As cyber threats grow in number and sophistication, organizations must find improved strategies to protect their increasingly complex technology environments. Over-burdened security teams are now protecting even larger attack surfaces that include more cloud services, applications, and mobile endpoints. Adding to these challenges, there is the need to comply with increasingly stringent privacy laws like GDPR. Meanwhile, the market for cybersecurity specialists is running at zero unemployment, creating a widening skills gap that makes responses to cyberattacks more difficult, and an effective incident response (IR) plan a critical concern for any organization.
Why Does Your Organization Need an IR Plan?
Incident response comprises all activities and processes involved with investigating, containing, and remediating a security incident or breach after it has happened, as well as ongoing attacks and advanced persistent threats (APT). Because security incidents happen without warning, having a well-conceived IR plan in place allows security teams to quickly triage a security incident at a high-level and then point analysts in the right direction. More importantly, without an IR plan, teams cannot respond in a repeatable manner or prioritize their time—which is critical because today’s lean security teams receive more alerts than they have time to investigate. By standardizing, centralizing, and automating your security tools and methods into a well thought out and tested plan, your analysts can respond to security incidents quicker and more effectively.
For mid-sized enterprises with limited staff, or organizations with a team that lacks technical maturity, a good IR plan is even more critical. Logical processes, automation, and the other benefits of a plan help organizations better deal with issues such as the tight cybersecurity labor market, and the loss of tribal knowledge due to attrition. In addition, by enabling smaller, less-skilled teams to respond quickly and effectively to the most credible alerts, organizations of any size can see potential ROI benefits from the reduction of full-time headcount.
A good IR plan that incorporates logical repeatable processes can also reduce an organization’s liability. For example, your IR plan should enable you to provide supporting documentation that may be required for data breach insurance. And in an era of increasingly strict and more punitive privacy laws, having a plan in place will help your security experts respond to incidents and give them more time to mitigate and prevent damage. This can save your organization from incurring possible legal costs and fines—not to mention the brand damage associated with a data breach. With the average cost of a data breach estimated at $3.62 million per incident (according to the Ponemon Institute), and with GDPR carrying fines of up to 4% of global revenue, these are not small concerns.
On a tactical, day-to-day level, a well-implemented IR plan will help your organization to identify and fix process gaps—also reducing their response time. This also enables response teams to leverage the information they uncovered during their investigation—allowing them to manage security events in near real time, so they can minimize and contain damage more effectively.
What are the Essential IR Capabilities?
A good IR plan allows you to treat a security incident like a crime scene. Your teams can cordon off the area (virtually, that is), then determine the extent of the attack and find all relevant correlations. By collecting and correlating all the data points from an attack and piecing together what happened, you can:
- Credibly discern the scope and severity of events
- Start a remediation process immediately
- Leverage automated tools, templates and playbooks to overcome the skills gap
- Provide an audit of the entire process surrounding an incident
For example, the first thing the investigator may want to know is who else executed a particular hash in their environment? The IR plan will tell the investigator to take the SHA256 hash and go into their software repository (hopefully there is one) and look at who has executed the hash in question. Now, the investigator has a complete list of the users that clicked on the file, which puts a perimeter around the investigation. This provides some finite information that helps the investigator understand the risk exposure from lateral movement, while providing a logical starting point for response and remediation.
According to the plan, the next step is determining what the threat does. For example, if the threat calls out to the Internet, the investigator would go into the firewall and look at who has accessed this IP address or domain. This will provide a list of everyone that called out to that command-and-control server and who might be pulling malware back to a machine.
Best Practices to Include in Your 2018 IR Plan
1) Automate – Use tools that allow your teams to respond to greater numbers of increasingly complex attacks—on more complex systems. Ideally, when there is a credible alert, this involves combining all the steps into a uniform response, based on the type of incident. Now, you can tactically automate repetitive steps, which enables analysts to focus on the most critical events and more strategic initiatives. For example, using the crime scene analogy above, automation could eliminate having to go into the SIEM to write a query or having to go into Bit9 (now Carbon Black) to run a report on a hash. As the analyst starts to build out these types of questions, each step can be automated. In other words, rather than having to go back manually and click a button, automation implemented in your IR plan does the work for you.
Figure 1 shows a readout of the emails of the recipients of a phishing email—a determination that is a critical part of any phishing investigation. It illustrates how a good IR tool can automatically search Microsoft Office 365 for all the emails received by the sender of a particular phishing message during the previous seven days.
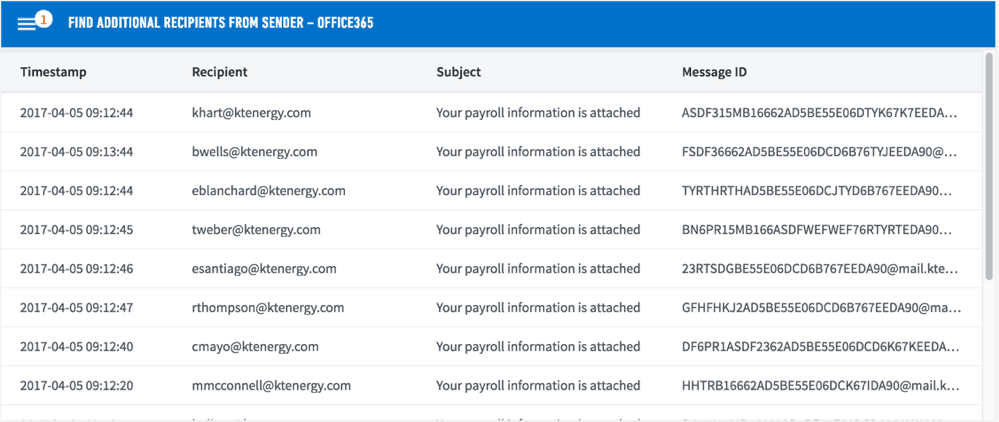
Figure 1 – A readout of emails of all those who have received a phishing email.
2) Leverage templates and playbooks – Tools that include agile playbooks and templates (for example, for phishing or APTs) can be customized or come preconfigured to automate multistep responses. These should adapt to the incident response details in real time, which includes guiding analysts through their response and outlining specific roles, responsibilities, and deadlines.
This phishing response is a great example of how teams can benefit from using IR best practices. Users often want to know about a suspicious email they have received. They might ask: “Is it good or bad? Can I click on the attachment or click on the link in the body of the email—or is it an actual phishing attack?” In a single day, security teams might receive hundreds of such queries from across their organization, and they have to respond to all of them, which involves investigating each one in the same way. Begin by looking at the header information, then review who it came from. Then determine if it is a spoofed address. If there are attachments or links, these may need to be detonated after determining if they are safe or not. And then finally, an email response must be sent to the user.
This graphic shows the order of operations in a typical phishing response, and how a playbook can automate the process.
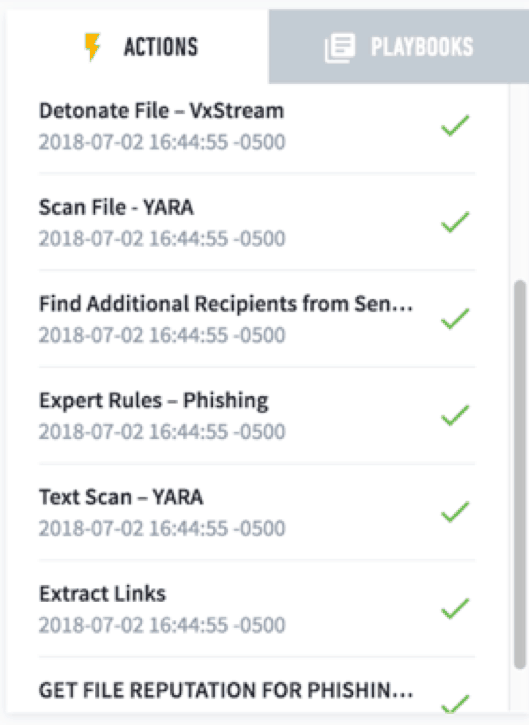
Figure 2 – A list of the automated steps taken during a phishing investigation.
A phishing investigation probably ranks as the most repetitive process analysts need to do, because unlike malware, they have to assume every email is a potential malicious phishing message. Performing all these steps—sometimes hundreds of times a day— can dramatically eat up analyst time. By leveraging a template or a playbook, analysts can treat each message exactly the same way, and automate all the many needed steps.
3) Adopt a centralized approach – Too often analysts must go into multiple tools to get a 360-degree view of an incident. For example, an investigator might have to go into one tool and ask it to show everything that happened on a particular computer. Then they must log in to another tool to find out if a user received any malicious messages, or if there were emails flagged as risky. Next, the investigator must go into their EDR tool and run a query to find out if anyone executed any of the suspicious attachments to determine the scope of the potential outbreak.
By contrast, a centralized IR approach gathers information from all your relevant tools into one timeline, so that you can conduct your investigation with all the needed data points in one place. This eliminates the “swivel chair” response that comes from having to use, at times, hundreds of tools. A centralized approach also orchestrates tools to enable rapid automated responses. This includes pulling in data from various security tools, applying analytics, and pushing actions out to other systems—for example, firewalls, email servers—to enable a more rapid response.
This approach not only gives you a centralized repository where you can get a full view of all of your different systems, but it also enables you to prioritize. It gives you an understanding of where your favorite tools stand in relation to your highest-fidelity events, and where they come in when you are launching incident responses. In other words, if I see this condition from this tool, I’m going to launch a particular incident response every single time.
A huge component of an effective IR plan is understanding what tools you have at your disposal and which ones give you the needed high-fidelity information. Many security departments invest in as many as 30 tools, making it an overwhelming job to determine which tools add value and provide the visibility teams need to protect their environments.
4) Battle test your IR plan – This includes exercises that review best practices, test various scenarios, and review performance. Then you can calibrate your plan to ensure it is ready for real-world threats. For example, you may want to rigorously test your visibility and tools at each phase of the kill chain. Basically, you do not want to detect everything at the point of data exfiltration. From a data protection, best practices standpoint—that is not where you want to start an investigation because the battle is already over. While that approach might provide faster remediation, you are going to lose every time. So, battle test your ability to detect threats quickly, and launch a response earlier in the kill chain. That way you can catch a security incident before your data leaves your environment.
5) Alleviate the skills gap – An effective IR plan can also address the problem of resource-constrained teams becoming overwhelmed with alerts, such as when there is too much noise and no ability to prioritize credible and critical events. By deploying tools with advanced analytics, automation, playbooks, and other capabilities, you can enable junior or new members of your security team to effectively respond to security incidents. This includes automating triage and enrichment tasks. This will also help all your analysts focus their energies on investigation and response—rather than on pivoting between tools and repeating basic steps.
It is also important to standardize the responses in your IR plan in order to reduce the ramp-up time for new analysts. Standardization, along with centralization and automation, will help to eliminate the need for extensive training. This means you can hire a more junior analyst who can start providing value more quickly—eliminating the need for so many ninjas, which is another ROI advantage.
Get with the Plan
Adopting a comprehensive IR plan in 2018 will go a long way toward preventing and mitigating the consequences of a cyberattack. Orchestration and automation of IR systems will also alleviate the current talent shortages in the cybersecurity industry, while improving your organization’s security posture by eliminating the common scenario of resource-constrained security teams struggling to identify critical incidents. Plus, an effective IR plan will improve your breach notification process and reduce the complexity of the breach obligations and notifications that are required when an attack results in the exposure of an individual’s protected data.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













