Information Security Explainers:
Defense In Depth: Stopping Advanced Attacks in their Tracks
In most organizations, the assumption of a security perimeter with trusted objects “inside” and untrusted objects “outside” no longer holds. Malicious insiders, compromised accounts, and zero-day vulnerabilities can quickly place malicious actors inside your network and at close range to critical infrastructure.
Defense in depth (DiD) is a security strategy that helps organizations deal with this situation. The strategy assumes that attackers will, or already have, penetrated different layers of the organization’s defenses. Multiple layers of security are needed to detect attackers at every stage of their attack cycle.
Related content: This is part of an extensive series of guides about information security.
What is defense in depth?
Defense in depth is a cybersecurity approach that uses layered defensive mechanisms to protect systems and data. With layering, if one defense fails, another is there to block an attack. This intentional redundancy creates greater security and can protect against a wider variety of attacks. DiD is also known as the castle approach because it resembles the walls of a castle.
Why is defense in depth important?
Defense in depth helps you ensure that you are protecting your systems as effectively as possible. It forces you to account for security even when your various tools and solutions have been compromised. No security tool or measure is perfect so you need to account for potential failures. By building in layers of security, you can reduce the chance of a single point of failure occurring in your systems.
Defense in depth architecture
Defense in depth architectures use controls that are designed to protect the administrative, technical and physical components of your systems.
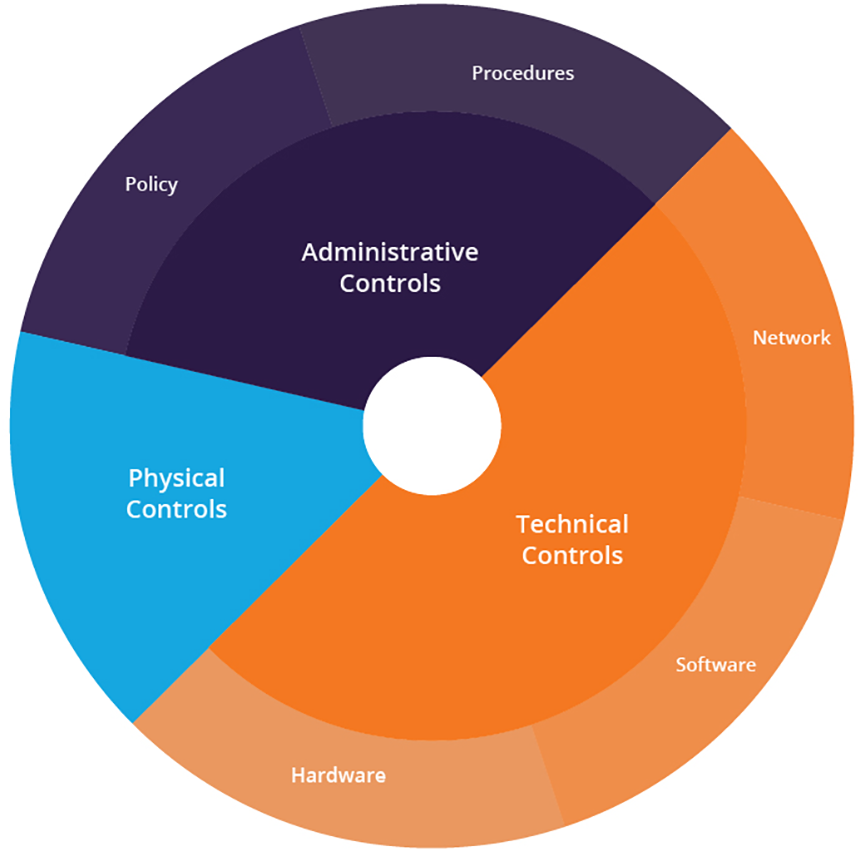
- Administrative controls— include procedures and policies that restrict permissions and guide users on how to maintain security.
- Technical controls— include specialized software and hardware that are used to protect system resources. For example, antivirus or firewall solutions.
- Physical controls— include physical infrastructure for protecting systems, such as locked doors and security cameras.
You can also use additional security layers to protect individual components of your systems:
- Access measures – include biometrics, virtual private networks (VPNs), authentication controls, and timed access.
- Workstation defenses – include anti-spam software or antivirus agents.
- Data protection – includes password hashing, encryption, and secure transfer protocols.
- Perimeter defenses – include intrusion detection and prevention systems and firewalls.
- Monitoring and prevention – include logging, vulnerability scanning, and security training for staff.
- Threat intelligence – data feeds providing up-to-date information about indicators of compromise (IoC), known threat actors and their tactics, techniques and procedures (TTP).
Defense in depth examples
There are many ways in which defense in depth can be applied. Below are two examples.
Website protection
DiD for websites involves a combination of anti-spam and antivirus software, web application firewalls (WAFs), privacy controls and user training. Often, these solutions are bundled in a single product. These tools are then used to protect against threats such as cross-site scripting (XSS) or cross-site request forgery (CSRF). Both of these attacks hijack a user’s session to perform malicious actions.
Network security
DiD for network security typically involves a combination of firewalls, encryption, and intrusion prevention systems. This layering works to first restrict traffic, then to detect when an infiltration occurs. Finally, even if an attack is missed encryption can prevent data from being accessible to attackers.
Important elements of a defense in depth cybersecurity plan
Creating an effective defense in depth strategy takes significant time and resources. To ensure you get the most from your efforts, make sure to include the following:
Audit your system
To effectively secure your systems, you need to know where all your assets are and asset priority levels. This includes files, applications and users. You also need to understand where your vulnerabilities are and how attackers can exploit issues.
Implement behavioral analytics
User and entity behavior analytics (UEBA) can help you monitor your system and users and detect incidents that are missed by traditional tools. UEBA uses behavioral baselines to identify anomalous behavior. This enables you to identify attackers using compromised credentials and malicious insiders.
Prioritize and isolate your data
Try to limit where high priority information is stored and who has access to it. For example, personally identifiable information needs to be secured more fiercely than old marketing materials. By restricting where data is stored and who has access, you reduce the entry points to data and are better able to focus your security efforts.
Use multiple firewalls
There are multiple types of firewalls you can use and you should employ these tools where appropriate. For example, you can use endpoint and app-level firewalls to inspect traffic between your devices. Using firewalls both inside and outside your network allows you to prevent lateral attacks and enables system isolation.
Implement endpoint protection
You should implement endpoint protection platforms (EPPs) to secure your endpoints and restrict access to your systems. These platforms often contain endpoint detection and response (EDR) technology that can help speed your response times and let you detect incidents in real time.
Implement an incident response plan
An incident response plan (IRP) can help you identify vulnerabilities in your systems, plan protective measures, and speed incident response times. IRPs detail who is responsible for managing incidents and how they should respond.
These plans ensure that your responses are standardized and that each incident is treated appropriately. Frequently, these plans include security orchestration, automation and response (SOAR) technologies with automated playbooks to guarantee a fast response.
Multi-Layer Security with Exabeam Security Management Platform
The Exabeam Security Management Platform is a next-generation security information and event management (SIEM) that can handle detection and response to cyber attacks, and also acts as an investigative layer to find malicious behavior in the system, before or during an attack, using advanced analytics. In case an attack is successful, Exabeam also includes incident response capabilities that allow the security team to address the attack and mitigate the damage caused.
Using Exabeam, along with other defense layers, can strengthen your organization’s security, improving your ability to prevent and mitigate advanced cyber attacks.






