The role of a CISO is more important than ever in this digital age. Given the increase in cyberattacks and ransomware, many organizations are reevaluating their cybersecurity strategies, how they monitor threats, and how to respond. Moreover, companies now face the challenges of ensuring security across expanding remote work environments.
That said, as a CISO, maintaining the safety, security, and continuity of the enterprise and its data is paramount. A typical tenure for a CISO is 18 months, so you better hit the ground running to achieve your security goals.
With this in mind, here’s a take on what to accomplish in your first 90 days as a CISO.
The Work Starts Before You Get the Job
Get a preparation head start. Open a communication channel with the organization of which you are going to be a part. What does the organization define as a good security outcome? Find out the cybersecurity objectives and timelines for the company (i.e., achieving cybersecurity maturity or recovering from a recent breach and strengthening their posture). This will help to transition into developing a security strategy quickly. Also, get a feeling for the company culture, what they expect from the CISO, and the security strategy in general.
Ask about high-value business processes. Who are the primary users of the systems and products? This begins to provide an overview of the type of internal pressures you may encounter and identify the sources of risks. You will also be able to gauge the percentage of internal and external threats that may arise. For example, sometimes, the most significant insider threat is the indifference of your peers; this must change for you to succeed.
Find out about the stakeholders to whom you’ll answer. For example, where does the CISO position report in relation to the other executives? What do they expect from a C-level executive? Be sure to define the expectations of your role as the CISO, understand what the organization expects and goals.
On the Job – Build Relationships
A large part of a CISO’s success is in your ability to form successful work relations with staff and with other departments. Schedule meetings with the key stakeholders early on. Identify the departments you will be interacting with, including legal, audit, risk, and even sales and marketing This will help to form relationships to implement cybersecurity awareness campaigns and policies.
The CISO must align with the company’s top executives (C-level executives). Find out what they would like to be informed about. What do these key stakeholders need from their new CISO, and what are they looking to fix?
All levels of an organization need to understand the security risks, their role in helping to minimize possible risks, and the policies to follow.
According to KPMG’s ‘Cyber security: it’s not just about technology’ report:
“Cyber security is not a department, but an attitude. Cyber security is often seen as the responsibility of a department of specialist professionals. This mindset may result in a false sense of security and lead to the wider organization not taking responsibility. The real challenge is to make cybersecurity a mainstream approach. This means, for example, that cybersecurity should become part of HR policy, even in some cases linked to remuneration.”
The reality is that most cybersecurity risks rely on the human factor and internal threats, which comprise 60% of all data breaches. For example, attackers look for privileged users with weak security awareness to conduct phishing scams.
Cooperation begins by building relationships. Cooperation amongst peers and understanding their expectations will help new CISOs assess the required security education to identify and implement an effective cybersecurity strategy.
Assess Your Department
Evaluate your current team. Please take into account their skills, personalities, and the department culture. For example, are frontline staff supported by their middle management? Evaluate the existing positions and how the roles can be adjusted or expanded to achieve your security goals, and share how this fits into the long-term career growth of each team member.
Good leaders delegate and great leaders announce their replacements. Within the first month, establish your second-in-command. It’s not essential to name this position out of the gate, but it’s important to understand if the talent is already there or needs to be groomed, or both. Who could take over your job in a crisis? Consider who you could be trained to grow into the role or whether you need to bring in someone from the outside.
Know Thy Auditors
Thanks to the increasing number of regulations, auditors (both external and internal) are a vital part of every organization’s security strategy—so meet them. Who is doing the internal audit, and who does the advisory work? A good rapport with the auditors can help develop good compliance plans and ensure everyone is on the same page.
Most organizations undergo external audits. Contact the external auditors, find out their requirements, and plan to align from the inside out. Understand their processes and the cadence of how they operate. Are they simply concerned with checking the box—or are they looking below the surface?
Understand your industry and its compliance requirements. Are there specific requirements, mandates, or geographic considerations? For instance, if your organization does business in Europe, you must comply with the GDPR. Stay up-to-date regarding what’s at stake and the possible fines and penalties that could impact your business if found non-compliant.
Evaluate Your Stack
The tools you use will shape how effective your security strategy will be; they are the foundation of great capabilities. Assess which tools your department has in the security stack and understand the history behind their purchase. What does your security portfolio look like, and how well are the platforms deployed? Count how many tools your SOC team members must use to do their job; document their complaints well. How many tools in your portfolio would you consider advanced or leverage advanced analytic content specific to use cases you need to deliver to your organization?
Evaluate how many of the security tools available in your portfolio are legacy or outdated. Legacy tools can cause more harm than good. Consider how to justify the addition of (or replacement) legacy tools with advanced security capabilities tailored to the organization’s specific needs.
Don’t Forget Sales, Corporate Communications and Legal
Chief information security officers are not only the head of the security team but are also part of the company executive leadership team. That is why a CISO needs to build relationships with key departments such as sales, operations, and communications.
In the event of an incident, the security team is only part of the incident response. PR and legal also have a hand in reporting, communicating with law enforcement, and other aspects of the incident response process. Thus, it’s essential to meet with PR and align for prompt reporting in case of a breach.
Likewise, legal should be involved in your response processes, including safely communicating under attorney-client privilege. For corporate communications, and by extension PR, make sure to set expectations on who will cover what topics during a significant incident, including creating talking points and meeting the press.
Your Security Strategy Is Based on the Information You Gather
In each interaction you have with your team, especially in the first 90 days, ask, “What’s the first thing we will celebrate”? The celebration should, without question, include your vendors.
Quick wins are essential for esprit de corps and your political capital. Quick wins begin by calling your shots early as a product of your vision and strategy. Let leadership know what you will report on, and when presenting, always call their attention to that detail.
Success is not operating incident-free; success is learning from that incident and reporting on collective failures openly to make a future change. Once you know the lay of the land, it’s time to design your cybersecurity strategy.
Here are some steps to implement:
1. Gather information
You can’t protect what you don’t know. Conduct an assets audit to understand what is critical for the business and must be protected first. Review business processes and understand how the company generates revenue, what sensitive information they manage, and how it is presently managed/stored. Keep in mind what you are legally required to protect according to compliance regulations. Understand how much you are responsible for that’s not presently visible; this could be a subsidiary that’s not fully integrated or critical applications that do not generate usable logs. Again, keep in mind what you are legally required to protect according to compliance regulations.
2. Analyze the threat landscape
Now that you know what you need to protect, analyze what threats you will face. Assess the environment in which the organization operates, including competitors. If your competitors have suffered breaches, you’re likely to face similar attacks. Identify the types of threats your organization needs to address and the techniques and motivations of potential adversaries.
3. Define goals and design your strategy
Hopefully, from discussions with the CEO, you know what the organization expects in cybersecurity. Then, translate those goals into actionable cybersecurity objectives. It’s crucial to pick a framework that allows you to track your progress in implementing security measures.
Evaluate how effective the current security measures are and the level of your organization’s security maturity. Are you protecting the critical infrastructure and assets? Are the compliance processes in line with the requirements?
State a timeline for your plan with measurable milestones and leeway for updates. However, having a target timeline in mind—a two-year plan—will help get everybody on track and measure progress.
4. Establish the right capabilities and desired outcomes
As mentioned above, your strategy relies on having the right capabilities and pre-defined outcomes. Here are some of the capabilities that will help you launch your program on the path to success (not in rank order):
- Create Timelines. Timelines are critical in mapping out a picture of remediation events. Timelines are the product of any outside breach response help you will receive. If needed in a crisis, it should be practiced as part of normal operations. Your team should have an agreed process and the ability to paint this picture.
- Identity. Do you support Zero-Trust? When is adaptive authentication used in your environment, and when is it not? Is it a two-factor or something else? How automated is your entitlement management an automated process? How do you identify credential misuse and compromise?
- Enrichment Capabilities. An important part of your team’s daily workflow will involve taking discrete data and piecing it together with other data to determine the following correct action. If this is left to manual processes or highly complex queries and searches, you are behind in the game. Enrichment, ideally automated enrichment, makes your team more intelligent and faster.
- Defined Outcomes. Problems and difficult questions will occur every day. Your team must be in sync regarding what success looks like and how to get there. What are the things you intend to do better than your industry peers?
- Understand Your Adversaries. Your team should understand how attackers behave, the tactics they deploy, and the techniques they use (familiarity with MITRE ATT&CK as an example).
- Understand Normal. You need to understand what normal behavior looks like for all of your users, roles, and entities.
- Clear and Aligned Metrics. Your organization should have clear goals and measurements from the business and your internal stakeholders. Make sure your reporting is aligned with your adversaries.
- Operate an Extended SOC. Make sure your developers and IT admins are an extension of your program. They don’t report to you but be sure they have the proper protocols to align with your charter.
- Design the Incident Response (IR) plan
Your incident response plan should be a critical part of your cybersecurity strategy. Having an incident response plan ensures the right people know what to do to contain and remediate an attack if an incident becomes a breach. NIST’s Computer Security Incident Handling Guide (SP 800-61) defined 4 phases of an effective incident response strategy.
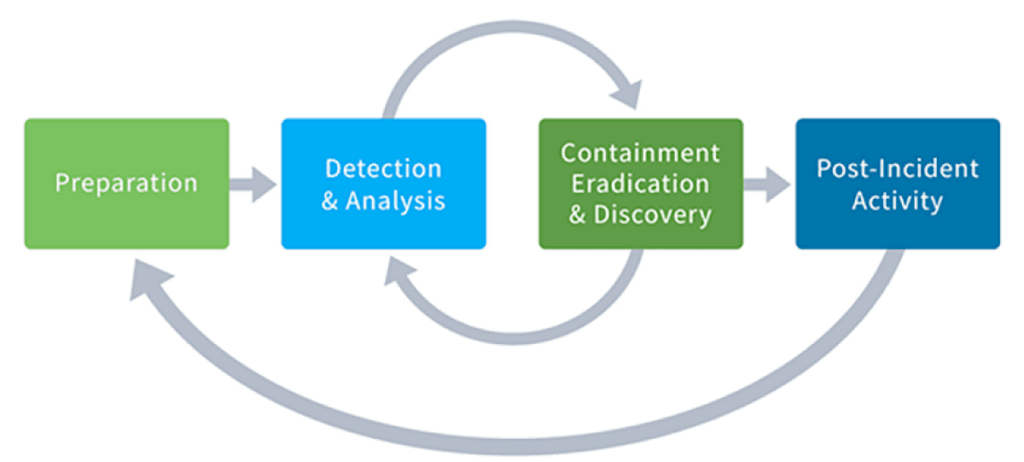
A well-defined incident response plan helps IT teams reduce reaction time, improve remediation, and minimize unexpected problems. Here are 6 steps that will help your team navigate intrusions effectively.
- Assemble your team. People form the core of every incident response team. It is crucial that this team combines individuals with the right skills, expertise, and access to management to ensure that they remain effective during an emergency.
- Detect, ascertain the source and scope. The next step is identifying the source of the incident. Security teams are typically aware of past or current incidents and the indicators that reveal their existence.
- Contain and recover. Once the source is found, it is important to ring-fence the intrusions to minimize access to critical company infrastructure; often known as a remediation event. This can be done by shutting off network access for compromised devices, rolling account resets, and revoking access to users with compromised accounts.
- Assess damage and severity. It can be challenging to estimate the extent of the damage sustained during an attack while the breach is still ongoing. Following threat containment and recovery, incident response teams should take note of the exact areas of the business that were affected during the attack.
- Begin notification process. Legislation such as GDPR and California’s CCPA requires companies to notify the public in the instance of a breach. This process should begin without delay once an incident is remediated and, in some cases, when identified. See Exabeam’s guide on creating a notification letter even before a breach occurs.
- Take steps to prevent the same event in the future. Repeat occurrences of security incidents are not a good look for any company. IT teams should always examine and evaluate why an incident occurred, the effectiveness of existing response strategies, and potential areas for improvement for the future. Failures and gaps must be tracked and remediated, similar to an audit failure.
For more information, including the top Exabeam blogs on incident response check this out.
The Bottom Line
Your first 90 days on the job are key to setting the tone and strategies that will deliver success along the organization. New CISOs must quickly and effectively integrate into the organization to tackle these corporate security goals while enabling high-level protective capabilities protection.
Most security solutions are sold based on functionality, instead of outcomes. When it comes to threat detection, investigation, and response, deploying a Next-Gen SIEM or XDR solution can help you create a proactive security posture. Using a proven and modern solution can make your life and the life of your team easier; focusing on outcomes and saving you time to dedicate to other strategic SOC initiatives.
As the leading Next-Gen SIEM and XDR, the Exabeam Fusion SOC Platform is a modern, modular, and cloud-delivered solution for SIEM and XDR. Exabeam delivers advanced security analytics with automated threat detection, investigation, and response (TDIR) with a use case-based approach focused on delivering outcomes.
See for yourself. Get a demo today.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












