Ponemon Study Reports 95% of Exabeam SIEM Users Rank It as Highly Effective for Security

The most important reason for using a SIEM is to improve the effectiveness of an organization’s cybersecurity program. SIEM technology is the heartbeat for processes to identify and manage threats. How users rank the effectiveness of their SIEM is the topic of this last of three posts describing findings of a recent Ponemon study commissioned by Exabeam. Effectiveness is an urgent issue. The survey reports over half of all organizations using SIEMs are experiencing attacks more than 1,000 times a week. About a third say they experience over 5,000 daily attacks. By a variety of measures, 85% to 95% of Exabeam users rank their SIEM as a highly effective solution for detecting, investigating and responding to those incidents. Here are some key findings:
Effectiveness in detecting and investigating cyberattacks – 95%
A core job of SIEM analysts is to detect and investigate cyberattacks. Analysts depend on the SIEM to transform a multitude of connected disparate security data into useful information. Effectiveness suffers when a SIEM presents unimportant or irrelevant issues that rob analysts of valuable time and dilute their efforts for cyber defense. Ponemon asked respondents to rate the effectiveness of their SIEM in detecting and investigating cyberattacks on a scale of 1 (not effective) to 10 (highly effective). Respondents using Exabeam ranked effectiveness at 95%. By contrast, just 59% ranked other SIEM solutions as highly effective.
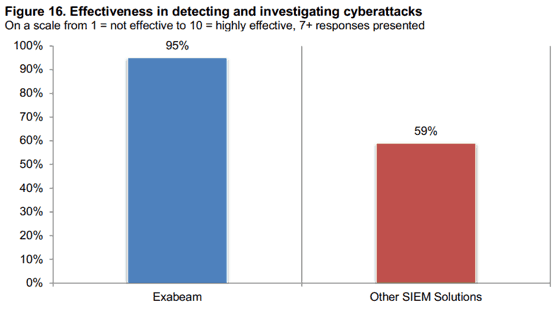
Figure 16: Ninety-five percent of Exabeam customers say their SIEM is more effective in detecting and investigating cyberattacks.
Enabling feature: enriched user and asset context. As a modern SIEM, Exabeam uses data science to provide context to security and operational data. It enriches these data to clarify details that are automatically discovered, assigned to, and presented with their associated objects. Machine learning uses this context for more accurate detection and investigation to increase the odds of repelling attacks and preventing breaches. Examples of Exabeam enrichment and context include:
- Dynamic peer grouping
- IP association
- Asset ownership
- User type
- Machine type
- Service account identification
-
Personal email address identification
Effectiveness in Prioritizing Alerts that Pose Significant Cyber Risk – 90%
Alert fatigue can kill a SIEM team’s ability to effectively execute responsibilities for digital security. It occurs when a constant blizzard of alerts overwhelms a team’s practical ability to rapidly know whether each individual alert matters – or not. A large organization may experience hundreds of thousands or millions of daily system alerts. By providing incident prioritization, a SIEM can improve security operations exponentially by automatically telling analysts the precise order of severity for addressing issues. Ponemon asked users to rank their SIEM’s effectiveness in prioritizing alerts. Almost all Exabeam users (90%) say their SIEM is highly effective in prioritizing alerts that pose a significant security risk. Just 51% of users of other SIEM solutions gave the same ranking. That’s a margin of nearly two-to-one favoring Exabeam’s effectiveness. As a result of effective prioritization, Exabeam users report they are able to investigate a higher percentage of daily alerts (83%). Users of other SIEM solutions are only able to investigate (45%).

Figure 17: Ninety percent of Exabeam customers say Exabeam is more effective in prioritizing alerts that pose significant threats.
Enabling Feature: Incident Prioritization. Exabeam provides user and entity behavior analytics (UEBA) that automatically prioritize incidents for more effective action by the security team. To enable this capability, Exabeam ingests data from all sources and analyzes it all together. UEBA provides behavioral analysis to identify abnormal behavior as a priority focus for analysts. Alerts associated with high-risk sessions are prioritized according to their risk scores. Exabeam machine learning and data science provide further gains in security intelligence, such as with Bayesian scoring.
Effectiveness in minimizing false positives – 85%
A major contributor to ineffective security efforts is when analysts must waste time responding to and clearing false positive alerts. The infamous false positive occurs when a SIEM alert incorrectly states a particular security condition or attribute is present. This is not a prevalent issue for Exabeam users, as 85% ranked it as highly effective in minimizing false positives when using SIEM to detect and investigate cyberattacks. Just 54% of users of other SIEM solutions assigned a similar ranking. As a result, Exabeam users reported just 10% of alerts are false positive, while users of other SIEM solutions said 33% of alerts are false positive.
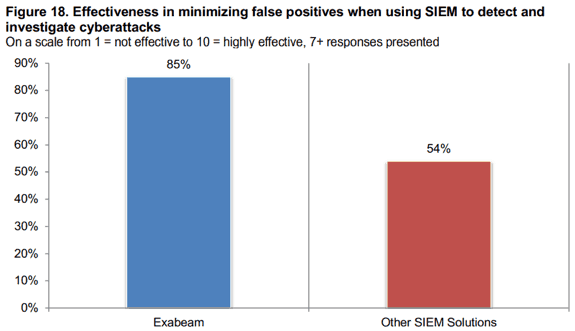
Figure 18: Eighty-five percent of Exabeam customers say their SIEM is effective in minimizing false positives.
Enabling feature: easily collect and manage data from anywhere. The key to minimizing false positives is having adequate data for the SIEM’s analytics. Exabeam provides a 360 view of events underpinned by a flexible centralized logging infrastructure capable of handling a myriad of data types and sources. It provides prebuilt integrations with more than 200 data sources including public, private and hybrid cloud services; on-premises log sources for security controls, databases, apps, and so forth; and network telemetry data such as flows and packets. Centralized remote-collector management ensures the intake of all essential data to maximize the accuracy of analytics and minimize false positives.
Value of out-of-box correlation rules and detection models – 89%
By applying correlation rules and detection models, a SIEM is supposed to help analysts understand if alerts are triggered by normal or anomalous behavior. Its ability to perform this function depends on the effectiveness of solution analytics. According to the Ponemon survey, Exabeam users ranked the value of out-of-box detection models at 89% and out-of-box correlation rules at 86%. Users of other SIEM solutions provided value rankings of just 55% and 61%, respectively.

Figure 23: Over 80% of Exabeam customers say their out-of-box correlation rules and detection models are valuable.
Enabling feature: behavioral baselining. With UEBA, Exabeam supplements correlation rules with a modern approach to threat detection using behavioral baselining. The idea is to detect threats by understanding how machines and humans normally behave; it then finds risky and anomalous activity that deviates from that baseline. The application of behavioral baselining incorporates three foundational elements of data science: machine learning, statistical analysis and behavioral modeling. Exabeam’s implementation dramatically improves the out-of-box value of its correlation rules, and detection models.
Conclusion
As the attack flow persists and grows for all organizations, one of the most important decisions for improving cybersecurity is the choice of a SIEM, a critical element for detecting, investigating and remediating cyberattacks. Through several measures of effectiveness, users in the Ponemon survey have overwhelmingly ranked Exabeam as a highly effective solution for identifying and managing threats compared to other SIEM solutions. I invite you to read the full report, Exabeam SIEM Productivity Report to learn more on what users are saying about how Exabeam is raising their organizations’ effectiveness with security.
Additional resources
Ponemon Study Reveals Analysts Tasks Take 50% Less Time When Using Exabeam
Ponemon Study Finds 90% of Users Get Lower Costs and More Value with Exabeam SIEM
Attend our webinar on Tuesday, October 22: How to Increase SOC Analyst Productivity and Security Effectiveness
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












