Survey Finds 35% of Security Professionals Say the Blue Team Rarely Catches the Red Team

As cyberattacks become more advanced and frequent, organizations are preparing their teams for sophisticated adversaries who can find gaps in existing security programs. One approach is to conduct red team/blue team exercises. Red teams can be internal teams or pen testers which are external groups brought in to emulate cybercriminals’ behaviors and tactics to gauge the effectiveness of the company’s current security technologies. Blue teams comprise the organization’s internal security personnel whose goal is to stop these simulated attacks. To give the company the most realistic picture of its defensive capabilities, the blue team is given no information on when the attack will occur and must respond without preparation.
A new study from Exabeam reports that the majority of organizations see significant value in red/blue team testing — and are using lessons learned from the exercises to strengthen their cybersecurity programs. The survey, conducted at Black Hat USA 2019, polled 276 IT security professionals and found that 74% have seen their companies increase investment in security infrastructure as a result of red and blue team testing, with 18% calling the budget changes significant.
Red team pentesting exercises are conducted regularly
When asked if their organization conducts red team exercises, 72% of respondents said their organizations did. Of those, 23% performed exercises monthly, 17% quarterly, 17% annually, and 15% bi-annually.
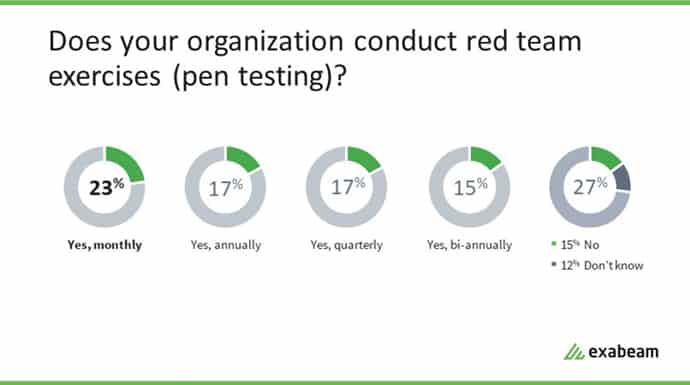
Figure 1: Seventy-two percent of respondents surveyed said their organizations conducted red team exercises.
Blue team defensive capabilities
On the flip side, 60% of respondents surveyed said their organizations conduct blue team exercises, with 24% performing them monthly, 12% quarterly, 11% bi-annually and 13% annually.
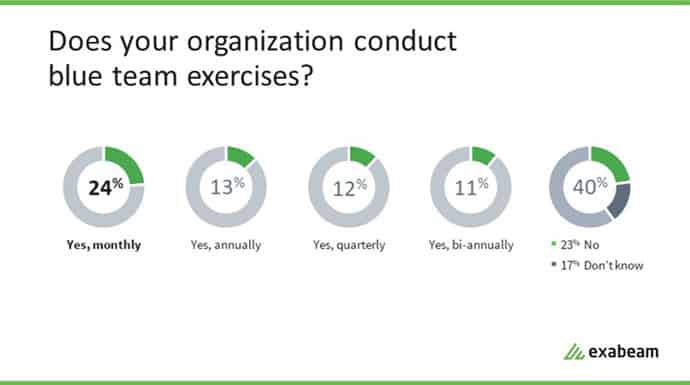
Figure 2: Sixty-percent of respondents said their companies conduct blue team exercises indicating a growing commitment to fortifying their security posture.
Do the security exercises work?
Of those surveyed, 68% of respondents believe that red team testing is more effective than blue team testing.

Figure 3: Sixty-eight percent of security professionals find red team exercises more effective than blue team testing.
When asked if the blue team was successful at catching the red team only 2% of those surveyed said they always caught them. Thirty-five percent of respondents claimed that the blue team never or rarely catches the red team, while 62% said they caught the red team occasionally or often.
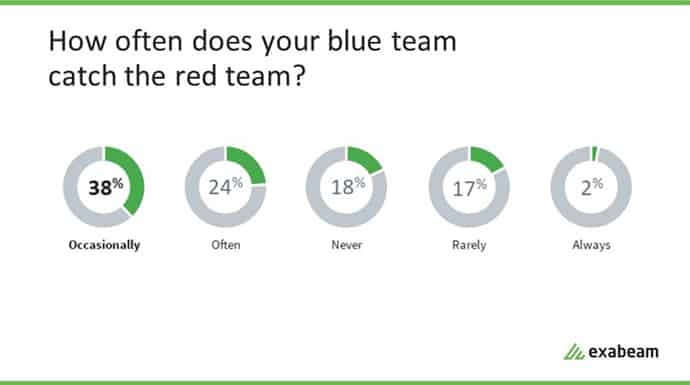
Figure 4: Thirty-five percent of respondents claimed that the blue team never or rarely catches the red team, while 62% said they caught the red team occasionally or often.
Seventy-four percent of IT security professionals surveyed have seen their companies increase security infrastructure investment as a result of red and blue team testing, with 18% calling the budget changes significant.
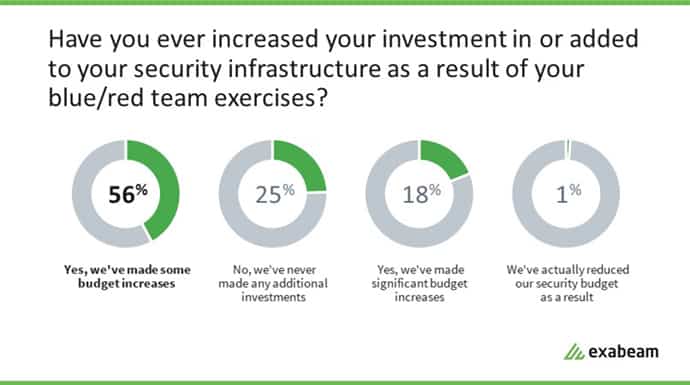
Figure 5: Seventy-four percent of security professionals surveyed have seen their companies increase security infrastructure investment as a result of red and blue team testing.
Improving defensive skills
According to the survey, top skills the blue teams needed to work on as a result of their exercises were communication and teamwork (27%), knowledge of the attacks and tactics (23%), and threat detection (20%). Incident response time (17%) and persistence (8%) were other areas the internal security teams said they needed to work on.
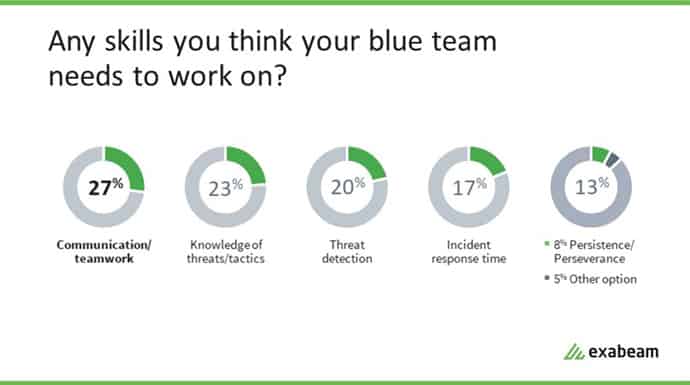
Figure 6: The survey identified communication and teamwork as the top skill blue teams need to work on, followed by knowledge of the attacks and tactics, threat detection, incident response time and persistence.
Regular red team/blue team testing can help companies harden their security infrastructure and train internal teams to handle attacks. The study also demonstrates that in addition to having technical knowledge interpersonal skills are important to foster more cohesive teams and better cooperation when an urgent alert arises.
How to detect and respond to threats
Proactive threat hunting is one method organizations can use to get in front of threats. Security teams can catch the adversary early in the process when they are introducing a threat by watching for telltale attack techniques. It starts with detecting threats before they are exploited as attacks, malware on an endpoint, for example.
User and entity behavior analytics (UEBA) is an emerging category of security solutions that uses analytics technology, including machine learning and deep learning, to discover abnormal and risky behavior by users, machines and other entities on your corporate network. Using behavior to track normal and anomalous behaviors to detect threats can improve your security posture.
Because they do not conform to predefined correlation rules or attack patterns or span multiple organizational systems and data sources, UEBA solutions can detect security incidents that traditional tools do not see.
To find out more about the most prevalent UEBA security use cases read our post, Top 10 UEBA Security Use Cases: Compromised User Credentials, Executive Assets Monitoring, Data Exfiltration Detection.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!










