Actually, your Zoom administrator can deactivate that notification, so chances are your meeting is being recorded and you don’t even know.
Recently the inevitable media spotlight was shone on Zoom and specifically the security risks attributed to their platform. The media’s focus took a predictable path of overhyping security concerns, in particular around Zoombombing, and came off the back of significant and sustained demand from a global workforce urgently needing access to web conferencing solutions to support #WFH. To Zoom’s credit they responded to the concerns, but scepticism remained.
Around the same time, the team here at Exabeam received requests from our customers to support the collection of logs from Zoom; customers needed their security teams to track user and admin activity and automatically detect risky behaviors before those threats caused harm to their business.
As a result, support for Zoom was added to the Exabeam Cloud Connector solution earlier this year.
In this post we’re going to focus on areas of risk as they relate to Zoom and how organizations can address the specific example of an insider threat or malicious actor snooping on Zoom meetings.
Let’s start with the core areas of concern raised by our customers:
- Eavesdropping
- Disruption
- Account (mis)use
- Administrator account (mis)use
1. Eavesdropping
One obvious hazard is loss or theft of information via web conferencing. While Zoom has made it easier to protect meetings with features including: requiring passwords, only allowing accounts from within a domain (that is an active directory domain), a waiting room, and preventing participants from joining before the host, not everyone is aware of these features, knows how to activate them or makes use of them. And as you’ll see there are other ways for bad actors to eavesdrop on a meeting.
2. Disruption
In 2020 this has been coined as Zoombombing, the “unwanted, disruptive intrusion, generally by Internet trolls and hackers, into a video conference call.” Similar to managing the risk of eavesdropping, organizations can help alleviate this concern by leveraging the security controls available within the Zoom application — including setting a password for your meeting, using the waiting room functionality, enabling screen sharing for host only and disabling the ability for attendees to make annotations on the screen. Of course, if you are going to promote your event in public forums like Facebook then consider using the Webinar functionality of Zoom for further control.
3. Account (mis)use
If your corporate policy prevents employees from using video conferencing for personal use, then you’ll want to be looking at the log files to determine if that is happening. However the bigger risk here is compromised credentials which in Zoom could lead to a range of outcomes from unauthorized outsiders covertly joining Zoom meetings to an attacker using valid credentials to defeat some of the defenses discussed in points 1 and 2.
4. Administrative account (mis)use
Administrative accounts hold the keys to the castle. As part of their privileges, a Zoom administrator can control various aspects including when a meeting is recorded and whether an announcement is played before an ad hoc recording is started. Being able to track those actions by an admin and determine whether it is normal behavior or a signal that there is an insider threat or credentials have been compromised is critical.
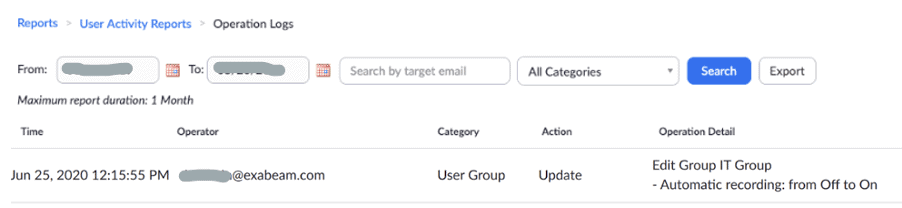
Figure 1: Zoom Operation Logs data, showing the actions taken by the administrator, as it appears in the Zoom application. Cloud Connector for Zoom presents this data in your SIEM or UEBA for investigation, see Figure 2 below.
Could this happen to you?
Of the four areas of risk highlighted, the potential for data exfiltration through eavesdropping carries the greatest risk. A rogue admin or external actor who has compromised the admin’s credentials could very easily identify a meeting of high-level importance, disable the notification that the meeting is being recorded and activate the recording, which they can then access once the meeting has concluded.
For an attacker, gaining access to privileged credentials is worryingly easy, thanks to employees’ willingness to click on links (that in turn lead to a drive-by download), unknowingly handing over their user name and password in what was a simple spear phishing attack or by just using common passwords that expose your organization to password-spraying attacks.
Once inside your network, spotting attackers with valid credentials is notoriously difficult. They look just like regular users and are only differentiated by their objective. The attacker wants to find out the limits of the victim’s access rights. If the user happens to have access to the desired systems and applications, the attacker will get what he or she wants, which can be anything from email attachments, network diagrams, source code or access to Zoom recordings. If the user doesn’t have the desired level of access, the attacker will jump from system to system until they find the right victim.
Even if you start monitoring the log data from Zoom tomorrow would a simple change in recording settings represent a threat or would it lead your team down the path of yet another false positive? This is where a UEBA solution pays dividends.
Behavior is key when it comes to accurate, early detection
To quickly and accurately identify actions within Zoom or in any other cloud application for that matter which puts the organization at risk, security teams need to be able to ingest the log files from their cloud applications into a UEBA solution.
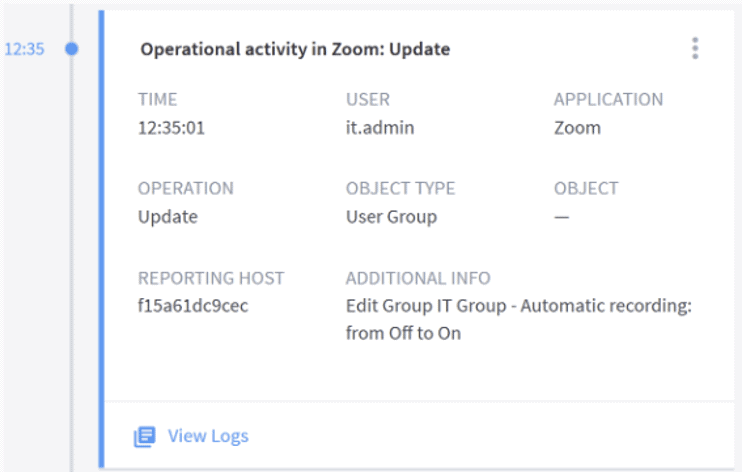
Figure 2: Changes made to Zoom settings by an administrator form part of the investigation timeline in Exabeam Advanced Analytics.
Exabeam Advanced Analytics is one such solution, it uses behavioral analytics to establish a baseline level of ‘normal’ user activity including their interactions with various entities, it then monitors the employee for deviations from their baseline as well as that of their peers, automatically flagging risky behavior in near real time. Finally, all the user’s activities for that day’s session, including normal and risky behaviors, is presented back in a timeline to facilitate your team’s investigations.
If you want to learn more about Exabeam Cloud Connectors check out the datasheet here or to see Exabeam Advanced Analytics in action, watch this video.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













