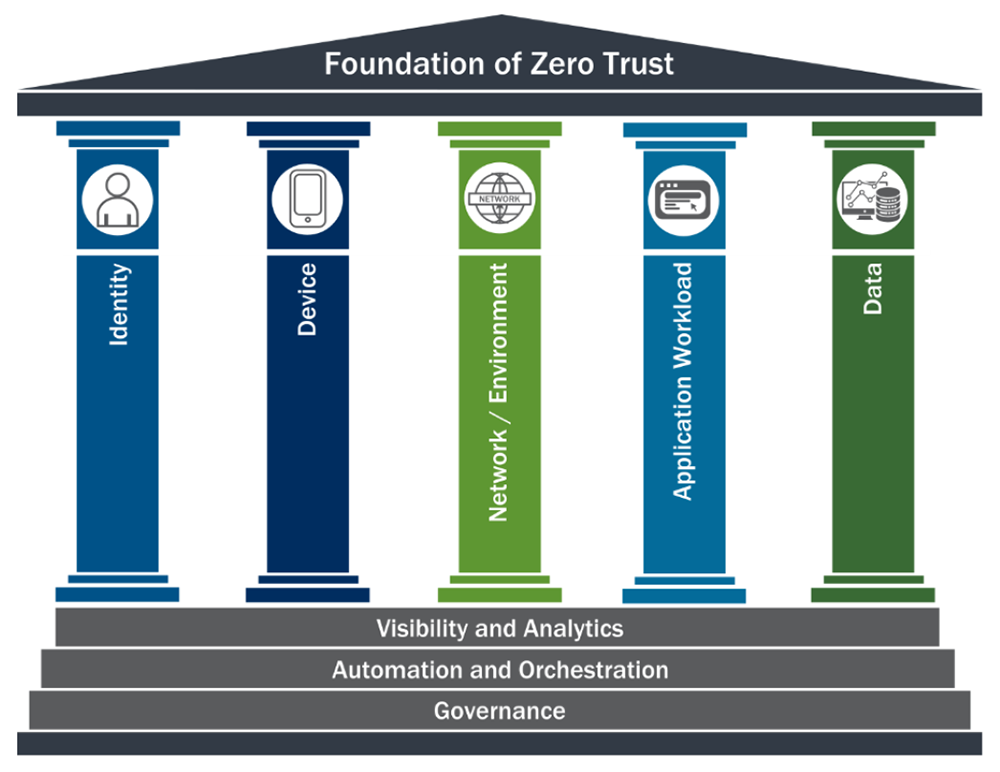
At the core of this conceptual illustration is incorporating visibility and analytics to the foundation, along with automation and orchestration — core capabilities of a Next-gen SIEM platform. Adding governance to the foundation provides an underlying principle for reporting on ZTA. Organizations need to do more than build a Zero Trust Architecture — they need to demonstrate that zero trust is being enforced automatically, is operating effectively, and is monitored for anomalies and outliers that could represent a breach of trust.
The key concepts of Zero Trust Architecture include:
1. No implicit trust — All resources must be accessed securely, and resource access is confirmed by rules, policies, and role trust rather than network location
2. Authentication and authorization must be confirmed for every credential and device with each session and every connection — especially to guard against lateral movement, permission escalations, and unauthorized new account creation.
3. Verify what every credential and entity accessing resources is doing during the session — This means if an authenticated credential starts acting unusually, the anomaly is recognized and identified automatically.
4. Inspect all ongoing log traffic for malicious activity, including locally and to cloud resources, analyzing for attacks and anomalies — Recently, we witnessed an attack against Apache logging processes and resources (Log4J), proving that even this part of the zero trust operation requires scrutiny.
5. Automate and orchestrate responses — It’s often a challenge to find sufficient skilled security analysts, so every step that can be automated in responses and coordinated across the security stack helps speed responses, controls potential breaches, and ensures repeatability.
A viable zero trust strategy includes answering questions like, “Who is monitoring the effectiveness of those policies in real time?” and, “How do you know when something unusual is happening when the basic authentication and authorization steps are complete?” That’s where a SIEM, such as Exabeam, comes in.
User behavior is central to zero trust
A security stack averages between 17 and 50 tools, services, machines, and processes. Some are dedicated to monitoring or enforcing security on each Zero Trust Architecture diagram pillar, from endpoints and network VPNs or proxies to identity protection, authentication, or cloud protections. But the truth is that few of the tools both understand normal user behavior relative to a baseline and can use that to pinpoint new or unusual anomalous behavior.
The more mature an organization’s security policies, processes, and tools are, the more prepared they are to deal with malicious actors. Security teams must be prepared to answer these types of questions:
- What is connected? What entities, credentials, applications, and (native or cloud) services are used by the organization or agency?
- Can security analysts observe the changing security posture of these entities and credentials as vulnerabilities and threats are discovered?
- Who is using the network? What users are part of the organization or are external and allowed to access enterprise resources? This includes every identity from service accounts to privileged users and BYOD.
- What is happening right now? Security teams need insight into traffic patterns and messages, with a clear vision of normal behavior for each to compare against new traffic, anomalous activity, and lateral movement.
- How is data protected? Outside of simple encryption solutions, organizations need fast visibility to strange data movement, file size changes, and more to quickly identify risk.
- What automated responses are available, and are security teams clear on how to take the next investigation steps if anomalous behavior is discovered?
- Has anomalous lateral movement occurred? Can you answer when, where, or what?
- If an executive or manager asks on the fly, can security analysts identify every entity (credentials and devices/resources) which may be involved?
- If a credential suddenly emerges or changes behavior and accesses new sources or sends out larger-than-normal files to new destinations, did you see it and stop it? Can you enforce data protection policies and cloud access — or were they bypassed?
Engaging the optimal Zero Trust Architecture
Moving from traditional patchwork or tool-centric approaches to optimal security response requires end-to-end visibility from a single point of reference. Rather than needing to manage logins for multiple tools and multiple UIs, a security analyst should have a single place to collect data, monitor risk for users and assets, and employ automated responses and playbooks for multiple attack types, from malware to malicious insiders — even compromised credentials.
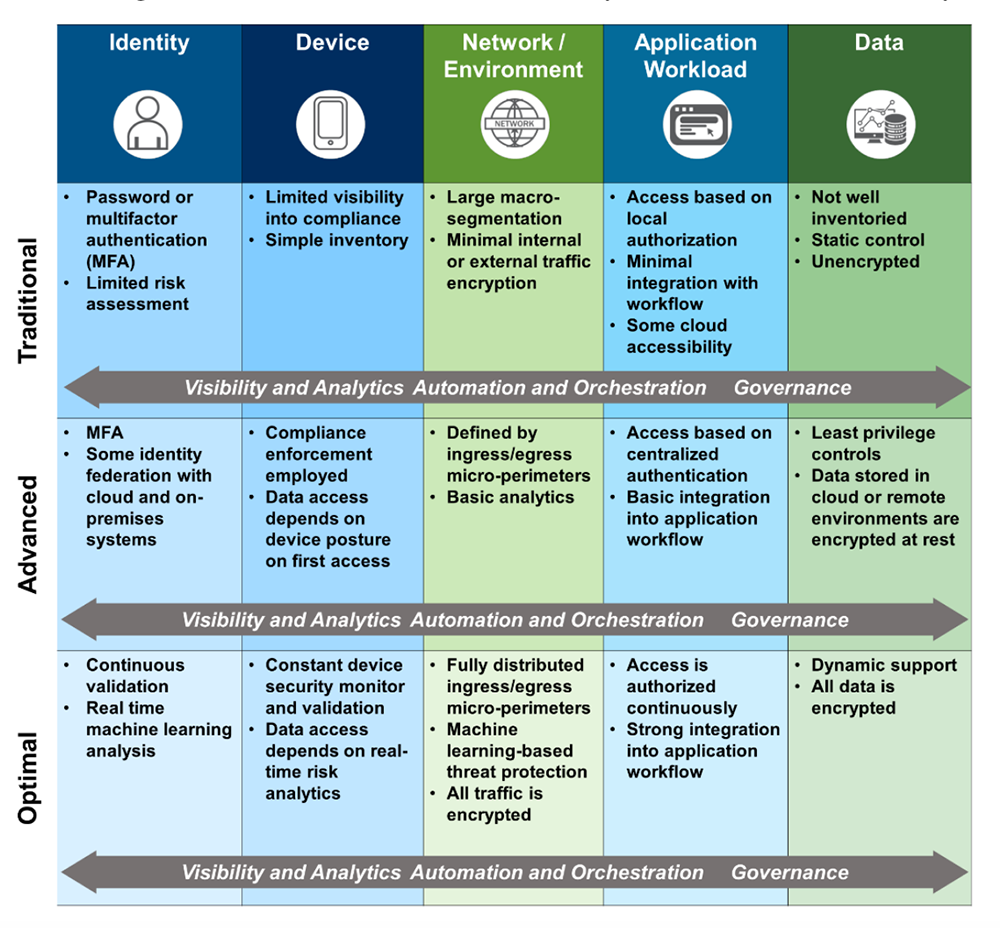
All it takes is one employee’s, contractor’s, or partner’s credentials to be compromised, and lateral movement may go unseen unless advanced* or optimal* zero trust is established.
* CISA/NIST
A foundation for ZTA, security operations, and beyond
While not a zero trust solution in name, the capabilities of Exabeam Fusion SIEM are a force multiplier for any zero trust investment. Exabeam makes it easy to ingest security events from every component within your Zero Trust Architecture. We store the data in a cost-effective way, run advanced analytics on it, and provide tools to search and report on this data in real time or for historic purposes. (Need a view of what happened a year ago?) The Exabeam Security Operations platform helps you make more sense of security event data by using machine learning to baseline and identify abnormal behaviors. Every activity is assigned a risk score and fed into a timeline of events your analysts can use to investigate and respond.
Alerts are created for activities that cross a certain risk threshold. This presents security analysts with a framework for triage and investigation that allows even junior (Level 1) analysts to perform investigation tasks of Level 3 analysts, and sets in motion automated response workflows that streamline an otherwise cumbersome and time-consuming process: investigations.
Key benefits of the Exabeam Fusion Security Operations Platform
- Cloud-delivered, providing the scale and efficiency of the cloud
- Available as a SIEM replacement or as an analytics upgrade to an existing SIEM
- Behavioral analytics and automation to quickly detect and respond to threats other tools miss
- Advanced alert triage capabilities — 83% of analysts report the ability to triage twice as many alerts as a legacy SIEM
- Advanced SOC functionality with threat-centric, use-case packages to deliver specific outcomes
Learn more about Exabeam and Behavioral Analytics
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












