It was a big week in the world of golf with the 2018 PGA Championship starting. Some would say it was an even bigger week in the world of cybersecurity. On August 8, PGA staff discovered they had been hacked when suddenly they received a shocking notice. After attempting to work on some files, they received this threatening message:
“Your network has been penetrated. All files on each host in the network have been encrypted with a strong algorithm. Any attempt to break the encryption could cause the loss of all of the work. This may lead to the impossibility of recovery of certain files. We exclusively have decryption software for your situation. No decryption software is available in the public.”
Ransomware often targets victims with high-value data that isn’t backed up properly
Ransomware attacks often target victims with high-value, unstructured data. In this case it was the PGA Championship and Ryder Cup files consisting of marketing materials such as PGA banners, logos, and signage, which are the type of files that organizations frequently don’t back up properly.
The extortion currency of choice was Bitcoin
For the return of the PGA files, the hackers’ message also included a Bitcoin wallet number, which aren’t linked to an individual or an entity. Following the frequent advice of law enforcement, anonymous sources say the PGA will not meet any extortion demands. And as often is the case, it’s been stated that the PGA’s IT team has not regained complete control of their files or identified the source of the hacking.
Anatomy of the PGA attack
While details were not released by the PGA, experts have speculated, based on the ransom note, that the ransomware used was BitPaymer. What makes this case unique is the pause in execution after infection. In this case it remained dormant until the perfect time to encrypt the files (right before the start of the PGA Championship), so that it could inflict the most damage.
One of the most glaring differences between typical malware and ransomware is that the second ransomware finishes encrypting, it announces its presence to the user. It does this because it has already taken the victim’s machine and files hostage and wants to demand ransom in exchange for the return of these assets. Ransomware is also highly automated; beyond the distribution stage, most of the ransomware process runs autonomously without needing communication with a command and control center to receive instructions. Instead, ransomware executables contain all the logic required for their hijack.
An overview of the ransomware attack chain
Let’s examine this ransomware attack chain:
1. The attackers are thought to have used BitPaymer, but delayed encryption until Tuesday, just before the start of the PGA’s namesake event. According to the PGA, the attackers actually offered to demonstrate their ability to decrypt files as a sign of good faith.
2. The hackers were in the system for a period of time before they encrypted the PGA files. This type of attack is known as “low and slow attack.”
3. Ransomware attacks often target victims with high value unstructured data or files. In this case it was PGA’s marketing content.
4. Typically, ransomware uses a defined kill chain to function. See figure 1. This includes a distribution campaign, infecting the target system, establishing persistency, then scanning for files, encrypting those files, and showing a ransom and providing payment instructions.
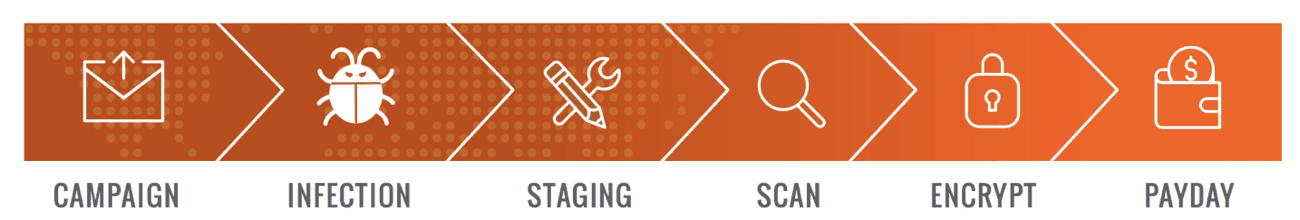
Figure 1: An example of a typical ransomware attack chain stages.
How organizations can proactively detect ransomware using a behavioral-based approach
Since all ransomware typically adheres to this same set of steps, it’s possible to use a behavioral approach such as User Entity Behavior Analytics (UEBA) to detect the behaviors that are associated with ransomware. By detecting phases earlier in the life cycle, such as during infection, staging, or scanning, it’s possible to identify the attack before encryption occurs. The PGA case differs from most other ransomware in that it paused after scanning, and encrypted the files when they would do the most damage (right before the PGA championship).
The key to stopping ransomware is to find attackers in your system before they begin to encrypt. Using a behavior-based approach is ideal to detect a ransomware attack, since it uses models and rules to track user behavior. Exabeam creates normal user behavior baselines and therefore is able to track any deviations from normal such as a user attempting to connect to illegitimate domain, and identifying any suspicious files downloaded by the user. Exabeam’s UEBA rules detect the first-time appearance of files and processes and will bubble up risky behavior that could be an indicator of malicious activity. See Figure 2.
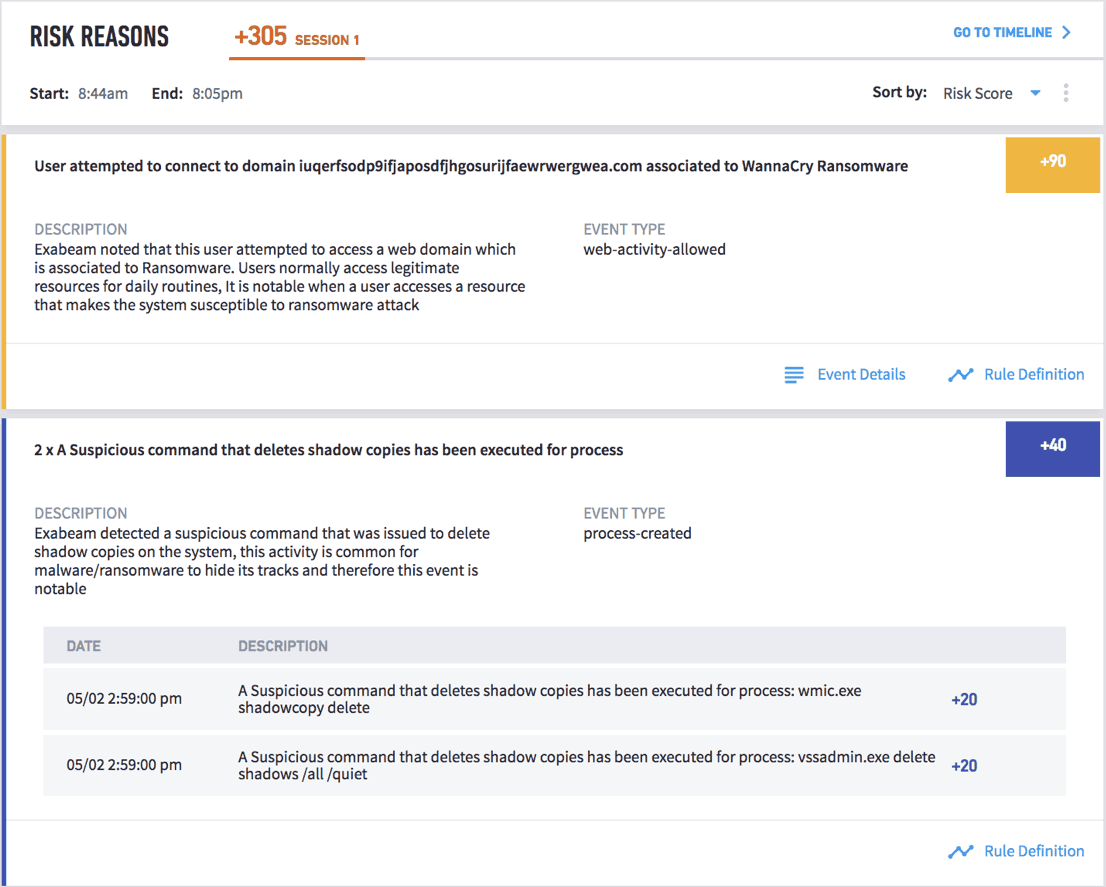
Figure 2: UEBA model rules detecting a user attempting to connect to a malicious domain and illegitimate file download.
During the scanning stage, many ransomware variants might scan local and network file systems as well as cloud file storage repositories such as Box, Dropbox and others, checking for read and write permissions. Exabeam behavior analytics track any first-time binary execution on peer groups, first time file access by remote groups, abnormal access to cloud services, first-time file access from remote locations and more and also provides rules to detect any abnormal file activities in the network.
See figure 3.
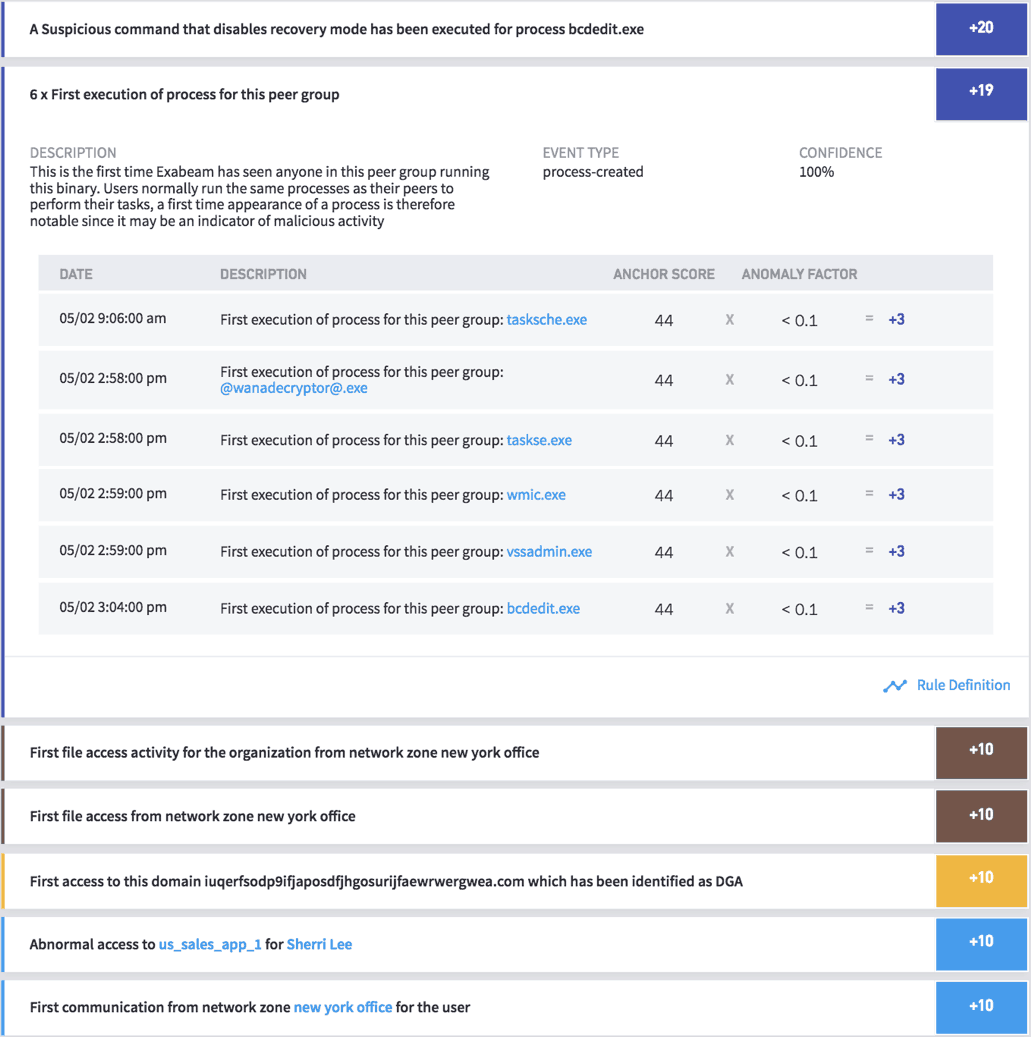
Figure 3: Exabeam detecting first execution of a binary by user’s peer groups, first file access from New York zone, abnormal remote access, and first-time access to malicious domain which might have been generated by a Domain Generating Algorithm (DGA).
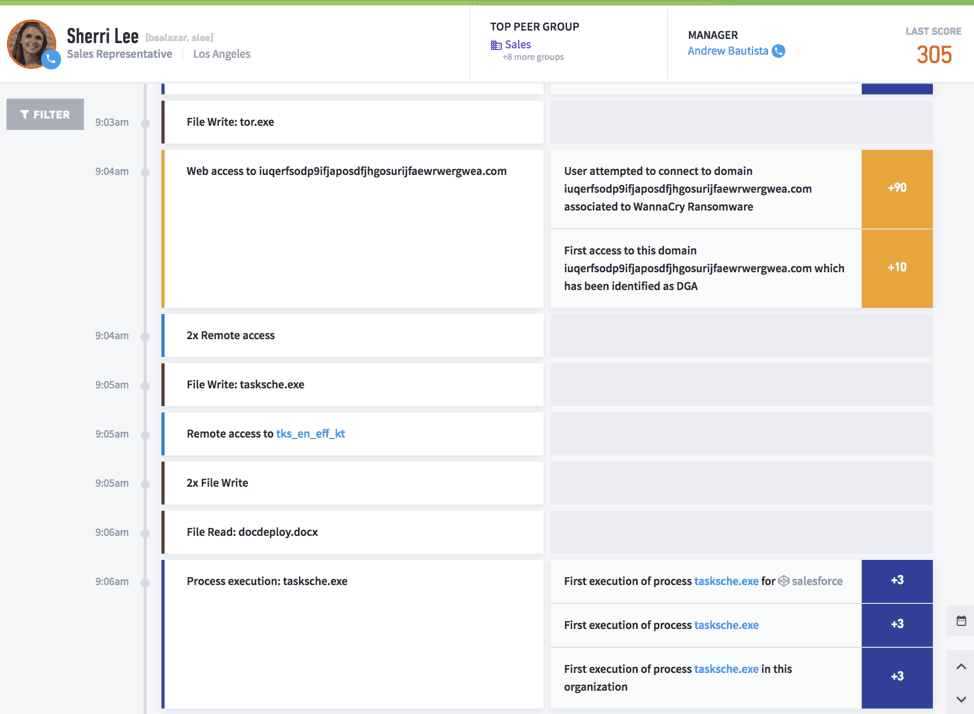
Figure 4: A timeline stitching together anomalous behavior, so investigators can pinpoint the ransomware attack pattern.
In addition to creating a timeline that shows all the relevant events, with UEBA, investigators can automate the response and block and contain the malware, preventing it from spreading the infection or impacting additional files. For example, Exabeam can automatically connect to third party services like IAM solutions to disable/suspend the suspected users or remove authorization from a group.
A behavioral-based approach to detection such as the UEBA used by modern SIEMs could have detected the PGA ransomware attack during the scanning phase, interrupting the attack before their marketing files were encrypted. In addition, automated response using SOAR technology, also found in modern SIEMs, allows for a quick response, stopping the ransomware from encrypting files en masse.
For additional information on telltale signs of ransomware attacks, see the Exabeam Ransomware Threat Report.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













