Exabeam Security Analytics
Automated threat detection powered by user and entity behavior analytics (UEBA) with correlation and threat intelligence.
Transform your legacy SIEM or data lake with UEBA
Exabeam Security Analytics is the only UEBA product in the market that can run on top of an existing SIEM or data lake to upgrade an organization’s defenses and contend with sophisticated and credential-based attacks. Exabeam Security Analytics ingests, parses, and normalizes data using a common information model (CIM) focused on security as well as data enrichment, with threat intelligence and other context, to help create security events. Exabeam Security Analytics UEBA capabilities baseline normal behavior for users and devices and highlight anomalies, assigning a risk score to each notable event.
Flexible integration to augment your security investments
Exabeam Security Analytics runs on top of a legacy SIEM or data lake to upgrade an organization’s defenses and contend with sophisticated and credential-based attacks. This enhances your existing investments and data repository.
- 200+ on-premises connectors
- 60+ cloud-delivered security product connectors
- 10+ SaaS productivity product connectors
- 20+ cloud infrastructure product connectors
- 9,500+ pre-built parsers
Upgrade your security team confidence, speed, and performance while getting more out of your existing cloud and on-premises infrastructure, as you unify them into a single control plane for monitoring and operations.


Understand normal behavior
To understand normal behavior and detect anomalies, even as normal keeps changing, all user and device activities get baselined and assigned a risk score. 1,800 rules, including cloud infrastructure security, and over 750 behavioral model histograms power Smart Timelines™ to convey the complete history of an incident, showing complete event flows, like lateral movement and credential use, visualizing the risk score associated with each event. The results: find and stop the threats others tools miss, and uplevel your security team speed and performance to stay ahead of your adversaries.
Detect and prioritize anomalies
Exabeam UEBA capabilities include over 1,800 rules and over 750 behavioral model histograms to find advanced threats, including credential-based attacks, insider threats, and ransomware activity. Smart Timelines™ visualize the complete history of an incident and highlight the risk associated with each event. Anomaly Search in Exabeam Security Analytics provides a simplified search experience with fast query and instant results. A single interface allows analysts and threat hunters to search for Exabeam-triggered events across their data repository, pairing behavior-based TTP detection with known IoCs to enhance threat hunting.

How it works
Exabeam Security Analytics transforms legacy capabilities to take on complex threats like credential-based attacks. Exabeam Security Analytics includes prescriptive use case content that deliver coverage on specific threat types (e.g. ransomware, phishing, malware, compromised credentials). To provide a better understanding of your security posture, the Security Analytics Outcomes Navigator analyzes your use case coverage and offers data source and parsing configuration changes to close any gaps.
behavioral models
Automatically baseline normal behavior of users and devices to detect, prioritize, and respond to anomalies based on risk.
rules
Including cloud infrastructure security, to detect, prioritize, and respond to anomalies based on risk.
MITRE ATT&CK® categories
Coverage for all ATT&CK categories, including 199 techniques and 379 sub-techniques.
Exabeam Security Analytics features
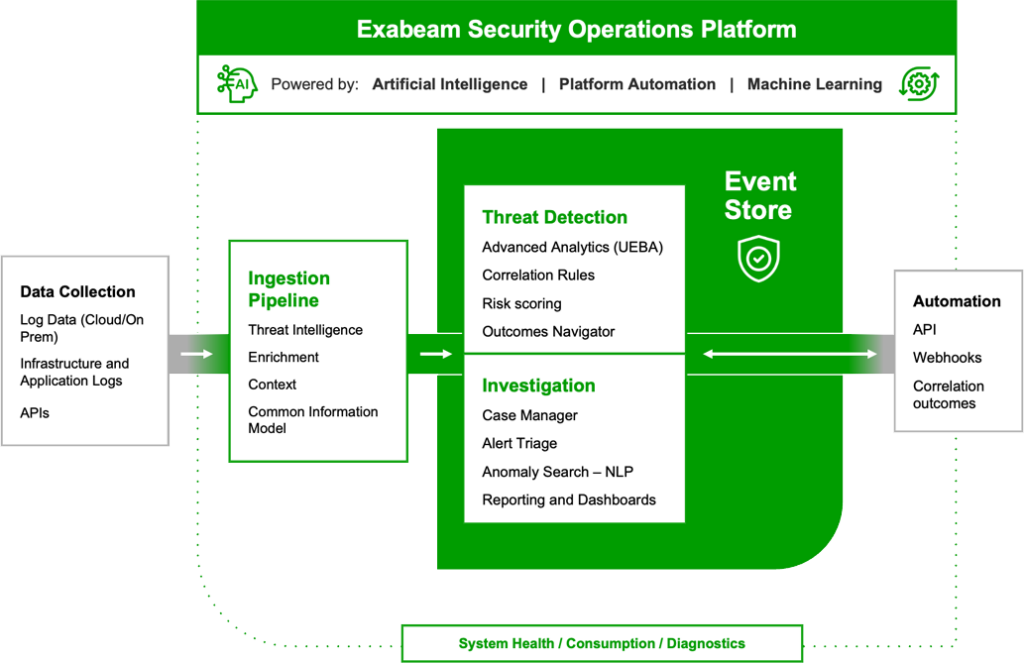
Exabeam Security Analytics provides UEBA-driven threat detection, investigation, and case management, across events from multiple security stacks and data repositories.
Collectors
Collect data from on-premises or cloud data sources from 22 product categories, 292 different vendors, and 549 different products with over 9,500 pre-built log parsers.
Log Stream
Rapid log ingestion processing over 2M events per second using a new CIM and parsing at ingest. A central console enables you to visualize, create, deploy, and monitor parsers within a unified ingestion pipeline for all Exabeam functions.
Common Information Model (CIM)
Exabeam built a CIM to transform raw logs into normalized, security events that are faster and easier to parse, store, and report on.
Anomaly Search
A simplified search experience with faster natural-language query and instant results over petabyte scale and/or years of data.
Reporting and Dashboards
Print, export, or view dashboard data with pre-built compliance reports, customized reports, and dashboards with 14 different chart types.
Correlation Rules
Write, test, publish, and monitor custom correlation rules, including defining higher criticality via Threat Intelligence Service-sourced activity.
Pre-built Correlation Rules
Over 190 pre-built correlation rules for detections against the most common threat types such as malware and compromised credentials.
Outcomes Navigator
Outcomes Navigator maps the feeds that come into the platform against the most common security use cases and suggests ways to improve coverage.
Service Health and Consumption
Visualize your service health for every Exabeam service and application, as well as data consumption, while monitoring your connections and sources.
Threat Intelligence Service
Available at no additional cost and refreshed every 24 hours, the Exabeam Threat Intelligence Service ingests commercial and open source feeds, then aggregates, scrubs, and ranks them, using machine learning algorithms to produce a highly accurate stream of IoCs.
Advanced Analytics
UEBA with more than 1,800 rules, including cloud infrastructure security, and 750-plus behavioral models to automatically baseline normal behavior of users and devices with histograms to detect, prioritize, and respond to anomalies based on risk.
Alert and Case Management
Centralize incidents sourced from Exabeam or third-party products for an analyst’s manual review or to automate the alert triage workflow.
Put Your Security Skills to the Test
Challenge yourself and compete with peers in a formidable game of Exabeam CTF. You’ll get a firsthand view into the power of Exabeam behavioral analytics, threat hunting, and automation and their ability to transform your team’s TDIR capabilities.

“It had previously been difficult to detect internal fraud at an early stage, but Exabeam scores all suspicious activities, so you can understand at a glance what is different and how it is different. Another advantage of Exabeam is that it does not require advanced skills.”
Hitoshi Uehara
General Manager of Information Systems | BBS Group

Trusted by organizations
around the world





















Frequently Asked Questions
Answer: Exabeam Security Analytics offers more than 1,800 rules, including cloud infrastructure security, and more than 750 behavioral model histograms that automatically baseline normal behavior of users and devices to detect, prioritize, and respond to anomalies based on risk. You can also write, test, publish, and monitor custom correlation rules for your most critical business entities and assets.
Answer: No! You can run Exabeam Security Analytics with your existing SIEM, data lake, or Exabeam SIEM.
Answer: Exabeam Security Analytics is a UEBA product that can run on top of an existing legacy SIEM or data lake to upgrade an organization’s defenses and contend with sophisticated and credential-based attacks.
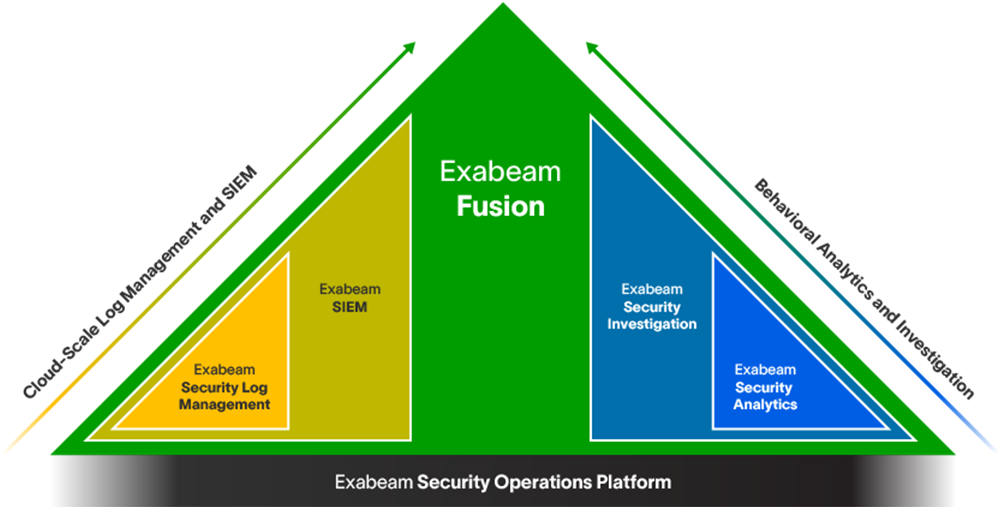
Explore the many ways Exabeam can work for you
Whether you replace a legacy SIEM, or complement an ineffective SIEM solution by adding UEBA, SOAR, and TDIR content, the modular Exabeam Security Operations Platform can help you achieve security operations success.
- SIEM replacement: Exabeam Fusion
- SIEM augmentation: Exabeam Security Investigation
Learn more about the Exabeam Security Operations Platform
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.

DATA SHEET
Exabeam Security Analytics
Security Analytics takes in logs, and upon intake, normalizes and parses them via CIM with data enrichment and threat intelligence to build events that automatically baseline normal behavior of users and devices to detect, prioritize, and respond to anomalies based on risk.

WHITE PAPER
10 Reasons to Augment Your SIEM with Behavioral Analytics
Modern User and Entity Behavior Analytics (UEBA) solutions employ a different approach by using variations of artificial intelligence and machine learning, advanced analytics, data enrichment, and data science to effectively augment your SIEM to combat advanced threats.
What else can Exabeam do for you?
At Exabeam, we deliver persona-based workflows, purpose-built for security. With support resources, professional services, training opportunities, and business partnerships, Exabeam can usher your organization through deployment and beyond.
See the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision










