Ask the Experts Series
Until recently, most security operations centers (SOC) were dependent on their analysts’ skill level and relied on manual steps to detect the cyber threats to their organization. This typically required examining known indicators of compromise (IOC)—one painful threat at a time. When a suspicious behavior was discovered, analysts relied on advanced skills such as sophisticated querying to find the threat, then had to stitch together all the relevant events to understand the context and patterns in order to build a timeline of what occurred.
For example, let’s say there’s a server that has been compromised that is discovered through alerts and notifications. There are many critical questions that must be answered immediately: Who has accessed the server? What damage have hackers inflicted? Have they created any false accounts? Have they injected malware into any systems? Did they access the network through a VPN, and from where? While it’s possible to get answers to these questions when using legacy threat hunting techniques, for most organizations this is difficult and involves skilled resources and a lot of time.
Using modern threat hunting techniques, security analysts can more easily and effectively pinpoint specific threats and expose all the related activities that bad actors might be using to attack your infrastructure. Modern threat hunting replaces prior legacy discovery methods by using known threat intelligence and indicators of compromise, as well as understanding the known tactics, techniques, and procedures (TTPs) used by the most advanced hackers. Modern threat hunting tools should also rely on data science to uncover new, as-yet unknown cyber threats by constantly analyzing log and other contextual data.
In this blog post, I’ll help you understand how using modern threat hunting can help you proactively stay ahead of cyber threats, rapidly mitigate threats that have occurred, and keep your teams informed on a broad range of anomalous network activities so they can proactively investigate as needed.
Legacy threat hunting—The way it used to be done
SOCs are mainly focused on detection and response and they might not be using the most up-to-date threat hunting tools. This work involves manually examining unusual outbound traffic, suspicious privileged account activity, login issues, unusually high database read access, possible unauthorized changes to registries or system files, geographical irregularities, and other unwanted behaviors.
Without modern tools, threat hunting relies on collecting forensic data. Using forensics, threats must be uncovered by knowing exactly where to search within logs and other files—with the success of such time intensive and laborious processes often relying on the skill level of the analysts.
For example, it’s necessary to recognize the connection between multiple, lateral network moves by the person originally logged in as a non-privileged user, and then being able to identify any subsequent data exfiltration after that user has successfully elevated their privileges. The skills required to reliably prevent data loss in such a scenario aren’t always available or affordable in the quantities you need to protect your organization’s assets.
Here is another example. Let’s say that you need to find a non-executive user who logged into your network between January 1 and today by way of a VPN connection originating from China who accessed an executive asset. To conduct this investigation in a traditional SEIM environment, you’d probably follow a procedure like this:
1. Search for all users who connected from China over the targeted time period.
2. Write down or copy and paste the user names to a file.
3. Search each user to determine when they started and ended their session.
4. Write down or copy and paste this session information to a file.
5. Search your Windows log files to determine if each user accessed an executive asset during their corresponding session times.
For this investigation to be meaningful, you’d also need a list of executive users and their assets, along with the Windows event codes associated with various access types. You’d then have to join the individual queries and filter out all the users who accessed the executive assets. There probably aren’t many organizations with the skills and bandwidth needed to perform this type of investigation, especially in cases where there is no hard evidence of a threat.
Modern threat hunting—The effective way to detect anomalies
Using modern threat hunting techniques—backed by broad access to your aggregated log data—with enriched contextual data and behavior analytics becomes a matter of selecting among the behavior types, risk reasons, and user context to drill down into suspicious, unusual, or “first time” events. Exabeam Threat Hunter combines existing threat intelligence, IOCs, and previous attack TTPs, then applies data science to the aggregated data gathered by the Exabeam Advanced Analytics engine to surface threats as they evolve. Threat Hunter also exposes related behaviors that might point to more serious threats and uncovers past breaches you didn’t know have taken place.
Modern threat hunting centralizes all its controls and information in one place
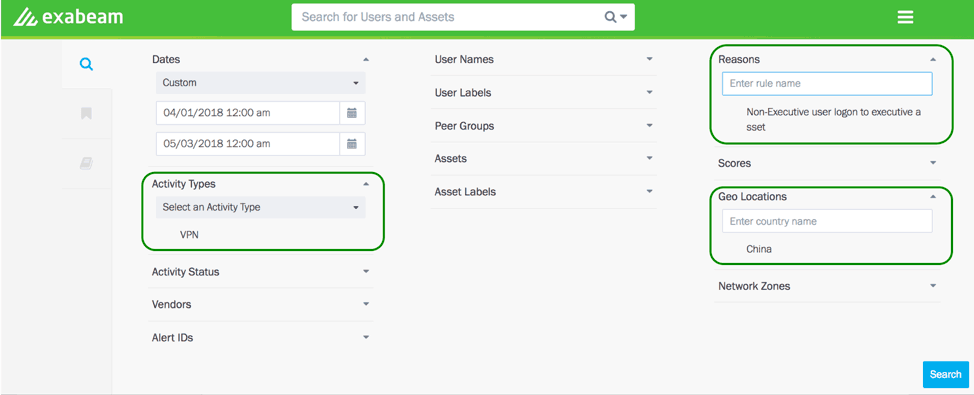
Figure 1 – Exabeam Threat Hunter – analysts can select user activity, risk reasons, and geo-location to pinpoint any non-executive users who logged into the network by VPNing from China, accessing an executive asset.
Here you can define broad or narrow anomalous behavior searches, or look for specific threats—even if the behaviors haven’t resulted in a score that would bring them to your attention. Each panel’s drop-down list is auto populated with all the user contextual information: user types, activity types, peer groups, and geolocations; asset information; and risk reasons that analysts can use to start a threat hunting session. Figure 2 shows the results from the threat hunting search criteria shown in Figure 1.
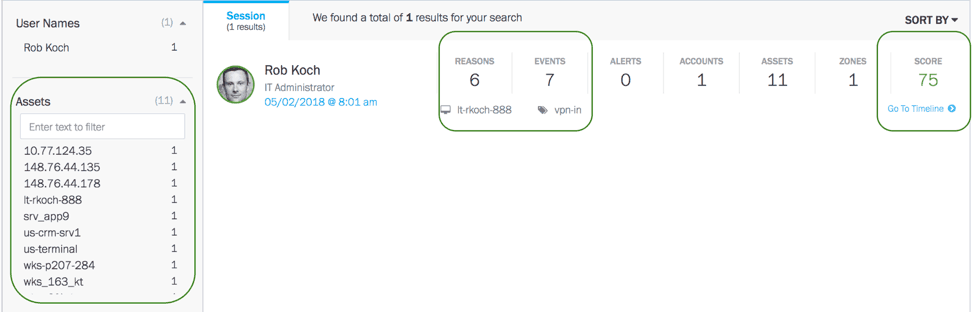
Figure 2 – Threat Hunting results show the risk reasons, all the assets the user accessed, and the risk score for the user. There is also an option for the analyst to drill into the user’s timelines to pinpoint anomalous behavior.
Your search identified a user account. The analysts can know the defaulted users from the results, and most importantly, can drill down to a specific user timeline and pinpoint all their activities and identify any anomalies.
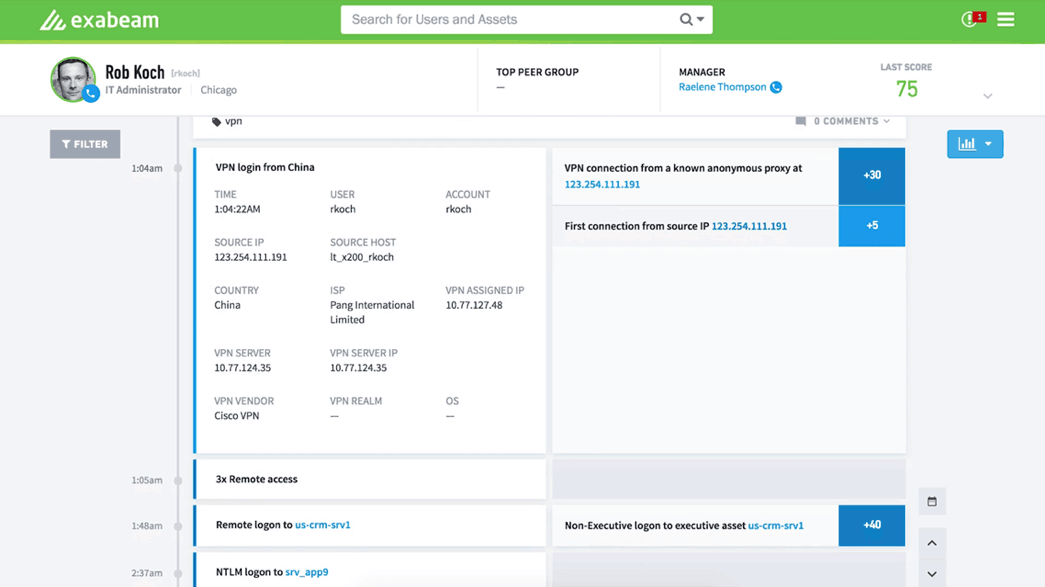
Figure 3 –Timeline showing all the behaviors stitched together: VPN access from an anonymous IP and logon to the executive asset, and the associated risk scores for the activity.
As you can see, it’s fairly easy to hunt for threats using Exabeam Threat Hunter. To summarize, here are the advantages of using a modern threat hunter like Exabeam:
• A point and click UI without the complex query language.
• Ability to run complex searches with context-aware data. For example, analysts are able to search by user type, user labels,
activity type, asset labels, user names, risk reasons, etc.
• Aid your investigators by stitching all the events together from their disparate sources, assess normal/abnormal behavior, and embed smart timelines
into search results so analysts can easily pinpoint anomalous behavior and mitigate incidents faster.
• Ability to save searches for future investigations.
To learn more about how Exabeam UEBA performs threat hunting, here are some more resources:
Exabeam Practitioner Training: Getting Started with Threat Hunting
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













