In this article, we introduce the basics of incident response and discuss Security Orchestration, Automation and Response (SOAR) — a tool which makes incident response more efficient, more effective and more manageable at scale.
In this article:
- What is incident response?
- What is case management?
- What is SOAR?
- Three key SOAR capabilities
- Dashboards and reporting
- How does SOAR fit with SIEM?
What is incident response?
Reactive incident response
Incident response is an organizational process that allows security teams to contain security incidents or cyber attacks, prevent or control damages. Incident response also allows teams to handle the aftermath of the attack—recovery, remediating security holes exposed by the attack, forensics, communication and auditing. This is known as reactive incident response.
Threat hunting
Threat hunting is the core activity of proactive incident response, which is carried out by skilled security analysts. It typically involves querying security data using a Security Information and Event System (SIEM), and running vulnerability scans or penetration tests against organizational systems. The objective is to discover suspicious activity or anomalies that represent a security incident.
Proactive incident response
Many security incidents are only discovered weeks or months after they took place—while some are never discovered. Many organizations are developing proactive incident response capabilities. This involves actively searching corporate systems for signs of a cyber attack.
What is case management?
Case management involves collecting, distributing and analyzing data tied to specific security incidents, to allow teams to effectively respond.
Case management solutions help security staff:
- Open a case for a confirmed security incident
- Quickly aggregate all relevant data into a digital representation of the case
- Enable fast prioritization of cases for response
- Investigate and add information to the case
- Record activity in the aftermath of an attack and close the case
What is SOAR?
Security Orchestration, Automation and Response (SOAR) is a category of security tools that:
- Collect security threat data and alerts from different sources
- Enable incident analysis, triage and prioritization, both automatically and manually with machine assistance
- Define and enforce a standard workflow for incident response activities
- Encode incident analysis and response procedures in a digital workflow format, enabling automation of some or all incident responses
Three key SOAR capabilities
SOAR tools provide the following four capabilities that help Security Operation Centers (SOC) respond to incidents more effectively.
Orchestration
Orchestration is the ability to coordinate decision making, and automate responsive actions based on an assessment of risks and the state of the environment.
SOAR tools can do this by integrating with other security solutions in a way that lets them “pull” data and “push” proactive actions. SOAR provides a generic interface, allowing analysts to define actions on security tools and IT systems without being experts in those systems or their APIs.
AN EXAMPLE OF ORCHESTRATION:
PROCESSING A SUSPICIOUS EMAIL
- A SOAR tool can investigate whether the sender has a malicious reputation, via threat intelligence, and use DNS tools to confirm the origin.
- The tool can automatically extract hyperlinks and validate them via URL reputation, detonate the links in a secure environment, or run attachments in a sandbox.
- Then, if an incident is confirmed, a playbook is run. The playbook looks in the email system to find all messages from the same sender or with the same links or attachments and quarantines them.
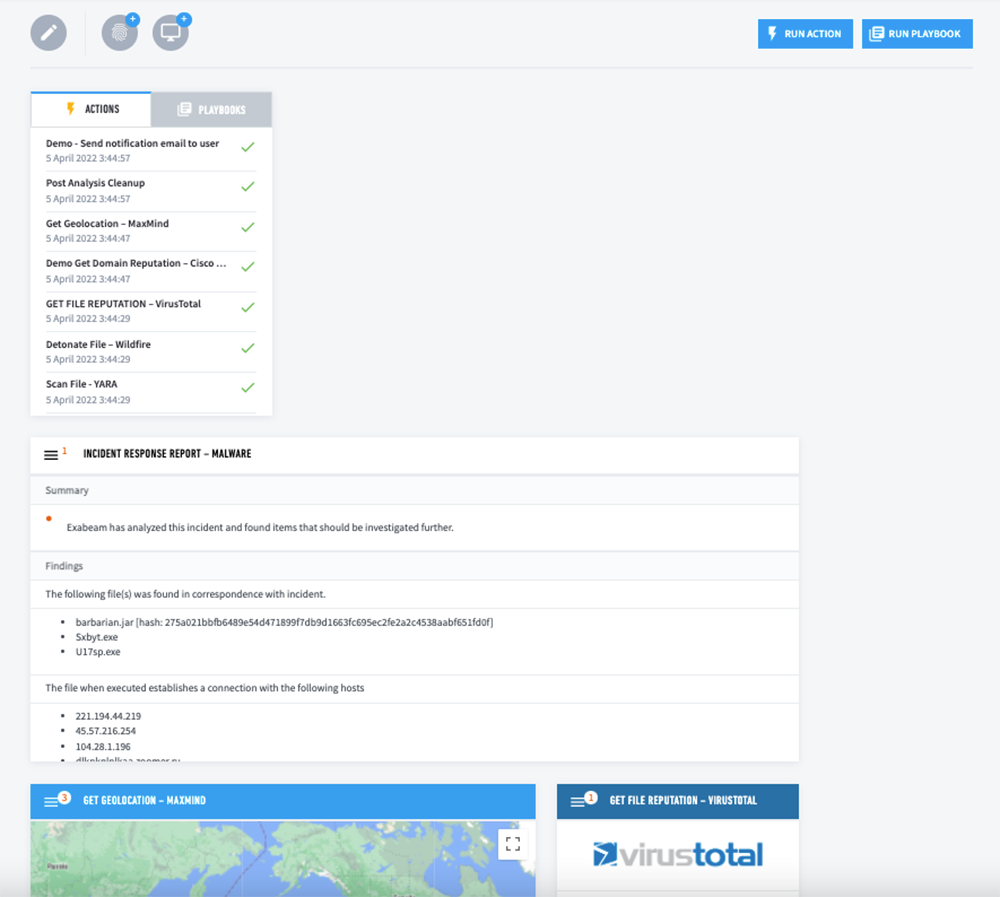
Automation
Automation is related to orchestration—it is machine-driven execution of actions on security tools and IT systems, as part of a response to an incident. SOAR tools allow security teams to define standardized automation steps and a decision-making workflow, with enforcement, status tracking and auditing capabilities.
Automation relies on security playbooks, which analysts can code using a visual UI or a programming language like Python.
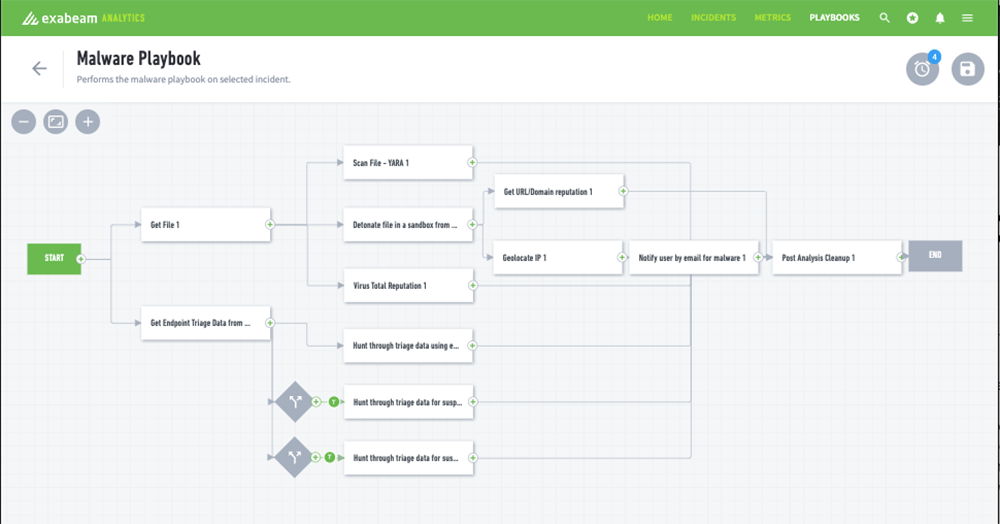
AN EXAMPLE OF AN AUTOMATION PLAYBOOK:
EXABEAM’S MALWARE PLAYBOOK
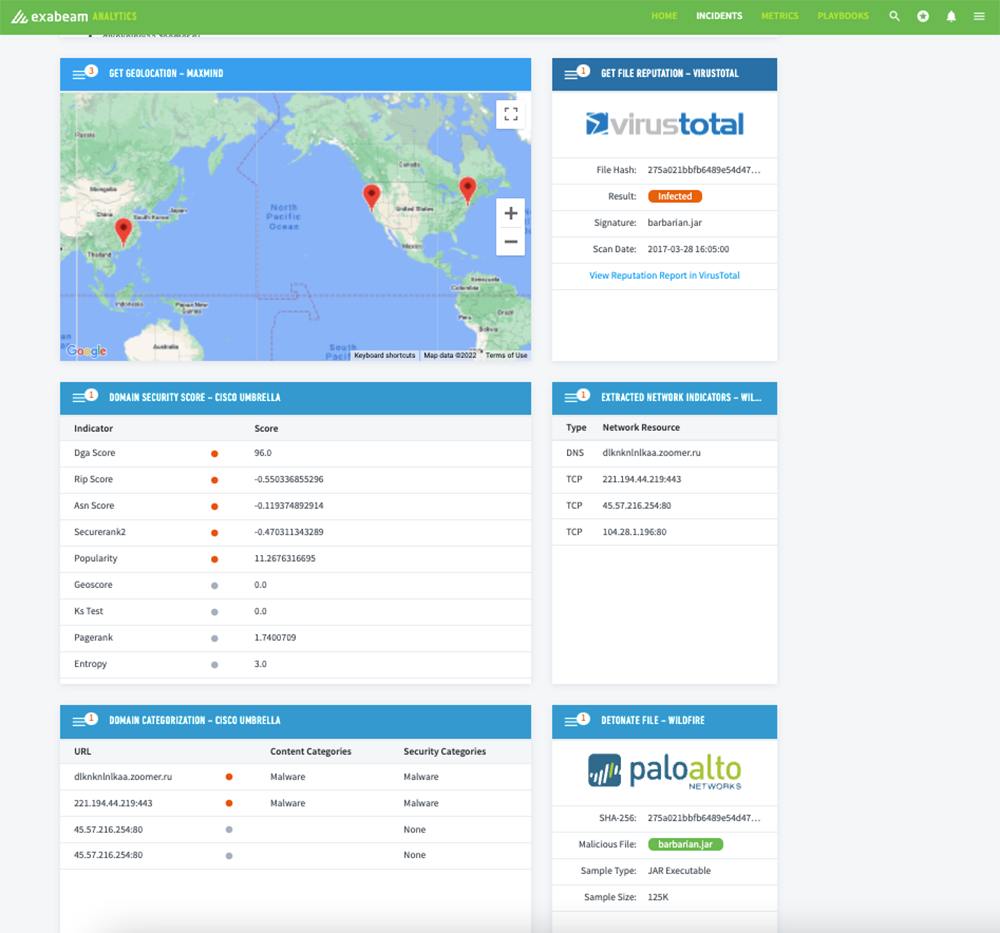
- The SOAR tool scans the malware file and detonates the file in a sandbox using external services.
- The SOAR tool checks the file against reputation services such as VirusTotal for accuracy.
- The SOAR tool identifies the geolocation of the source or originating IP address.
- The system notifies the user about the malware and a post-analysis cleanup is performed.
Incident Management and Collaboration
This SOAR capability helps security teams manage security incidents, collaborate and share data to resolve the incident efficiently.
- Alert Processing and Triage – A SOAR tool gathers and analyzes security data, typically taken from the SIEM, correlates data to identify priority and criticality, and automatically generates incidents for investigation. The incident already includes relevant context information, allowing analysts to investigate further. This removes the need for a human to notice the relevant security data, identify it as a security incident and manually set up an incident in the system.
- Journaling and Evidentiary Support – A SOAR tool provides an investigation timeline to collect and store artifacts of the security incident, for current and future analysis. Artifacts may relate to known attacker’s activities, which may be carried out over an extended period. Additional artifacts can be pulled in to investigate if they are related to the ongoing incident.
- Case Management – The tool can record actions and decisions made by the security team, making them visible to the entire organization and external auditors. Over time, the SOAR tool creates an organizational knowledge base of tribal knowledge—threats, incidents, historical responses and decisions and their outcomes.
- Management of Threat Intelligence – A SOAR tool brings in threat data from open-source databases, industry leaders, coordinated response organizations, and commercial threat intelligence providers. The SOAR tool attaches the relevant threat information to specific incidents, and makes threat intelligence easily accessible to analysts as they are investigating an incident.
Dashboards and reporting
SOAR tools are not only responsible for coordinating and automating incident response, but also for enabling central measurement of SOC activity.
SOAR tools generate reports and dashboards including:
- Analyst-level reports – activity by each analyst, such as number and types of incidents, mean time to detect and respond per analyst, and so on.
- SOC manager reports – reporting on the number of analysts, incidents handled per analyst, and mean time for specific stages of the incident response process, to identify bottlenecks.
- CISO-level reports – alignment of risks with IT metrics to see the impact of incidents on business performance and regulations; measuring efficiently by looking at MTTD and MTTR across the entire organization, and reduction of labor through automation.
How does SOAR fit with SIEM?
SOAR tools work closely with SIEM, the SOC’s central information system. SOAR tools leverage the integration with SIEM to:
- Receive alerts and additional security data to identify security incidents
- Draw in data required for analysts to further investigate an incident
- Assist analysts in proactive incident response and threat hunting, which relies on querying and exploring cross-organization data
SOAR as part of Next-gen SIEM solutions
next-generation SIEM solutions include a native component that enables handling and responding to detected incidents via automated and manual case management, workflow and orchestration, and capabilities for advanced threat defense. SOAR should be an integrated part of the SIEM.
The Exbeam SOC Platform is an example of a SIEM solution based on modern data lake technology, which enables advanced analytics and User Entity Behavior Analytics. In addition, Exabeam comes with two components that provide full SOAR functionality:
- Exabeam Incident Responder and Exabeam Case Management – provides security case management, integration with third-party tools, centralized security orchestration, and automated incident response via security response playbooks.
- Exabeam Threat Hunter – a point-and-click interface that lets SOC analysts quickly perform searches to identify patterns in vast amounts of historic security data. The search results provide incident timelines outlining normal and anomalous activity that happened around the threat.
Learn more about Automating Incident Response
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













