Improve threat detection, enhance your ability to investigate, reduce incident response times and upgrade your cloud security
Security leaders are tasked with building world-class security programs capable of defending against both today’s threats and tomorrow’s attacks — all on a fixed budget.
Elastic’s SIEM (Elastic Security) offers powerful data centralization capabilities. It is built on the Elastic Stack to visualize, search and filter security data. ELK Stack or Elastic Stack is a combination of Elasticsearch, Logstash, and Kibana, which are open source tools that are the foundation of a log management system by Elastic:
- Elasticsearch is a distributed data store where data can be searched quickly, allowing for advanced queries that give developers opportunities to perform detailed analysis.
- Logstash is the data ingestion tool that sits in front of Elasticsearch which collects data from various sources. Logstash supports a wide range of data types and ingests data from a multitude of sources—like systems, web servers, firewalls, access, databases, and applications—and it can collect the data all at once.
- Kibana is a visualization layer that works on top of Elasticsearch.
Elastic’s SIEM provides a platform to centralize all log data and annotate relevant events to help analysts to search and alert on threats. Elastic’s SIEM provides a library of visualizations and dashboards in Kibana, and the SIEM app provides key metrics regarding host and network-related security events.
However, the platform requires extensive customization and maintenance to be usable. Customers who deploy Elastic’s SIEM, must be prepared to do some groundwork in terms of identifying all the necessary log sources, ingesting them into the system, and setting up, tuning, and maintaining all of the required correlation rules. Also, analysts often require knowledge of what data to query and filter. And exhaustive analyst cycles are needed to perform triage and investigation directly in Elastic’s SIEM.
Exabeam overcomes these challenges by adding intelligence to Elastic’s SIEM. With the addition of advanced analytics, security teams can make the most out of their Elastic SIEM investment. Exabeam accomplishes this by deploying alongside Elastic’s SIEM without needing to make architectural changes to their Elastic deployment. Exabeam ingests data from Elastic’s SIEM to provide organizations with:
- Improved threat detection
- An enhanced ability to investigate
- Visibility into activity in cloud applications, and
- Faster incident response
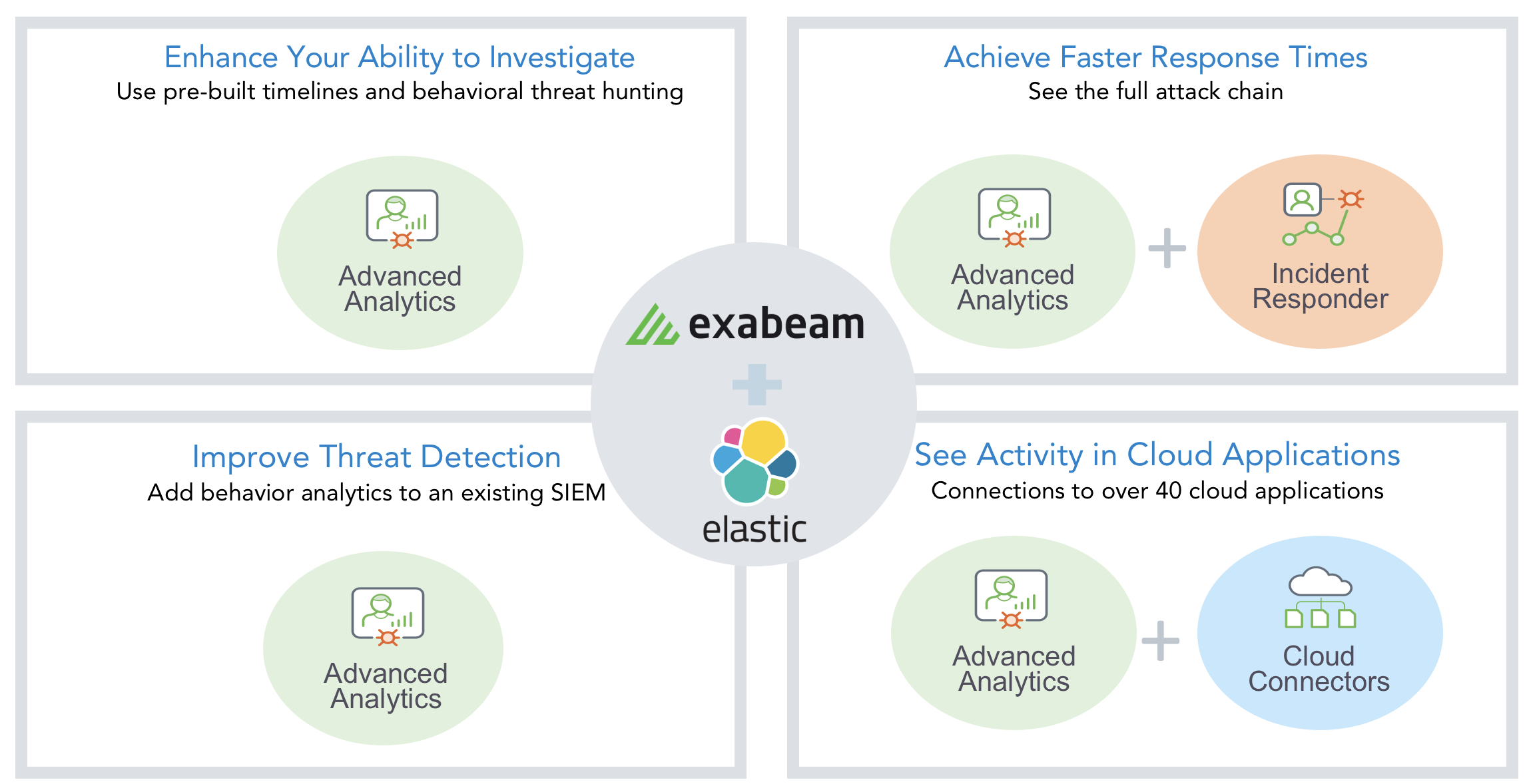
Figure 1: Benefits of adding intelligence to Elastic’s SIEM with Exabeam
Improve threat detection
Elastic’s SIEM threat detection relies on the use of correlation rules to help analysts identify any known indicators of compromise (IoCs). IoCs are artifacts observed on your network that indicate an intrusion— or predefined conditions which may be indicative of threats. Many SOC analysts use IoCs for alerting and guidance. However, they do suffer from a major limitation, they are only alerted on known threat indicators, not unknown threats.
Furthermore, identifying an IoC doesn’t allow an analyst to see the whole picture or to understand the intent of the attacker. For example, if an IoC pertains to a potentially rogue IP, security analysts need to know:
- Who is behind the IP?
- Is the IP still malicious?
- Does it represent a threat targeting my organization?
- Are there other attack vectors at play?
- And various other questions…
Acquiring context around the potentially malicious artifact is crucial for effective security management. In Elastic’s SIEM, it’s also a lot of work. To address this, analysts try to enrich IoCs with available tools – hybrid analysis, threat intel like VirusTotal – to achieve reliable correlation. But, this often results with inconclusive results and analysts have to dig up and correlate all the events in order to complete their investigation
In contrast, Exabeam Advanced Analytics provides advanced threat detection with user and entity behavior analytics (UEBA). Exabeam enhances your Elastic deployment by prioritizing alerts and by enriching data so that your analysts can be more efficient in protecting your network. All relevant events are automatically grouped in a chronological order with risk scores assigned to anomalous events dynamically. The highest risk users and assets are prioritized to make it easy for investigations.
Exabeam enhances security logs including Windows servers, VPNs, firewalls, endpoint devices, DNS servers, etc. Logs tell you what users and entities are doing. The additional context informs you who the users and entities are– it gives them their identity. Exabeam’s patented technology is able to map the IP-to-host-to-user. For example, if you know the source IP address of a user’s workstation from the logs, and the user then VPNs from a different location, you will be able to map the IP address of the user to the hostname on record. Exabeam is also able to identify user peer groups, service accounts, and all IDs and emails related to a user.
One of the key pieces that help in detecting threats is behavior models. Behavior models detect any deviation from normal behavior. Risk scores are then assigned to events depending on the severity of the risk, deviation, and other factors. Here is one example (see Figure 2) that models the behavior of all the assets the user is able to access remotely. This model detected anomalous access to an asset, atl-addc-002.
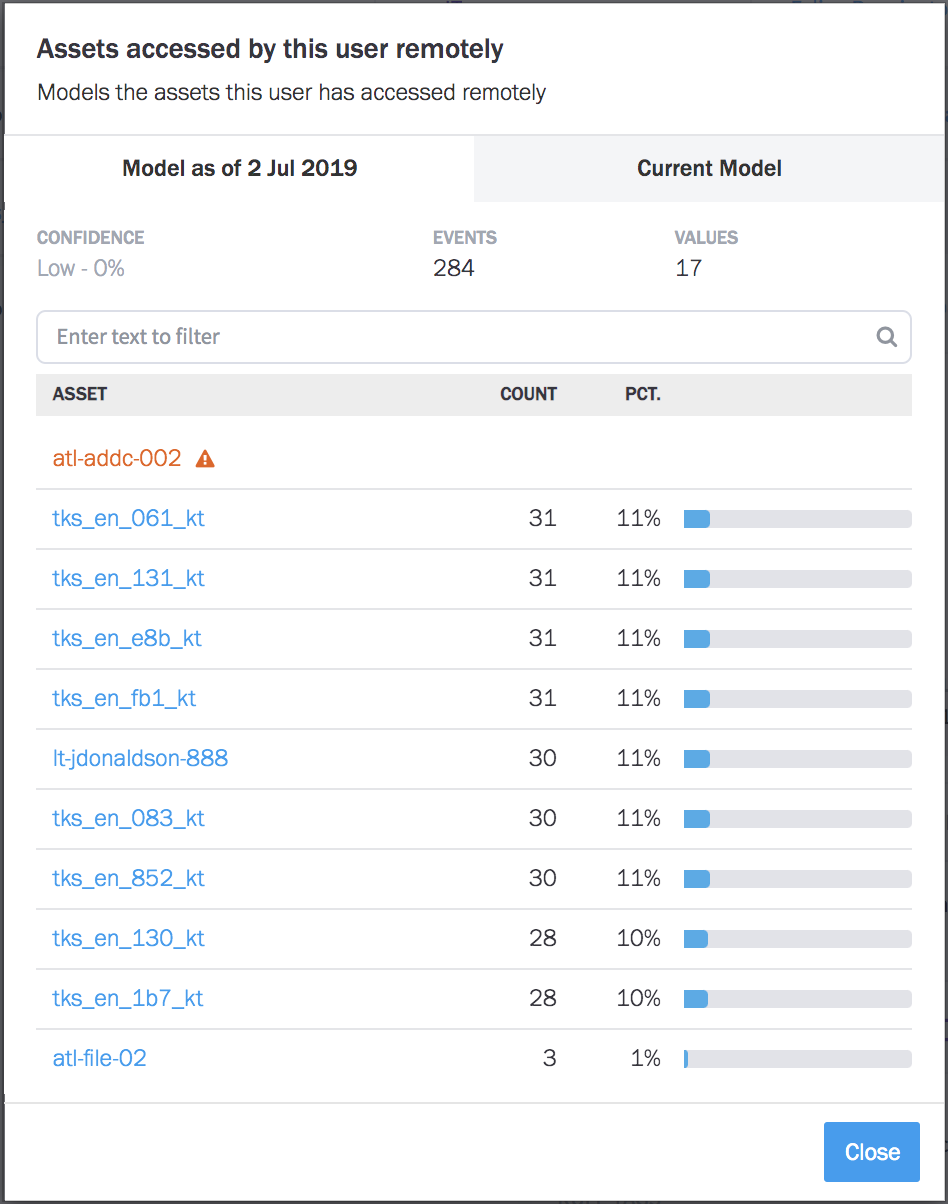
Figure 2: A behavior model showing all assets accessed by the user remotely.
Exabeam puts all behavior and other user events in chronological order in Exabeam Smart Timelines to make it easy to see the full attack chain. Of all the security solutions available to the SOC, only Smart Timelines (see Figure 3) contain both normal and abnormal behavior. Analysts can easily follow attacks that move laterally. These timelines are automatically presented in order of highest risk to help focus analyst cycles where they matter most.
Smart Timelines are also a big time saver. A study by the Exabeam research team found that each machine-built Smart Timeline can replace as many as 700 manual queries which would otherwise be required to obtain similar visibility.
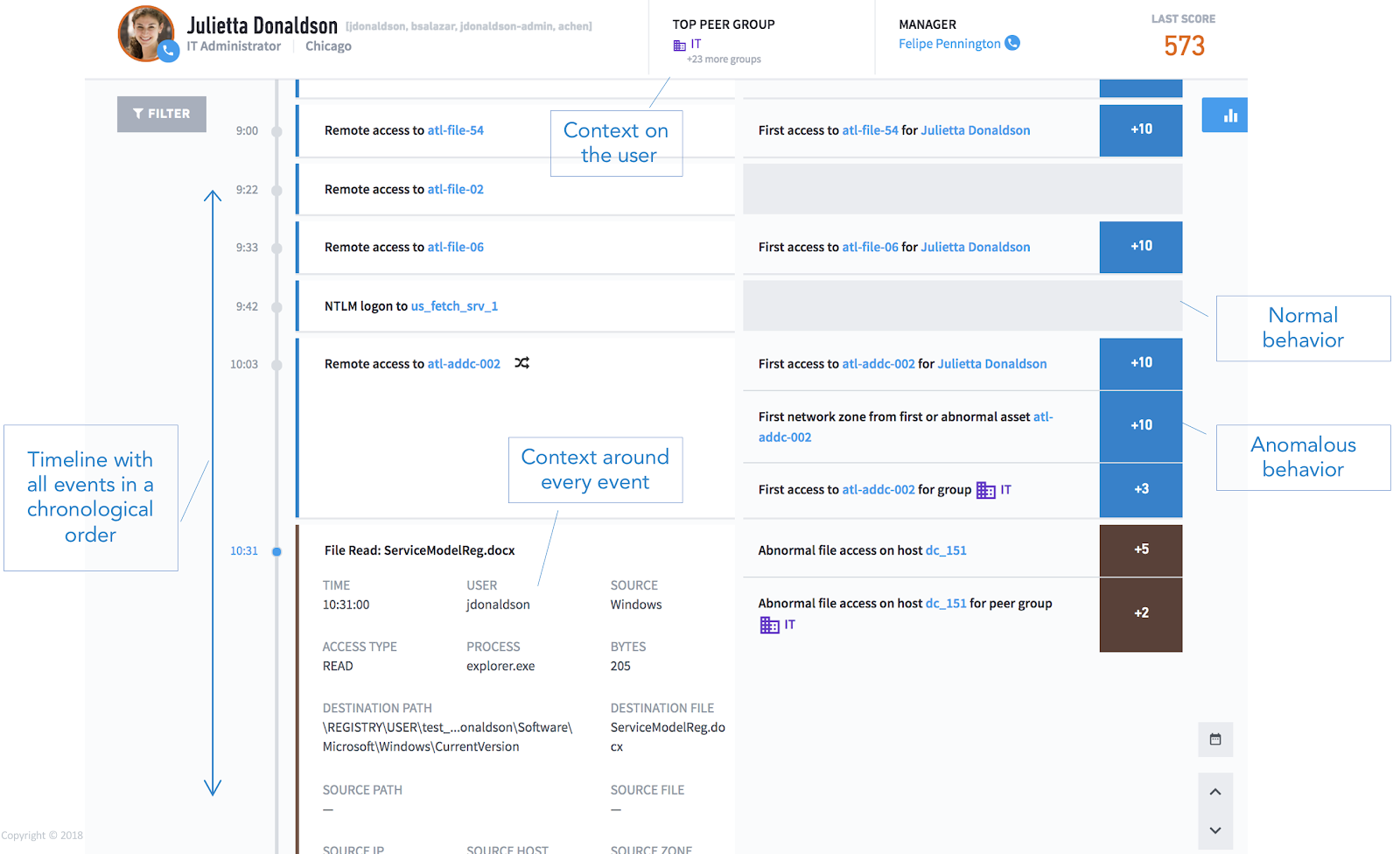
Figure 3: A sample Smart Timeline showing all normal and anomalous events along with the context collected for the user and assets.
Enhance your ability to investigate
Elastic’s SIEM offers KQL (Kibana Query Language) to retrieve data. KQL queries help to get relevant events as long as analysts know what to query. But, success depends on analysts’ skill level to query and hunt for any suspicious indicator or behavior. They must also stitch together all relevant events to investigate if there is a threat to an organization. This takes a lot of effort.
Exabeam automates a lot of that manual work. Exabeam Advanced Analytics can ingest data from Elastic either by using Elastic query or some customers leverage Elastic Logstash to feed data directly into Exabeam. Once ingested, Exabeam adds context and constructs a Smart Timeline to allow analysts to rapidly analyze data from myriad data sources to find anomalous and high risky behavior.
Smart Timelines eliminate the need for analysts to build their own incident timelines, and reduce their need to “query and pivot” between IT and security applications to collect event details. Because the timelines are automatically created for all users and devices, analysts can review the activities of a user or device anytime, whether there is an identified incident or not. Since the dots have already been connected, threat hunting becomes very easy for analysts.
Another important threat hunting tool is Exabeam Threat Hunter. Threat Hunter includes a simple point-and-click interface to let your analysts proactively search for incoming threats without performing any complex queries. Threat Hunter allows analysts to easily search for abnormal behaviors in their environment, which may be indicative of a threat. Unlike Elastic’s SIEM, which returns event logs as results, Threat Hunter returns entire Smart Timelines to help analysts to speed up their investigation efforts. Analysts are able to string together many conditions (see Figure 4) with drop-down menus that are pre-populated with reasons for risk, activity types, usernames, assets, and MITRE ATT&CK tactics and techniques to make it easy for analysts to hunt for relevant events.
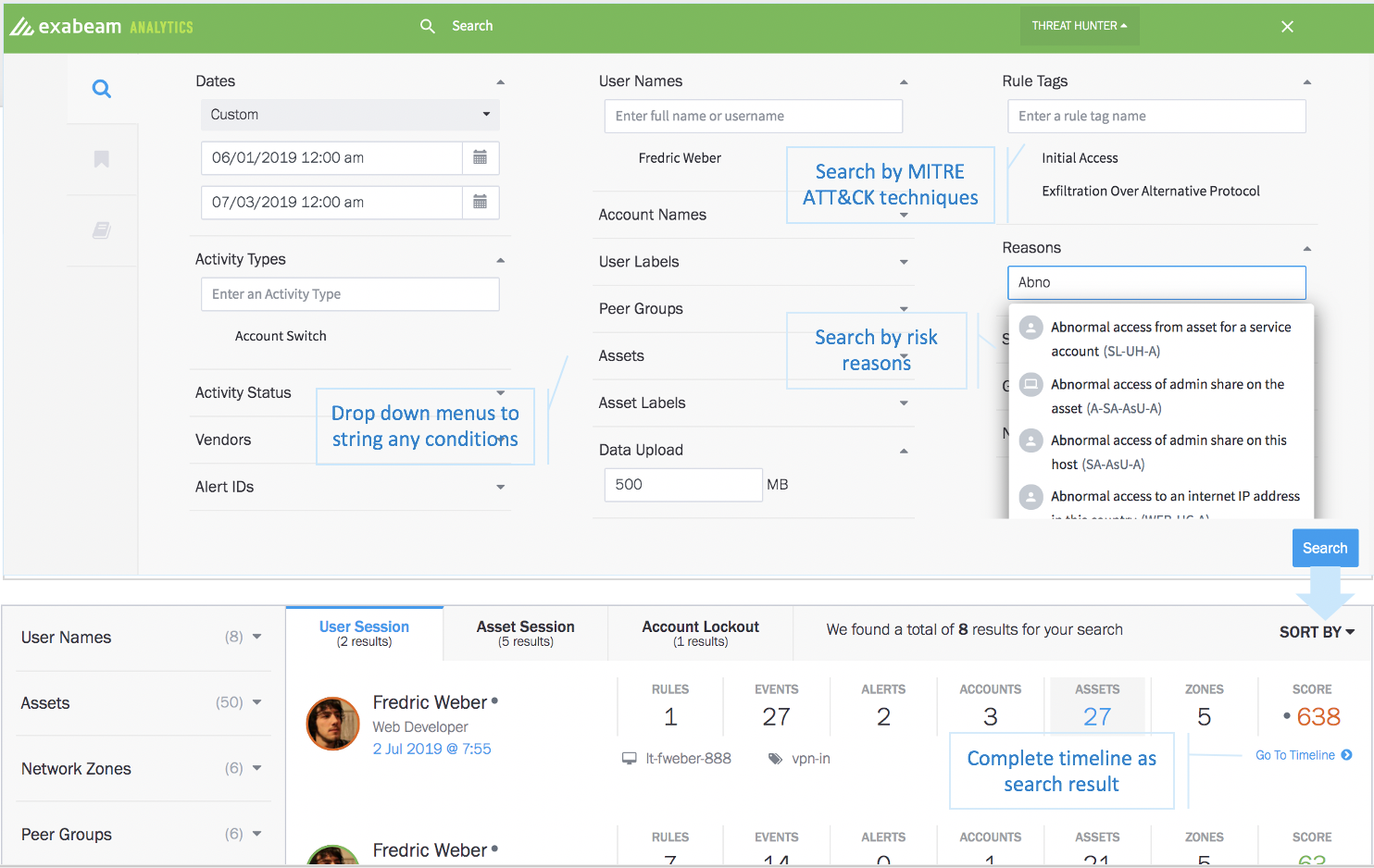
Figure 4: Exabeam Threat Hunter – analysts can string together any conditions using drop-down menus to hunt for anomalous events.
Gain visibility into activity in cloud applications
Elastic’s SIEM provides cloud monitoring by sourcing logs from various cloud applications and cloud infrastructure services like Google, Azure and AWS. But analysts still need to enable detection rules and enrich the data in order to effectively detect and investigate threats, as mentioned above.
Exabeam provides a more elegant solution. Exabeam extends security to the cloud via Exabeam Cloud Connectors to help organizations monitor activity in cloud services and cloud infrastructure. Cloud Connectors are pre-built connectors that enable security teams to easily collect logs from over 40 popular cloud services such as AWS, GitHub, Google, Microsoft Office 365, Salesforce and others. They allow enterprises to detect threats using behavior analytics in their cloud applications. They also extend any compliance-based security requirements to the cloud. As shown in Figure 5, all the activities that the user takes in cloud applications are monitored and the events are shown in a timeline. Analysts get the full context of the story, including both cloud and on-premises application activities.
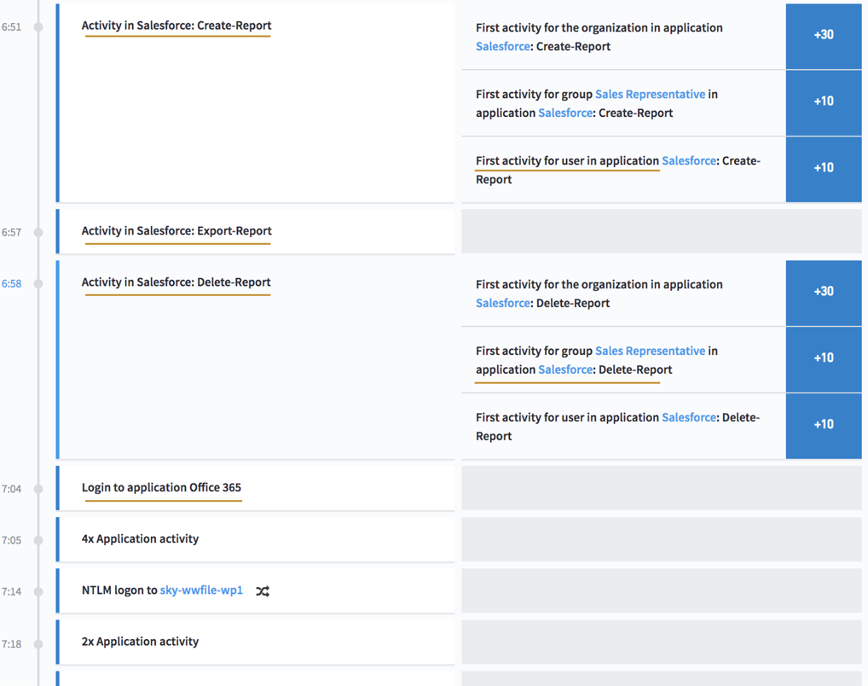
Figure 5: A user timeline showing various Salesforce and Office365 activities
All the events from cloud applications are automatically enriched with out-of-the-box behavior models and context, and are shown in timelines along with other activities. In addition, Cloud Connectors automatically adapt to any API changes, so you can rest assured that the connector is always operating as intended.
Achieve faster response times
Elastic’s SIEM does not include security orchestration, automation and response (SOAR) capabilities. However, third party SOAR solutions can be added directly via APIs.
In contrast to third-party integration for SOAR solutions — Exabeam Incident Responder is natively integrated with Exabeam Advanced Analytics. You can’t respond to attacks you don’t see. The direct integration with Advanced Analytics ensures analysts have full visibility of the attack, no matter how complex or sprawling their nature, and that the automated response can be effective.
Additional administrative advantages
In addition to the above operational advantages Exabeam provides by augmenting Elastic SIEM or ELK Stack, Exabeam SaaS and MSSP deployment options and its modular architecture reduce administrative overhead.
- Exabeam Cloud Platform – expedites the provisioning and consumption of new applications, tools, threat intelligence and use case content like parsers, rules and models.
- Deployment options – allow you to choose from options including SaaS maintained and supported by Exabeam or your own service provider.
- Automated Content Updates – distribute new use case content and content packs via the Exabeam Cloud Platform. New content packs include detection rules, behavioral models, threat intel feed and parsers from new log sources. Customers can sign up to get these critical content updates automatically, so they have the latest content to be protected from threats.
In Conclusion
Each business environment is different. Contact us to see how you can add intelligence to your Elastic SIEM deployment with Exabeam. Visit Exabeam.com to request a demo.
For more information refer to the following articles.
Comparing DIY ELK vs Exabeam SIEM
Benefits of Detection and Investigation with Smart Timelines
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













