SIEM Explainers:
Exploring SIEM Examples: Modern Capabilities and Top Solutions for Cybersecurity
Security information and event management (SIEM) has become a fundamental component of the security toolbox, combining two functions: security information management and security event management. It was designed to use rules and statistical correlations to turn log entries and events from security tools into actionable information. This information helps security teams detect threats in real time, manage incident response, perform forensic investigation on past security incidents, and prepare audits for compliance purposes.
While specific requirements vary for organizations of different sizes and industries, SIEM systems offer a well-rounded security solution that can look holistically across an IT environment to identify real security threats before they disrupt business operations or cause lasting damage to their brand and reputation.
How does SIEM work?
In the past, SIEM solutions required meticulous management at every stage of the data pipeline — data ingestion, policies, reviewing alerts, and analyzing anomalies. But SIEM solutions are getting smarter at pulling data together from far more IT and security sources.
Data collection
Most SIEM solutions collect data by deploying collection agents on end-user devices, servers, network equipment, or other security systems like firewalls and antivirus, or via protocols syslog forwarding, simple network management protocol (SNMP), or Windows management instrumentation (WMI). More modern SIEM systems can integrate with a wide range of data sources including cloud services, network data and on-premises log data, and other non-standard data sources like badging systems, OT controllers, and multiple threat intelligence feeds.
Data storage
Traditionally, SIEM solutions relied on storage deployed in the data center, which made it difficult to store and manage large data volumes. As a result, only some log data was retained. Modern SIEM systems are built on top of modern data lake technology such as Amazon Simple Storage Service (S3) or Hadoop, allowing nearly unlimited scalability of storage at a low cost. This makes it possible to retain and analyze 100% of log data across even more platforms and systems.
Policies and rules
SIEM allows security staff to define profiles, specifying how enterprise systems behave under normal conditions.They can then set rules and thresholds to define what type of anomaly is considered a security incident. Increasingly, SIEM solutions use machine learning (ML) and automated behavioral profiling to automatically detect anomalies and dynamically define rules on the data, to discover security events that require investigation.
Data consolidation and correlation
The central purpose of a SIEM solution is to pull together all the data and allow the correlation of logs and events across all organizational systems. An error message on a server can be correlated with a connection blocked on a firewall, and a wrong password attempted on an enterprise portal. Multiple data points are combined into meaningful security events, and delivered to analysts by notifications or dashboards. Modern SIEM solutions are getting better and better at learning what is a “real” security event that warrants attention.
Modern SIEM capabilities for today’s cybersecurity challenges
As SIEM solutions have evolved over the years, they now go beyond rules and correlations to include additional advanced functionality throughout the threat detection, investigation, and response (TDIR) workflow. This enables more complex threat identification, making behavioral anomalies visible to security teams. Advanced automation has replaced many manual tasks including incident response.
User and entity behavior analytics (UEBA)
UEBA enables SIEM solutions to go beyond signatures, rules, and correlations, using artificial intelligence (AI) and deep learning techniques to look at patterns of human behavior. This can help effectively detect zero-day and insider threats, which may not correspond to known attack signatures.
Security orchestration, automation, and response (SOAR)
Modern SIEM systems integrate with enterprise systems and automate incident response, rather than simply monitoring and alerting. For example, the SIEM solution may detect an alert for ransomware and perform containment steps automatically on affected systems before the attacker can encrypt the data, while simultaneously creating communications or other notifications.
Additional advanced capabilities
- Complex threat identification — Correlation rules can’t capture many complex attacks, because they lack context, or can’t respond to new types of incidents. With automatic behavioral profiling, SIEM can detect behavior that suggests a threat.
- Detection without rules or signatures — Many threats facing your network can’t be captured with manually defined rules or known attack signatures. SIEM systems can use ML to detect incidents without pre-existing definitions.
- Automated attack timelines — Traditional SIEM solutions require analysts to collate data from various sources to make sense of the attack timeline. This can be time consuming and requires special expertise. Modern SIEMs can automatically build an attack timeline and present it visually so that less specialized analysts can understand it. This makes investigation and incident triage much faster.
- Cloud delivery — Cloud-native SIEM solutions leverage elastic cloud storage and data lakes. This makes them much more scalable than traditional, on-premises SIEM systems, which rely on equipment that cannot handle the massive volumes of data generated by large enterprises.
Choosing a SIEM Solution
With all the options available, choosing a SIEM solution can be a challenging task. The SIEM examples above are all robust solutions with broad user bases. It’s important to not only evaluate functionality, but the vendor’s track record and market position as well. Consider what you need today and will likely need in the future.
SIEM solutions on the market today all offer a range of features and functionality.
Exabeam Fusion
Exabeam Fusion is a cloud-native solution that uses a behavior-based approach for TDIR. By aggregating all relevant events and weeding out illegitimate events, Exabeam Fusion boosts analyst productivity and detects threats missed by other tools. This improves detection rates and response time, and ensures that all alerts are considered — even those coming from “noisy” systems that generate many alerts. Exabeam Fusion combines SIEM logging and correlation with UEBA to see signature-based events, correlated events, and behavior anomalies together in a single timeline.
In addition, Exabeam Fusion is natively integrated with its SOAR capability and offers easy extensions out to more than 100 vendor products, providing automated incident response operations to configured (and customizable) scenarios. This enables almost any threat to be dealt with automatically or via trigger in real time. Prescriptive workflows and prepackaged use case content (external threats, compromised insiders, and malicious insiders) enable successful security operations center (SOC) outcomes and response automation. Exabeam Fusion also provides the cloud-based log storage, rapid and guided search, and comprehensive compliance reporting expected of any modern SIEM solution.
Splunk
Splunk has a SIEM solution that is based on its ability to handle both security as well as application and network monitoring use cases. This makes it popular with both security teams and IT operations. Like other top SIEM solutions, Splunk’s SIEM provides information in real time and the user interface is relatively user-friendly. Pricing is based on workloads protected.
Splunk Enterprise Security has limited integrated behavioral analytics and automation capabilities, which creates a challenge in detecting advanced threats and tactics such as lateral movement. The solution requires significant customization to be effective for most organizations and is not built in. To detect lateral movement, many custom queries need to be run by a specialized user, potentially resulting in a large number of alerts on benign activity. One other challenge users report is a lack of clean integration across product capabilities: SIEM, SOAR, and UEBA.
Microsoft Sentinel
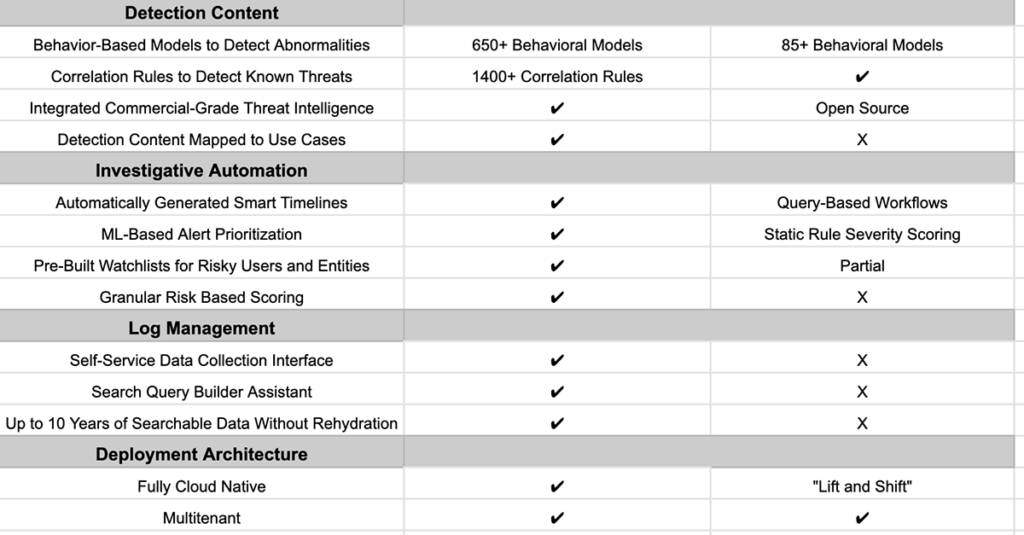
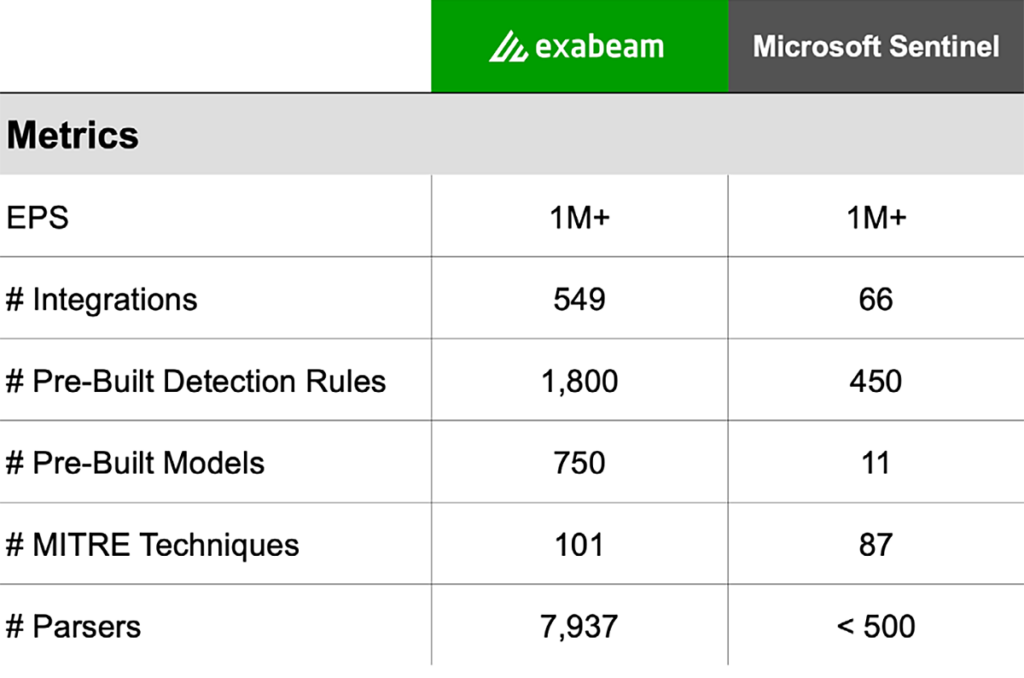
Microsoft Sentinel is a cloud-based SIEM that is primarily focused on the collection and consolidation of Microsoft cloud security logs and events, although they do support logs from a limited number of non-Microsoft solutions. It is a popular choice for customers who work in Microsoft environments and are looking to unify all their tools under one security management platform. It also offers a unique pay-as-you-go licensing model which meets the budget requirements of many SMBs. Microsoft Sentinel is also known for its smooth data onboarding process — again, for Microsoft product logs.
With their Microsoft-first approach to security, Sentinel UEBA supports limited data sources with limited use cases. Provided content also fails to cover the entire TDIR lifecycle and automation rules, and playbooks are complex and require coding skills. Sentinel licensing is complicated and can hide many necessary costs — for instance, offering log storage for free while not illustrating the usage, search, or limited scope under what qualifies as “free”.
IBM QRadar
IBM QRadar SIEM allows you to view your IT infrastructure in real time and monitor events triggered from those sources along with security alerts. It is a modular architecture that facilitates the detection and prioritization of threats. QRadar supports multiple logging protocols and offers various configuration-side options, as well as high-end analytics. The solution provides an app store where customers can download additional IBM and third-party content to use with QRadar.
IBM QRadar is fairly costly and has a complex pricing model. In addition, QRadar has weak UEBA capabilities and limited visualization capability, which are a basic requirement of modern SIEM solutions. Other drawbacks are that upgrades can be complex and require extensive effort, as there is often limited product support (although you can purchase upgraded support). The product has limited visualization, and limited reporting capabilities which must be supplemented with externally-developed scripts.

Conclusion
As cyberattacks become more common and higher profile, it is more important than ever to understand what security tools are available to provide the necessary defense. SIEM solutions centralize security and event notifications in a single platform, managing all stages in the data pipeline, including analyzing anomalies. Modern SIEM solutions add intelligence to improve organizations’ security profile, using functionality like SOAR and UEBA to automate threat detection, reduce alert noise, and respond to threats. The best SIEM solutions cover these core capabilities, and add modern features designed to stop the next attack.
Want to learn more about SIEM?
Are you struggling to find a reliable SIEM solution? Exabeam offers a purpose-built solution that simplifies security investigations and helps teams detect intrusions and malicious activity. With user-friendly search interfaces, context-enhanced parsing, and data visualization, Exabeam can cut security task time by 51%.
Watch our on-demand webinar, Not All SIEMs Are Created Equal.






