USING SMART TIMELINES AND CONTEXTUAL ENRICHMENT TO DETECT LATERAL MOVEMENT
Lateral movement refers to techniques cyber attackers use to progressively move through a network, searching for targeted key data and assets.
In today’s security landscape, hackers are becoming more sophisticated. They use multiple ways to get basic access, such as a phishing attack or malware infection, then impersonate a legitimate user while looking to elevate their privileges. They typically aren’t concerned with being detected—most organizations don’t have the staff, tools, or bandwidth to detect that anything unusual is going on.
Once a bad actor has gained a foothold, it might take days or weeks to perform reconnaissance to find weaknesses in your systems. For example, a database might have a default system administration account, or a user having access to all of your customer records might be using a weak password. Once inside, it’s not uncommon for an attacker to change systems and identities as they learn more about your network topology.
Once the attacker has found something of interest, often they spend time staging the data before finally exfiltrating it. These actions might not happen until a month or more after the original attack.
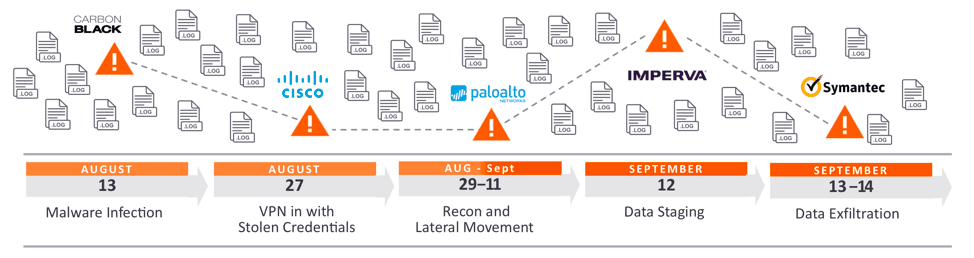
Figure 1 – A malicious actor VPNs with stolen credentials, moves laterally finding critical assets, and eventually exfiltrates data.
It’s expensive to detect modern attacks using legacy products
With most legacy cybersecurity products, you pay based on the amount of log data you ingest. As your organization grows, you hire more people, perhaps spread across multiple locations, and add many IT products to provision everyone with the network access they need. Your logs—and costs—grow exponentially.
Most organizations cherry pick their data, gathering only what they believe to be the most critical logs. Typically, they decide to completely ignore “chatty” logs from endpoint detection and response (EDR) systems and routers. But without the insights such logs provide, they’re blind to the advanced attacks seen today such as lateral movement.
Most organizations hunt for attacks using ineffective and unscalable methods
Even if your budget can withstand the cost of ingesting every log file, and you have the staff to conduct comprehensive investigations with all of that data, using traditional (manual) hunting and pivoting methods is ineffective and unscalable. Your investigations will take too long to produce the results you will need to mitigate a breach.
One problem with manual methods is the signal-to-noise ratio your team has to deal with. For example, without doing a lot of work, how do you know whether a user who just logged in from Beijing is actually at that location at this time? Or whether they have the privileges to access your customer database? How long would it take your team looking at their log files to determine the user’s name, machine, and supervisor and list the locations the user normally connects from, then stitch all of this data together to assess the validity of the user’s actions?
Another problem is getting the right data at the right time to connect all the parts of a potential attack. Many of your logs don’t contain critical information. For example, Log 1 might have user information and a device name, but no IP address. Log 2 might have an IP address and device name, but no user information. Log 3 might have only a user name and time, and nothing else. You end up with disparate information, insufficient context, and an incomplete timeline. Figure 2 shows a jumbled set of such log entries.
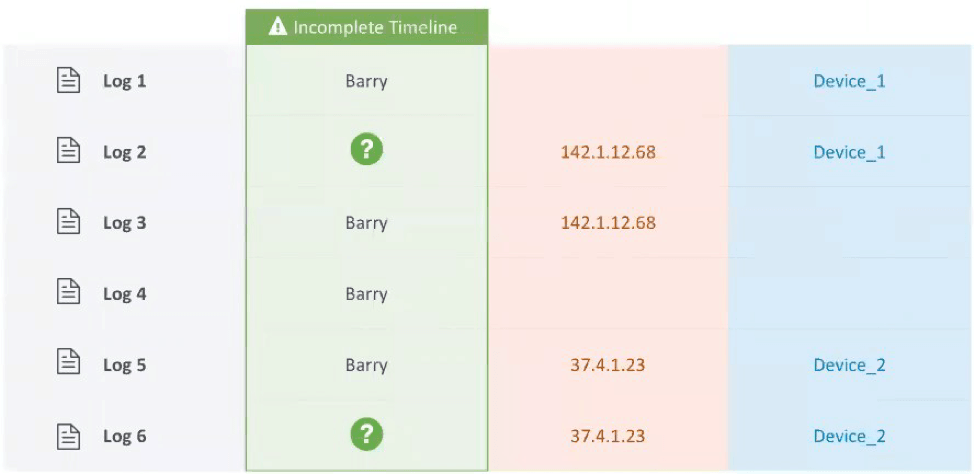
Figure 2 – Example of an incomplete timeline manually constructed from a number of logs
Correlation rules don’t work for these types of investigations. It takes a lot of manual effort to run queries from multiple data sources to stitch together events manually to create a timeline. When eventually armed with the needed information, your security team then has to investigate every instance where potentially suspicious activity occurred—or risk missing critical parts of an attack. And if each investigation takes 2 – 3 hours (a very optimistic estimate), how many highly skilled security analysts would be unnecessarily tied up with all the security alerts?
…lateral movement actions often eschew malware in favor of stealing or reusing a valid user’s credentials…impersonating a valid user gives attackers a quieter and subtler way to spread through a network than directly exploiting multiple machines…it’s critically important for security professionals to build up the internal network intelligence that can recognize the tell-tale signs when credentials are abused or abnormally used.
Lateral Movement: When Cyber Attacks Go Sideways
Wade Williamson in Security Week, April 11, 2016
Security teams need smart, contextually-enriched timelines with contextual insights to surface attacks involving lateral movement.
Exabeam Smart Timelines detect anomalous events before a security breach
What if you approach attack investigations in a new way—relying more on data analytics and machine learning? Assume you can ingest all the data from every log, and that the cost—regardless of the data amount—isn’t a factor. Then imagine a technology that constantly examines all of the data collections, stitches it together, and then enriches it with data from other sources.
The result is a Smart Timeline with the missing details automatically filled in. Exabeam Smart Timelines stitches together both the normal and abnormal behavior for every user, machine, and asset on your network. It automatically baselines normal behavior, so it becomes easy to detect the deviations. Now you can immediately notice when something unusual is starting to occur. Using a pre-generated timeline for every user and device provides insights you’ve never been able to surface before.
For example, the system might reveal that a user logged into your VPN from China and accessed executive assets to exfiltrate sensitive information, and this is the first time this has happened. With Smart Timelines you can do the following:
- Examine the person’s timeline to see the details of what happened before and after the event
- Determine the user’s normal behavior and see the deviations from the normal.
- View the user’s name, associated assets, email, supervisor name and contact information and other details, and examine earlier sessions to learn if any notable anomalous behaviors exist.
- Make a call to the user’s supervisor to learn if the user is actually in China. If not, you can be almost certain you’re dealing with a threat.
Such an investigation might take between 1 – 5 minutes, not days!.
Exabeam’s Smart Timelines automatically combine sequence, behavior, identity, and scope into a security information model that’s shared with all Exabeam products—giving you a single, unified dashboard view of your entire network operation.
Smart Timelines follow lateral movement throughout the attack
Now assume a user’s credentials have been compromised, but neither you nor they know this has happened. User credentials can be used as a starting point of an attack where the attacker can then make a lateral movement in your network looking for other assets while using those credentials. Figure 3 shows how such an attack would be missed in a traditional investigation as it might appear completely unrelated to user’s timeline.
It’s easy to spot and attribute the lateral movement to a user’s session with a Smart Timeline—very useful for investigators looking to pinpoint the attack chain and respond quickly.
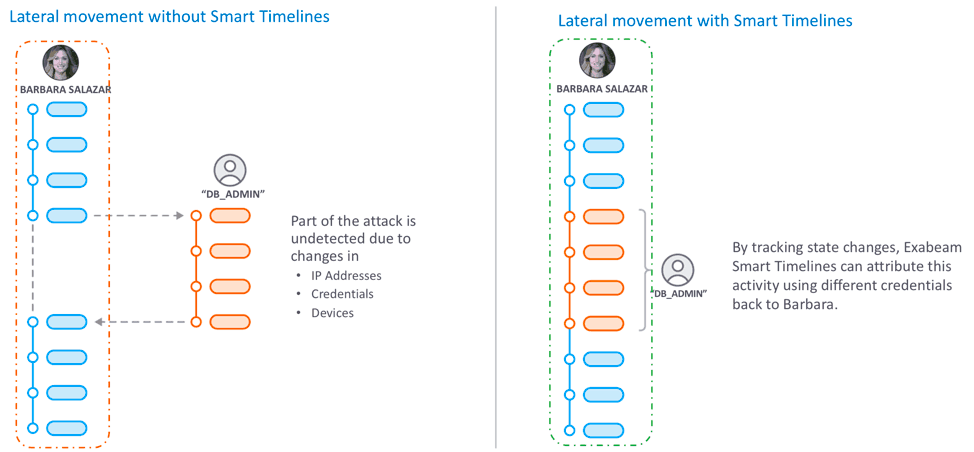
Figure 3 – An example of a lateral movement detection without and with Smart Timelines
Faster incident mitigation using a single-pane view of all related risk reasons
For a traditional investigation, security analysts must review many log files from multiple sources. Then they must painstakingly run queries and stitch together their findings to make sense of the events from these disparate systems—copying and pasting their findings and notes into a single location for reporting and mitigation purposes.
With Exabeam Advanced Analytics’ unified user interface (Figure 4), all investigations can be driven from a single application that is designed for gathering threat intelligence. It provides all the risk reasons, user details, and associated assets and their details, along with all the events stitched together in a timeline—making it easy for investigators to document and mitigate security incidents. Each abnormal action is assigned a risk score, with an accumulated total triggering an alert if it exceeds a predetermined value.
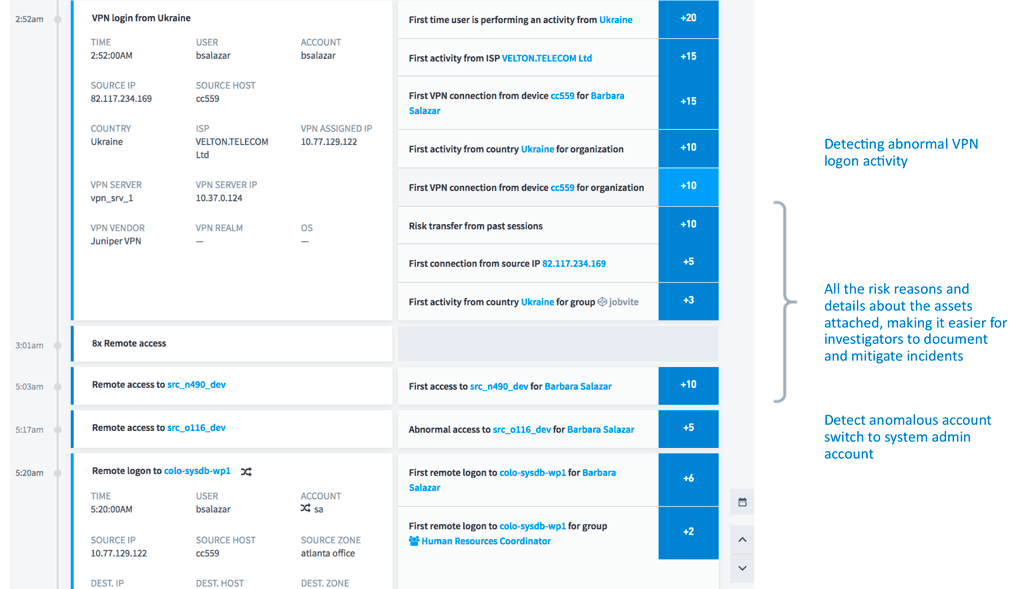
Figure 4 – Drilling down in Smart Timeline to view normal and anomalous user behavior and the associated risk reasons
Entry-level analysts can conduct productive investigations by drilling down from a user or asset, looking into the details of the incident, including the event timelines.
Exabeam Threat Hunter – An investigation tool
Exabeam Threat Hunter is a unique investigation tool that can be used to perform ad-hoc searches for gathering additional information. Investigators can search for related users and assets, which can be linked to their current investigation by using a drop-down menu—without writing queries.
Security teams can define broad or narrow anomalous behavior searches or look for specific threats—even if the behaviors haven’t resulted in a score that would bring it to their attention. Each panel’s drop-down list is auto populated with the user contextual information: User and activity types, peer groups, and geolocations; asset information; and the risk reasons analysts need to start a threat hunting session.
Exabeam Threat Hunter allows investigators to search for anomalous lateral movement indicators like account switching, remote asset logon, VPN activity, data upload to cloud and personal emails. This provides an effective tool for investigators to document and mitigate incidents while reducing mean time to detect and respond (MTTD/R)
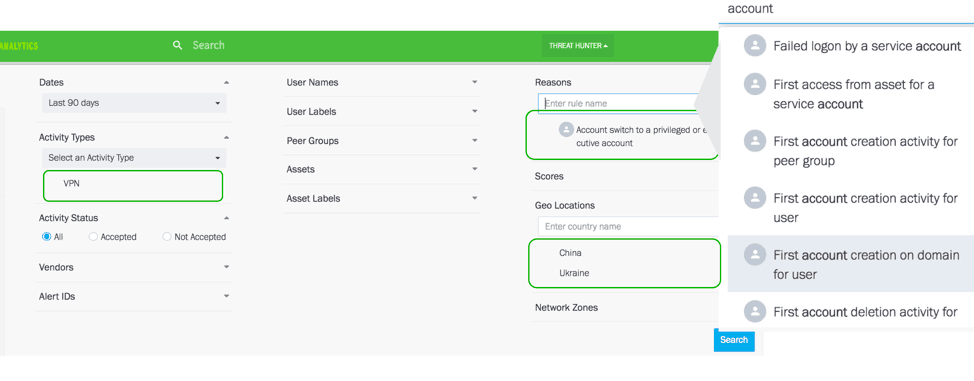
Figure 5 – Exabeam Threat Hunter: Analysts search by user activity, asset, event codes, anomalous lateral movement and risk reasons
For more information on Exabeam threat detection and investigation methodologies see:
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












