Has the Notorious Carbanak Cybercrime Spree Reached its Finale? What You Need to Know About Stopping the Next APT Attack.

In March 2018, the infamous and mysterious Carbanak mastermind was finally caught. The still unnamed leader of the Carbanak hacker gang (who some claim stole over $1 billion) accused of targeting banks, ATMs, and point-of-sale systems around the world was apprehended in Spain, according to the European Union Agency for Law Enforcement Cooperation (Europol).
According to Europol, since 2013 the Carbanak gang had been using a series of advanced persistent threat (APT) malware attacks originally called Carbanak (also referred to as FIN7, Anunak, and Carbon Spider), targeting financial institutions. It’s alleged that during Carbanak’s multiphased attack spanning five years, it distributed malware using phishing emails with malicious attachments that caused ATMs to release cash at set times for money mules to pick up, and even transferred money into the gang’s bank accounts.
While the true extent of the Carbanak cybercrime spree is controversial—the FBI and U.S. Secret Service issued a joint statement saying that they have not received a single report that Carbanak malware affected the U.S. financial sector (countering the claims made by some cybersecurity companies)—understanding and preparing for all the possible permutations of an APT attack is critical.
The Characteristics of Advanced Persistent Threats
Advanced persistent threats are continuous, stealthy, and orchestrated by those targeting a specific entity. The motives can be political such as the ViperRAT APT group that targeted the Israeli Defense Force by spying on their military and hacking into the personal Android mobile devices of Israeli soldiers.
Or, they can target retail using sophisticated strategies such as in the Neiman Marcus attack where 60,000 security alerts were missed as hackers stole credit card information during a protracted eight-month crime spree in 2014. Card-stealing software was automatically deleted from the point-of-sale payment register system at the end of each day, triggering hundreds of alerts that looked like false positives and went unheeded by the security teams.
One feature is clear, APTs’ multistep, covert, and persistent attacks can unfold over a long period of time, such as in the PF Chang’s security breach when data was stolen from 33 restaurant locations over eight months. And APTs feature a human-run command and control system that continuously monitors and extracts sensitive data from their victims such as in the Carbanak case.
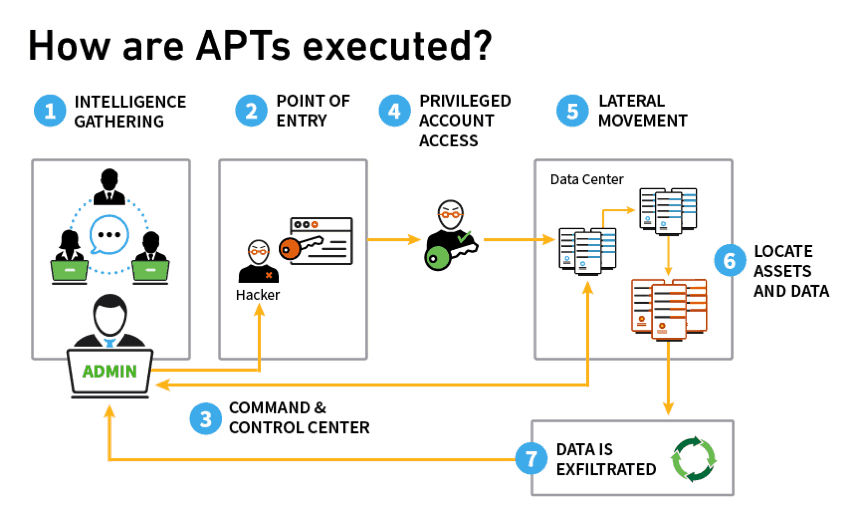
Figure 1 – These steps show how APT attacks are executed from the intelligence gathering stage to data exfiltration.
How to Combat APT Attacks Using Next-gen SIEM
As we’ve seen, APT attacks typically involve the use of stolen credentials, access to administrative assets, lateral movements, and organizational data exfiltration. Lateral movement is a method attackers use to move through a network by using IP addresses, credentials, and machines in search of key assets and data.
Modern SIEM solutions track suspected activities like changes to devices, IP addresses, or credentials. Using SIEM tools with behavior analytics can detect APT attacks because they’re able to track user behaviors more effectively, enrich the data with contextual information, track lateral movements, and detect data exfiltration.
Below are the approaches used by next-gen SEIMs to identify an APT attack.
Enrich Data with Context
Enriching your data with context is key. The first step is determining if the entities involved are servers, users, service accounts, or HR, finance, or executive employees. This is best achieved through the use of behavioral analytics. Data on events provide information on the actions of the users and entities, while context tells us the identities of the users and entities. Modern SIEMs can enrich contextual data dynamically. For example, determining what peer groups the user belongs to by comparing their behaviors to their peers will flag the anomalous. (For more information on understanding peer group behaviors, read the blog Dynamic Peer Analysis for UEBA Explained.)
Session Tracking for User and Entity Behavior Timelines
Identifying and tracking normal user behavior is key, so that anomalous behaviors and deviations can be identified. Advanced analytic tools can baseline user behavior for a period of time and establish a trigger for any deviations from the normal. Figures 3 and 4 show abnormal access of an asset and an abnormal data upload by a user.
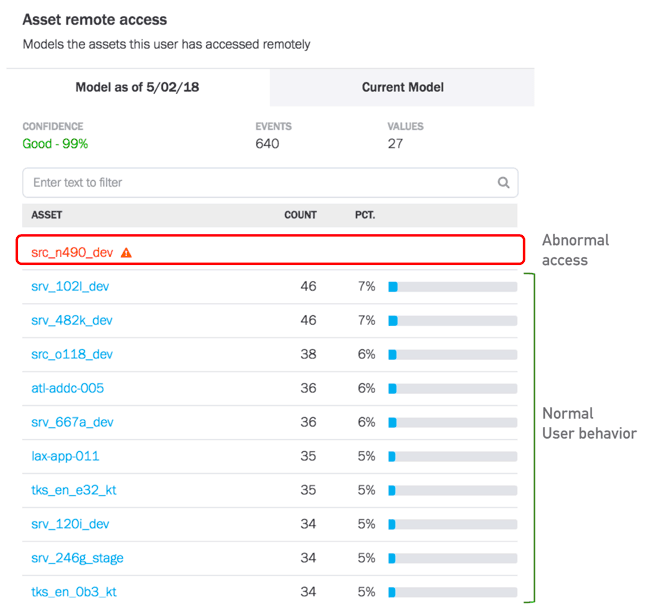
Figure 2 – This model shows normal and abnormal access of an asset by a user.
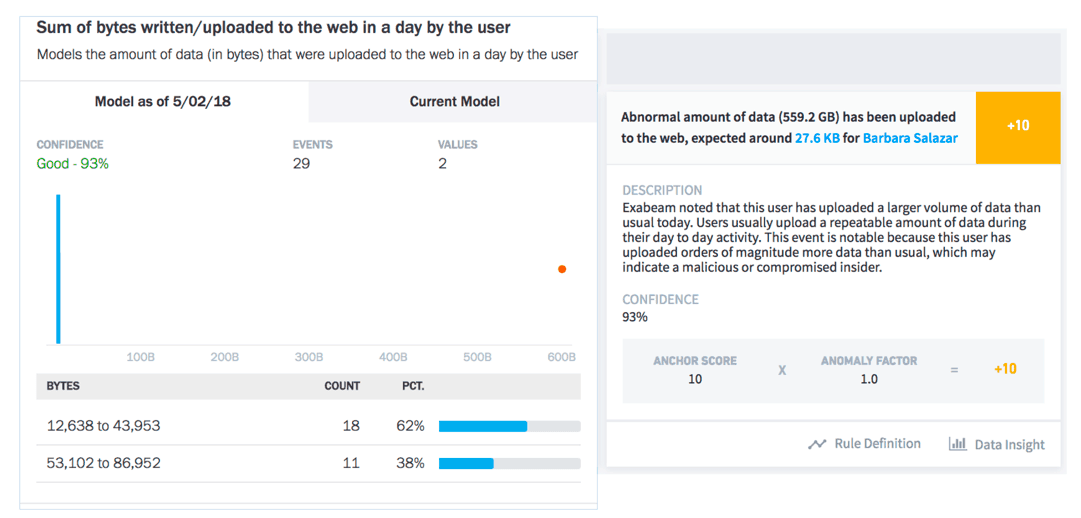
Figure 3 – This model shows abnormal data upload by a user.
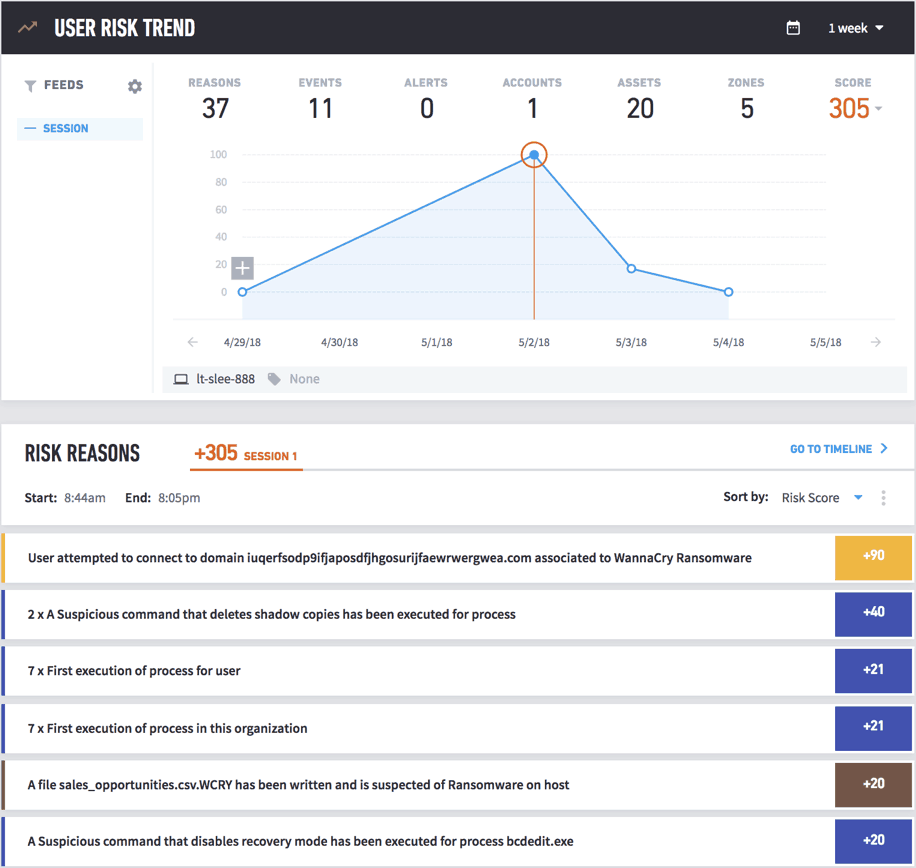
Figure 4 – This shows the tracking of a user session and shows risky behaviors with explanations for the behaviors.
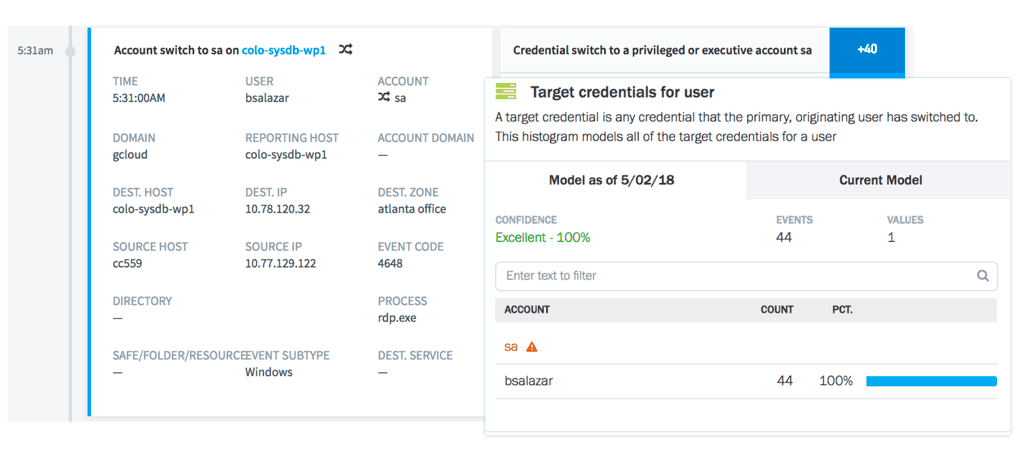
Figure 5 – A user timeline and model showing a switch to a privileged account.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!











