MITRE ATT&CK Explainers:
What is MITRE ATT&CK® Framework and How Your SOC Can Benefit
What Is MITRE ATT&CK Framework?
MITRE is an American-based non-profit organization created especially to provide technical and engineering guidance to the federal government. MITRE ATT&CK stands for Adversarial Tactics, Techniques and Common Knowledge.
Initially, the organization developed the MITRE ATT&CK framework for a research project conducted during 2013. By 2015, the framework was released to the public—for free – and today it helps security professionals in all industries protect their organizations against emerging and known threats.
The MITRE ATT&CK framework originally researched threats against Windows enterprise systems. Today, it also covers mobile, ICS, Linux and MacOS. The ATT&CK framework mainly contains publicly available threat intelligence and incident reporting. It provides insights on cyber adversary tactics and techniques employed by threat actors throughout the attack lifecycle.
In practice, MITRE ATT@CK helps security teams think like an attacker, and better understand the adversary. The framework offers not only a collection of data, but can be used to strengthen the security posture of organizations. The framework serves as a collective information base that helps professionals to detect and stop adversarial behavior. This is why cybersecurity analysts and threat hunters continuously contribute research on new techniques.
MITRE ATT&CK Framework Use Cases
Threat Detection Prioritization
Even highly-resourced teams cannot defend against all possible attack vectors. The framework offers teams a blueprint that helps them learn where to focus their threat detection efforts.
For example, one team may choose to prioritize threats that occur earlier in the attack lifecycle. Others may prioritize certain detections designed to identify the unique techniques commonly used by a specific attacker group known to target their industries.
Teams can explore the techniques, risks, and targeted platforms to educate themselves and inform their overall security plan, alongside using the ATT&CK framework to track their progress over time.
Evaluation of Existing Defenses
The ATT&CK framework can help evaluate current tools and assess the coverage provided by certain attack techniques. Different telemetry levels can be applicable to each unique detection. For example, one team may determine they require higher confidence in the depth of detection, while other scenarios may require lower levels of detection.
Teams should define the threats that must be prioritized by the organization, and evaluate how existing coverage measures up. Additionally, this can help during red-teaming activities—the matrix can help set the scope required for a pentest or a red team exercise, and also serve as a scorecard after and during the test.
Attacker Group Tracking
Organizations often focus their tracking efforts on certain known behaviors of specific adversary groups that are relevant to their sector or vertical. The ATT&CK framework continuously evolves as threats evolve and emerge. Organizations can use the framework as a source of truth that helps understand and track the behavior and techniques employed and exhibited by hacker groups.
What Are the ATT&CK Matrices?
The ATT&CK framework defines the following three matrices:
Enterprise Matrix
This matrix covers the stages of a cyberattack lifecycle that occur after an exploit is initiated. The MITRE ATT&CK enterprise matrix includes eleven tactics that address the actions a threat actor may need to successfully perform in order to achieve an ultimate objective. For example, an ultimate objective may be gaining initial access to a certain system, collecting data, exfiltrating data, or moving laterally.
In 2020, the matrix was modified to include sub-techniques and the 11 tactics now also include a collection of 184 techniques, each containing 0-15 sub-techniques.
Industrial Control System Matrix
The MITRE ATT&CK industrial control systems (ICS) matrix, like the enterprise matrix, covers the stages of a cyberattack that occur after an exploit starts. However, the ICS matrix focuses primarily on threats specific to supervisory control and data acquisition (SCADA) systems, operational technology (OT) and critical infrastructure.
Since the ICS matrix covers attack stages that overlap with the other matrices, it lists many of the same tactics. But due to the nature of the different platforms, two tactics from the other matrices are not included while the two ICS-specific tactics are included in the total eleven tactics. These tactics include a collection of 96 techniques. However, the matrix has not yet been updated to include the new sub-techniques format.
Mobile Matrix
The mobile matrix addresses the same cyberattack lifecycle stages covered by the enterprise matrix, including the same eleven tactics. The enterprise matrix, however, focuses primarily on enterprise networks, while the mobile matrix covers only attack vectors and threats that are specific to mobile devices.
The mobile matrix contains different techniques and sub-techniques than those covered by the enterprise matrix. The techniques center around mobile-specific attack vectors and do not cover any general attack vectors (even those that may also apply to mobile devices). There are a total of 100 mobile techniques, and the mobile matrix does not currently include a sub-techniques category.
Related content: Read our explainer on MITRE Engage.
How Does the MITRE ATT&CK Framework Compare to Modern Cybersecurity Standards?
The MITRE ATT&CK framework is a veteran in the cybersecurity realm, but that does not make the framework obsolete. In fact, the framework is becoming increasingly popular, and more information is added to ensure it remains relevant.
Government agencies, organizations and individuals are sharing intelligence with the framework and their continued contributions ensures the framework continues to evolve along with new threats and discoveries.
The framework provides a standardized language baked on tactics, techniques and procedures (TTP), which is both universal and accessible to all. Additionally, the framework offers detailed classifications on how attackers interact with systems across all environments.
Related content: Read our explainer on What are TTPs.
Unlike other security frameworks that are designed for specific users and industries, the MITRE framework provides a broad scope of security best practices applicable to any organization. Here are several common security frameworks:
NIST Cybersecurity Framework
NIST stands for National Institute of Standards and Technology. NIST is a US agency that offers a host of information, including security frameworks. The general-use security framework was created to help any organization interested in strengthening their cybersecurity posture.
The NIST framework is considered both flexible and cost-effective. It includes a five-step process designed to address cybersecurity risks as well as maint security infrastructure. The steps outline several methods that help in the identification, protection, detection, response and recovery from attacks.
NIST SP 800-53
In addition to the general framework, the NIST also created another framework—SP 800-53—which defines several security requirements for federal information systems and the entities that either support or use these systems.
The goal of this framework is to protect critical and classified data stored in government networks. It outlines clear security measures designed to improve the security posture of federal agencies as well as their contractors.
HITRUST
The Health Information Trust Alliance’s Common Security Framework was created especially for healthcare organizations. It helps protect information systems that handle protected health information when in transit, as well as at rest.
The HITRUST framework provides concrete recommendations designed to protect healthcare data as well as achieve and maintain compliance with regulatory entities, including the Health Insurance Portability and Accountability Act of 1996 (HIPAA).
ISO 27000 Series
The ISO 2700 standard was created by the International Electrotechnical Commission and the International Organization of Standardization for information security management systems. The goal of ISO 27000 is to help managers stay on top of security controls and measures. The framework has made available several publications. It covers many aspects of security, including security controls and effective management of IT operations.
MITRE ATT&CK Framework and Next-Gen SIEM
Modern security information and event management (SIEM) solutions, or Next-Gen SIEMs, aggregate information from a variety of sources, and apply advanced analytics on the data, to help determine the next right action. When security threats are detected, or anomalies surface with users or entities, Next-Gen SIEM tools can initiate an automated response action as well as push alerts to administrators.
The importance of information for effective Next-Gen SIEM
Information is a core element of Next-Gen SIEM technology. To perform well, these systems need a solid information base. The tool can then baseline normal behavior, categorize threats, correlate activities under each threat, and provide the relevant information with an automation, escalation, or an alert.
To be effective, Next-Gen SIEM tools need to identify the behavioral anomaly, connect it to an attack pattern, its objective and the available remediation. This enables the system to generate an effective automated response and provide administrators with the information to take action and prevent future occurrences of the event.
How the MITRE ATT&CK framework improves Next-Gen SIEM
The framework provides the following features that support SIEM:
- A solid knowledge base – the level of information needed to enable effective SIEM requires a comprehensive and regularly updated knowledge base. It must contain enough information to help pinpoint the techniques, tactics and tools used by threat actors. SIEM solutions can integrate with the MITRE ATT&CK framework and gain detailed information about each threat discovered by the tool.
- Standards terminology – while online sources and published research may use different names for the same techniques, the ATT&CK framework provides standard terminology which is widely used and accepted. SIEM systems can use the ATT&CK classifications in reports to provide consistency in terminology and enable IT and security teams to easily understand and make use of this information.
- Information on adversaries – cybercrime groups can deal massive damage to their targets. They may be funded by governments or consist of confederations of individuals who do not even know each other’s faces and names. However, each group is unified under certain attack methods. The MITRE framework provides information about the modes of operation of certain groups. SIEM tools can leverage the information to identify attacks by these groups.
- Use Case content alignment – Next-Gen SIEM solutions provide “content”, use case coverage that includes detection and response patterns, and aligns with the MITRE ATT&CK framework. For example, a solution can provide a threat response pattern that includes the attacker’s likely actions, mapped to response playbooks that can be instantly activated, either manually or automatically
MITRE ATT&CK Framework and XDR
Extended detection and response (XDR) solutions correlate data generated across multiple locations, including clouds, networks and endpoints. XDR tools analyze the information and use it to detect threats and initiate response sequences and alerts.
The importance of information for effective XDR
According to Gartner, XDR technology requires diverse threat intelligence and defensive techniques in order to be truly effective. XDR solutions rely on information to detect threats. If this information is not diverse enough, many threats may pass through undetected.
Features of MITRE ATT&CK relevant for XDR
The framework provides the following features that support XDR:
- Expanded knowledge base – the MITRE framework can provide XDR solutions with the information needed to perform deeper investigation and threat detection, and apply the relevant prevention techniques.
- Improved playbooks – the framework offers incident response teams the information needed to create a progressive playbook that accounts for adversarial behaviors in an authoritative and standard way.
- A shared source of truth – the alignment of XDR with the MITRE ATT&CK framework creates a security operations center (SOC) workflow that enables analysts to conduct comprehensive impact assessments and determine how to mitigate and protect against certain types of attacks.
How can frameworks like MITRE ATT&CK benefit XDR solutions?
- Content alignment – Similar to Next-Gen SIEM, XDR solutions can provide “content”, including detection and response patterns, and align with the MITRE ATT&CK framework. For example, a solution can provide a threat response pattern that includes the attacker’s likely actions, mapped to response playbooks that can be instantly activated, either manually or automatically.
- Easier investigation – a key focus of XDR is to provide “everything in one place”, pulling together data from different sources to build an attack timeline. Using MITRE ATT&CK data, XDR can improve this process, identifying that events in the environment are part of a known attack campaign, and using data from the framework to add context to the attack scenario.
- Guided response – while in some cases XDR can directly provide an orchestrated response, in other cases it can guide human response. By using MITRE ATT&CK data, the XDR solution can not only identify and visualize the threat, but also suggest specific response actions that have proven effective against this threat.
How Exabeam Fusion and XDR Leverages the MITRE ATT&CK Framework
Exabeam Fusion SIEM and XDR include a set of pre-packaged use cases. These pre-packaged use cases include threat-specific content, pre-defined investigation checklists, and response playbooks tailored to each defined scenario. Exabeam in-house security experts mapped each use case scenario across the MITRE ATT&CK framework, including the specific MITRE tactics and techniques associated with every use case, providing more insight for the security analyst investigating potential threats in Exabeam. For example, the compromised credential use case maps to nine different MITRE techniques.
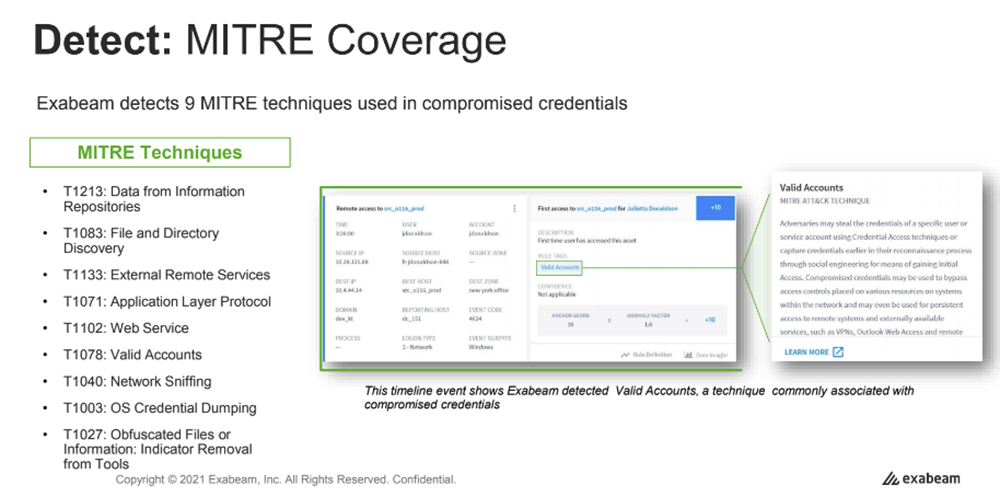
Exabeam Fusion includes these two products:
- Exabeam Fusion XDR: Market-leading behavioral analytics, alert triage, threat hunting, pre-built investigation playbooks, TDIR workflow automation, and integrations with hundreds of third-party security and productivity tools enable organizations to find complex threats that often go unnoticed across their diverse environment.
- Exabeam Fusion SIEM: All Fusion XDR features and capabilities plus centralized log storage, powerful search, and reporting to meet common regulation and compliance use cases.
No other SIEM or XDR provider delivers more out-of-the-box content in support of the framework. For a detailed mapping of Exabeam’s support of the MITRE ATT&CK Framework, please follow this link – Exaberam’s MITRE support is shown in shades of green – ATT&CK® Navigator
Learn more: Learn more about Exabeam Fusion SIEM






