Information Security Explainers:
Cyber Kill Chain: Understanding and Mitigating Advanced Threats
Cyberattacks have evolved dramatically over the past two decades. Social engineering, insider threats, and cloud technology have changed the way we view the information security perimeter, and in many people’s minds, have rendered the perimeter irrelevant.
The cyber kill chain is a traditional security model that describes an old-school scenario — an external attacker taking steps to penetrate a network and steal its data — and breaksdown the steps of the attack to help organizations prepare. Nevertheless, it is still remarkably successful at describing threat vectors and attacks that are facing organizations today.
Related content: This is part of an extensive series of guides about information security.
What is the cyber kill chain?
The cyber kill chain (CKC) is a classic cybersecurity model developed by the computer security incident response team (CSIRT) at Lockheed Martin. The purpose of the model is to better understand the stages required to execute an attack, and to help security teams stop an attack at each of its stages.
The CKC model describes an attack by an external attacker attempting to gain access to data or assets inside the security perimeter. The attacker performs reconnaissance, intrusion of the security perimeter, exploitation of vulnerabilities, gains and escalates privileges, moves laterallyt to gain access to more valuable targets, attempts to obfuscate their activity, and finally, exfiltrates data from the organization.
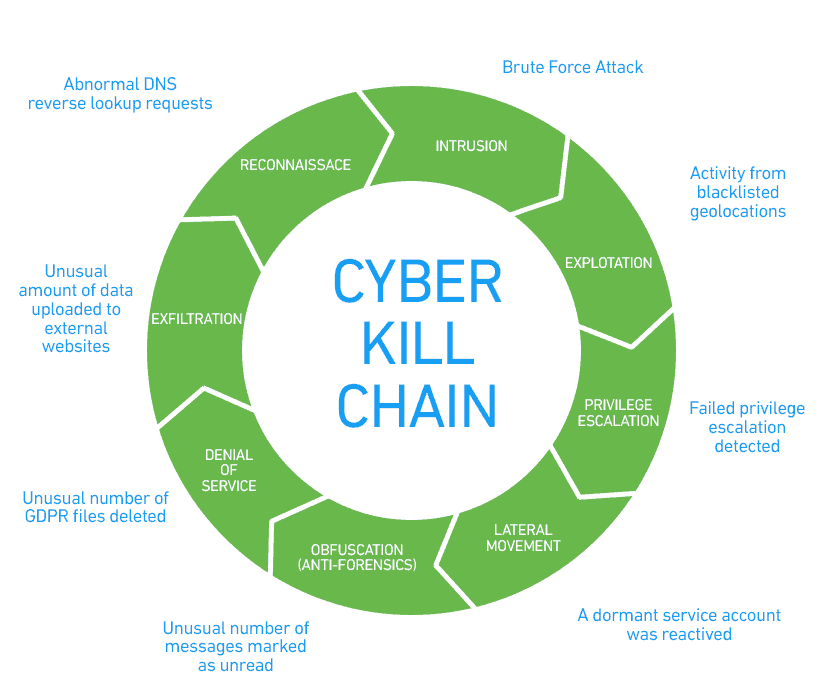
The cyber kill chain model mainly describes an advanced persistent threat (APT), a sophisticated malicious actor waging an organized attack campaign against a specific company.
8 phases of the cyber kill chain
Below, we briefly explain each stage of an attack according to the Lockheed Martin CIRT CKC model. For each stage, you’ll see a brief list of attacks taken from the MITRE ATT&CK Framework, which is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations.
1. Reconnaissance
At the reconnaissance stage, the attacker gathers information about the target organization. They can use automated scanners to find vulnerabilities and weak points that may be able to be penetrated. Attackers will try to identify and investigate security systems that are in place, such as firewalls, intrusion prevention systems, and authentication mechanisms.
2. Intrusion
At the intrusion stage, attackers are attempting to get inside the security perimeter. Attackers commonly inject malware into a system to get a foothold. Malware could be delivered by social engineering emails, a compromised system or account, an “open door” representing a gap in security — such as an open port or unsecured endpoint — or an insider accomplice.
Examples of attacks in the intrusion stage:
- External remote services
- Spear phishing attachments
- Supply chain compromise
3. Exploitation
At the exploitation stage, attackers seek additional vulnerabilities or weak points they can exploit inside the organization’s systems. For example, from the outside, the attacker may have no access to an organization’s databases, but after the intrusion, they can see that a database uses an old version and is exposed to a well-known vulnerability.
Examples of attacks in the exploitation stage:
- PowerShell
- Local job scheduling
- Scripting
- Dynamic data exchange
4. Privilege Escalation
In the privilege escalation stage, the goal of the attacker is to gain privileges to additional systems or accounts. Attackers may attempt brute force attacks, look for unsecured repositories of credentials, monitor unencrypted network traffic to identify credentials, or change permissions on existing compromised accounts.
Examples of attacks in the privilege escalation stage:
- Access token manipulation
- Path interception
- Sudo attack
- Process injection
5. Lateral Movement
In the lateral movement stage, attackers connect to additional systems and attempt to find the organization’s most valuable assets. Attackers move laterally from one system to another to gain access to privileged accounts, sensitive data, or critical assets. Lateral movement is a coordinated effort that may span multiple user accounts and IT systems.
Examples of attacks in the lateral movement stage:
- SSH hijacking
- Internal spear phishing
- Shared webroot
- Windows remote management
6. Obfuscation
At the obfuscation stage, the attacker tries to cover their tracks. They may try to delete or modify logs, falsify timestamps, tamper with security systems, and take other actions to hide previous stages in the CKC and make it appear that sensitive data or systems were not touched.
Examples of attacks in the obfuscation stage:
- Binary padding
- Code signing
- File deletion
- Hidden users
- Process hollowing
7. Denial of Service
At the denial of service (DoS) stage, attackers attempt to disrupt an organization’s operations. Usually the aim is to distract security and operational staff, enabling the malicious actorsto achieve their real goal, which is data exfiltration. DoS can be waged against networks and production systems, including websites, email servers, or customer-facing applications.
Examples of attacks in the DoS stage:
- Endpoint denial of service
- Network denial of service
- Resource hijacking
- Service stop
- System shutdown
8. Exfiltration
At the exfiltration stage, an advanced attacker finally hits home, getting their hands on the organization’s most sensitive data. Attackers will find a mechanism — typically some sort of protocol tunneling — to copy the data outside the organization. Then, they can sell it, use it for additional attacks (for example, in the case of customer personal data or payment details), or openly distribute it to damage the organization.
Examples of attacks in the exfiltration stage:
- Data compressed
- Data encrypted
- Exfiltration over alternative protocol
- Exfiltration over a physical mediumScheduled transfer
Security controls you can use to stop the cyber kill chain
SBS security proposed five methods an organization can use to stop an attack at each of its stages. These are:
- Detect – Determine attempts to scan or penetrate the organization.
- Deny – Stop attacks as they happen.
- Disrupt -Intercept data communications carried out by the attacker and interrupt them.
- Degrade – Create measures that will limit the effectiveness of an attack.
- Deceive – Mislead an attacker by providing false information or setting up decoy assets.
The following information shows how security tools can be used to apply each of the security controls to each kill chain stage.
Reconnaissance
Detect
- Web Analytics
- Threat Intelligence
- Network Intrusion Detection System
Deny
- Information Sharing Policy
- Firewall Access Control Lists
Weaponization
Detect:
- Threat Intelligence
- Network Intrusion Detection System
Deny: Network Intrusion Prevention System
Delivery
Detect:
- Endpoint Malware Protection
Deny:
- Change Management
- Application Allowlisting
- Proxy Filter
- Host-Based Intrusion Prevention System
Disrupt: Inline Anti-Virus
Degrade: Queuing
Contain:
- Router Access Control Lists
- App-aware Firewall
- Trust Zones
- Inter-zone Network Intrusion Detection System
Exploitation
Detect:
- Endpoint Malware Protection
- Host-Based Intrusion Detection System
Deny:
- Secure Password
- Patch Management
Disrupt: Data Execution Prevention
Contain:
- App-aware Firewall
- Trust Zones
- Inter-zone Network Intrusion Detection System
Installation
Detect:
- Security Information and Event Management (SIEM)
- Host-Based Intrusion Detection System
Deny:
- Privilege Separation
- Strong Passwords
- Two-factor Authentication
Disrupt: Router Access Control Lists
Contain:
- App-aware Firewall
- Trust Zones
- Inter-zone Network Intrusion Detection System
Command & Control
Detect:
- Network Intrusion Detection System
- Host-Based Intrusion Detection System
Deny:
- Firewall Access Control Lists
- Network Segmentation
Disrupt: Host-Based Intrusion Prevention System
Degrade: Tarpit
Deceive: Domain Name System Redirect
Contain:
- Trust Zones
- Domain Name System Sinkholes
Actions on Objectives
Detect: Endpoint Malware Protection
Deny: Data-at-rest Encryption
Disrupt: Endpoint Malware Protection
Degrade: Quality of Service
Deceive: Honeypot
Contain: Incident Response
Exfiltration
Detect:
- Data Loss Prevention (DLP)
- SIEM
Deny: Egress Filtering
Disrupt: DLP
Contain: Firewall Access Control Lists
Source: SBS Cybersecurity
How UEBA technology helps identify and stop advanced persistent threats
The cyber kill chain model primarily focuses on advanced persistent threats (APTs). APT attackers excel at hiding their activity and covering their tracks, and can be very difficult to detect once they are inside the corporate network. APT attacks are conducted by a group of skilled hackers who target enterprise systems by infiltrating and moving laterally through the organization over a period of months, while carefully avoiding detection. While each of those steps may evade traditional detection techniques, together they create an anomalous picture.
Modern security tools, such as user and entity behavior analytics (UEBA), can help detect various techniques used by modern attackers. Using machine learning with UEBA provides the ability to learn user behavior and integrate it into the detection engine, saving analysts an enormous amount of detection time.
UEBA dynamically adapts to an environment and, unlike traditional methods, can detect subtle changes in behavior. UEBA can analyze massive amounts of data from disparate systems, and identify anomalous behavior with users, machines, networks, and applications. When something seems abnormal or suspicious, the UEBA system can pick up on it and alert security teams.
In order to resolve behavioral patterns into attack sequences, security analysts need to see the complete picture of the attack kill chain. UEBA should tie all the relevant events together into a timeline to make sense of the attack. This makes it possible to detect APTs and related attacker techniques early in the game before an actual breach occurs. For example, UEBA can detect reconnaissance activity, which appears as irregular network traffic; identify penetration attempts as unusual or suspicious logins; and pick up on anomalous behavior of compromised user accounts in subsequent stages of the attack.
Speed is critical in finding sophisticated attack sequences. With modern tools such as UEBA, security analysts can now trace the steps an attacker has taken and detect them before they cause damage to an organization.
Want to learn more about Information Security?
Have a look at these articles:
- Information security (InfoSec): The Complete Guide
- The 8 Elements of an Information Security Policy
- PCI Security: 7 Steps to Becoming PCI Compliant
- Cloud Security 101
- Threat Hunting: Tips and Tools
- IT Security: What You Should Know
- Machine Learning for Cybersecurity: Next-Gen Protection Against Cyber Threats
- Penetration Testing: Process and Tools






