FASTER DETECTION OF THREATS AND AUTOMATED PLAYBOOKS TO REDUCE INCIDENT RESPONSE OVERLOAD
Despite all of the investment and interest focused on cybersecurity, security operations center (SOC) analysts and incident responders haven’t realized much improvement in their effectiveness or job satisfaction. SOCs are often understaffed, spread across multiple time zones, and lacking the needed skills.
Frustrations in SOC methodology are compounded by today’s security landscape. Research from CyberEdge Group’s 2018 Cyberthreat Defense Report shows that “optimism for dodging a successful cyberattack in the coming year has fallen from 62% in 2014 to 38% this year.”
All in all, the incident response (IR) of security teams continues to require a brute force approach to 1) find a threat, 2) understand why it happened and what has been affected, then 3) fix it, so that it doesn’t happen again. A typical IR process involves several manual tasks performed by overburdened security teams who spend an inordinate amount of time on repetitive mundane tasks.
Under such conditions, achieving timely and repeatable incident response results are unlikely.
Pain points using the traditional, manual IR processes
Typical SOC analysts deal with many pain points in their daily workflow. Many are due to manual processes that continue to be the norm:
- Alert fatigue – Tier 1 analysts spend much of each day sifting through a deluge of raw alerts, trying to find legitimate threats among an overwhelming number of false positives.
- Redundant, mind-numbing processes – Examining raw log files and aligning facts from disparate, non-integrated systems requires extraordinary attention to detail.
- Cross-system “chair swiveling” – An IR case typically requires consulting between 5 – 15 sources, including endpoint detection and response (EDT), firewall, malware, other threat intelligence feeds, human resource systems, and more—often with no integration.
- Communication delays – Despite best efforts to close incidents as quickly as possible, analysts often endure long delays while waiting for responses from other employees and security stakeholders. This can prolong an organization’s risk exposure.
- Lack of skilled personnel – Most SOCs are overburdened and understaffed to such an extent that they’re simply unable to investigate every alert in their queue. Couple that with there not being enough skilled security analysts to meet today’s needs. As reported in CSO, a 2018 ESG survey of 620 North American and European IT and cybersecurity professionals cites that “51 percent of respondents claimed their organization had a problematic shortage of cybersecurity skills.” And according to CyberEdge Group’s 2018 Cyberthreat Defense Report, “IT security’s greatest inhibitor is their lack of skilled security personnel.”
Manual Incident Response Steps
A typical IR response might include the following steps and timelines:
- Detection and triage (1 – 3 hours) – Analysts waste time weeding out false positives from real threat events.
- Data gathering and further investigation (1 – 2 days) – Next comes long sessions of chair swiveling between systems, copying and pasting data to a common file, and resolving IP addresses, machine names, domain controllers, and other bits of information so as to determine actors, locations, and asset ownership.
- Data validation and normalization (1 – 3 days) – Now analysts have to verify the accuracy of events—for example, whether foreign VPN access is due to an employee actually being in that country at the time of the event. Analysts typically run multiple queries over various data sources, attempting to consolidate the results from multiple sources and manually stitching together information to create a timeline to find the anomalous events.
- Completion (1 – 2 days) – All previous data is organized into a coherent, actionable report.
- Response (a few minutes to many weeks) – Finally the threat can be mitigated. This might be as simple as resetting a password, or as complex as isolating a group of infected computers, reimaging them, then ensuring appropriate employee training occurs to help prevent future occurrences. And if the incident resulted in a data breach, the incident response probably needs to also include your executive, legal, and marketing departments.
Automation and orchestration can reduce IR team overload
The right mix of IR automation and IT orchestration can drastically cut the time analysts spend on manual steps—often from many days to mere minutes. While far from being a silver bullet, automation and orchestration are proven approaches to improving the security, efficiency, cost, and morale of security teams and organizations that depend on them.
- Automation – Enables systems to handle the repeatable, predictable, and previously manual tasks of traditional IR processes, freeing up your analysts to focus on complex issues and accomplish more.
- Orchestration (aka integration) – Standardizes the inputs and outputs across disparate systems and tools, enabling two-way, machine-to-machine communication and control. Tightly coupled with automation, orchestration helps analysts pivot across indicators and get fast answers to questions—without the need for manual queries and lookups.
Incident Response Playbooks
A common way for SOC teams to pass along expertise is through response runbooks, or playbooks. By codifying SOPs and best practices for handling specific threat types, they’re often used in training junior members in how to become more effective.
We recommend that you consider automating your playbooks, thereby coupling actions with logic and providing analysts with pushbutton activation. But the skills required to implement this type of response automation are ordinarily beyond the capabilities of many security organizations. For this we have an answer.
Exabeam Smart Timeline, a key artifact of Incident Response
One of the key steps in incident response is automatically weeding out the false positives and stitching together the event timeline so that the investigation is more accurate and faster. Exabeam provides pre-built Smart Timelines that automatically stitch together both normal and abnormal behaviors, so investigators can accurately pinpoint the series of anomalous events, along with its associated assets, users, and risk reasons—which are all attached to the timeline. This saves a lot of time and investigators are able to mitigate security incidents quicker, lowering the mean time to respond (MTTR)
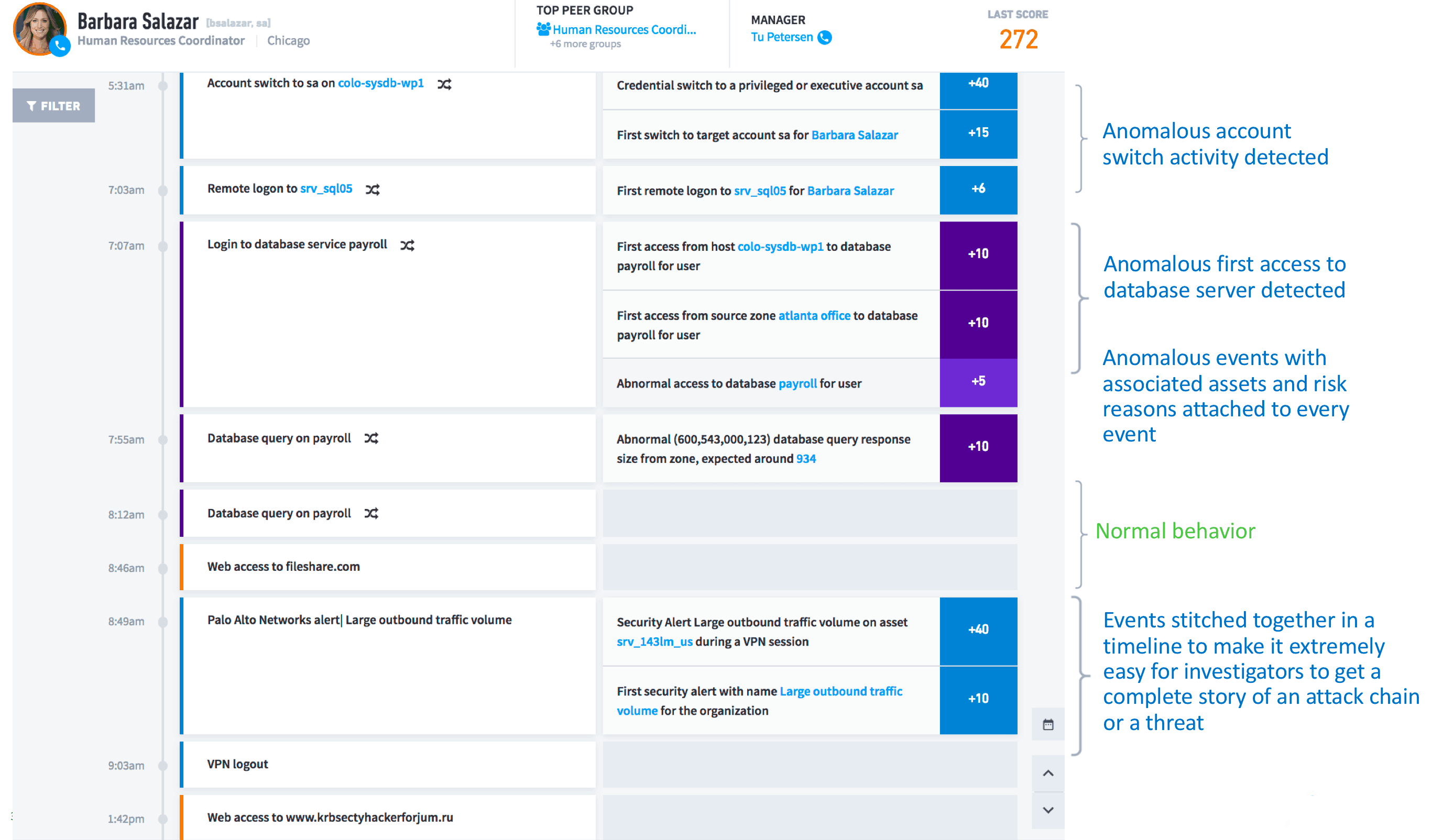
Figure 1 – Exabeam Smart Timeline provides the complete story of user behavior so investigators can pinpoint the anomalous and respond to security incidents faster (low MTTR).
Automation and Orchestration with Exabeam
Exabeam Incident Responder comes with numerous prebuilt playbooks and templates that give you easy-to-customize responses to common threats—such as phishing, malware infection, data exfiltration, and others.
Advantages to using Exabeam’s solution include:
- Pre-built Smart Timelines to get a complete story of an attack chain or a threat
- Two-way integration with hundreds of security and non-security products
- Easy to use, drag-and-drop configuration—no programming required
- Easy to customize and highly configurable
- Fully integrated with Exabeam Advanced Analytics (detection) and Exabeam Case Management
- Lowers mean time to detect (MTTD) because of comprehensive behavior analytics feature sets
- Lowers mean time to respond (MTTR) with its Smart Timelines and orchestration capabilities
Exabeam playbooks can also help with communication bottlenecks affecting most IR efforts. Security analysts often need to reach out to users to confirm unusual behaviors, file tickets with other teams to initiate mitigations, and get approvals to take more drastic containment steps. Exabeam playbooks can integrate with other communication systems, including IT service management and messaging/ChatOps. And they can be configured to pause so as to solicit input or stakeholder approval, or let a human decide on the best course of action.
Figure 2 shows an analyst playbook interaction for a malware process flow. It shows the various triggers, events, and actions that can be assembled using a drag-and-drop interface.
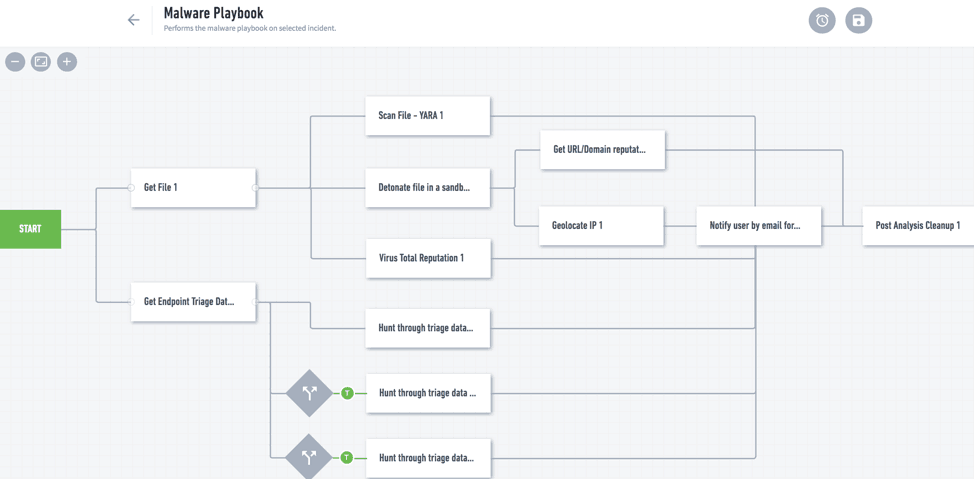
Figure 2 – Sample Incident Responder playbook response for a malware infection
When run, the playbook returns essential information security analysts can use in the investigation. These results appear in cards for quick review (Figure 3).

Figure 3 – Exabeam Incident Responder playbooks runs show results in multiple cards for quick review
In addition to seeing playbook results, you can pass information returned from one to other playbooks—such as one that automatically contains a threat and another that will block future incidents of the same type.
Get ahead of your Incident Response bottleneck
The more time a security incident remains unmitigated, the longer your organization is exposed to breach risks. Orchestrating your systems and automating your response playbooks can eliminate much of the time and tedium required to mitigate security events, while freeing your analysts to focus on more critical issues that demand their high-level skills.
Here’s more information about how Exabeam can help you achieve your IR goals:
- 5 Best Practices for Your Incident Response Plan
- White paper: The Incident Response Makeover Guide – Understanding how automation can slash response timelines and include SOC productivity
- White paper: Step-by-Step Incident Response for Today’s Top 3 Security Scenarios
- White paper: Streamlining IR Operations with Orchestration and Automation
- Datasheet: Exabeam Incident Responder
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













